Open vSwitch as a virtual network core
This article uses KVM / libvirt for virtualization, but I’ll note right away that the article is not so much about KVM as about the features of the advantages of using Open vSwitch to integrate virtual and physical network devices using VLAN technology (802.1q). In epic times, all sorts of crutches and props of varying degrees of surprise were used to forward tagged traffic to the hypervisor (tuntap, brctl, vconfig, ebtables, etc.), which caused cluttering up the operating system hosting the hypervisor with a large number of unnecessary virtual network interfaces that appealed to the eyes ifconfig and generally grieving administrators with the need to build a standard network device (switch) from individual parts like a bicycle. In addition to supporting 802.1q from the switch, in fact many more functions are required today. So the need for a virtual device with the most appropriate for the functionality of a standard modern managed switch led to the emergence of the project Open vSwitch (hereinafter - OVS).
Let's start from the very beginning by installing a clean copy of ubuntu-14.04.1-server-amd64 with the option "Virtual Machine host". After installation, the system has the following form:
The picture is still simpler:


Another nice moment for those who have already begun to worry about where to place the startup scripts for applying this configuration. You don’t have to do anything else, the OVS configuration by the above ovs-vsctl commands is not only applied, but is automatically saved, so you don’t need to worry about the discrepancy between the current and the saved OVS configuration.
And we only need to update the / etc / network / interfaces file only a little due to the replacement of the eth0 interface with ovs-br0:

For now, let's leave them off.
we will correct virtualok configs
If you look now at the state of the network interfaces of the switch and the operating system, you will see that no changes have occurred. Ports on the switch are not added, there are no unnecessary network interfaces in the system.
Now we will start both VMs:

Open vSwitch , it can be used to organize, for example, the bonding of two interfaces and something else .
That's all. I hope someone will help this article decide to useOpen vSwitch in their projects and just sandboxes instead of the standard linux bridge.

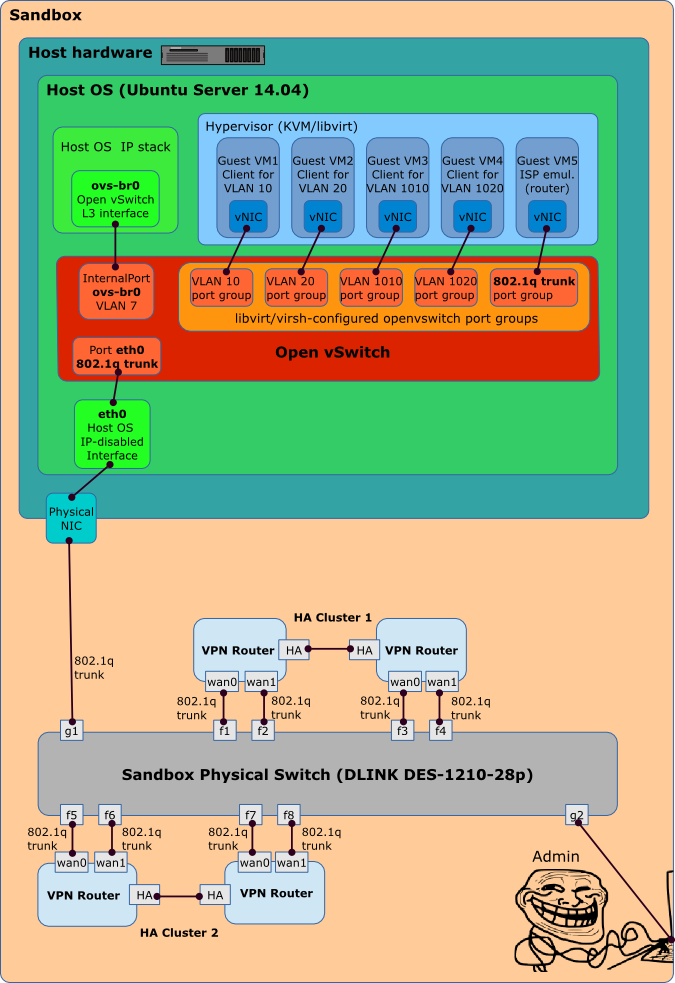
Figure 1: Sandbox ProjectThe KDPV (Figure 1) depicts the OVS case for building a sandbox to prepare for replacing our outdated VPN routers with new ones. It is necessary to configure new VPN routers in the same way as already installed in our company with the same IP addresses, filtering rules and dynamic routing settings. And test everything in the sandbox, emulating ISPs (through which VPN routers connect) and sites of our localhost. But again, this article is not about the complexity of setting up our VPN routers, but about how to connect them to our cozy virtual sandbox through VLAN in general and OVS in particular.
Let's start from the very beginning by installing a clean copy of ubuntu-14.04.1-server-amd64 with the option "Virtual Machine host". After installation, the system has the following form:
Displaying network options utilities
Everything is very standard, or anything unusual.root @ sandbox: ~ # ifconfig | grep -vE 'RX | TX | coll | inet6 | MTU'eth0 Link encap: Ethernet HWaddr 00: 1b: 78: 9c: 2b: fc inet addr: 10.0.7.1 Bcast: 10.0.7.255 Mask: 255.255.255.0 lo Link encap: Local Loopback inet addr: 127.0.0.1 Mask: 255.0.0.0 virbr0 Link encap: Ethernet HWaddr 1a: 70: 19: e9: 3c: c7 inet addr: 192.168.122.1 Bcast: 192.168.122.255 Mask: 255.255.255.0
root @ sandbox: ~ # route -nKernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 0.0.0.0 10.0.7.254 0.0.0.0 UG 0 0 0 eth0 10.0.7.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0 192.168.122.0 0.0.0.0 255.255.255.0 U 0 0 0 virbr0
root @ sandbox: ~ # cat / etc / network / interfaces | grep -v ^ #auto lo iface lo inet loopback auto eth0 iface eth0 inet static address 10.0.7.1 netmask 255.255.255.0 network 10.0.7.0 broadcast 10.0.7.255 gateway 10.0.7.254 # dns- * options are implemented by the resolvconf package, if installed dns-nameservers 10.0.1.1
root @ sandbox: ~ # virsh net-list --allName State Autostart Persistent -------------------------------------------------- -------- default active yes yes
root @ sandbox: ~ # virsh net-dumpxml default<network> <name> default </ name> <uuid> 865fd53b-5bd5-430c-b7c7-664125dee9f6 </ uuid> <forward mode = 'nat'> <nat> <port start = '1024' end = '65535' /> </ nat> </ forward> <bridge name = 'virbr0' stp = 'on' delay = '0' /> <ip address = '192.168.122.1' netmask = '255.255.255.0'> <dhcp> <range start = '192.168.122.2' end = '192.168.122.254' /> </ dhcp> </ ip> </ network>
root @ sandbox: ~ # brctl showbridge name bridge id STP enabled interfaces virbr0 8000.000000000000 yes
The picture is still simpler:

Figure 2: Initial System StatusInstall openvswitch:
apt-get install openvswitch-switchAfter its installation, no changes in the network settings occur, only the OVS service is launched, waiting for our orders. We will not keep him waiting. Enter the following commands from the console or put them in a temporary .sh script and run:
switching the host to the tagged port of the switchovs-vsctl add-br ovs-br0 ovs-vsctl set port ovs-br0 tag = 7 ovs-vsctl add-port ovs-br0 eth0 ovs-vsctl set port eth0 trunks = 7,10,20,1010,1020,30,1030 ifconfig eth0 0 ifconfig ovs-br0 10.0.7.1/24 up ip r add default via 10.0.7.254
Explanations
ovs-vsctl add-br ovs-br0It creates an almost empty instance of the virtual switch, there is only one port to which the same-name internal interface ovs-br0 is connected.
ovs-vsctl set port ovs-br0 tag = 7Configure this port as an access-port for VLAN 7.
ovs-vsctl add-port ovs-br0 eth0We add to our switch another port to which we switch the interface eth0.
ovs-vsctl set port eth0 trunks = 7,10,20,1010,1020,30,1030we do this port trunk for the specified VLAN ID. In principle, the trunks parameter can be omitted at all, then the port will skip all VLAN IDs.
ifconfig eth0 0Reset IP configuration for eth0. It will no longer be associated with the OS IP stack.
ifconfig ovs-br0 10.0.7.1/24 upInstead of eth0 to the IP stack of the OS, we screw the internal interface ovs-br0.
ip r add default via 10.0.7.254Well, do not forget to restore the routing table
We switch a host to the tagged port of the switchWe are online! (with)
We look that changed in network settings
Well, in the form of pictures:root @ sandbox: ~ # ovs-vsctl show40952e4d-81ad-433b-b08b-f88ccd55f26a Bridge "ovs-br0" Port "ovs-br0" tag: 7 Interface "ovs-br0" type: internal Port "eth0" trunks: [7,10,20,1010,1020,30,1030] Interface "eth0" ovs_version: "2.0.2"
root @ sandbox: ~ # ifconfig | grep -vE 'RX | TX | coll | inet6 | MTU'eth0 Link encap: Ethernet HWaddr 00: 1b: 78: 9c: 2b: fc lo Link encap: Local Loopback inet addr: 127.0.0.1 Mask: 255.0.0.0 ovs-br0 Link encap: Ethernet HWaddr 00: 1b: 78: 9c: 2b: fc inet addr: 10.0.7.1 Bcast: 10.0.7.255 Mask: 255.255.255.0 virbr0 Link encap: Ethernet HWaddr 32: b9: dd: 38: 09: f5 inet addr: 192.168.122.1 Bcast: 192.168.122.255 Mask: 255.255.255.0
root @ sandbox: ~ # route -nKernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 0.0.0.0 10.0.7.254 0.0.0.0 UG 0 0 0 ovs-br0 10.0.7.0 0.0.0.0 255.255.255.0 U 0 0 0 ovs-br0 192.168.122.0 0.0.0.0 255.255.255.0 U 0 0 0 virbr0

Nothing unexpected, everything is logical and intuitive.Figure 3: Install openvswitch and connect it to OS IP stack instead of eth0. The virbr0 switch interface will not be shown later, it is not interesting for us and does not affect anything.
Another nice moment for those who have already begun to worry about where to place the startup scripts for applying this configuration. You don’t have to do anything else, the OVS configuration by the above ovs-vsctl commands is not only applied, but is automatically saved, so you don’t need to worry about the discrepancy between the current and the saved OVS configuration.
And we only need to update the / etc / network / interfaces file only a little due to the replacement of the eth0 interface with ovs-br0:
But the switch currently has only two ports, how can we connect our 5 virtual machines to it? There are at least 2 ways. The first, the most obvious one, is to add a port using the ovs-vsctl add-port command (access or trunk option).root @ sandbox: ~ # cat / etc / network / interfaces | grep -v ^ #auto lo iface lo inet loopback auto eth0 iface eth0 inet manual auto ovs-br0 iface ovs-br0 inet static address 10.0.7.1 netmask 255.255.255.0 network 10.0.7.0 broadcast 10.0.7.255 gateway 10.0.7.254 # dns- * options are implemented by the resolvconf package, if installed dns-nameservers 10.0.1.1
Then you can select it directly in the virt-manager GUI to connect the network interface of the virtual machine. But we will go in a more scalable way. At the same time, it is not necessary to create ports at all (as is the case with the standard linux core bridge). Instead, you can create a port group for OVS. Each port group is intended to connect the VM to the corresponding VLAN. Unfortunately, their configuration from the virt-manager GUI is not available, you must manually prepare a simple XML file describing the necessary port groups and then apply it via the libvirt API using the virsh command, as follows:ovs-vsctl add-port ovs-br0 vlan10 tag = 10 - set interface vlan10 type = internal- (two lines) is used to execute several ovs-vsctl commands in one line.
XML config for the configuration shown in Figure 1
We execute these commands:<network> <name> ovs-network </ name> <forward mode = 'bridge' /> <bridge name = 'ovs-br0' /> <virtualport type = 'openvswitch' /> <portgroup name = 'vlan-10 '> <vlan> <tag id = '10' /> </ vlan> </ portgroup> <portgroup name = 'vlan-20'> <vlan> <tag id = '20 '/> </ vlan> </ portgroup> <portgroup name = 'vlan-1010'> <vlan> <tag id = '1010' /> </ vlan> </ portgroup> <portgroup name = 'vlan-1020'> <vlan> <tag id = ' 1020 '/> </ vlan> </ portgroup> <portgroup name =' trunkPortGroup '> <vlan trunk =' yes '> <tag id = '30' /> <tag id = '1030' /> </ vlan> </ portgroup> </ network>
vi /tmp/ovs-network.xml virsh net-define /tmp/ovs-network.xml virsh net-start ovs-network virsh net-autostart ovs-network
Explanations
vi /tmp/ovs-network.xmlcopy the above XML content into this file
virsh net-define /tmp/ovs-network.xmlconfiguring new network for KVM
virsh net-start ovs-networkrun it
virsh net-autostart ovs-networkmake its launch automatic
to remove unwanted network
we represent the resulting:virsh net-destroy ovs-network virsh net-autostart --disable ovs-network virsh net-undefine ovs-network

Figure 4: Created port groups for our VMsLet's create a pair of VM1 and VM2 virtual machines in virt-manager and when creating the Advanced options Virtual network 'ovs-network' option: Bridge network
For now, let's leave them off.
we will correct virtualok configs
virsh edit VM1Find the interface section and add the portgroup parameter
<interface type = 'network'>
<mac address = '52: 54: 00: 5e: b9: b2 '/>
<source network = 'ovs-network' portgroup = 'vlan-10' />
<model type = 'virtio' />
<address type = 'pci' domain = '0x0000' bus = '0x00' slot = '0x03' function = '0x0' />
</ interface>
If you look now at the state of the network interfaces of the switch and the operating system, you will see that no changes have occurred. Ports on the switch are not added, there are no unnecessary network interfaces in the system.
Now we will start both VMs:
and check the host network settings again
As you can see, the ports of the corresponding port-groups were added to the switch, and the system added a pair of interfaces with MAC addresses corresponding to the VMs (if you turn off the VM, the corresponding ports and interfaces will disappear again).root @ sandbox: ~ # ovs-vsctl show
40952e4d-81ad-433b-b08b-f88ccd55f26a
Bridge "ovs-br0"
Port "vnet0"
tag: 10
Interface "vnet0"
Port "ovs-br0"
tag: 7
Interface "ovs-br0"
type: internal
Port "eth0"
trunks: [7, 10, 20, 1010, 1020, 30, 1030]
Interface "eth0"
Port "vnet1"
tag: 20
Interface "vnet1"
ovs_version: "2.0.2" root @ sandbox: ~ # ifconfig | grep -vE 'RX | TX | coll | inet6 | MTU'
eth0 Link encap: Ethernet HWaddr 00: 1b: 78: 9c: 2b: fc
lo Link encap: Local Loopback
inet addr: 127.0.0.1 Mask: 255.0.0.0
ovs-br0 Link encap: Ethernet HWaddr 00: 1b: 78: 9c: 2b: fc
inet addr: 10.0.7.1 Bcast: 10.0.7.255 Mask: 255.255.255.0
virbr0 Link encap: Ethernet HWaddr 32: b9: dd: 38: 09: f5
inet addr: 192.168.122.1 Bcast: 192.168.122.255 Mask: 255.255.255.0
vnet0 Link encap: Ethernet HWaddr fe: 54: 00: 5e: b9: b2
vnet1 Link encap: Ethernet HWaddr fe: 54: 00: 7f: 40: d0 
Figure 5: running a pair of VMsI will also mention that 802.1q is not the only feature of
That's all. I hope someone will help this article decide to use
')
Source: https://habr.com/ru/post/242741/
All Articles