Hackers hacked more than 3 million iTunes accounts?
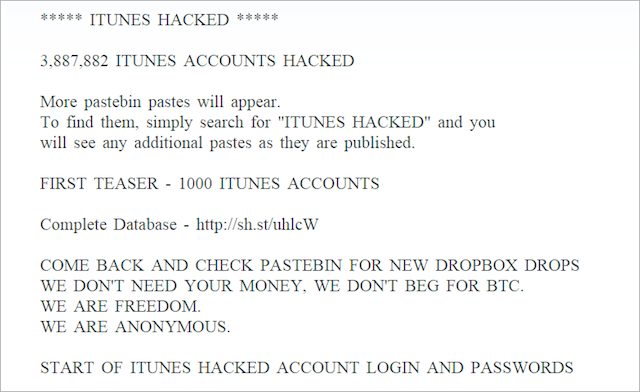
On Tuesday, there were reports of a leak of 3,887,882 iTunes accounts on the Internet. The base with the accounts and passwords unknown posted on Pastebin.com and several other sites. Currently, these records have already been deleted, but we can access some statistics, which are listed below.
In the published file, the most common passwords are:
')

Most of the passwords are fairly well-known; they are headed by similar “ratings” year after year. In a study by Positive Technologies on corporate network security in 2013, the password “123456” turned out to be the most popular even among system administrators: it was used by administrators of internal networks in every third system. Unfortunately, despite all such leaks, simple vocabulary passwords continue to be the most massively vulnerable even where corporate security policies are supposed to exist.
On the other hand, in the list of the most popular passwords from hacked iTunes accounts there are unexpected options that raise questions - for example, EBEANS. It seems strange and rating mail domains, the most common in the database. Do so many connoisseurs of iTunes use the old Hotmail service?

And here are a dozen of the most common mail domains from the .ru zone. There are some oddities here too:

At the moment, it is not known whether this leakage is a consequence of the exploitation of some kind of new vulnerability, or whether it is composed of many databases collected at different times using various attacks, including phishing, trojans and brute force. How "live" are the accounts in this database, too, is still unknown.
Recall that in early September, multi-million databases of hacked accounts for Yandex.Mail, Mail.ru and Gmail were published. At the same time, some experts noted that the “leaks” were most likely collected from many different bases (including very old ones), and they were all laid out at once to achieve a certain resonance in public opinion. For example, to promote two-factor identification or USB keys. It is possible that the story about hacking iTunes is of the same sort.
UPD: According to the results of data validation by a number of mail servers, the next “compilation of old practices” was presented, and it was updated several months ago. At the same time, there are actually working accounts in the list.
Source: https://habr.com/ru/post/242439/
All Articles