New 0day vulnerability in Windows is exploited in-the-wild
Specialists of iSIGHT Partners today announced a new vulnerability CVE-2014-4114 in Windows 7+, which was discovered by them a month earlier. According to company analysts, the vulnerability was exploited by a cybercrime group whose traces lead to Russia. Vulnerability can be exploited using a specially crafted MS PowerPoint document that contains OLE embeddable objects. The component of the Windows subsystem, which is responsible for processing embedded objects, contains a vulnerability that allows to download an .INF file from a remote server and install it in the system.

The exploit is a PowerPoint document that contains two objects, oleObject1.bin and oleObject2.bin. Each of these files contains a link to an external IP address. One of them is used to download the .INF file that will be used to install the malware, and the second contains a link to the malicious program itself — the BlackEnergy Lite dropper (Win32 / Rootkit.BlackEnergy). This dropper will be installed into the system using the downloaded .INF file. We recently wrote about a malicious campaign to distribute BlackEnergy Lite of one of the hacker groups, whose roots also go to Russia. In both cases, the targets are the NATO countries.
')
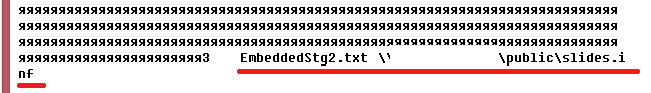
Fig. Link to the .INF file in oleObject2.bin.
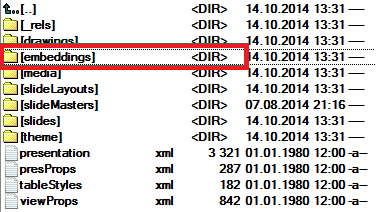
Fig. Directory with OLE objects in a malicious PowerPoint document.
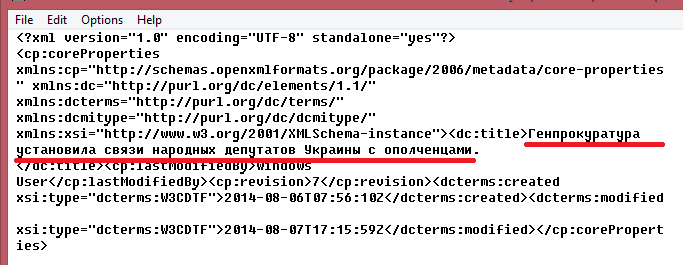
Fig. The presentation topic contains a reference to the conflict in Ukraine.
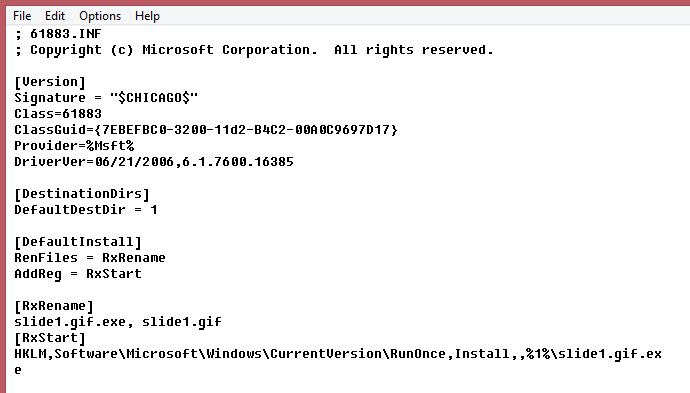
Fig. The format of the downloaded .INF file that is used to install the malware. The vulnerability allows both of these files to be downloaded from the attacker's server.
Vulnerable are up-to-date versions of Windows 7, the latest Windows 8 & 8.1, and also RT. Microsoft promises to close this vulnerability today as part of the monthly patch tuesday.

The exploit is a PowerPoint document that contains two objects, oleObject1.bin and oleObject2.bin. Each of these files contains a link to an external IP address. One of them is used to download the .INF file that will be used to install the malware, and the second contains a link to the malicious program itself — the BlackEnergy Lite dropper (Win32 / Rootkit.BlackEnergy). This dropper will be installed into the system using the downloaded .INF file. We recently wrote about a malicious campaign to distribute BlackEnergy Lite of one of the hacker groups, whose roots also go to Russia. In both cases, the targets are the NATO countries.
')

Fig. Link to the .INF file in oleObject2.bin.

Fig. Directory with OLE objects in a malicious PowerPoint document.

Fig. The presentation topic contains a reference to the conflict in Ukraine.

Fig. The format of the downloaded .INF file that is used to install the malware. The vulnerability allows both of these files to be downloaded from the attacker's server.
Vulnerable are up-to-date versions of Windows 7, the latest Windows 8 & 8.1, and also RT. Microsoft promises to close this vulnerability today as part of the monthly patch tuesday.
Source: https://habr.com/ru/post/240345/
All Articles