SSL3 protocol check in 20 bank clients
More than a week has passed since the critical SSL3 vulnerability (CVE-2014-3566) has become publicly available. Let's see how TOP 20 banks reacted to this news.
For HTTPS testing, we will use the wonderful tool www.ssllabs.com
Let's start with something big and green.
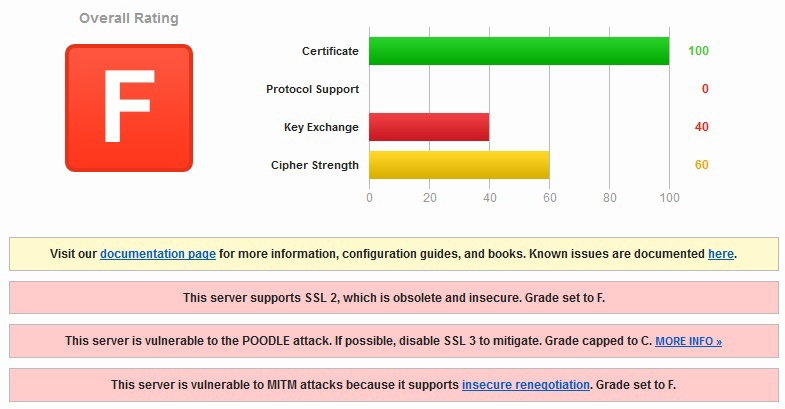
The first result is immediately very indicative:
This server is vulnerable to the POODLE attack. If possible, disable SSL 3 to mitigate. Grade capped to C.
This server supports insecure renegotiation. Grade set to F.
')
Comments are superfluous (although, to be fair, I must say that in the evening of 10/22/2014 the rating was C.
Well, well, let's look at someone, say, a blue of three letters and two numbers:
This server is vulnerable to the POODLE attack. If possible, disable SSL 3 to mitigate. Grade capped to C.
I think you should not repeat further and give statistics on 20 banks:
SSL3 is disabled for three banks, partially for two banks (it is disabled for physicists, enabled for legal entities).
In 15 banks, SSL3 is NOT disabled.
At least two bank clients work ONLY via SSL3!
Four banks have a safety rating of F.
And on the screen, so to speak, Epic F.
Source: https://habr.com/ru/post/241293/
All Articles