Expel evil spirits from the ReadyNAS

Habré already has several articles on the security of various devices from the so-called “Internet-things” sphere: home routers, smart TVs, NAS devices, etc.
This article tells about the features of NAS models ReadyNAS. An article about how I managed to drive a stranger out of a NAS device, which was very well established there. Looking ahead, I would say that the information gathered was not enough to say who the stranger was: a hacker with a human face and self-interest or an insensitive virus. Therefore, in the title of this article appears the impersonal word "evil".
One day, my friend called me and asked: “look what’s wrong with this piece of iron? well, I keep films on it ... well, you understand what I mean! ”And then the descriptions of the symptoms followed. It was an ordinary working evening, and my head was already thinking not super. Of course, from the telephone conversation, I really did not understand. But I decided not to conduct interrogations by phone and arrive at the scene, personally see what and how. I asked to disconnect the device from the Internet before my arrival.
')
When I arrived at his home, I still did not understand what kind of symptoms he described to me. But just in case, I decided to look a piece of iron. It turned out to be ReadyNAS. The device looked quite normal in appearance; there were no special brakes or inappropriate behavior. No unidentified users were found on the device list. After that, I decided to still look at the logs. So, to clear your conscience. I had no reason to worry. So my motivation was more likely to reassure my friend. Like, I was carrying with a piece of iron, everything is fine in the logs, I don’t see any brakes, a false alarm. Leaving immediately, without depicting even an attempt to really understand it was ugly. But the logs were not so soothing. And I realized that the evening will stand out with the struggle.
And what are the logs?
The line “Enabled root SSH access” was found in the logs

Search in Google issued a page with a description of the utility . Judging by the description, the utility was designed to provide root access to the device via SSH. And the root password should be the same as the user admin. The admin user was used by us to access the device via the web interface. Fellow swore that he did not put this plugin.
I will make a small digression. ReadyNAS devices are divided into those where the ReadyOS OS and RAIDiator are installed.
In the case of ReadyOS, the included SSH server can be seen among other services through the web interface.
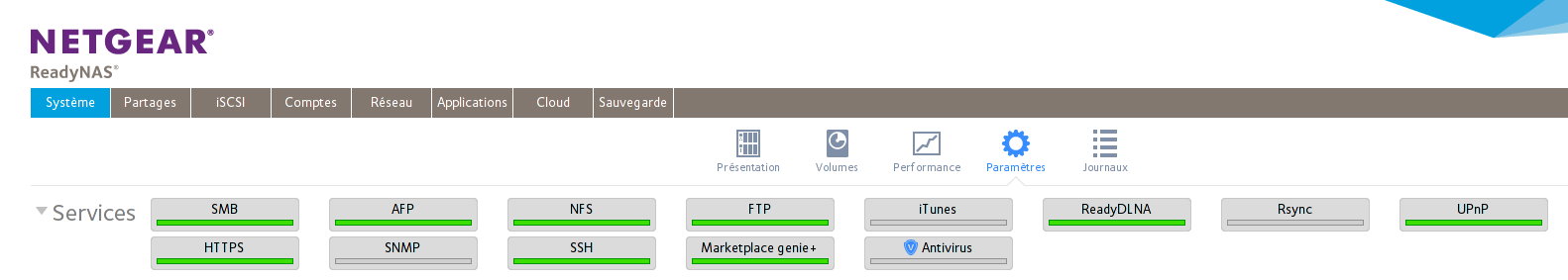
But with RAIDiator, the SSH server is available after installing the enable root plugin. After this procedure, there is no enable root in the plug-in lists, and no information about the enabled SSH server appears in the list of services:
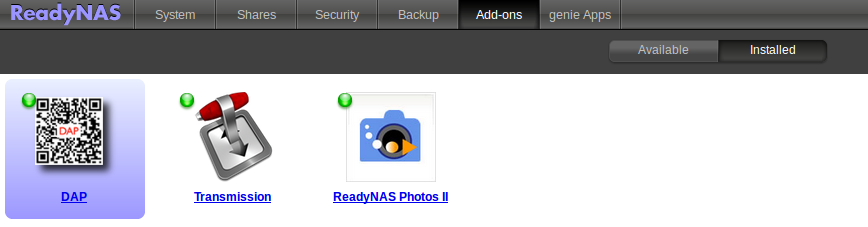

So On systems running RAIDiator, it can be revealed that the uninvited guest in the device is somewhat more problematic.
Having executed the trite telnet 192.168.0.1 22, I made sure that the SSH server really works. But it failed to log in as root - the intended admin password did not fit. Authorization from admin led to reset the session. As it turned out, besides the root user, the rest of the device in / etc / passwd was written / bin / false
It can be assumed that the attacker has changed the password. I thought, “Great! The rogue has no physical access to the device, but there is root access. And I have physical access ... but what's the use? After all, there is no root access. And how to solve the problem? ”The first thing that comes to mind is resetting the device to factory settings. But the last thing I wanted to do was this: I had to merge terabytes of films somewhere. The procedure is not fast. And I didn’t really want to come the second time. And I began to look for alternatives.
Decision
Further description of the solution takes very little text, but it took a lot of time and nerves. The first thing I tried was to upload this enable root plugin on the device in the hope that it would reset the root password. I hoped that the plugin simply overwrites / etc / shadow for root with the default password. The plugin was successfully filled, the device rebooted. But the problem is not solved.
The next step I decided to try to update the firmware of the device, if it is not the latest version. Suddenly it will overwrite the system files and the problem will be miraculously solved?

The firmware was not the latest version, an update was available. I pressed the treasured button. The system warned that the procedure will take time and I will be notified of the result at the end. However, the result turned out to be negative: a mismatch of checksums. I began to feel that I could hardly go to bed early ... And even if I could, in a dream, I would be tormented by thoughts like: “why should I throw this rascal out of the system?” And you can forget about a good dream anyway. My head completely refused to work, and I didn’t find anything better than just poking the “Update” button, in the hope that the device would stop being naughty and update ... Did I believe that it would end well? Hardly. I did not know what to do anymore, there was not so much left of the former fighting spirit. But by some miracle, the system has actually been updated since the 5th and went to reboot. It was a real miracle! After that we successfully logged in from root with password from admin.
Once on the device, I ran through the file system and logs, hoping to find traces of the presence of a stranger. But I could not find them: the last team showed information only about my own visit. A file with a history of commands ( .bash_history ) was completely absent. And in the file /var/log/auth.log there was also information only about my visit. So it was not possible to find out when the device was compromised, from which IP address and which commands were executed. The only evidence was the date and time of the initial installation of the enable SSH root plugin in the web interface logs. Yes, we can say that some unnoticed code remained in the device, which works with the privileges of the root. But the decision to reinstall the system is not for me, but for my friend. But he decided not to do it yet. In addition, as it turned out after the interrogation with predilection, it was the reboot of the device that was straining my friend while watching a movie. What the attacker needed to do was to enable the SSH root enable plug-in. The time of a sudden reboot coincided with the time found in the logs of the web interface regarding the installation of the SSH root enable . So, perhaps, we really responded quickly and the attacker did not have time to mess things up.
Conclusion
I advise many of my friends and acquaintances not to give out “white” IP to my devices from the “Internet of Things”. You can "score" (or unwilling) to change the factory passwords on the device. But by hiding them from public access via the Internet, you can save yourself from such unpleasant stories. While changing the factory password is not a fact that will solve the problem. I tell them: “put them behind the router. Especially since you do not have to pay for another static address. Need access remotely? Configure the router port forwarding correctly. According to the port knoking technology ( article one , article two ) ”Tortured to explain in detail how to do this, wrote an article Example of a secure home LAN configuration . I hope some readers will also be helpful.
And those few comrades for whom it is problematic to tweak the article due to the small knowledge in the field of network technologies ... I just ask them to fork out on the Mikrotik router and come with pre-configured settings in which I can only change the settings for the interface where the cable from the provider is plugged in
UPD: Mikrotik can be useful in terms of analyzing the traffic from the studied device to the network. Mikrotik allows you to intercept and analyze traffic very conveniently: in the config, the address of the computer is set, where the log will be analyzed, the traffic collection rule. Next, we start Wireshark on the computer, configure it and see the traffic in real time. More on this here . Those. traffic can be analyzed without taking the priests from his chair, there is no need to collect test networks.
Although, on the device itself one could try to sniff traffic through tcpdump (if it is there, it will be necessary to take a look).
Source: https://habr.com/ru/post/240763/
All Articles