Cryptographic solutions. From crypto providers to browser plug-ins
Manufacturers of cryptographic information protection (CIPS) offer various mechanisms for integrating cryptographic tools into information systems. There are solutions focused on supporting systems with a Web interface, mobile and desktop applications, server components. SKZI are integrated into Microsoft applications and into Open Source products, provide support for various application protocols and electronic signature formats.
Given the growing number of projects using EDS and the emergence of mass projects for individuals, developers of such projects need to be well-versed in the EDS solutions offered by manufacturers in order to make the system user-friendly and inexpensive in terms of technical support. Thus, even 5 years ago, the main factor in choosing a cryptographic tool was its full compliance with the requirements of regulators, with today's diversity, important criteria may include coverage of supported platforms, the ability to integrate with a browser, support for mobile users, the ability to install without system administrator rights, etc. .
This material attempts to classify the means of cryptographic protection of information.
The classification is based on:
In addition, it shows how to integrate SKZI with Web-based applications and the possibility of its use on mobile platforms
')
The general classification scheme is shown in the table:
In the first article we will look at solutions, starting from crypto-providers through browser plug-ins inclusive. In subsequent articles will be considered the remaining funds.
The de facto industry standard is the class of cryptographic agents known as crypto-providers. A cryptographic provider is a library providing a special API and specially registered in the OS, which allows you to expand the list of cryptoalgorithms supported in the OS.
It should be noted that the imperfection of the extension mechanisms offered by MS Windows forces crypto-provider developers to further modify high-level crypto libraries and MS Windows applications in the process of their execution in order to “teach” them to use Russian cryptoalgorithms.
It should be understood that not all single types of SKZI implement the full scope of functionality shown in the tables. To clarify the capabilities of the crypto tools, please contact the manufacturer.
Problems:
Pros:
The Open Source library OpenSSL has broad cryptographic capabilities and a convenient mechanism for its expansion with other cryptoalgorithms. OpenSSL is the main crypto core for a wide range of open source applications.
After GOSTs were added to this library by Cryptocom, patches appeared for the "hotelization" of many popular applications using OpenSSL. On the basis of OpenSSL, some vendors have developed and certified SKPI, in addition to the number of products OpenSSL is "implicit" way.
Problems:
Pros:
The PKCS # 11 library provides a universal cross-platform software interface to USB tokens and smart cards.
Functions are divided into:
Thus, the PKCS # 11 standard supports a full set of cryptographic primitives suitable for implementing cryptographic formats (PKCS # 7 / CMS / CADES, PKCS # 10, X.509, etc.) and protocols (TLS, IPSEC, openvpn, etc.).
To ensure speed, a part of crypto-primitives can be implemented in software.
In the PKCS # 11 standard, starting from version 2.30, GOST R 34.10-2001, GOST R 34.11-94, GOST 28147-89 are supported.
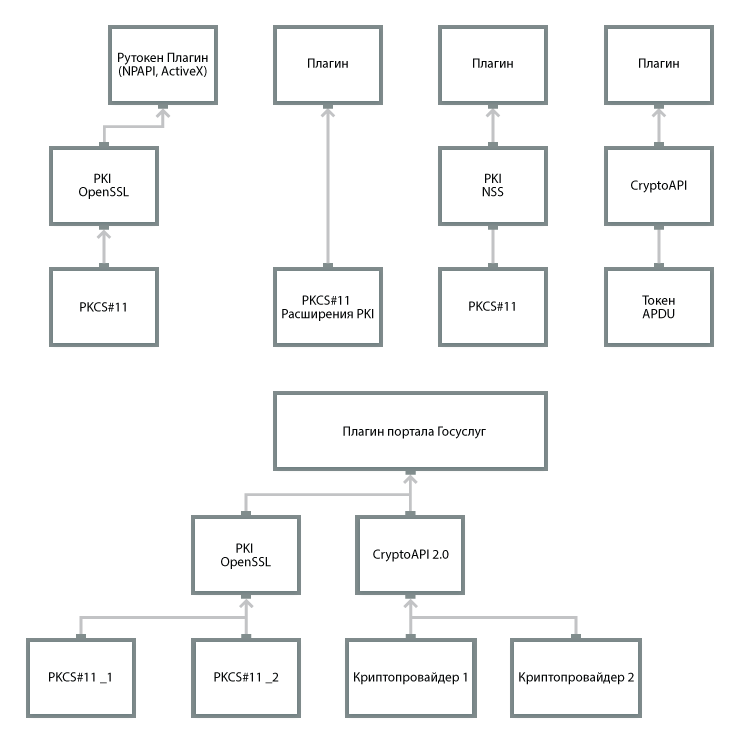
Using the library PKCS # 11 ensures software compatibility of various vendors when working with tokens. Through PKCS # 11 interface, applications written on the basis of CryptoAPI, NSS, OpenSSL can work.
An example of application compatibility is shown in the diagram. Thus, it is possible to use a suitable application in the appropriate place of the information system.
PKCS # 11 are also without the support of hardware devices with software implementation of cryptoalgorithms and storage of objects in the file system.
Examples - PKCS # 11 integrated into NSS (Mozilla), aToken project, Agave-Pro library.
The company Crypto-Pro has a library PKCS # 11, implemented on the basis of MS CryptoAPI:
There are PKCS # 11 libraries for mobile platforms. An example of such a library is the library for Rutoken EDS Bluetooth, which allows you to use your device on iOS and Android.
NSS is a Mozilla community cryptographic library. NSS is used by applications such as the Mozilla Firefox browser, the Mozilla Thunderbird email client.
Currently there are two projects on the "hotelization" of the NSS:
Proprietary libraries provide their own API for embedding into applications. You can add to this list:
The basic principle of the local proxy is to accept an unprotected connection from the application, set up a TLS tunnel with a remote server, and transfer the “application layer” between the application and the remote server through this tunnel.
In addition, some local proxies are additionally complemented with a special digital signature mechanism of specially marked WEB forms (Inter-PRO, MagPro Crypto Tunnel). There are local proxies that provide the WEB API of the digital signature for the browser (a system of HTTP requests and responses similar to the software API of the crypto library).
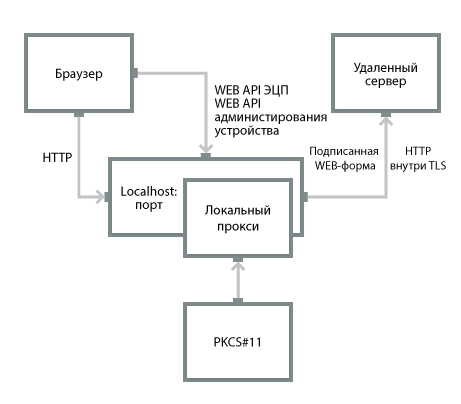
Problems:
Pros:
In order to call the native library from the WEB-page scripts, most browsers support special extensions - ActiveX for IE and NPAPI-plugin for GH, MF, Opera, Safari, etc. Currently there is a wide range of products related to browser plug-ins on the market . Architecturally, these plug-ins can be executed in different ways. Some of them work on the basis of CryptoAPI and require additional installation of a crypto-provider, others use PKCS # 11-compatible devices as a crypto-core and do not require installation of additional SKZI on the client’s workplace. There are universal plug-ins that support both all main crypto-providers and a wide range of hardware SKZI.
Problems:
Pros:
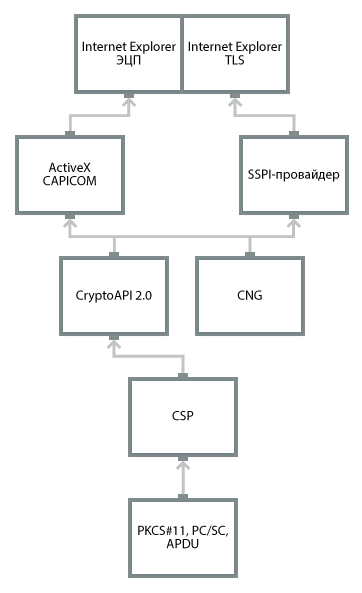
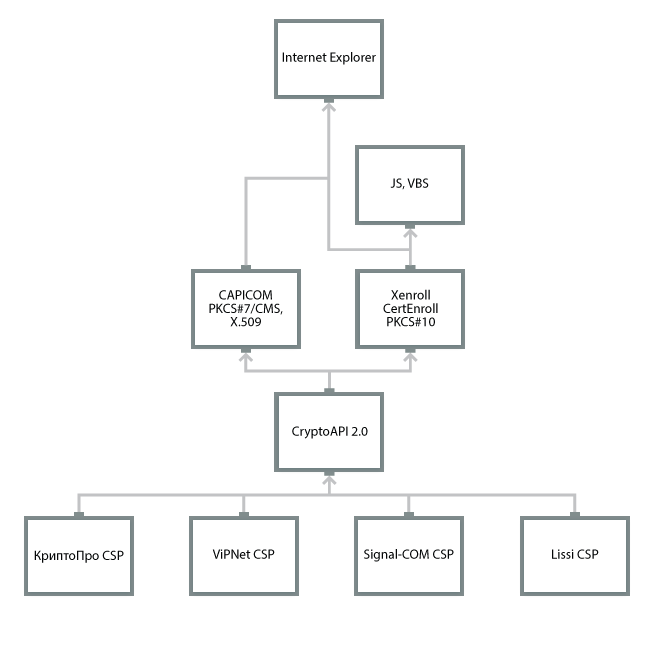
Microsoft has developed two main client-side ActiveX components that translate CryptoAPI functionality into scripts and into a browser.
To generate a key and create a PKCS # 10 request, the XEnroll / CertEnroll component is used, and the CAPICOM component is used for EDS / encryption and working with certificates.
In the following articles, the remaining solutions will be considered in detail.
Given the growing number of projects using EDS and the emergence of mass projects for individuals, developers of such projects need to be well-versed in the EDS solutions offered by manufacturers in order to make the system user-friendly and inexpensive in terms of technical support. Thus, even 5 years ago, the main factor in choosing a cryptographic tool was its full compliance with the requirements of regulators, with today's diversity, important criteria may include coverage of supported platforms, the ability to integrate with a browser, support for mobile users, the ability to install without system administrator rights, etc. .
This material attempts to classify the means of cryptographic protection of information.
- Considered mainly SKZI used on client sites to protect client-server connections via TLS, to organize digital signature, encrypt the transmitted data;
- CRPDs used to create VPNs and file system encryption, stored data, and CAs are not considered;
- Separately allocated hardware cryptographic devices.
The classification is based on:
- integration technologies (CryptoAPI, Active-X, NPAPI, etc.), which support CMIS for embedding into applications and application systems;
- interfaces that provide the CMIS for embedding in applications and application systems.
In addition, it shows how to integrate SKZI with Web-based applications and the possibility of its use on mobile platforms
')
The general classification scheme is shown in the table:
| Crypto Providers | Native libraries (openssl-style, PKCS # 11, NSS, own interfaces) | Local proxies | Browser Plugins | Cloud signature | Browsers with Russian cryptography |
| Email clients with Russian cryptography | Russian cryptography in frameworks, platforms, interpreters | Desktop cryptographic applications | BIOS cryptography UEFI | EDS service providers | Trusted Environment Emulators |
| Hardware |
In the first article we will look at solutions, starting from crypto-providers through browser plug-ins inclusive. In subsequent articles will be considered the remaining funds.
Crypto Providers
The de facto industry standard is the class of cryptographic agents known as crypto-providers. A cryptographic provider is a library providing a special API and specially registered in the OS, which allows you to expand the list of cryptoalgorithms supported in the OS.
It should be noted that the imperfection of the extension mechanisms offered by MS Windows forces crypto-provider developers to further modify high-level crypto libraries and MS Windows applications in the process of their execution in order to “teach” them to use Russian cryptoalgorithms.
It should be understood that not all single types of SKZI implement the full scope of functionality shown in the tables. To clarify the capabilities of the crypto tools, please contact the manufacturer.

| Specification | Microsoft CSP, Microsoft CNG, CryptoAPI 1.0 -> CryptoAPI 2.0 |
| Platforms | Windows family. There is a port on GNU \ Linux, OS X, iOS, Android |
| Algorithms and cryptographic protocols | EDS, encryption, hash function, imitation protection, HMAC, VKO; TLS, EAP-TLS, Kerberos |
| PKI Integration | X.509, PKCS # 10, CMS, CRL, OCSP, TSP |
| EDS mechanisms | Native program interface, C-style; Embedding in applications |
| Authentication mechanisms | Client authentication within TLS. KERBEROS authentication in the Windows domain. Own authentication mechanisms based on random data EDS |
| TLS Guest Accommodation Mechanisms | Embedding in system TLS |
| Application Protocol Support | HTTPS, SMTPS, IMAPS, POP3S, RDP, NNTPS, FTPS, LDAPS |
| Secure Message Formats | PKCS # 7, CMS, XMLSec, S / MIME; CADES (CryptoPro EDS), PDF signature (CryptoPro PDF), MS Office Signature (CryptoPro Office Signature) |
| Browser Integration | EDS in IE via ActiveX CAPICOM, PKCS # 10 via ActiveX XEnroll / CertEnrool TLS in IE through embedding in SSPI-provider EDS in various browsers through proprietary plug-ins (CryptoPro Pro EDS Browser Plugin) TLS proxy (CryptoPro sTunnel) Custom browsers (CryptoPro Fox, Digital Design Protected Browser) |
| Directory Service Integration | MS Active Directory; client part with arbitrary LDAP directory |
| Mobile platforms | Port CryptoPro CSP on iOS, Android |
| Commandline utility | there is |
| Keystores | Registry, USB Tokens |
| Interacting with USB tokens | Keys and Certificates Store Use of hardware implementation of algorithms Via PKCS # 11, PC / SC, APDU |
| Applications | IE, Microsoft Office, Microsoft Outlook Express, Microsoft Outlook, Microsoft Word / Excel, Microsoft Authenticode, Microsoft RDP, Microsoft Certification Authority, Microsoft IIS, Microsoft Exchange, Microsoft Terminal Server, Winlogon, Microsoft EFC Proprietary applications Open source software (sTunnel, FireFox, Apache via Trusted TLS, patch for OpenVPN) Adobe Reader SAP |
| Framework Integration | Microsoft .NET (CryptoPro .NET) |
| Installation | Setup program requires system administrator rights |
| Examples (GOST) | CryptoPro CSP ViPNet CSP Signal-COM CSP Lissy CSP CryptoPro Rutoken CSP Validata CSP |
Problems:
- Lack of normal cross-platform;
- Installation with administrator rights, setting;
- Installing a Windows update may require an ISP update;
- The need to embed in applications by modifying the code "on the fly";
- CSP is a non-native interface for non-Windows applications.
Pros:
- Wide coverage of Windows applications;
- Rich toolkit for developers of secure systems;
- Proven on a large number of projects technology.
Native Libraries
Openssl-style
The Open Source library OpenSSL has broad cryptographic capabilities and a convenient mechanism for its expansion with other cryptoalgorithms. OpenSSL is the main crypto core for a wide range of open source applications.
After GOSTs were added to this library by Cryptocom, patches appeared for the "hotelization" of many popular applications using OpenSSL. On the basis of OpenSSL, some vendors have developed and certified SKPI, in addition to the number of products OpenSSL is "implicit" way.

| Specification | The OpenSSL API is one of the de facto standards for open source software. |
| Platforms | Windows family, GNU \ Linux, OS X, iOS, Android |
| Algorithms and cryptographic protocols | EDS, encryption, hash function, imitation protection, HMAC, VKO; Tls |
| PKI Integration | X.509, PKCS # 10, CMS, CRL, OCSP, TSP |
| EDS mechanisms | Native program interface, C-style; |
| Authentication mechanisms | client authentication within TLS own mechanisms based on e-signature of random data |
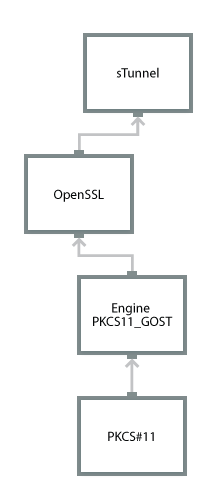
| TLS Guest Accommodation Mechanisms | TLS with Russian cryptography is supported in the library (in the case of using OpenSSL as a browser crypto engine) OpenSSL-based TLS proxy (for example, sTunnel) |
| Secure Message Formats | PKCS # 7, CMS, XMLSec (when used with the library www.aleksey.com/xmlsec , including GOST), S / MIME |
| Browser Integration | Through TLS-proxy Through proprietary plugins In Chromium OpenSSL one of the possible crypto engines |
| Directory Service Integration | Openldap |
| Mobile platforms | iOS, Android |
| Commandline utility | there is |
| Keystores | Files, USB tokens |
| Interacting with USB tokens | Keys and Certificates Store Use of hardware implementation of algorithms Via PKCS # 11 |
| Applications | OpenVPN, Apache, sTunnel, Nginx, Postgre SQL, postfix, dovecot Proprietary applications |
| Framework Integration | OpenSSL is integrated into a large number of frameworks (PHP, Python, .NET, etc.), but there is no GOST. Required to release patches to frameworks |
| Installation | The installer, in general, does not require system administrator rights Copying Starting using cryptographic applications from a USB flash token |
| Examples (GOST) | MagPro CryptoPack LearSL OpenSSL (non-graded) OpenSSL + engine PKCS11_GOST + Rutoken EDS |
Problems:
- OpenSSL and its equivalents are not supported by Microsoft applications;
- The need to patch open source software that supports OpenSSL to enable GOST.
Pros:
- Cross-platform;
- Use in a huge number of projects, open source of most of the project - the identification and elimination of vulnerabilities (as an example, the recent identification of heartbleed);
- Distributed by copying - you can make applications that do not require installation;
- Wide coverage of open source software applications, based on which you can make protected certified products;
- Broad integration into frameworks, but at the same time problems with GOST.
PKCS # 11
The PKCS # 11 library provides a universal cross-platform software interface to USB tokens and smart cards.
Functions are divided into:
- Access functions to the device;
- Functions for writing / reading arbitrary data;
- Key management functions (search, create, delete, import, export);
- The functions of working with certificates (search, import, export);
- EDS functions;
- Hash functions;
- Encryption features;
- Calculation functions imitovstavki;
- Functions for generating a matching key (Diffie-Hellman);
- Session key export / import functions;
Thus, the PKCS # 11 standard supports a full set of cryptographic primitives suitable for implementing cryptographic formats (PKCS # 7 / CMS / CADES, PKCS # 10, X.509, etc.) and protocols (TLS, IPSEC, openvpn, etc.).
To ensure speed, a part of crypto-primitives can be implemented in software.
In the PKCS # 11 standard, starting from version 2.30, GOST R 34.10-2001, GOST R 34.11-94, GOST 28147-89 are supported.
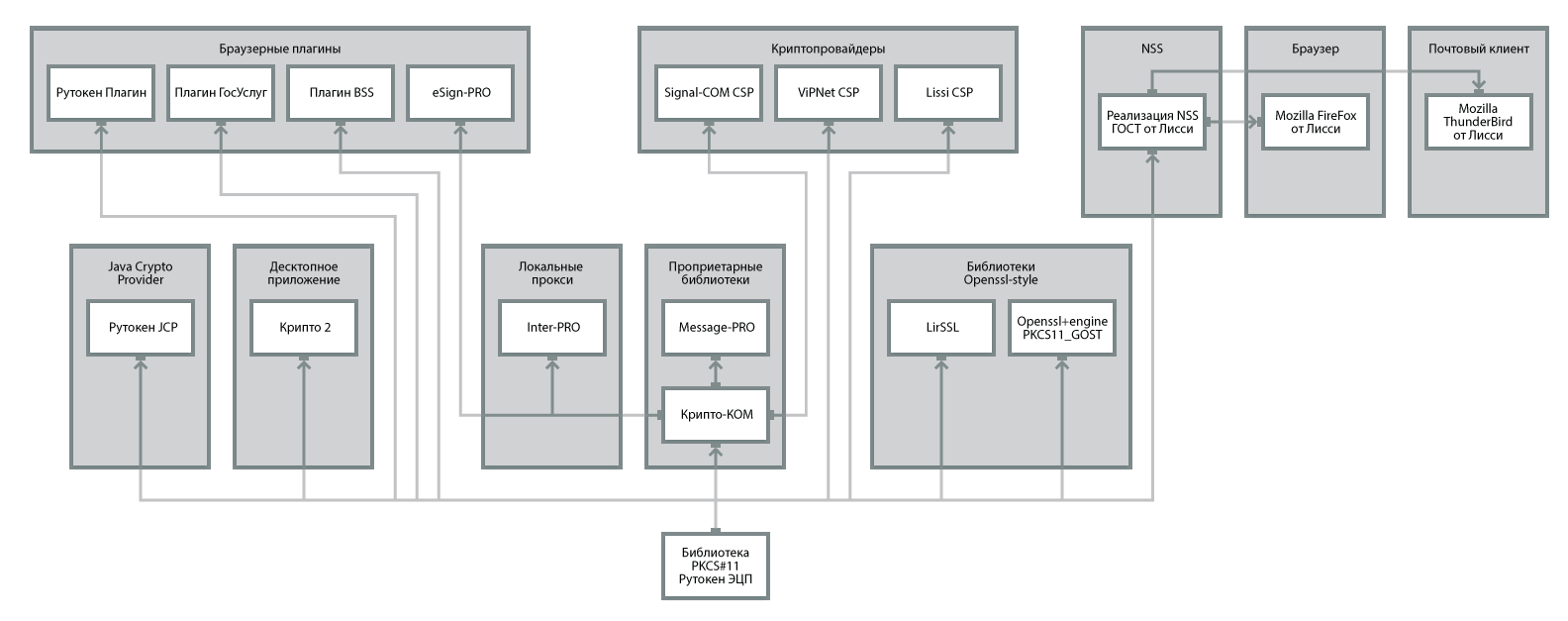
Using the library PKCS # 11 ensures software compatibility of various vendors when working with tokens. Through PKCS # 11 interface, applications written on the basis of CryptoAPI, NSS, OpenSSL can work.
An example of application compatibility is shown in the diagram. Thus, it is possible to use a suitable application in the appropriate place of the information system.

PKCS # 11 are also without the support of hardware devices with software implementation of cryptoalgorithms and storage of objects in the file system.
Examples - PKCS # 11 integrated into NSS (Mozilla), aToken project, Agave-Pro library.
The company Crypto-Pro has a library PKCS # 11, implemented on the basis of MS CryptoAPI:

There are PKCS # 11 libraries for mobile platforms. An example of such a library is the library for Rutoken EDS Bluetooth, which allows you to use your device on iOS and Android.
NSS
NSS is a Mozilla community cryptographic library. NSS is used by applications such as the Mozilla Firefox browser, the Mozilla Thunderbird email client.
Currently there are two projects on the "hotelization" of the NSS:
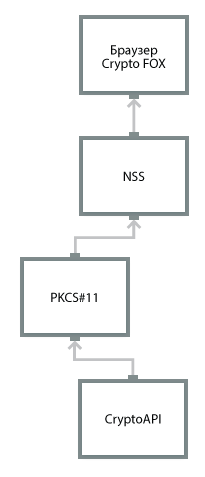
- The company Lissi periodically publishes on its site available for download the latest versions of Mozilla Firefox and Mozilla Thunderbird, reassembled with the support of Russian cryptography. In addition, there are a number of products of this company, built on the basis of the modified NSS library - the high-level NSSCryptoWrapper library, LCSignPlugin plugin, desktop application for EDS for Android SignMaker-A.
It should be noted that the NSS modified by the specialists of this company allows the use of both software PKCS # 11 tokens and hardware (Rutoken EDS, eToken GOST, JaCarta GOST, MS_KEY). - Atoken is an open source project by R-Alpha. Within the framework of the project, a software PKCS # 11-token with Russian cryptography was created and patches for a specific version of NSS and the Security Manager component were posted, allowing Russian cryptography (TLS, EDS, PKI) to be used in Mozilla products. In addition, R-Alpha offers the implementation of a software PKCS # 11-token with the support of an Agava-C certified library called Agave-Pro.
Libraries with own interface
Proprietary libraries provide their own API for embedding into applications. You can add to this list:
- Agave-C
- Crypto C
- Crypto-COM
Local proxies
The basic principle of the local proxy is to accept an unprotected connection from the application, set up a TLS tunnel with a remote server, and transfer the “application layer” between the application and the remote server through this tunnel.
In addition, some local proxies are additionally complemented with a special digital signature mechanism of specially marked WEB forms (Inter-PRO, MagPro Crypto Tunnel). There are local proxies that provide the WEB API of the digital signature for the browser (a system of HTTP requests and responses similar to the software API of the crypto library).

| Specification | - |
| Platforms | Windows family, GNU \ Linux, OS X. Based on the ACT of iOS, Android |
| Algorithms and cryptographic protocols | EDS, encryption, hash function, imitation protection, HMAC, VKO; Tls |
| PKI Integration | X.509, PKCS # 10, CMS, CRL, OCSP, TSP |
| EDS mechanisms | Signed WEB-forms when passing traffic WEB API |
| Authentication mechanisms | client authentication within TLS |
| TLS Guest Accommodation Mechanisms | Through the proxying mechanism |
| Secure Message Formats | PKCS # 7, CMS |
| Browser Integration | Through the proxying mechanism |
| Mobile platforms | iiOS, Android based on open source software sTunnel |
| Keystores | Registry, files, USB tokens |
| Interacting with USB tokens | Keys and Certificates Store Use of hardware implementation of algorithms Via PKCS # 11, PC / SC, APDU |
| Applications | Browsers WEB server RDP Mail clients and servers |
| Installation | The installer, in general, does not require system administrator rights Copy, Run Run from USB flash token |
| Examples (GOST) | MagPro Crypto Tunnel Inter-PRO VPNKey-TLS Lirtunnel CryptoPro sTunnel sTunnel |
Problems:
- proxy must be running;
- the application should work through a proxy, you need to "teach" it to it;
- non-standard ports can be used, hence the problems in the firewall
- if the application “walks” through localhost, then, for example, localhost is spelled out in the address bar of the browser - non-standard
- additional restrictions on the development of a web site - in some cases using only relative links so as not to “fly out” from the tunnel
- the proxy is configured to proxy the final group of sites; expanding the group is an update of the client config
- working through an external proxy requires additional configuration of the local proxy, and there may be problems with user authentication on the external proxy
Pros:
- the solution uses universal technology, so you can not be afraid of its obsolescence;
- the solution can be applied on a large number of platforms, including mobile platforms;
- cross-browser compatibility, support of all WEB-servers without modification;
- does not require installation;
- support for various application protocols.
Browser Plugins
In order to call the native library from the WEB-page scripts, most browsers support special extensions - ActiveX for IE and NPAPI-plugin for GH, MF, Opera, Safari, etc. Currently there is a wide range of products related to browser plug-ins on the market . Architecturally, these plug-ins can be executed in different ways. Some of them work on the basis of CryptoAPI and require additional installation of a crypto-provider, others use PKCS # 11-compatible devices as a crypto-core and do not require installation of additional SKZI on the client’s workplace. There are universal plug-ins that support both all main crypto-providers and a wide range of hardware SKZI.
Crossbrowser Plugins

| Specification | - |
| Platforms | Windows family, GNU \ Linux, OS X |
| Algorithms and cryptographic protocols | EDS, encryption, hash function, imitation protection, HMAC |
| PKI Integration | X.509, PKCS # 10, CMS, CRL, OCSP (CryptoPro EDS Browser plugin), TSP (CryptoPro Pro EDS Browser plugin) |
| EDS mechanisms | API for use in JavaScript |
| Authentication mechanisms | EDS random data |
| TLS Guest Accommodation Mechanisms | - |
| Secure Message Formats | PKCS # 7, CMS, XMLSec (CryptoPro Pro EDS Browser plugin), CADES (Crypto Pro Pro EDS Browser plugin) |
| Browser Integration | ActiveX (for IE) NPAPI |
| Mobile platforms | not supported |
| Keystores | Registry, files, USB tokens |
| Interacting with USB tokens | Keys and Certificates Store Use of hardware implementation of algorithms Through PKCS # 11, via CryptoAPI |
| Applications | Browsers |
| Installation | The installer does not require system administrator rights |
| Examples (GOST) | CryptoPro Pro EDS Browser plugin eSign-PRO CryptoPlugin Lissi Public Services Portal Plugin JC-WebClient Rutoken Plugin BSS plugin CryptoARM Browser plugin |
Problems:
- lack of TLS
- NPAPI removal from Chromium
- browsers on mobile platforms do not support plugins
- IE security settings can block plugin execution
Pros:
- cross-platform for plugins based on PKCS # 11
- cross-browser compatibility
- PKCS # 11 based plugins do not require SKZI installation
- transparent use for the user
ActiveX
Microsoft has developed two main client-side ActiveX components that translate CryptoAPI functionality into scripts and into a browser.
To generate a key and create a PKCS # 10 request, the XEnroll / CertEnroll component is used, and the CAPICOM component is used for EDS / encryption and working with certificates.

In the following articles, the remaining solutions will be considered in detail.
Source: https://habr.com/ru/post/241221/
All Articles