Cloudflare has enabled free SSL for all sites.
This happened on September 29, but the news passed unnoticed by Habr.
As it is written in the company's blog , “just yesterday there were 2 million sites on the Internet that support SSL. Today we will double this number. ”

What is offered in brief: free wildcard certificates, SPDY support, the ability to encrypt traffic also between cloudflare and your server. Interested please under the cat.
So, the new option from Cloudflare is called Universal SSL. It involves issuing a certificate that is valid for both the root domain and all sub-domains of the first level. Certificates are issued by GlobalSign and Comodo.
(Let me remind you, if someone does not know that Cloudflare is one of the content delivery network (CDN), popular due to the availability of a free data plan).
The choice is now offered 4 schemes of the website: without encryption for the entire length of the request and 3 new options:
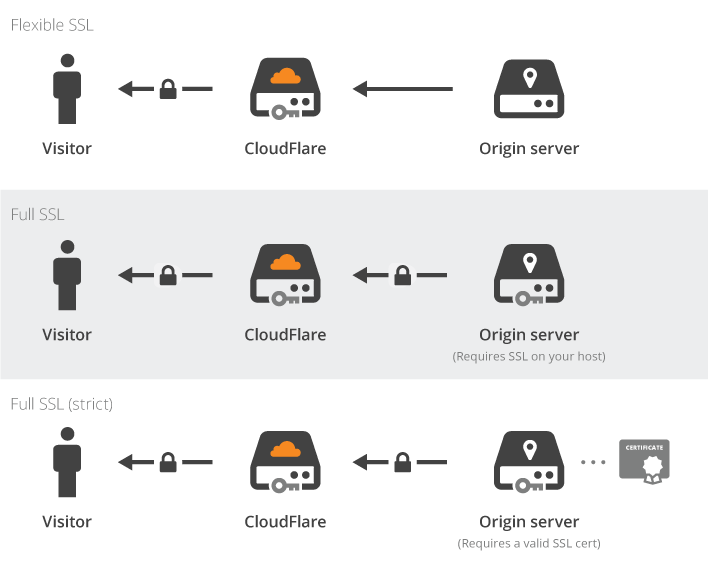
The first of them does not require any changes on the server side, while the traffic is transmitted between proxy servers and your resource in the clear.
The Full SSL option allows the use of any self-signed certificate, which is not much more reliable than the first scheme and protects traffic only from passive listening. Therefore, the third option is called the recommended option, requiring the server to have a valid certificate from a recognized CA.
In the future, it is supposed to use the own Cloudflare CA, which allows to protect the channel between the server and the proxy (in this case, Cloudflare CA certificates will not be recognized in browsers, the scheme is planned exclusively for business purposes). In addition, in the future we plan to introduce certificate pinning support.
With all the advantages listed above, Universal SSL technology has a number of differences from using SSL on Cloudflare paid plans. This at the same time allows the company to maintain its business model and solve a number of restrictions related to the massiveness of SSL solutions and the corresponding increase in the load on the proxy servers:
')
Using ECDSA creates a noticeably less server load than using “traditional” RSA algorithms. SNI technology, in turn, allows you to host more than 2 million network-managed sites on a limited number of Cloudflare IP addresses. At the same time, the host name is transmitted as part of TLS negotiation (and not after the establishment of a closed channel, as in the traditional scheme requiring a dedicated IP or port), which allows the proxy server to immediately select the required certificate and establish a connection with the required resource.
Unfortunately, these technologies are not supported by a number of older operating systems and browsers. Among them, the strongest positions are in IE / WinXP (including earlier OS), as well as Android up to version Ice Cream Sandwich. If it is necessary to maintain the maximum number of devices / OSes, it is proposed to use paid rates, including more complete cipher suite's (which is logical, you have to pay for the additional load on the servers).
The full list of supported clients for Universal SSL is as follows:
However, any version of Internet Explorer on Windows XP does not support SNI.
Read more: cloudflare blog , origin security
Despite the above disadvantages, the technology looks quite interesting (considering the cost). Many sites that have not yet used HTTPS were given the opportunity to correct this “omission” :) What do you think?
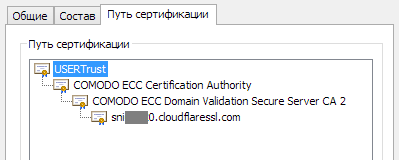
UPD: In the user's browser, server certificates look like this:
As it is written in the company's blog , “just yesterday there were 2 million sites on the Internet that support SSL. Today we will double this number. ”

What is offered in brief: free wildcard certificates, SPDY support, the ability to encrypt traffic also between cloudflare and your server. Interested please under the cat.
So, the new option from Cloudflare is called Universal SSL. It involves issuing a certificate that is valid for both the root domain and all sub-domains of the first level. Certificates are issued by GlobalSign and Comodo.
(Let me remind you, if someone does not know that Cloudflare is one of the content delivery network (CDN), popular due to the availability of a free data plan).
The choice is now offered 4 schemes of the website: without encryption for the entire length of the request and 3 new options:

The first of them does not require any changes on the server side, while the traffic is transmitted between proxy servers and your resource in the clear.
The Full SSL option allows the use of any self-signed certificate, which is not much more reliable than the first scheme and protects traffic only from passive listening. Therefore, the third option is called the recommended option, requiring the server to have a valid certificate from a recognized CA.
In the future, it is supposed to use the own Cloudflare CA, which allows to protect the channel between the server and the proxy (in this case, Cloudflare CA certificates will not be recognized in browsers, the scheme is planned exclusively for business purposes). In addition, in the future we plan to introduce certificate pinning support.
With all the advantages listed above, Universal SSL technology has a number of differences from using SSL on Cloudflare paid plans. This at the same time allows the company to maintain its business model and solve a number of restrictions related to the massiveness of SSL solutions and the corresponding increase in the load on the proxy servers:
- Only ECDSA cipher suite is supported
- SNI ( Server Name Indication ) is used
')
Using ECDSA creates a noticeably less server load than using “traditional” RSA algorithms. SNI technology, in turn, allows you to host more than 2 million network-managed sites on a limited number of Cloudflare IP addresses. At the same time, the host name is transmitted as part of TLS negotiation (and not after the establishment of a closed channel, as in the traditional scheme requiring a dedicated IP or port), which allows the proxy server to immediately select the required certificate and establish a connection with the required resource.
Unfortunately, these technologies are not supported by a number of older operating systems and browsers. Among them, the strongest positions are in IE / WinXP (including earlier OS), as well as Android up to version Ice Cream Sandwich. If it is necessary to maintain the maximum number of devices / OSes, it is proposed to use paid rates, including more complete cipher suite's (which is logical, you have to pay for the additional load on the servers).
The full list of supported clients for Universal SSL is as follows:
Desktop Browsers
- Internet Explorer 7 and later
- Firefox 2
- Opera 8 with TLS 1.1 enabled
- Google Chrome:
- Windows XP: Chrome 6 and later
- Vista and beyond - full support
- OS X since 10.5.7: Chrome 5.0.342.0 and later
- Safari 2.1 and later (starting with OS X 10.5.6 or Windows Vista).
However, any version of Internet Explorer on Windows XP does not support SNI.
Mobile Browsers
- Mobile Safari for iOS 4.0+
- Android 3.0 (Honeycomb) +
- Windows Phone 7+
Read more: cloudflare blog , origin security
Despite the above disadvantages, the technology looks quite interesting (considering the cost). Many sites that have not yet used HTTPS were given the opportunity to correct this “omission” :) What do you think?
UPD: In the user's browser, server certificates look like this:

Source: https://habr.com/ru/post/239507/
All Articles