0day detected in MS14-060 update
Microsoft has released security alert SA 3010060 , which reports a new 0day vulnerability in the OLE package manager (Packager.dll) component for Windows Vista +. An update for the Packager.dll system library was released last week as part of the monthly patch tuesday to close another 0day vulnerability (CVE-2014-4114), which we wrote about here . A vulnerability CVE-2014-6352 has been discovered in a component that has already been fixed. This vulnerability, like its predecessor, is already used by attackers for remote code execution through a specially crafted PowerPoint presentation file with an embedded OLE object.

To assist users, a FixIt solution was released, which can be downloaded from this link . In a typical attack scenario using this vulnerability, attackers send a malicious PowerPoint presentation file to the user's inbox. Next, the exploit allows you to download malware from a remote server and install it into the system. For users of EMET 5.0, you can add a special setting that will block the actions of the exploit. In addition, UAC will also display a corresponding warning about elevation of rights during the execution of the exploit.
')
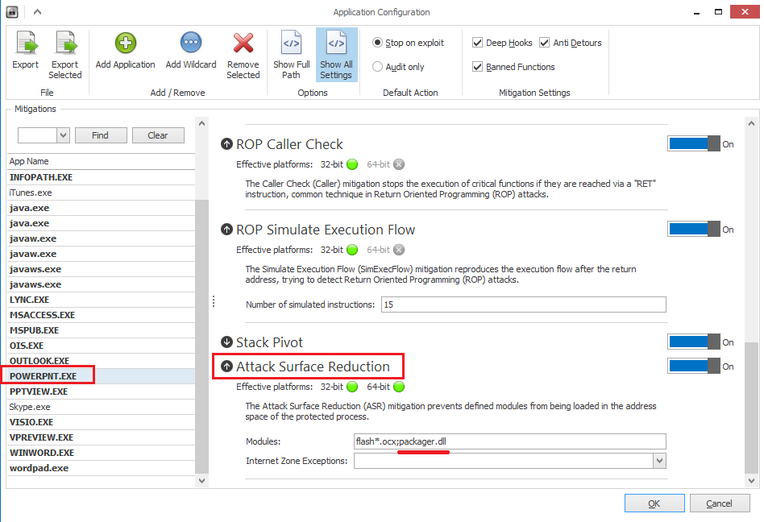
Fig. Configure EMET to block the loading of Packager.dll in the context of the PowerPoint process. Read more about ASR here .
Microsoft also recommends enabling the ASR option for the dllhost.exe process, but all other anti-exploit settings should be turned off, apparently for compatibility reasons. In automatic mode, this can be done through a special .xml file, the contents of which can be found in the Workarounds section of this link .

be secure.

To assist users, a FixIt solution was released, which can be downloaded from this link . In a typical attack scenario using this vulnerability, attackers send a malicious PowerPoint presentation file to the user's inbox. Next, the exploit allows you to download malware from a remote server and install it into the system. For users of EMET 5.0, you can add a special setting that will block the actions of the exploit. In addition, UAC will also display a corresponding warning about elevation of rights during the execution of the exploit.
')

Fig. Configure EMET to block the loading of Packager.dll in the context of the PowerPoint process. Read more about ASR here .
Microsoft also recommends enabling the ASR option for the dllhost.exe process, but all other anti-exploit settings should be turned off, apparently for compatibility reasons. In automatic mode, this can be done through a special .xml file, the contents of which can be found in the Workarounds section of this link .

be secure.
Source: https://habr.com/ru/post/241195/
All Articles