Protecting HTTP traffic with Citrix Netscaler
Today, any medium and large organization in its work relies on a number of infrastructure IT products and a set of business applications. Flawless operation of the infrastructure and business applications is a crucial condition for the successful functioning of the organization. Accordingly, the main task of IT services is to provide uninterrupted, secure and productive real-time access to this corporate platform.
The solution, however, must meet a number of high requirements: to ensure the continuity of the company's business processes, to meet strict security standards, to maintain high IT infrastructure performance and to be easily scalable in order to provide the necessary expansion in accordance with the growth of the organization.
Over the past few years, this is the most corporate platform of capacious and heavyweight applications running exclusively on certain types and even versions of operating systems, transformed into lightweight, scalable and cross-platform web applications. I am not talking only about large web projects, forums and other high-traffic resources. Modern business translates CRM, ERP and other SAP and 1C similar platforms to the web. The reasons, I hope, are clear to everyone. But there is only one small cornerstone that modern business often ignores, and it, in turn, reminds of itself, when at best the entire enterprise stops working, at worst - leakage or loss of confidential information.
')
So in my case, the customer woke me up at one in the morning with a request to solve the problem, as their platform underwent a DDoS attack, paralyzing the work of both the entire enterprise and the work of clients. There are no explanatory instructions and descriptions of how Netscaler works, which was the main help in writing an article.

The first thing that had to be done with the customer’s web platform was to close the external network interface. In order to somehow reduce the load, I had to register a pool of IP addresses for access and testing outside. Then a web server was configured to limit the number of simultaneous sessions and requests. Further, countries began to open up through GeoIP. Then I had to recompile the web server to add some functionality to repel attacks. After failtoban was configured, dozens of lines of scripts were written for cron. It took 16-20 hours, but it was disappointing that many of the “patches” were in conflict with each other and were “scattered” throughout the system. And the attack, however, continued: the system now and again responded with an error 503. No one has ever done preventive measures, so there was no way to react immediately. This was done as a temporary measure in order to tune everything in one place with feeling and in a proper way - in Citrix Netscaler.
Netscaler is a multifunctional platform that solves most network problems or bottlenecks. This product can be compared with the Lego designer, from various parts of which you can configure a universal transformer - it will be compact and at the same time possess all the necessary tools for working with traffic. Netscaler can be used either as a VPX virtual device on all modern hypervisors, or as a physical device.
First of all, we will need to register at citrix.com. If your company already uses Citrix, then you can download the product under an existing account. If not, choose Create Customer Account, fill in the required fields, choose a username and password and you are already logged in with your account, even the email address does not need to be confirmed.
1. Go to the Downloads section.
2. Select NetScaler ADC, then Evaluations and Trial Software from the drop-down menu, and click the Find button.
3. Expand the section with the release where there is View All NetScaler Customer Trials.
4. Choose Try it FREE.
5. Fill out the form and click Proceed to download.
6. On the download page images will be available for different hypervisors: choose the one that suits you.
7. Install Netscaler in our hypervisor.
8. When you first start the console will wizard settings. We need to specify some data. Netscaler does not accept DHCP and logically has one interface, despite that it may have several physical or virtual ones. You must specify a local IP address that is available in the DMZ zone. I took 172.16.0.100
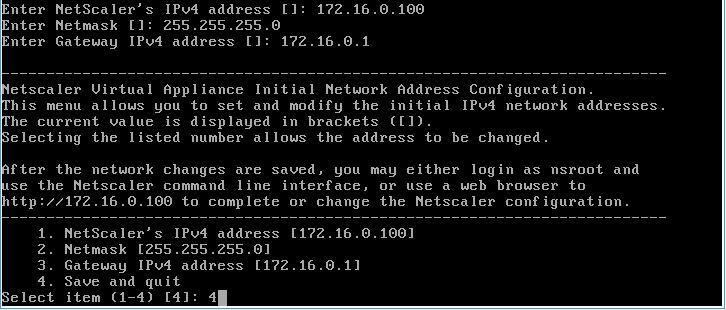
9. Open the page http://172.16.0.100 in the browser and log in with the username / password nsroot / nsroot
10. We will be asked to indicate the time zone, DNS and some other IP address. 172.16.0.100 is the address of Netscaler itself. Subnet IP address that will be used to work with other servers and services. That is, the flies are separate - cutlets too: the managing IP is one, for working with services it is another. Suddenly you have two DMZ zones or vlan networks or networks with different masks. Since in my case there is only one network, I indicated 172.16.0.101.
11. After a couple of clicks Next, you will be taken to the Configuration tab.
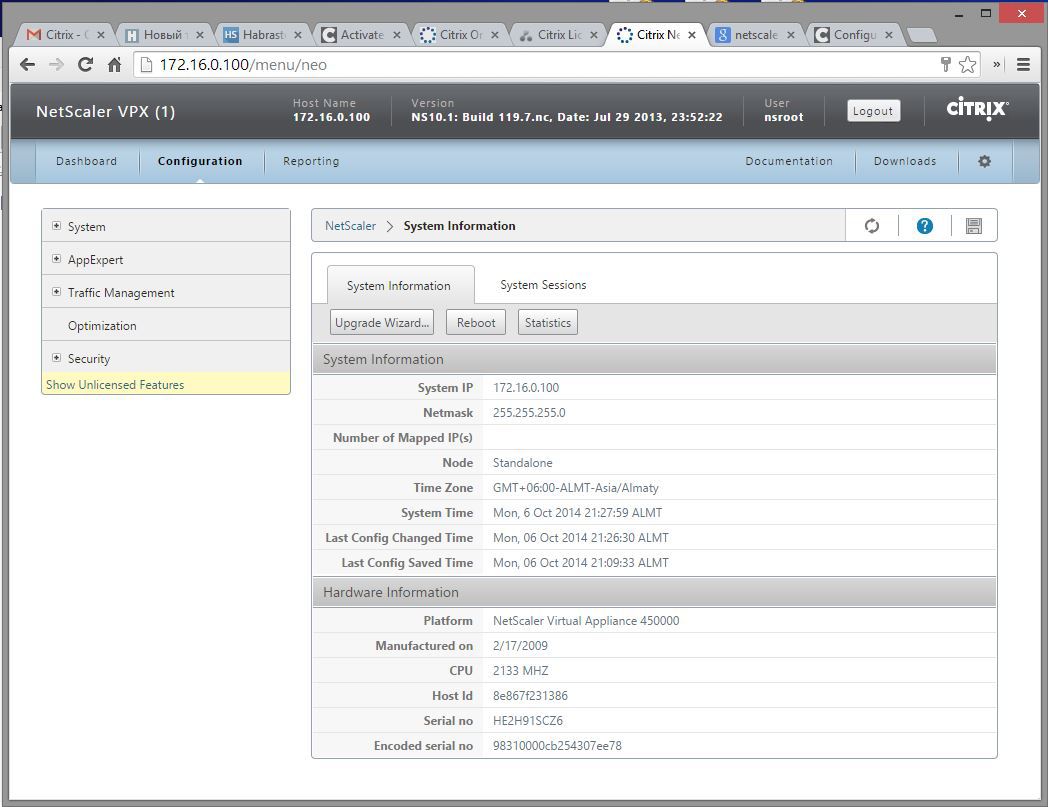
1. Now you need to download the license file. Go to the My Account page, select Activate and Allocate Licenses, click on the link in the corner Don't see your product? and enter the license code that we received in the mail. Double-click Continue and now see our product in the lists. From this moment began the countdown of the license.
2. Copy the Host Id to the buffer (this is the MAC address of our Netscaler) from the Configuration page of the Netscaler web interface, and return to the site where you need to download the license.
3. Insert the MAC address in the Host ID field, click Continue, then Confirm, then Ok and the file with the LIC extension will start loading.
4. Done, this is our license for a period of 90 days.
5. We update the Netscaler interface page (hereinafter referred to as NS), log in, we will again be asked to indicate the license. We select the file, load it and after successful loading it will be necessary to reboot the system, which will inform the window.
6. After the reboot in the licensing tab there will be a list of what is available to us within 90 days.

1. We must immediately clarify that the previous version is always available for a free trial. Unfortunately, Java version 7/45 x86 is required for full control and configuration via GUI. In the new version of NS, you can work with the latest any version of the JRE. If you do not want to do downgrade, you can use the command line. All the necessary commands will be at the end of the section. To do this, you need to open a terminal SSH session to our NS IP with a login / password of nsroot / nsroot.
2. To begin with, you have a web site that needs to be protected. He has his own domain name and is assigned an IP address. His native IP address will remain, but we need to register a virtual server in NS. To do this, you need a free IP address, which will be called VIP, and through it users will be accessed to your real web server. If the web service is external, then the IP is external, if the internal one is, respectively. Take for example 172.16.0.102.
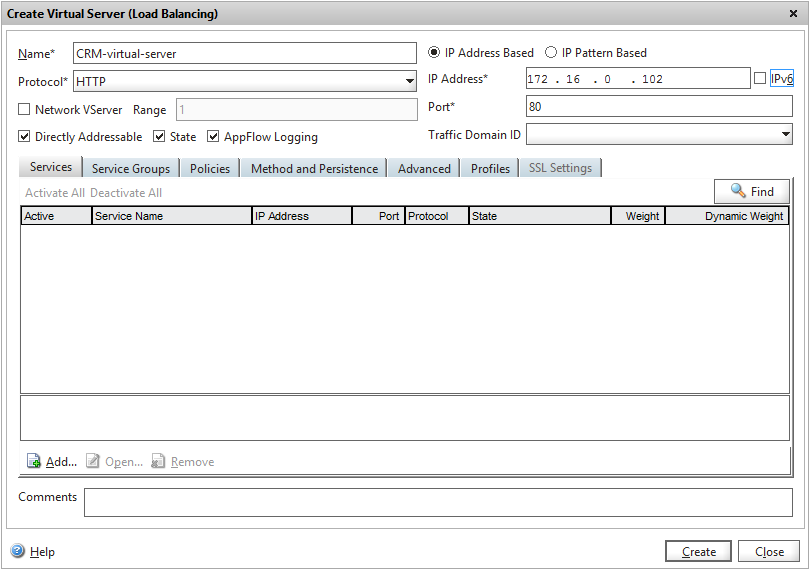
3. Go to Traffic Management, then to Virtual Servers and click the Add button.
We come up with a name, select the HTTP protocol, specify the VIP (virtual IP) and the port on which this virtual server will work, click Create and then Close.
4. Go to Servers, click Add, and specify the data of our web server. In fact, we need to give a name and specify an IP address or name. The port is not needed, as there can be other services on the server and on different ports.

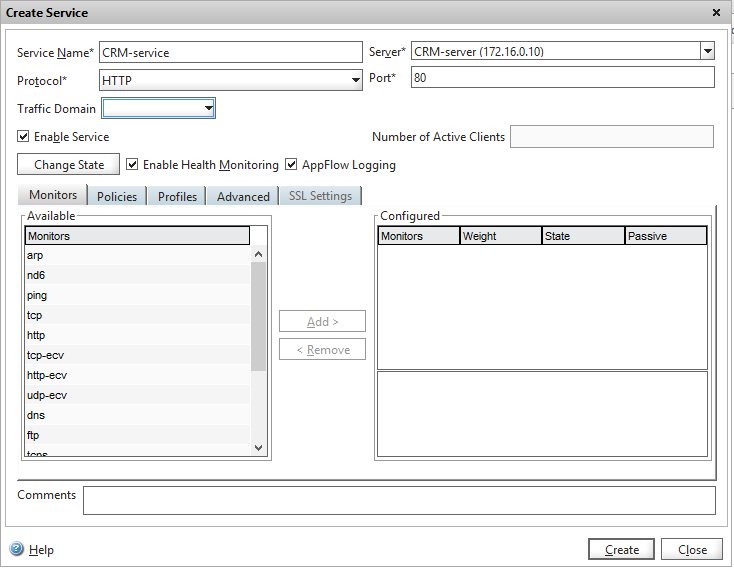
5. Now we need to connect our virtual server with the real one in the form of a certain service. We go to Services, click Add again, give a name, choose a protocol, service and port on which our server accepts connections.
6. It remains to add the created service to our virtual server. Go to the Virtual Servers, click on Open, put a tick in the Active column and confirm with OK. After that, your Virtual Server will become UP & RUNNING.

7. After all the changes, you need to click the icon in the form of a floppy disk to save the current configuration.
8. Open the page in the browser http://172.16.0.102 and voila, our site opens. From the first time, it is not entirely clear how this works, so let's look at what we did:
a) created a virtual server that will work on the virtual IP address via HTTP protocol through the 80th port.
b) add data about our real server
c) indicated that our server has HTTP service on port 80
d) offered our virtual server to process data for a specific service
e) saved the configuration.
9. Through the command line
Our virtual server is working. If the real server provides HTML content with conditional links, then it will even work out, otherwise you will have to change all full links to conditional links or change the DNS servers if the links point to a domain name. Suppose you have a site where the links are complete, for example <a href='http://www.domain.com/page1'> link </a>, then you need to redo it into <a href='/page1'> link </a>.
If you can not quickly redo it, then in DNS you reassign A record to www and the head domain to the IP address of your virtual server, that is, to 172.16.0.102.
The first thing we can do is gzip compression. At the same time, compression on a real server can be disabled. No, NS will not unpack and repack traffic, but for the purpose of sharing processor resources, let the web server do what it is supposed to do - deliver the finished content, NS retrieves it from the server as it is, and gives the end user already compressed according to the rules we specify .
1. In the System> Settings> Configure basic features menu, check the box on HTTP Compression.
2. In the web interface, go to Traffic Management> Load Balancing> Services, select the service, click Open, go to the Advanced tab and tick the box that we want to compress traffic. You can also specify other parameters, let's say the maximum number of clients and requests.
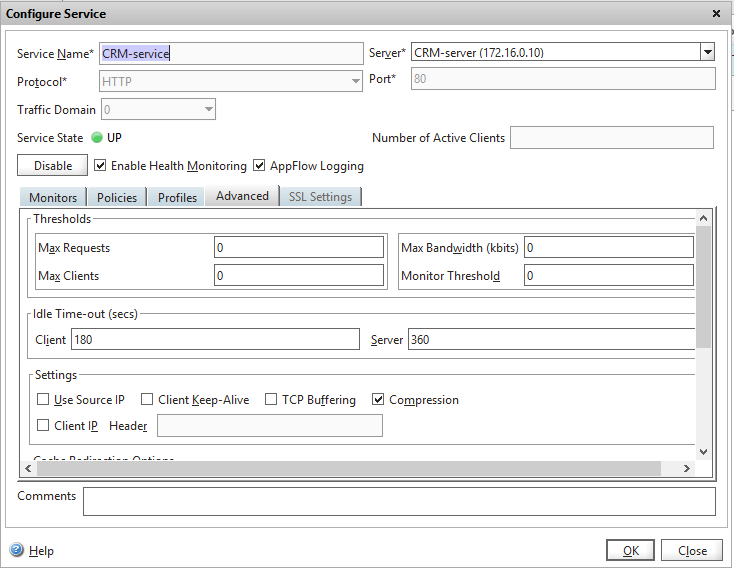
3. From this point on, our traffic is compressed according to the standard NS settings. But not all is compressed. Suppose some web servers in their MIME settings specify application / x-javascript for the js extension instead of text / javascript, respectively, no compression occurs. We can fix this situation by adding your policy.
Go to the Optimization> HTTP Compression> Policies menu, click Add, click Switch to Classic Syntax, and add a new rule.

4. The rule has been created, but so far it is not active and does not work. Right-click on the rule, select Policy Manager, select the Response tab, then Default Global, click the Insert Policy and select our rule, setting the highest priority.
5. Such rules can also be set to pdf, json and other types. You can also specify which minimum size to compress, from which subnets, for which browsers, etc. etc. Rules can be made not global, but for a specific service.
6. Through the command line:
“So what?” You say. And you will be right. All that has been described above is able to do a standard web server. As for protecting data from hacking, there is no way to train a standard server. You always have to rely on the correctness of the source code, which in most cases we did not write. And no one can ever give guarantees that there are no errors or omissions in the executable code.
At one time, while developing a large Internet project in a small team, I was seriously puzzled by the protection against SQL injections and wrote an API for accessing the database. I was calm for the project, until I began to check what programmers from my team are doing. Instead of passing the values by reference, they “collected” the SQL query according to the habit, concatenating the query with string and numeric variables, not worrying not only about screening, but even banal checking of the variables for validity of their values. What can we say about the sites of some online banks, where in 10-15 minutes I found several SQL vulnerabilities. And besides this, there are also cross-site scripting, fake cookies, the formation of malicious JSON and XML requests, etc.
To our joy, Netscaler is struggling with this pretty successfully.
1. In the System> Settings> Configure basic features menu, tick the Application Firewall.
2. In the Security> Application Firewall menu, launch the Application Firewall Wizard
3. Choose our configuration name and type Web 2.0
4. In Specify rule, leave everything as it is and click Next.
5. In the next dialog, we note what our web server works on.
6. In the Select signature action, leave everything as is.
7. In Select deep protections, we tick the first 4 options. It should be noted that HTML Cross-Site Scripting by default prohibits sending any HTML tags to GET and POST requests. This is not a problem, as for any rule you can set filters and conditions.
8. In Select deep actions, check the options that you want to block. At the initial stage, it is recommended not to block, but to walk around your site, to stage all possible user behaviors and already when statistics gather, decide what to block and where to create additional rules. All but cross-site scripting can be blocked immediately.
9. After creating the rule, open it and make additional settings.
a) set encoding
b) create a page where the user will be redirected if there was a hacking attempt. This is usually the home page, but you can create a separate page with information that your actions seemed suspicious and will be sent to the administration, and, if necessary, to the competent authorities.
c) a lot of other fine settings, a description of which can be found in the documentation.
10. Now we go to our site, open the pages with fictitious SQL injection http://172.16.0.102/?Search=00&q=CB506-67902 'UNION SELECT aaa FROM aaa and watch how we flip to the main page.
11. Put in the browser a plugin that allows you to edit the cookie, fix a couple and refresh the page. Cookies on your side do not change, but they will not be transmitted to the web server. NS caches all cookies that the original server sent to save. If in the next REQ request, NS finds a discrepancy between a previously set cookie, it will simply block them.
12. If you ticked the Block in the Cross-Site Scripting section, then try a GET or POST request to transfer HTML and also be redirected to the main page.
13. Isn't it great? If you dig in the settings, you will find a lot of interesting and useful things for yourself. Cookies can be encoded for security purposes that the user cannot and simply forge, because the NS will decode its key before transferring them to the web server. You can specify the types or names of the fields to specify the format of the data in the form of regular expressions for testing or screening. On certain pages or fields, you can make exceptions to check for HTML or SQL. With a properly configured NS, your site’s security will increase hundreds of times.
14. Through the command line
Finally, we come to the point of why it all started. In order not to go deep into how protection works, you can read the article Nginx Module for Combating DDoS . The principle is one to one, but I did not manage to launch this module as it should in a real situation.
1. Go to the Security> Protection Features> HTTP DoS menu and out of habit click Add.
2. In addition to the name there are two fields where you need to insert values. Let's figure out how to count them.
The first field Queue depth is the quantitative value of users who are waiting for their turn to respond to the server.
Suppose you have 86400 unique users per day or 3500 per hour or 60 per minute or 1 every second.
Of course, at night they are not there, in the daytime there are a lot of them. Multiply 10 times for greater importance and get 10 users per second. In general, you can see the statistics.
Suppose one user requests an average of 5-10 requests per page (html, css, js, img, etc.) and scans them for 5-10 seconds (which is why AJAX taxis).
That is, the server approximately at the peak of its load fulfills up to 100 responses per second.
Imagine that your web server is able to send up to 500 responses per second, but it receives 10,000 requests per second, or 20 times more.
How many real users are currently experiencing a problem? That's right, the same 10, the rest is an attack. When should start to panic? Immediately after 10? I would like to, but the minimum value is 21, so let's leave it as it is. That is, as soon as there are 21 or more sessions in the queue for receiving data, automatic protection against attack will be activated.
Now with the second field Client detect rate. This is the percentage of users who will be checked for lice. If we put 1% for verification, with the protection automatically turned on, the number of responses from the server will be only 5 (500 * 0.01), while 10,000 will wait for their turn. In other words, only 0.05% of current users will be tested. However, if the scan level is high (for example, at 10% the value will be checked 1000 requests), then this can block all outgoing traffic with checks already overloaded with an attack, if your channel is narrow. But I would put 30-35% to immediately begin to fight off the attack, since the channel is very thick. The field can be left empty and depending on the width of the channel, which NS can measure, the number of requests, responses and other indicators, the level of verification itself can vary.
3. Next, we go through the menu Traffic Management> Load Balancing> Services, open our service with the Open button and in the Policies / HTTP DoS tab insert the policy we just created.

4. Through the command line
Can this thing a lot. From what may be needed for sites is:
1. Separation of static and dynamic content to relieve the load.
2. Proxy static content.
3. Caching dynamic content and flushing the cache according to certain conditions or time.
4. Proxy and caching mySQL and other relational databases in order to reduce the number of samples.
5. Separation of traffic and content by network addresses, geo-location and many other parameters.
6. Encryption traffic.
7. Work as a DNS server.
8. By default, NS already has network protection, for example, from ICMP flood, etc.
Everything is configured quite easily, although not always intuitively. The instruction is available on the vendor website . You can read in Russian about the main features on the site http://netscaler.kz .
The lack of information in Russian about this platform greatly affects its prevalence in the CIS countries. Apparently, therefore, our modern network administrators underestimated the capabilities of this product.
After all, it’s not for nothing that two years ago, Cisco officially announced that it was stopping the further development of its ACE balancer, and more recently Netscaler is part of some series of Cisco switches.
Thank!
The solution, however, must meet a number of high requirements: to ensure the continuity of the company's business processes, to meet strict security standards, to maintain high IT infrastructure performance and to be easily scalable in order to provide the necessary expansion in accordance with the growth of the organization.
Over the past few years, this is the most corporate platform of capacious and heavyweight applications running exclusively on certain types and even versions of operating systems, transformed into lightweight, scalable and cross-platform web applications. I am not talking only about large web projects, forums and other high-traffic resources. Modern business translates CRM, ERP and other SAP and 1C similar platforms to the web. The reasons, I hope, are clear to everyone. But there is only one small cornerstone that modern business often ignores, and it, in turn, reminds of itself, when at best the entire enterprise stops working, at worst - leakage or loss of confidential information.
')
So in my case, the customer woke me up at one in the morning with a request to solve the problem, as their platform underwent a DDoS attack, paralyzing the work of both the entire enterprise and the work of clients. There are no explanatory instructions and descriptions of how Netscaler works, which was the main help in writing an article.
How it all began
The first thing that had to be done with the customer’s web platform was to close the external network interface. In order to somehow reduce the load, I had to register a pool of IP addresses for access and testing outside. Then a web server was configured to limit the number of simultaneous sessions and requests. Further, countries began to open up through GeoIP. Then I had to recompile the web server to add some functionality to repel attacks. After failtoban was configured, dozens of lines of scripts were written for cron. It took 16-20 hours, but it was disappointing that many of the “patches” were in conflict with each other and were “scattered” throughout the system. And the attack, however, continued: the system now and again responded with an error 503. No one has ever done preventive measures, so there was no way to react immediately. This was done as a temporary measure in order to tune everything in one place with feeling and in a proper way - in Citrix Netscaler.
Netscaler is a multifunctional platform that solves most network problems or bottlenecks. This product can be compared with the Lego designer, from various parts of which you can configure a universal transformer - it will be compact and at the same time possess all the necessary tools for working with traffic. Netscaler can be used either as a VPX virtual device on all modern hypervisors, or as a physical device.
Install and configure virtual machines
First of all, we will need to register at citrix.com. If your company already uses Citrix, then you can download the product under an existing account. If not, choose Create Customer Account, fill in the required fields, choose a username and password and you are already logged in with your account, even the email address does not need to be confirmed.
Download, install and configure Netscaler
1. Go to the Downloads section.
2. Select NetScaler ADC, then Evaluations and Trial Software from the drop-down menu, and click the Find button.
3. Expand the section with the release where there is View All NetScaler Customer Trials.
4. Choose Try it FREE.
5. Fill out the form and click Proceed to download.
6. On the download page images will be available for different hypervisors: choose the one that suits you.
7. Install Netscaler in our hypervisor.
8. When you first start the console will wizard settings. We need to specify some data. Netscaler does not accept DHCP and logically has one interface, despite that it may have several physical or virtual ones. You must specify a local IP address that is available in the DMZ zone. I took 172.16.0.100
9. Open the page http://172.16.0.100 in the browser and log in with the username / password nsroot / nsroot
10. We will be asked to indicate the time zone, DNS and some other IP address. 172.16.0.100 is the address of Netscaler itself. Subnet IP address that will be used to work with other servers and services. That is, the flies are separate - cutlets too: the managing IP is one, for working with services it is another. Suddenly you have two DMZ zones or vlan networks or networks with different masks. Since in my case there is only one network, I indicated 172.16.0.101.
11. After a couple of clicks Next, you will be taken to the Configuration tab.
Registration and Licensing
1. Now you need to download the license file. Go to the My Account page, select Activate and Allocate Licenses, click on the link in the corner Don't see your product? and enter the license code that we received in the mail. Double-click Continue and now see our product in the lists. From this moment began the countdown of the license.
2. Copy the Host Id to the buffer (this is the MAC address of our Netscaler) from the Configuration page of the Netscaler web interface, and return to the site where you need to download the license.
3. Insert the MAC address in the Host ID field, click Continue, then Confirm, then Ok and the file with the LIC extension will start loading.
4. Done, this is our license for a period of 90 days.
5. We update the Netscaler interface page (hereinafter referred to as NS), log in, we will again be asked to indicate the license. We select the file, load it and after successful loading it will be necessary to reboot the system, which will inform the window.
6. After the reboot in the licensing tab there will be a list of what is available to us within 90 days.
Configuring servers, services, policies, policies and rules
1. We must immediately clarify that the previous version is always available for a free trial. Unfortunately, Java version 7/45 x86 is required for full control and configuration via GUI. In the new version of NS, you can work with the latest any version of the JRE. If you do not want to do downgrade, you can use the command line. All the necessary commands will be at the end of the section. To do this, you need to open a terminal SSH session to our NS IP with a login / password of nsroot / nsroot.
2. To begin with, you have a web site that needs to be protected. He has his own domain name and is assigned an IP address. His native IP address will remain, but we need to register a virtual server in NS. To do this, you need a free IP address, which will be called VIP, and through it users will be accessed to your real web server. If the web service is external, then the IP is external, if the internal one is, respectively. Take for example 172.16.0.102.
3. Go to Traffic Management, then to Virtual Servers and click the Add button.
We come up with a name, select the HTTP protocol, specify the VIP (virtual IP) and the port on which this virtual server will work, click Create and then Close.
4. Go to Servers, click Add, and specify the data of our web server. In fact, we need to give a name and specify an IP address or name. The port is not needed, as there can be other services on the server and on different ports.
5. Now we need to connect our virtual server with the real one in the form of a certain service. We go to Services, click Add again, give a name, choose a protocol, service and port on which our server accepts connections.
6. It remains to add the created service to our virtual server. Go to the Virtual Servers, click on Open, put a tick in the Active column and confirm with OK. After that, your Virtual Server will become UP & RUNNING.
7. After all the changes, you need to click the icon in the form of a floppy disk to save the current configuration.
8. Open the page in the browser http://172.16.0.102 and voila, our site opens. From the first time, it is not entirely clear how this works, so let's look at what we did:
a) created a virtual server that will work on the virtual IP address via HTTP protocol through the 80th port.
b) add data about our real server
c) indicated that our server has HTTP service on port 80
d) offered our virtual server to process data for a specific service
e) saved the configuration.
9. Through the command line
add lb vserver CRM-virtual-server HTTP 172.16.0.102 80 add server CRM-server 172.16.0.10 add service CRM-service CRM-server HTTP 80 bind lb vserver CRM-virtual-server CRM-service save config Compression and compression of traffic
Our virtual server is working. If the real server provides HTML content with conditional links, then it will even work out, otherwise you will have to change all full links to conditional links or change the DNS servers if the links point to a domain name. Suppose you have a site where the links are complete, for example <a href='http://www.domain.com/page1'> link </a>, then you need to redo it into <a href='/page1'> link </a>.
If you can not quickly redo it, then in DNS you reassign A record to www and the head domain to the IP address of your virtual server, that is, to 172.16.0.102.
The first thing we can do is gzip compression. At the same time, compression on a real server can be disabled. No, NS will not unpack and repack traffic, but for the purpose of sharing processor resources, let the web server do what it is supposed to do - deliver the finished content, NS retrieves it from the server as it is, and gives the end user already compressed according to the rules we specify .
1. In the System> Settings> Configure basic features menu, check the box on HTTP Compression.
2. In the web interface, go to Traffic Management> Load Balancing> Services, select the service, click Open, go to the Advanced tab and tick the box that we want to compress traffic. You can also specify other parameters, let's say the maximum number of clients and requests.
3. From this point on, our traffic is compressed according to the standard NS settings. But not all is compressed. Suppose some web servers in their MIME settings specify application / x-javascript for the js extension instead of text / javascript, respectively, no compression occurs. We can fix this situation by adding your policy.
Go to the Optimization> HTTP Compression> Policies menu, click Add, click Switch to Classic Syntax, and add a new rule.
4. The rule has been created, but so far it is not active and does not work. Right-click on the rule, select Policy Manager, select the Response tab, then Default Global, click the Insert Policy and select our rule, setting the highest priority.
5. Such rules can also be set to pdf, json and other types. You can also specify which minimum size to compress, from which subnets, for which browsers, etc. etc. Rules can be made not global, but for a specific service.
6. Through the command line:
enable ns feature cmp set service CRM-service -CMP yes add cmp policy ns_cmp_javascript -rule "RES.HTTP.HEADER Content-Type CONTAINS javascript" -resAction COMPRESS add cmp policy ns_cmp_json -rule "RES.HTTP.HEADER Content-Type CONTAINS json" -resAction COMPRESS add cmp policy ns_cmp_pdf -rule "RES.HTTP.HEADER Content-Type CONTAINS application/pdf" -resAction COMPRESS bind cmp global ns_cmp_javascript -priority 10001 -state ENABLED bind cmp global ns_cmp_json -priority 10002 -state ENABLED bind cmp global ns_cmp_pdf -priority 10003 -state ENABLED save config Data protection
“So what?” You say. And you will be right. All that has been described above is able to do a standard web server. As for protecting data from hacking, there is no way to train a standard server. You always have to rely on the correctness of the source code, which in most cases we did not write. And no one can ever give guarantees that there are no errors or omissions in the executable code.
At one time, while developing a large Internet project in a small team, I was seriously puzzled by the protection against SQL injections and wrote an API for accessing the database. I was calm for the project, until I began to check what programmers from my team are doing. Instead of passing the values by reference, they “collected” the SQL query according to the habit, concatenating the query with string and numeric variables, not worrying not only about screening, but even banal checking of the variables for validity of their values. What can we say about the sites of some online banks, where in 10-15 minutes I found several SQL vulnerabilities. And besides this, there are also cross-site scripting, fake cookies, the formation of malicious JSON and XML requests, etc.
To our joy, Netscaler is struggling with this pretty successfully.
1. In the System> Settings> Configure basic features menu, tick the Application Firewall.
2. In the Security> Application Firewall menu, launch the Application Firewall Wizard
3. Choose our configuration name and type Web 2.0
4. In Specify rule, leave everything as it is and click Next.
5. In the next dialog, we note what our web server works on.
6. In the Select signature action, leave everything as is.
7. In Select deep protections, we tick the first 4 options. It should be noted that HTML Cross-Site Scripting by default prohibits sending any HTML tags to GET and POST requests. This is not a problem, as for any rule you can set filters and conditions.
8. In Select deep actions, check the options that you want to block. At the initial stage, it is recommended not to block, but to walk around your site, to stage all possible user behaviors and already when statistics gather, decide what to block and where to create additional rules. All but cross-site scripting can be blocked immediately.
9. After creating the rule, open it and make additional settings.
a) set encoding
b) create a page where the user will be redirected if there was a hacking attempt. This is usually the home page, but you can create a separate page with information that your actions seemed suspicious and will be sent to the administration, and, if necessary, to the competent authorities.
c) a lot of other fine settings, a description of which can be found in the documentation.
10. Now we go to our site, open the pages with fictitious SQL injection http://172.16.0.102/?Search=00&q=CB506-67902 'UNION SELECT aaa FROM aaa and watch how we flip to the main page.
11. Put in the browser a plugin that allows you to edit the cookie, fix a couple and refresh the page. Cookies on your side do not change, but they will not be transmitted to the web server. NS caches all cookies that the original server sent to save. If in the next REQ request, NS finds a discrepancy between a previously set cookie, it will simply block them.
12. If you ticked the Block in the Cross-Site Scripting section, then try a GET or POST request to transfer HTML and also be redirected to the main page.
13. Isn't it great? If you dig in the settings, you will find a lot of interesting and useful things for yourself. Cookies can be encoded for security purposes that the user cannot and simply forge, because the NS will decode its key before transferring them to the web server. You can specify the types or names of the fields to specify the format of the data in the form of regular expressions for testing or screening. On certain pages or fields, you can make exceptions to check for HTML or SQL. With a properly configured NS, your site’s security will increase hundreds of times.
14. Through the command line
enable ns feature AppFW add appfw profile crm-appfw-profile -type HTML XML set appfw profile crm-appfw-profile -cookieConsistencyAction block log stats learn set appfw profile crm-appfw-profile -bufferOverflowAction block log stats set appfw profile crm-appfw-profile -crossSiteScriptingAction log stats learn set appfw profile crm-appfw-profile -SQLInjectionAction block log stats learn set appfw profile crm-appfw-profile -startURLAction log stats learn set appfw profile crm-appfw-profile -defaultCharSet utf-8 add appfw policy crm-appfw-policy true crm-appfw-profile bind appfw global crm-appfw-policy 10 save config Reflect DDoD attacks
Finally, we come to the point of why it all started. In order not to go deep into how protection works, you can read the article Nginx Module for Combating DDoS . The principle is one to one, but I did not manage to launch this module as it should in a real situation.
1. Go to the Security> Protection Features> HTTP DoS menu and out of habit click Add.
2. In addition to the name there are two fields where you need to insert values. Let's figure out how to count them.
The first field Queue depth is the quantitative value of users who are waiting for their turn to respond to the server.
Suppose you have 86400 unique users per day or 3500 per hour or 60 per minute or 1 every second.
Of course, at night they are not there, in the daytime there are a lot of them. Multiply 10 times for greater importance and get 10 users per second. In general, you can see the statistics.
Suppose one user requests an average of 5-10 requests per page (html, css, js, img, etc.) and scans them for 5-10 seconds (which is why AJAX taxis).
That is, the server approximately at the peak of its load fulfills up to 100 responses per second.
Imagine that your web server is able to send up to 500 responses per second, but it receives 10,000 requests per second, or 20 times more.
How many real users are currently experiencing a problem? That's right, the same 10, the rest is an attack. When should start to panic? Immediately after 10? I would like to, but the minimum value is 21, so let's leave it as it is. That is, as soon as there are 21 or more sessions in the queue for receiving data, automatic protection against attack will be activated.
Now with the second field Client detect rate. This is the percentage of users who will be checked for lice. If we put 1% for verification, with the protection automatically turned on, the number of responses from the server will be only 5 (500 * 0.01), while 10,000 will wait for their turn. In other words, only 0.05% of current users will be tested. However, if the scan level is high (for example, at 10% the value will be checked 1000 requests), then this can block all outgoing traffic with checks already overloaded with an attack, if your channel is narrow. But I would put 30-35% to immediately begin to fight off the attack, since the channel is very thick. The field can be left empty and depending on the width of the channel, which NS can measure, the number of requests, responses and other indicators, the level of verification itself can vary.
3. Next, we go through the menu Traffic Management> Load Balancing> Services, open our service with the Open button and in the Policies / HTTP DoS tab insert the policy we just created.
4. Through the command line
enable ns feature HttpDoSProtection add dos policy crm-ddos-policy -qDepth 21 -cltDetectRate 33 bind service CRM-service -policyName crm-ddos-policy save config And what else can Netscaler
Can this thing a lot. From what may be needed for sites is:
1. Separation of static and dynamic content to relieve the load.
2. Proxy static content.
3. Caching dynamic content and flushing the cache according to certain conditions or time.
4. Proxy and caching mySQL and other relational databases in order to reduce the number of samples.
5. Separation of traffic and content by network addresses, geo-location and many other parameters.
6. Encryption traffic.
7. Work as a DNS server.
8. By default, NS already has network protection, for example, from ICMP flood, etc.
Conclusion
Everything is configured quite easily, although not always intuitively. The instruction is available on the vendor website . You can read in Russian about the main features on the site http://netscaler.kz .
The lack of information in Russian about this platform greatly affects its prevalence in the CIS countries. Apparently, therefore, our modern network administrators underestimated the capabilities of this product.
After all, it’s not for nothing that two years ago, Cisco officially announced that it was stopping the further development of its ACE balancer, and more recently Netscaler is part of some series of Cisco switches.
Thank!
Source: https://habr.com/ru/post/239411/
All Articles