How vGate helps in investigating security incidents in a virtual infrastructure
Modern virtual data centers, as a rule, are well protected from outside attacks. Traditionally, firewalls, antiviruses, IPS / IDS and other components are used in virtual infrastructures (VIs), but for some reason they often forget about attacks from the inside, completely trusting the administrators of the VIs. At the same time, the specificity of the virtual infrastructure implies a greater number of privileged users compared to the physical environment, which automatically creates a separate group of incidents related to intentional (for example, copying protected information) or unintentional actions (for example, the administrator accidentally turned off the host) for the VI. Thus, in the virtual infrastructure, it is necessary to control and restrict the access of privileged users, as well as to be able to retrospectively analyze their actions to detect and investigate incidents.
In order to show what incidents are possible in the virtual infrastructure, we deployed a virtual server on the VMware platform. To protect the simulated VIs, use certified vGate R2. Its main functions are:
In addition, vGate has a number of tools that can be used to detect and investigate information security incidents. Such mechanisms include “Audit” and “Reports”. About this in more detail.
“Audit” in vGate logs security events (for example, unauthorized access to the infrastructure, creating or deleting VMs, changing VMs, etc.) and collecting them from all protected resources (ESX servers, VMware vCenter Server, vGate authorization server). Using Audit, you can filter security events (by different categories), configure the list of logged events, send security events via SNMP / SMTP protocols, and maintain an event log in a text document.
Using the "Reports", you can monitor the system and receive various reports, for example, on the most frequent information security events, access to the HMI during off-hours, attempts to unauthorized changes to the settings controlled by policies, access to VM files and control of the HI, and others.
Next, we will try to simulate the actions of the attacker and show what incidents can occur in the virtual infrastructure and how they can be identified and investigated using vGate. Our virtual stand consists of:
When trying to access the authentication server, AVI 1 receives the following message through an agent:
')
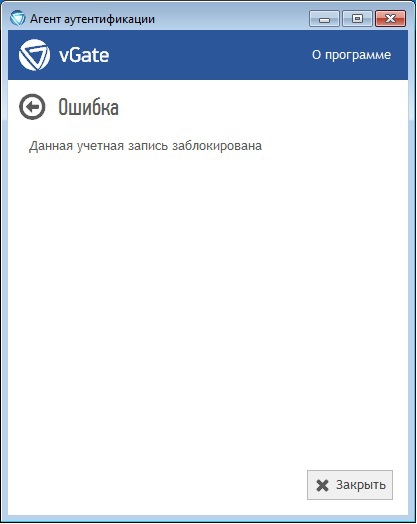
AVI asks for help from the AIB, which, applying filtering in audit events, found out that on the computer with IP 192.168.2.143 three attempts were made to enter the AVI 1 password (the number of attempts to enter a password incorrectly is configured by the vGate password policy) 1 has been blocked. AIB knows that IP 192.168.2.143 belongs to AWP AVI 2. Thus, AIB found out that AVI 2 recognized the login of AVI 1 and tried to find the password for its account.

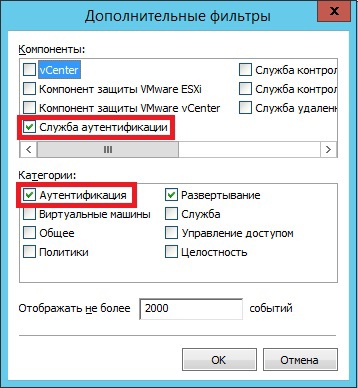


There was a leak of confidential information that was processed on the WIN7 virtual machine. The AIB filters events by categories:
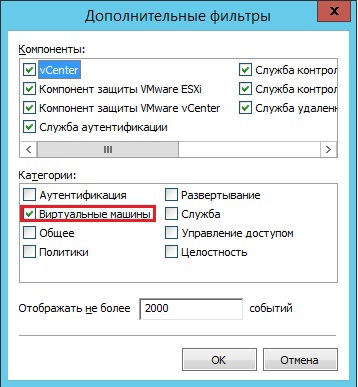
And it finds in the list an event related to the WIN7 virtual machine:


He finds out that AVI 1 has cloned this VM, which requires further proceedings to clarify the reason for AVI 1’s actions.
VM1 virtual machine does not start, but personal data is processed on this machine and integrity monitoring is set for it in accordance with the security policies in effect in the organization. The AIB filters audit events by the “text contains” parameter and enters the name of the VM1 virtual machine.

It turns out that the integrity of the vmx file has been compromised, namely, the amount of RAM in the virtual machine has been changed.
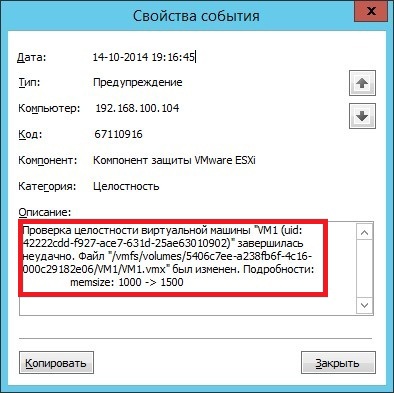
After reviewing earlier events, the AIB finds out that AVI 1 has changed the VM configuration.
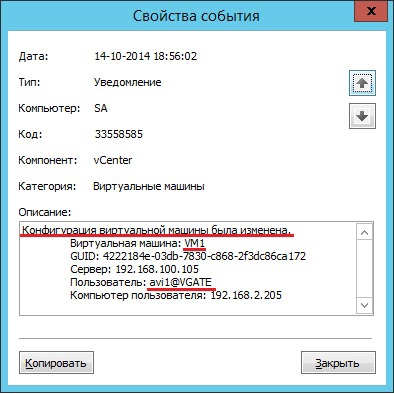
When a user tries to access a virtual machine, a user is denied due to a virtual machine being unavailable. The AIB filters audit events by the “text contains” parameter and enters the name of the virtual machine.
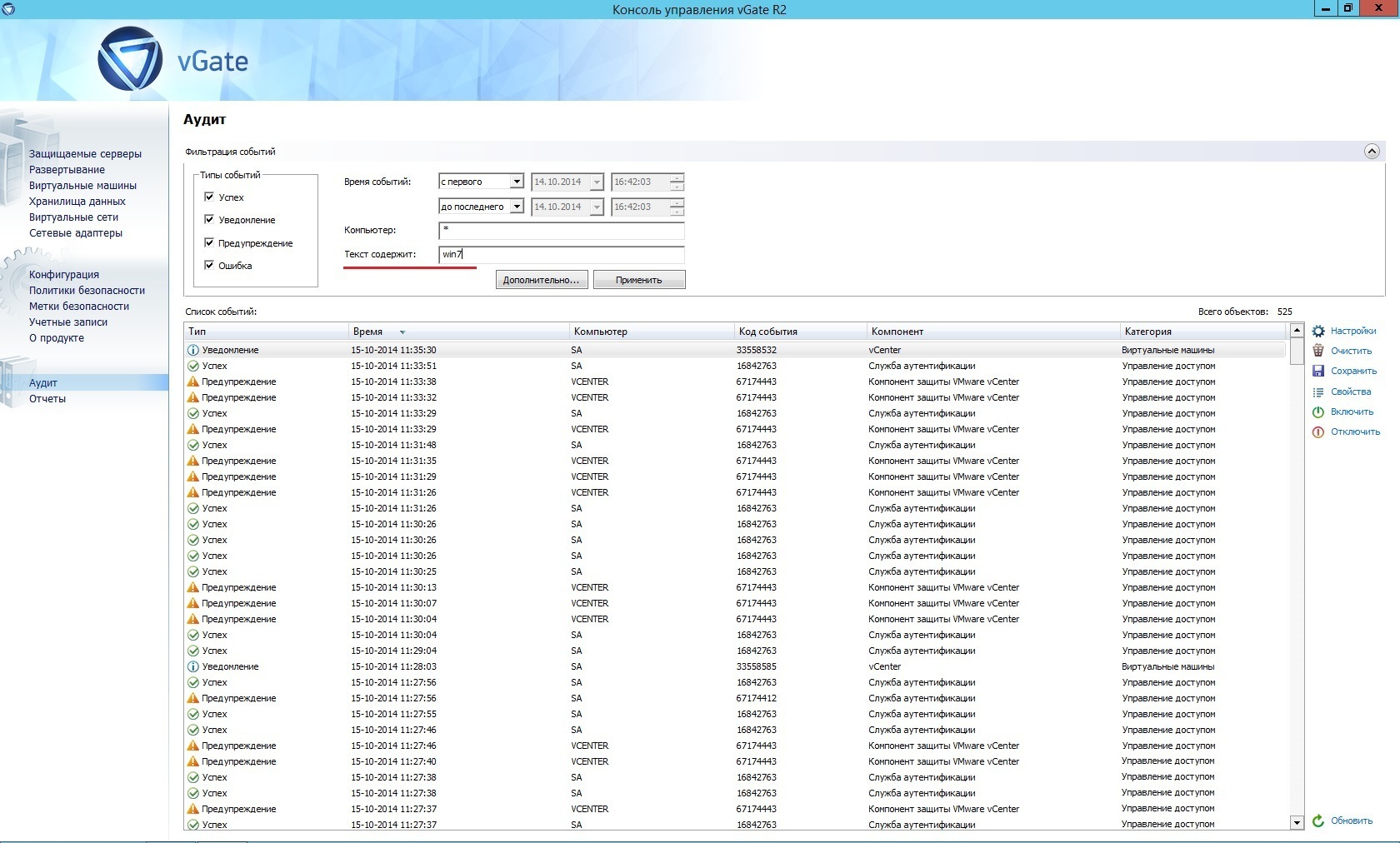
As a result of applying the AIB filter, all security events related to this virtual machine will be available. AIB finds out that AVI 1 changed the settings of the virtual machine, deleted it or performed other actions with the virtual machine, which led to its inaccessibility.
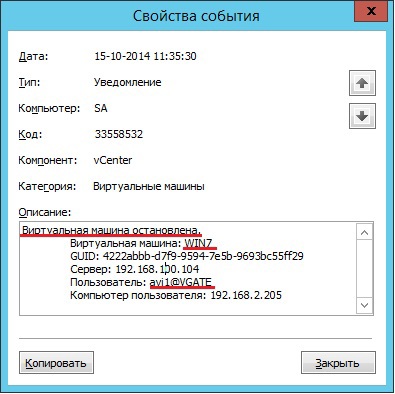
AIB during the periodic monitoring of events formed the report "The most frequent events of IB"
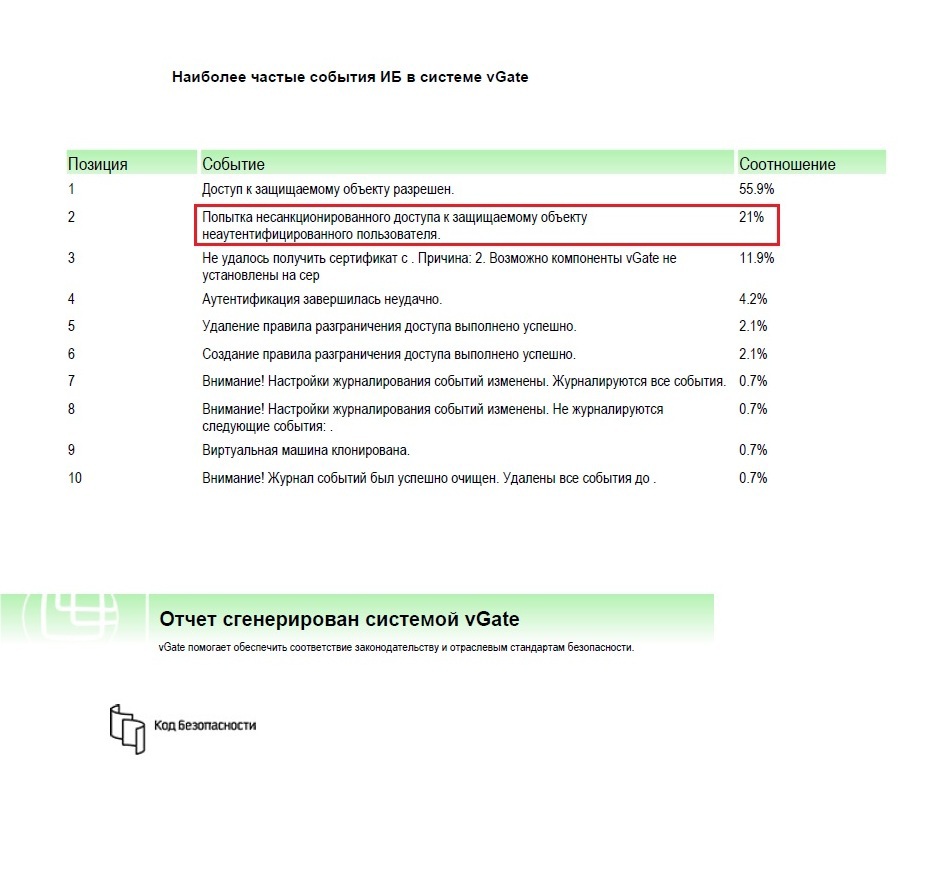
The report often includes the event “Attempt of unauthorized access to the protected object”. The AIB for further analysis filters out audit events by the type of warning events and the access control category.

As a result of applying the filter, the AIB sees recurring events in which the subject and the access object are the same, and the destination ports are different. From which it can be concluded that AVI 2 (IP 192.168.2.143) ran software for analyzing open ports.
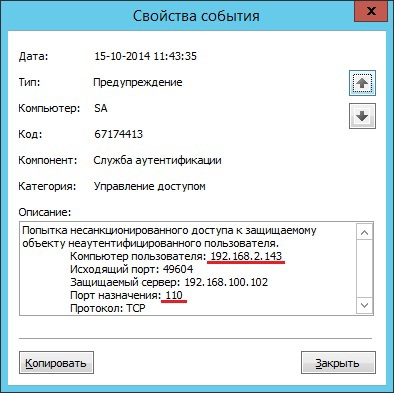

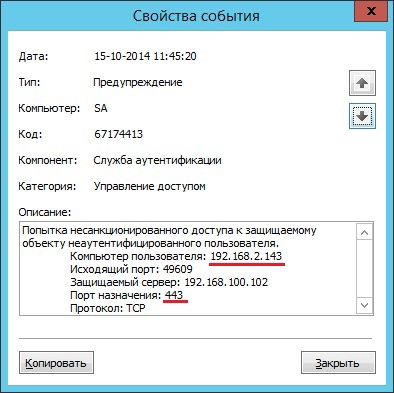
The user of VM WIN7 cannot access it, or the performance of this VM is slowed down. The user contacts AVI 1, who sees that new VMs have appeared on this host. AVI 1 refers to the AIB about what happened.
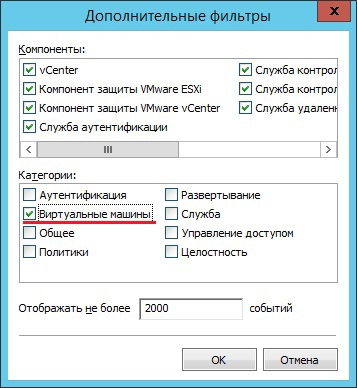


The AIB in audit events applies additional filtering by event category. By selecting the category “Virtual Machines” in the list of events associated with virtual machines, it finds the events of cloning and launching AVI 2 of several virtual machines. Accordingly, the AIB concludes that AVI 2, through the cloning and subsequent launch of a large number of virtual machines, caused the exhaustion of the computing resources of the host.
The WIN7 virtual machine has an agentless anti-virus installed (or, for example, an intrusion detection / prevention system) that protects all the virtual machines on this host, but, nevertheless, a virus infection has occurred. Having made a selection of events related to this virtual machine, AIB found out that AVI 1 turned off this machine, which is a reason to find out the reasons.
The examples considered are fairly simple, but their main goal was to show vGate incident detection functionality, which can be used to identify more complex incidents. Each of the considered incidents can be prevented by using the appropriate settings and vGate policies, as well as by setting up prompt notifications to security administrators about suspicious and malicious actions. If vGate, for example, is integrated with the SIEM system, it will add up to even more tools for detecting and investigating incidents not only in the virtual infrastructure, but also in the entire infrastructure as a whole.
Stand
In order to show what incidents are possible in the virtual infrastructure, we deployed a virtual server on the VMware platform. To protect the simulated VIs, use certified vGate R2. Its main functions are:
- control of access to various objects of VI through enhanced authentication and separation of powers between administrators of VI and IB administrators;
- protection of VMs and confidential data that is stored and processed on these machines;
- protection of VI in accordance with the requirements of regulators.
In addition, vGate has a number of tools that can be used to detect and investigate information security incidents. Such mechanisms include “Audit” and “Reports”. About this in more detail.
“Audit” in vGate logs security events (for example, unauthorized access to the infrastructure, creating or deleting VMs, changing VMs, etc.) and collecting them from all protected resources (ESX servers, VMware vCenter Server, vGate authorization server). Using Audit, you can filter security events (by different categories), configure the list of logged events, send security events via SNMP / SMTP protocols, and maintain an event log in a text document.
Using the "Reports", you can monitor the system and receive various reports, for example, on the most frequent information security events, access to the HMI during off-hours, attempts to unauthorized changes to the settings controlled by policies, access to VM files and control of the HI, and others.
Next, we will try to simulate the actions of the attacker and show what incidents can occur in the virtual infrastructure and how they can be identified and investigated using vGate. Our virtual stand consists of:
- from a server with VMware vCenter and two ESXi hosts (host number 1 and host number 2);
- vGate authorization server (deployment option when routing is performed by vGate authorization server), which also houses the information security administrator's workstation (we will call it AIB for short);
- AWS of the administrator of virtual infrastructure No. 1 (AVI 1), which has access to confidential information (on the AWS, the vGate and VMware vSphere Client authentication agent is installed); AWS of Administrator of Virtual Infrastructure No. 2 (AVI 2), which does not have access to confidential information (vGate and VMware vSphere Client authentication agent is installed on AWS).
Simulated situations
Incident number 1. Password selection
When trying to access the authentication server, AVI 1 receives the following message through an agent:
')

AVI asks for help from the AIB, which, applying filtering in audit events, found out that on the computer with IP 192.168.2.143 three attempts were made to enter the AVI 1 password (the number of attempts to enter a password incorrectly is configured by the vGate password policy) 1 has been blocked. AIB knows that IP 192.168.2.143 belongs to AWP AVI 2. Thus, AIB found out that AVI 2 recognized the login of AVI 1 and tried to find the password for its account.




Incident number 2. VM cloning
There was a leak of confidential information that was processed on the WIN7 virtual machine. The AIB filters events by categories:

And it finds in the list an event related to the WIN7 virtual machine:


He finds out that AVI 1 has cloned this VM, which requires further proceedings to clarify the reason for AVI 1’s actions.
Incident number 3. Violation of the integrity of the VM
VM1 virtual machine does not start, but personal data is processed on this machine and integrity monitoring is set for it in accordance with the security policies in effect in the organization. The AIB filters audit events by the “text contains” parameter and enters the name of the VM1 virtual machine.

It turns out that the integrity of the vmx file has been compromised, namely, the amount of RAM in the virtual machine has been changed.

After reviewing earlier events, the AIB finds out that AVI 1 has changed the VM configuration.

Incident number 4. Violation of the availability of VM
When a user tries to access a virtual machine, a user is denied due to a virtual machine being unavailable. The AIB filters audit events by the “text contains” parameter and enters the name of the virtual machine.

As a result of applying the AIB filter, all security events related to this virtual machine will be available. AIB finds out that AVI 1 changed the settings of the virtual machine, deleted it or performed other actions with the virtual machine, which led to its inaccessibility.

Incident number 5. Analysis of open ports
AIB during the periodic monitoring of events formed the report "The most frequent events of IB"

The report often includes the event “Attempt of unauthorized access to the protected object”. The AIB for further analysis filters out audit events by the type of warning events and the access control category.

As a result of applying the filter, the AIB sees recurring events in which the subject and the access object are the same, and the destination ports are different. From which it can be concluded that AVI 2 (IP 192.168.2.143) ran software for analyzing open ports.



Incident number 6. Exhaustion of resources
The user of VM WIN7 cannot access it, or the performance of this VM is slowed down. The user contacts AVI 1, who sees that new VMs have appeared on this host. AVI 1 refers to the AIB about what happened.



The AIB in audit events applies additional filtering by event category. By selecting the category “Virtual Machines” in the list of events associated with virtual machines, it finds the events of cloning and launching AVI 2 of several virtual machines. Accordingly, the AIB concludes that AVI 2, through the cloning and subsequent launch of a large number of virtual machines, caused the exhaustion of the computing resources of the host.
Incident number 7. Turn off VM
The WIN7 virtual machine has an agentless anti-virus installed (or, for example, an intrusion detection / prevention system) that protects all the virtual machines on this host, but, nevertheless, a virus infection has occurred. Having made a selection of events related to this virtual machine, AIB found out that AVI 1 turned off this machine, which is a reason to find out the reasons.
Conclusion
The examples considered are fairly simple, but their main goal was to show vGate incident detection functionality, which can be used to identify more complex incidents. Each of the considered incidents can be prevented by using the appropriate settings and vGate policies, as well as by setting up prompt notifications to security administrators about suspicious and malicious actions. If vGate, for example, is integrated with the SIEM system, it will add up to even more tools for detecting and investigating incidents not only in the virtual infrastructure, but also in the entire infrastructure as a whole.
Source: https://habr.com/ru/post/241205/
All Articles