Artificial intelligence, import substitution and other features of application security

The security of Russian information systems falls every year: in 2014, 77% of the critical applications of large companies and state-owned enterprises contained dangerous vulnerabilities. The situation of import substitution further complicates the situation: it is necessary to build systems from "raw" domestic software. To respond to these security challenges, new-generation security solutions are needed, combining a serious scientific approach and a high degree of automation for early detection of threats. These and other observations were shared with journalists by experts from Positive Technologies at a press conference on application security.
Despite the 15-year experience in the information security market, the company rarely conducts such public presentations for the media. One of the reasons for the "disclosure" was a recent IDC study, according to which Positive Technologies took 3rd place in the market of security software in Russia. After the publication of this report, it became clear that for some journalists, “security software” is synonymous with “antivirus” because they are much less familiar with other security technologies - including security analysis systems, compliance monitoring, code analyzers, application protection systems.
')
Experts decided to tell journalists about these technologies. Moreover, another reason has emerged: the company Positive Technologies has recently released a new product line to protect applications in various industries, including Internet banking and ERP systems, public services portals and telecoms web services. It is possible that these developments will seriously change the information security market, both Russian and global.
Began, however, from afar. The first speaker was Boris Simis, deputy general director of PT for business development. He spoke about the history of the company, which set the task to collect the best hackers and the largest vulnerability database for analyzing the security of large companies. “Our guys can hack everything that moves! The main thing is to channel this energy into a peaceful course, ”said Boris.

Currently, the main offices of researchers and developers of "Positive" are located in Moscow and St. Petersburg, and the regional sales and support network covers the United States, Great Britain, Europe, India, South Korea, North Africa and the countries of the Persian Gulf.
At the same time, according to the observations of Boris Simis, the development of information security business abroad is more active - thanks to the good awareness of customers: they already know what threats exist and what remedies exist, and in fact speak the same language with software manufacturers. In Russia, the idea of information security among management of enterprises is much worse, protective products are often implemented formally, without an understanding of the situation.
The topic of awareness was continued in her report by the head of the analytics department at the company, Evgenia Poseluevskaya, who said that now such a term appeared - “sellers of fear”. That is what some information security analysts call them, accusing them of artificially causing panic. However, Positive Technologies is different in that it collects its data in the course of real penetration tests. And with regard to real vulnerabilities, the situation in 2014 has deteriorated in a completely natural way - companies are more actively surfing the Internet and using more applications, but they are not in a hurry to investigate the security of these applications. Here's what the top vulnerabilities look like this year:

A full study of vulnerabilities in 2014, the data of which were presented at a press conference, will be published a little later; 2013 studies can be found on the company's website . Evgenia Poseluevskaya also presented the vulnerability statistics of popular open source systems. There is a myth that the fact that using the open source model makes products “safer,” but in practice this is not always the case.
The speech of Sergey Gordeychik, deputy general director of Positive Technologies for the development of technologies, consisted of two parts. In the first part, Sergey explained why modern application protection tools cannot cope with new threats. And in the second - about what import substitution in the Russian IT industry is from the point of view of security.
According to the expert, it will not be possible to replace the hardware base and system software for a long time, so they become “untrusted products”, which may contain bookmarks of a foreign manufacturer. And the replacement of high-level software will occur with the help of domestic products created in a hurry, have not passed sufficient testing and often use third-party code. As a result, a high-risk situation is created, or the “H6 offender model” (when the offender is already in the system, but has not yet begun any active actions).
This situation will require modern approaches to security. Sergey Gordeychik presented the following trends, the development of which can change the AppSec market:
- code security control at all stages, by automating secure development (SSDL);
- combining approaches, in particular a combination of various code analysis methods;
- automating the verification of vulnerabilities, for example, by generating exploits - special requests that show exactly how this vulnerability is “turned on”;
- behavioral analysis and self-study, that is, the creation of a model of the "correct" system operation, followed by an analysis of deviations;
- intellectual processing of threats, including such a grouping and visualization of events, which will allow IB experts to receive the most important messages (for example, a chain of attacks) instead of a complete list of thousands of positives;
- closing gaps before correcting the code using virtual patching at the firewall level;
- integration of protection tools into a common ecosystem, including the interaction of the firewall with code analyzers, antivirus, DLP systems and other protection tools.

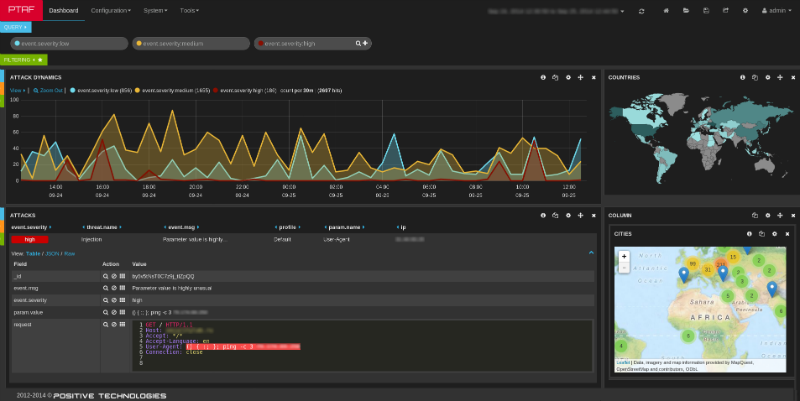
Speaking then, Denis Baranov, director of application security at the company's research center, spoke about the practical implementation of the above protection principles in two new products. The PT Application Inspector system, whose abbreviation (AI) does not coincide with the abbreviation of “artificial intelligence,” combines static (SAST), dynamic (DAST) and interactive (IAST) methods for analyzing application security in its work. And the result of the analyzer are the exploits that show developers exactly how to fix the code.
The same exploits allow you to eliminate the threat before the code is fixed: they are transferred to another company product - the PT Application Firewall firewall, which uses them for virtual patching. In addition, PT AF uses behavioral analysis of traffic, which allows to detect new attacks for which there are no signatures yet. Denis demonstrated how this firewall even detected a ShellShock attack in its basic configuration.
As the last speech at the press conference, they showed a video-feedback from the client: the leading specialist of the information security department of MegaFon OJSC Sergey Khimanych spoke about using the Positive Technologies developments to protect the web services of one of the largest Russian telecom operators.
“We studied the products of various companies, including leaders of the foreign market, but preferred the Russian solution PT Application Firewall,” a MegaFon representative said. “With this system, we can track and block attacks on our applications in real time, maintaining a high level of security for millions of subscribers.”
During the session of questions and answers, the further interest of the company, as well as the ways in which the company attracts hackers to the “bright side” aroused the greatest interest of journalists. Boris Simis and Sergey Gordeychik believe that the main thing in this matter is that the sooner the better. They told, in particular, about the Positive Education program , thanks to which students of 50 leading Russian universities can use the company's training materials when studying practical security.
On the way to the banquet, the company's experts arranged a tour of their office for journalists. There was found a hacked ATM, and a supercomputer for the selection of encryption keys, and many other amazing things. Want to see? - come to the next press conference "Positive"!

Source: https://habr.com/ru/post/240307/
All Articles