Hacking using search, inattention and my accomplice GitHub

Introduction
One fine, bright morning, being shaken by the fact that the temperature outside the window seemed to be 5 degrees more than usual, I felt an influx of unprecedented illumination and the idea sneaked into my brain - “but those offerings and accounts that are sold on the “black market” - they are stolen by all sorts of phishing sites and steelers, and as far as I know the steelers, all logs should be stored on a web host on the Internet. ”
From this moment there was no time to delay - it was necessary to test. I ran headlong into the computer, convulsively driving in the address line "google.com" and first entered the search query "stealer filetype: txt". What I saw did not surprise me as much - among the search requests I saw the expected logs of one of the popular steelers.
View screenshot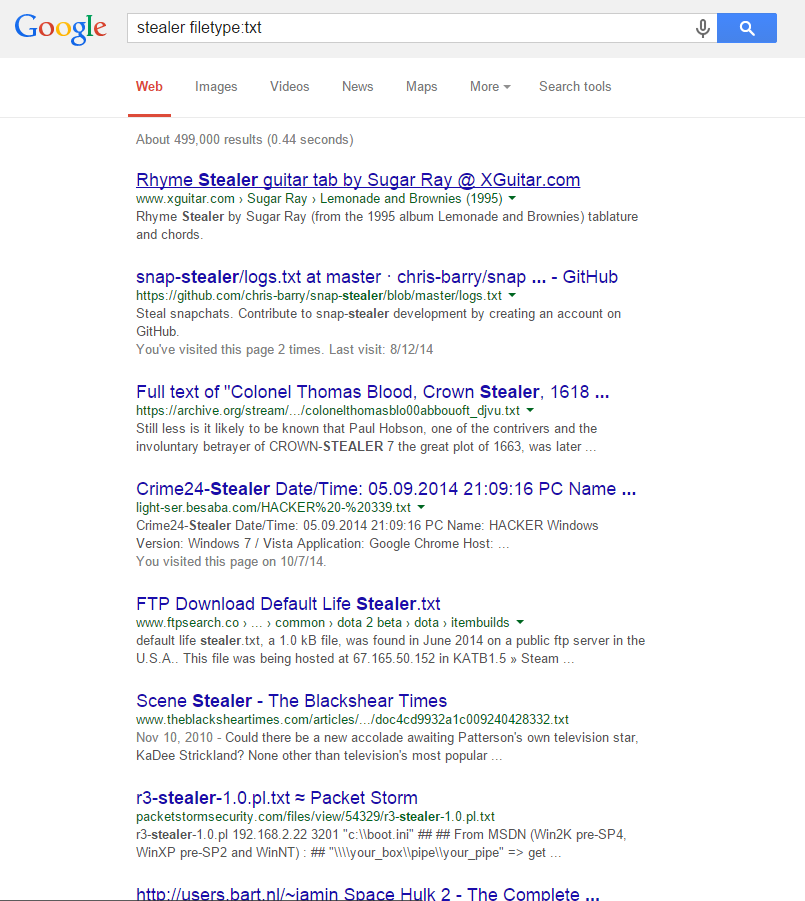

Chapter 1. Why do I need to use robots.txt, tags nofollow and put stubs
After that, I could not be stopped. I, like the wolf, who sensed the blood of his victim, continued to search, but with requests that were more oriented to the specific names of the styler:
View screenshot # 1

View screenshot # 2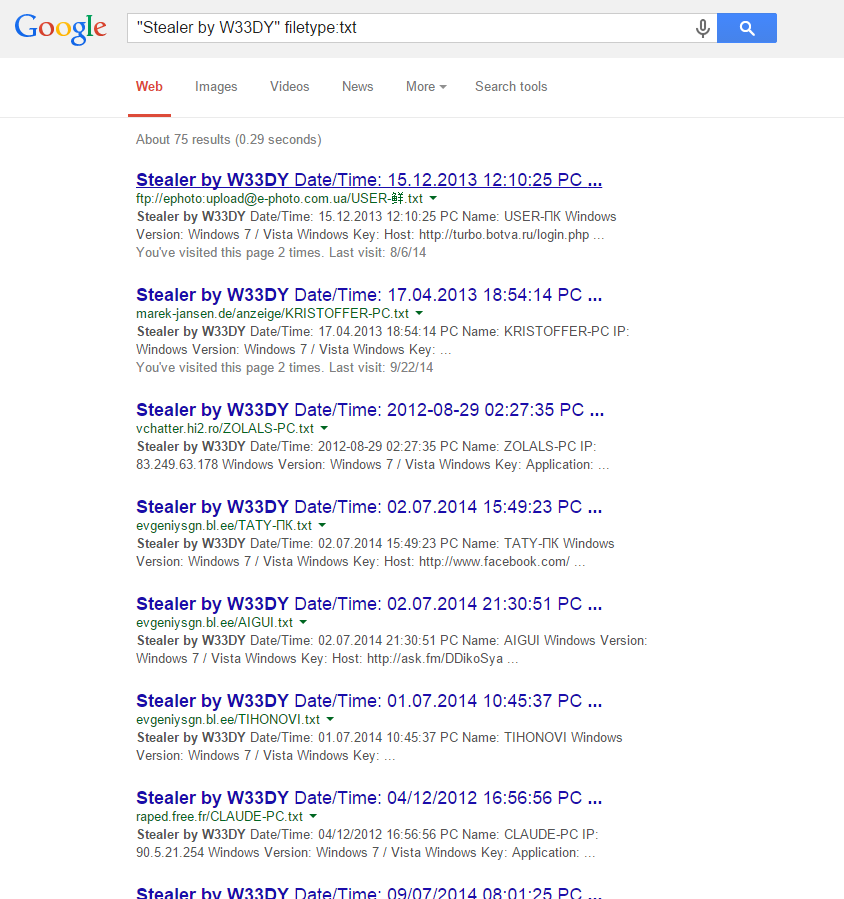

And then it dawned on me again - “after all, apart from logs with accounts, unsuccessful users who got into the“ thief program ”, you can find something more serious, such as configs,” and I went to GitHub.
Chapter 2. Why do I need to block files with configs through .gitignore
Speaking openly, the opportunity to do what I did and see what I saw because of the inattention or laziness of some users who prefer to use GitHub instead of alternative services that allow you to create private repositories ( gitlab , bitbucket ).
Take, for example, the mask of the automatically generated MYSQL host of one popular hosting and we get, again, the expected result:
View screenshot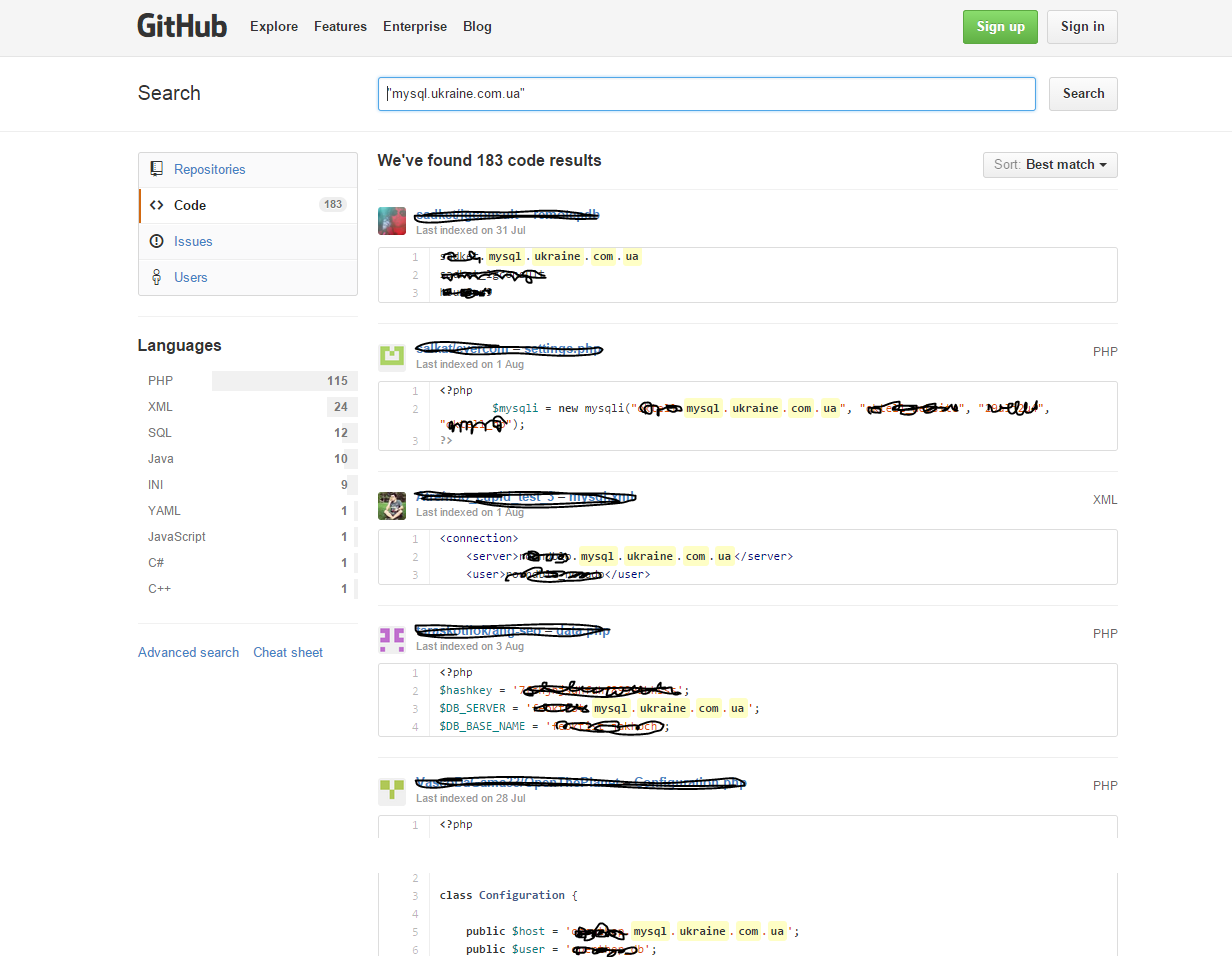

Then you do not need to have a lot of imagination to understand what to do with all this.
Conclusion
Please use the .gitignore file and do not deploy your configs.
')
Source: https://habr.com/ru/post/239567/
All Articles