China carries out MiTM-attack on iCloud users
The so-called “great Chinese firewall” has mastered working with iCloud and now intercepts traffic from Chinese Apple users to iCloud servers.
The researchers from the organization Greatfire.org laid out evidence of MiTM-attacks, in which the authorities receive confidential user information: iMessage messages, contacts, photos, and so on.
The attack is carried out using a fake digital certificate: if the user is inattentive and ignores the warning, then his connection with iCloud will be encrypted with the keys of the Chinese government.
')
Warning about the wrong certificate when trying to connect to https://www.icloud.com
ICloud operation via Chinese MiTM proxy

For now, a fake certificate is offered only when trying to connect to the IP address 23.59.94.46. That is, not all Chinese users suffer, because iCloud DNS can return other IP addresses.
Wirecapture with MITM: www.cloudshark.org/captures/03a6b0593436
Self-signed certificate used in attack: http://www.mediafire.com/download/ampbnqncc277krv/fakeicloudcert.zip
Connection log: http://pastebin.com/tN7kbDV3
Traceroute: http://pastebin.com/8Y6ZwfzG
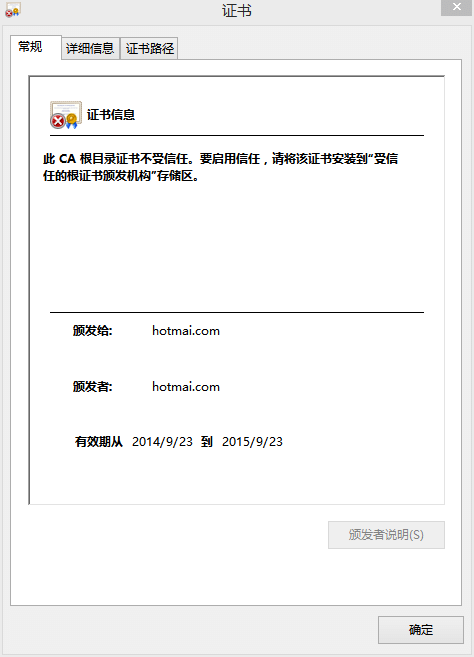
Hotmail mitm

Wirecap: https://www.cloudshark.org/captures/6011389a8ea3
TCP Traceroute: https://twitter.com/siyanmao/status/518963824481681408
The researchers from the organization Greatfire.org laid out evidence of MiTM-attacks, in which the authorities receive confidential user information: iMessage messages, contacts, photos, and so on.
The attack is carried out using a fake digital certificate: if the user is inattentive and ignores the warning, then his connection with iCloud will be encrypted with the keys of the Chinese government.
')
Warning about the wrong certificate when trying to connect to https://www.icloud.com

ICloud operation via Chinese MiTM proxy

For now, a fake certificate is offered only when trying to connect to the IP address 23.59.94.46. That is, not all Chinese users suffer, because iCloud DNS can return other IP addresses.
Wirecapture with MITM: www.cloudshark.org/captures/03a6b0593436
Self-signed certificate used in attack: http://www.mediafire.com/download/ampbnqncc277krv/fakeicloudcert.zip
Connection log: http://pastebin.com/tN7kbDV3
Traceroute: http://pastebin.com/8Y6ZwfzG
Hotmail mitm

Wirecap: https://www.cloudshark.org/captures/6011389a8ea3
TCP Traceroute: https://twitter.com/siyanmao/status/518963824481681408
Source: https://habr.com/ru/post/240993/
All Articles