4SICS Conference: Vulnerable Collider, Havex Trojan, and Other “Russian Threats”
Modern automated process control systems are increasingly vulnerable to hackers - however, vendors and users are in no hurry to recognize and correct a dangerous situation. This observation was the main topic of discussion at the international summit on the safety of industrial control systems 4SICS , which was held in late October in Stockholm.
“Despite the entire Internet revolution, we are still not sufficiently concerned about security, because the old IT paradigm tells us: we function autonomously, are not connected to anyone, we have our own cunning software, and no one can attack us. But the reality has changed a long time ago, ”said one of the key speakers of the event, Stefan Löders, head of security at the European Center for Nuclear Research (CERN).
')

Among the problems of the "new reality" that upset Löders, the shortcomings of the Siemens SIMATIC WinCC Open Architecture platform were mentioned - it is used to manage many critical objects in different countries of the world, from Zurich Airport to the Large Hadron Collider (the latter is precisely CERN). Vulnerabilities in this SCADA platform were found two years ago by Positive Technologies experts, who demonstrated the ability to gain full access to the management system using the vulnerabilities found.
At the 4SICS conference, the Deputy CEO of Positive Technologies Sergey Gordeychik demonstrated new examples of techno nightmares that could be caused by an attack on SCADA systems. The report entitled The Great Train Cyber Robbery showed how the vulnerabilities of IT components in an automated process control system can affect functional safety in various industries. Sergey stressed that these are not isolated cases: company experts regularly discover zero-day vulnerabilities in SCADA systems, examining the security of solutions from various manufacturers, including ABB, Emerson, Honeywell, Siemens, and others.

It is worth noting that the conference was held in the capital of Sweden just at the time when the territorial waters of this country were stubbornly searching for a Russian submarine . Although the Swedes have been searching for this mysterious submarine for the first time in the past 33 years, the current campaign has come out particularly noisy: thanks to the media and social networks, one amateur photo of a
For example, a representative of the Swedish information security company Netresec gave a report on the Havex Trojan , which was used this year for a multi-stage attack on European automated process control systems: hackers hacked vendor sites and infected the official SCADA distributions, which were then downloaded by clients and launched into work. As a result, the attackers managed to gain control over management systems in several companies in France, Germany and other countries where infected software was used.
In general, the report of the Swedish information security experts came out very informative, and even the vendors who distributed the infected software were disclosed. But at the same time, on the very first slides of the presentation, one could see a statement that the hacker group was acting "from the territory of Russia, in the interests of Russia, and probably with the support of the Russian authorities":
"It’s possible that they are not allowed to enter the country."

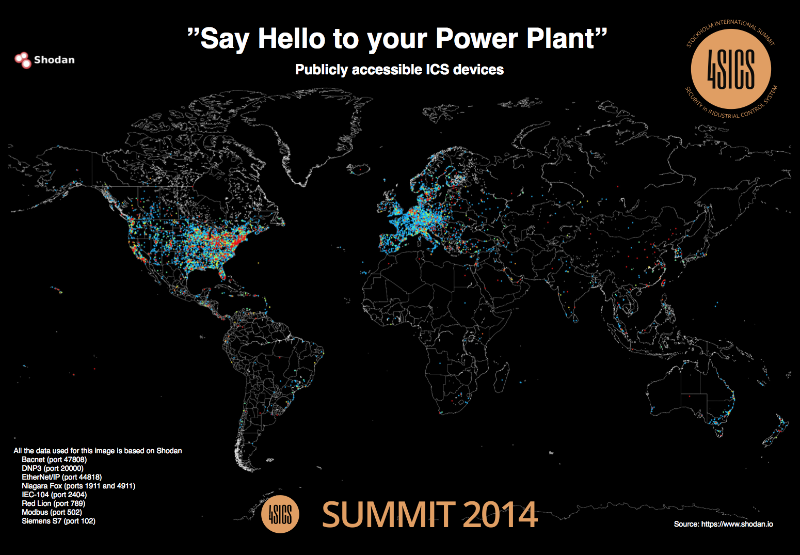
However, there were also speakers at the conference who appreciated the contribution of Russian information security specialists to the ennoblement of the Universe. That turned out to be John Materley, the creator of the project Shodan.io. This "search engine on the Internet of Things" scans the Internet in search of automated control systems with online access, and displays these systems on an interactive map . Presenting the results of his project’s work on the 4SICS forum, John Materli said a big thank you to the team of security experts at the automated process control systems from Positive Technologies, especially Dmitry Efanov and Alexander Timorin.
At the conclusion of the conference, the participants held a round table discussion on forecasts in the field of safety of industrial control systems for the next 5-10 years. The predictions were unhappy: the most serious challenge to the security of the near future was called parting with Windows XP , and generally concluded that there was no improvement in the situation. Dale Peterson, the founder of Digital Bond and a former NSA analyst, commented on these decadent attitudes very succinctly : “Well then just relax.”
Source: https://habr.com/ru/post/242589/
All Articles