We get into the computer without using input tools, look for the Joker and connect to the server on Android - in tasks NeoQUEST-2014!

The qualifying round of NeoQUEST-2015 will start very soon, and as a preparation for it, we offer, together with us, to sort out the tasks of the in-person round of NeoQUEST-2014! We have already described how NeoQUEST-2014 passed, shared the reports and photos (perhaps, someone even found himself on them!). Now let us tell about that mysterious and hidden from the viewers' eyes, but the most important part of NeoQUEST is the competition of cybersecurity experts who turned out to be the best in the February online tour.
The confrontation for participants included 5 tasks, but one of them was not passed by anyone. In this article we will analyze the four passed:
- “Am I Joker?” - we are engaged in competitive intelligence, using all the information about the user that we managed to get from social networks, we are entering a third-party site and exploiting its vulnerability;
- “Unexpected find” - is there a computer and a flash drive, but there is no mouse or keyboard? It does not matter, because the flash drive is not simple, but with SecureDrive, and one of its partitions can be defined by the computer as a CD;
- “Do not believe your eyes” - how to find a malicious program on a computer that hides its network activity, and at the same time files on the disk?
- “Frames decide everything” - we connect to a web server that suddenly turns up on an Android phone, and create a special jar to get the key.
Before proceeding to the analysis of tasks, let's say about the most important - who nevertheless became the winner of NeoQUEST-2014:
I place - AV1ct0r
II place - Dor1s
III place - Abr1k0s
')
AV1ct0r received the main prize - a trip to an international conference on information security, and the guys divided the LEGO-robot and a 3D-pen with a set of colored plastic between them.
By the way, many guests of the event also left with small, but pleasant gifts won in competitions (about this in the article about how the NeoQUEST-2014 full-time tour went).
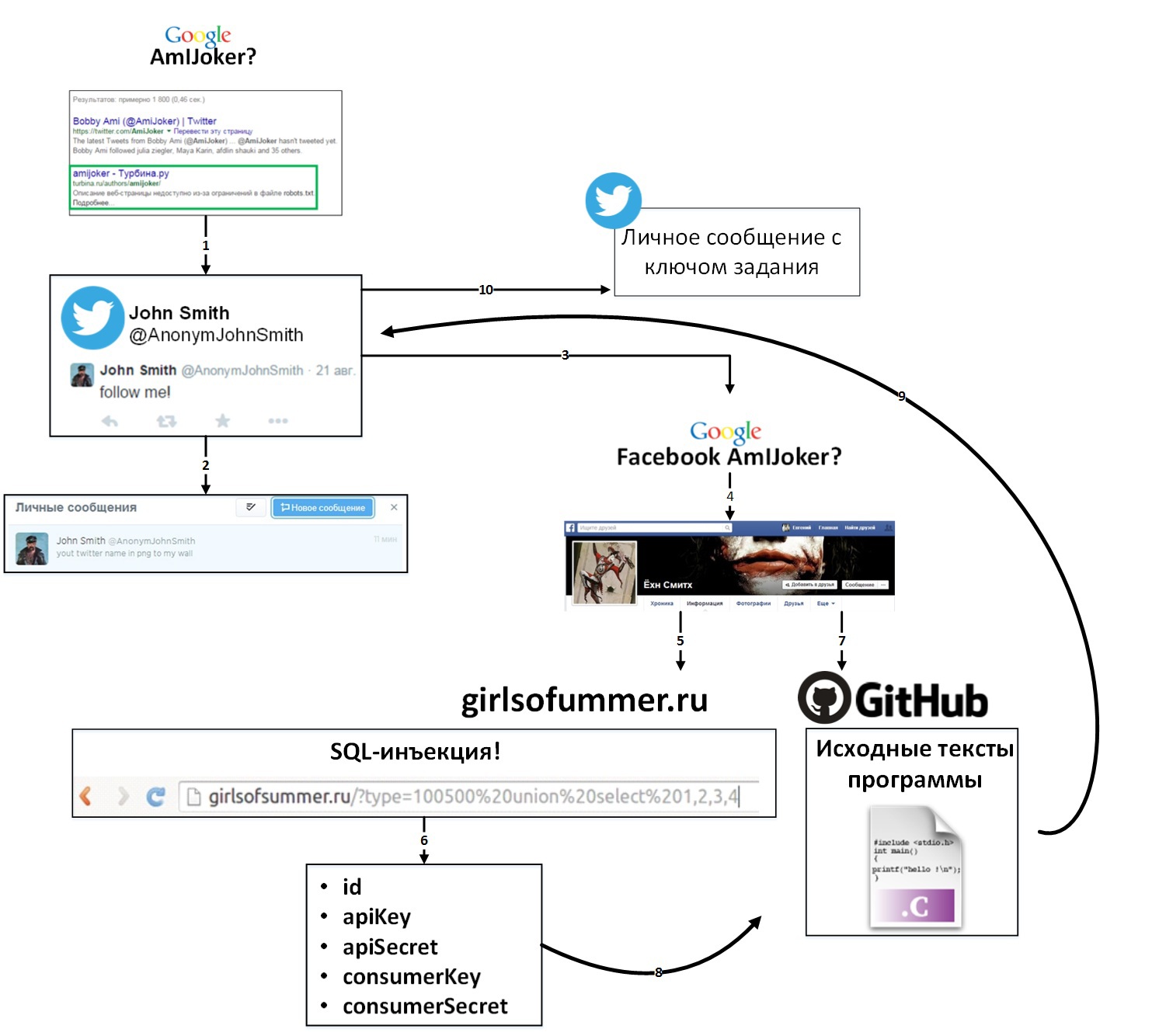
Am I Joker? - task number 1
The entry point to the execution of the task was hidden in the title. Further passage of the task was divided into the following stages:
- Searching for the phrase amijoker in the google.com search engine gave information interesting to the participants:
- eponymous account on the website of the tourist community "Turbine"
- link to the user profile on the social network Facebook
- Getting useful information from the account on the Turbine website did not require registration participants. Here are what members might notice when carefully viewing the AmIJoker user profile:
- link to John Smith's blog on Twitter
- call to subscribe to blog on twitter
- information that the user is a programmer
- If you go to the user's Twitter blog and subscribe to it, immediately after that, John Smith subscribed to the member's account and sent him a personal message with the following text: “your twitter name in png to my wall”. In this part of the assignment, participants had to guess that the name in the png should be hidden with the help of steganography. But not any algorithm will do. Of the ideas where to search for the desired algorithm, the most logical was the idea of searching in your account on Facebook.
- Indeed, a link to the project posted on github.com was posted on the account wall, and in the personal information another link to github.com
- Go to github.com on the first link and see the project. The program is written in PHP and works with the Twitter API. With it, you could upload a photo, but not enough keys for the API and OAuth. This is where the second link to github.com comes in handy.
- In this repository, a project written in the C language is saved. It implements one of the simplest steganography algorithms. But how to get the keys to work with the Twitter API?
- Here and attentiveness of participants was checked! In the legend, it was not for nothing that the song by Aerosmith - “Girls Of Summer” - was mentioned. After a brief search, many found the site of summer girls. Also the address of this site could be found in the general information of the account on Facebook. The site looks summer-like and is pleasing to the eye!
- The site does not carry much functionality, however, an experienced eye may notice that switching between photos occurs through the transfer of GET parameters. One of the two parameters is vulnerable to sql injections. With the help of this simple injection, participants could get the keys needed to work with Twitter api:
- id 1
- apiKey 603445921-b8c9k8OMhalLS8FakTpDHoUuXIzKuHLabOPWspsR
- apiSecret O0DWIqmlNT02RKUZcXHIvkyMWG7Hwd9vKzAjd7JJ89Kbg
- consumerKey vlC5S1NCMHHg8mD1ghPRkA
- consumerSecret 3w4cIrHyI3IYUZW5O2ppcFXmsACDaENzFdLIKmEU84
Having received all the necessary tools, it was necessary to simply insert the keys into the finished program and upload the picture to Twitter.
If the participant's name was correctly recorded inside the png file, then in response to the picture, he received a personal message with the task key.
In general, the scheme of the task looked like this:
Unexpected find - task number 2
All that was given to the participants is a computer without any means of input and a Transcend flash drive with the SecureDrive function ... The computer only had a monitor and a usb port, and the keyboard and mouse did not function. BIOS, by the way, was password-protected, so participants had to make do with what they had. According to the assignment, participants were required to copy backup copies of sent mail from this computer and find a letter with a secret key.
In this situation, it is obvious that interaction with a computer is possible only with the help of autorun programs from a flash drive. The simplest test shows that autostart from removable media is disabled. Here you need to remember that autorun is possible not only from them, but also from CDs, and also pay attention to the issued USB flash drive, namely to SecureDrive. There is a section on the flash drive, which is defined by the computer as a compact disk, and on the other partition there was a special program that helped work with the protected partition of the flash drive! This was supposed to push the idea of using the section for their own purposes!
Such flash drives are quite common, and are often used as bootable ones, so it’s enough just to find information on how to replace the contents of a virtual CD-ROM with your own. To do this, use the utility from the manufacturer - JetFlash Online Recovery , designed to restore the partition from SecureDrive in case of problems with the device. An examination of the utility shows that the partition is created based on an ISO image that is stored separately from the executable file. In this case, there are no checks, so that the required modification of the flash drive is achieved by replacing this image with a specially prepared one.
After receiving the ability to execute arbitrary commands on the target computer, you can start searching for backup copies. The presence of the IIS shortcut on the desktop pushes to check the root of the C: \ drive for the presence of the corresponding folder in it:
dir C:\ There is also a backup folder. Since the search for the desired letter without the possibility of using the keyboard can take a long time, the next step is to copy this folder to the second section of the flash drive. Before this, you need to determine the drive letter assigned to it in order to prepare the copy command:
xcopy C:\backup F:\backup /I /Q /Y Copying takes a long time due to the number of files with letters. For the same reason, the required letter cannot be found manually. However, the legend of the job gives a hint: the secret key was mailed on June 12! It remains only to automate the search process with the parameter, which is quite simple:
grep -l "12 Jun" * | sort -u | xargs grep -E "\<[a-f0-9]{32}\>" Among the rows found, you can manually find the desired key.
Do not believe your eyes - task number 3
In order to find the key, participants were given sheets with the logo "NeoQUEST", containing the word RDP, IP-address and login-password. The first logical thought is to try to access the specified computer via RDP ... and it works!
The task says nothing about how to find the key, which means that you have to act on a whim. The desktop of the computer was empty, with the exception of three shortcuts with browsers that were clearly located there for a reason. When I try to launch Google Chrome ... nothing happens. A normal browser window opens, you can go to any site, read news, for example. When you run Mozilla Firefox - the situation is similar. Internet Explorer - all without changes. It is logical to try to look at browser-specific data: the history of visiting web pages, saved passwords, cookies, etc. ... But everything turns out to be unsuccessful - the history is cleared, there are no passwords.


Okay, if the browser "externally" functions as usual and has no hooks, then perhaps the "internal" operation, invisible to the average user, has its own characteristics. And the first detectable feature is the browser's periodic calls to the remote server, despite the fact that the open tabs are empty. Such actions are easily detected by the standard operating system application - Resource Monitor.

Having installed the Wireshark sniffer and analyzed the outgoing traffic, the participants were able to detect the data flow to the WEB server 10.0.25.120 to the stub.php file. It can be interesting! But no, no matter how much you scan this IP-address, no matter how much you break on this server - no result. And, running ahead, really: the server is absolutely empty, there is no valuable information on it and it is used only to indicate that the participants are moving in the right direction.
The following feature is found after a more in-depth analysis of the functioning of browser processes, namely, the resources they use. To do this, you can use both standard tools (Resource Monitor) and third-party (although it is still a question of how “third-party” you can call the funds from Mr. Russinovich) Process Explorer and Process Monitor.
Process Explorer allows you to see the hierarchical display of processes, their properties, security settings, the resources they have, and so on. But when browsing through interesting processes do not show anything interesting.
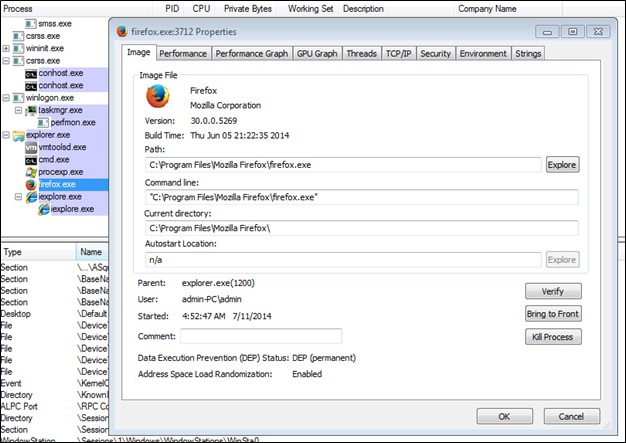
But after using Process Monitor, the answer to the task is practically in the hands.
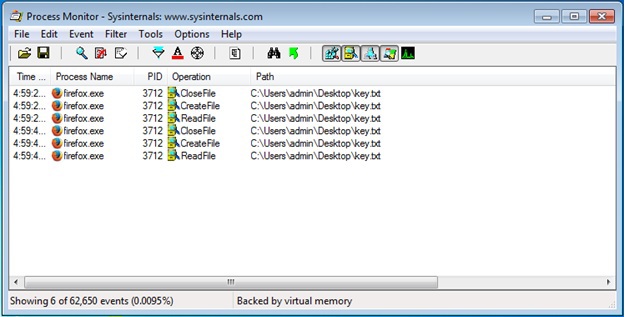
Process Monitor shows that periodically there is a request to the key.txt file, which lies on the desktop. Strange, but there is no such file. How to be? And here it is worth remembering the old trick - the file can be hidden, but, knowing the location, you can open it. A brilliant program allows you to do this (exhale!): Notepad.exe
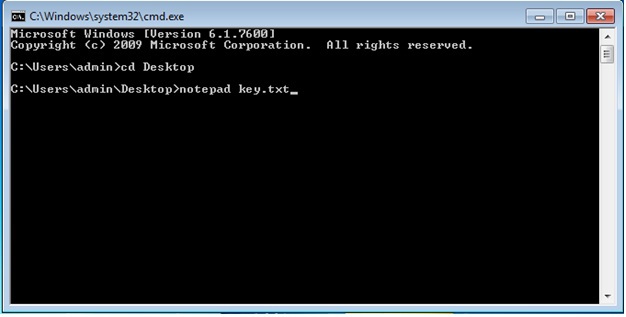
That's all. In the Notepad window that opens, the key required for the participant is located. Victory!

Now everything is clear. There is malware on the computer that somehow injects its code into all browsers, with the help of which it hides its network communication with the website. In addition, it also hides its files on the disk, in particular, the file with the key to the task.
Frames solve everything - task number 4
In the legend, the participants were told that it was necessary to track down the business contacts of one person: “Certainly there are a lot of useful numbers in the phone book” (extract from the legend) and an IP address was given where you can access this book.
When switching to this IP through a browser, the user was asked to upload a picture. If the user uploaded the jpg-file, then he was given a link to the edited image.
At first glance, this is a task for Web security, but this is not at all the case. If you start to "pick" saytik, then you can see a few interesting things!
First, using the Source Code Disclosure vulnerability, you can download the upload.php file, just by writing something like 192.168.0.222 : 8080 / upload.php in the address bar of your browser or by changing the case in the file extension. The source code upload.php is:
<html> <head> <title>Make your retro pattern</title> </head> <body> <?php $my_name = htmlspecialchars(trim($_POST["action"])); echo $my_name; $date = date_create(); if($_FILES["filename"]["size"] > 1024*1024) { echo ("Sorry bro ... your file is more then 1Mb..."); exit(); } $valid_types = array("jpg", "jar"); $ext = substr($_FILES['filename']['name'], 1 + strrpos($_FILES['filename']['name'], ".")); if (!in_array($ext, $valid_types)) { echo 'invalid file type'; exit(); } if(copy($_FILES["filename"]["tmp_name"], "/sdcard/pws/www/".$my_name."_".md5($_FILES["filename"]["name"].date_timestamp_get($date)).$_FILES["filename"]["name"])) { echo("success"); } else { echo("error"); } sleep(5); echo("<br>Your file is here"); $url="/res/".$my_name."_".md5($_FILES["filename"]["name"].date_timestamp_get($date)).$_FILES["filename"]["name"]; echo("<p><a href=".$url.">Your new file</p>"); ?> </body> </html> What is interesting here? For a start, we see that you can download not only uninteresting jpg for us, but also a very interesting jar, apparently, this server can work with Java. Next we see the path “/ sdcard / pws / www /”, the word sdcard is very similar to the fact that the server is on the phone (although it is still difficult to believe in it!). And if you just go and search Google for this line, it becomes very similar to the fact that this is the Palapa Web Server, raised on Android.
In addition, participants could find a very interesting file information, simply by scanning the site with a scanner, for example, ArxScanSite, defining the file structure of the site. This file is a picture below.
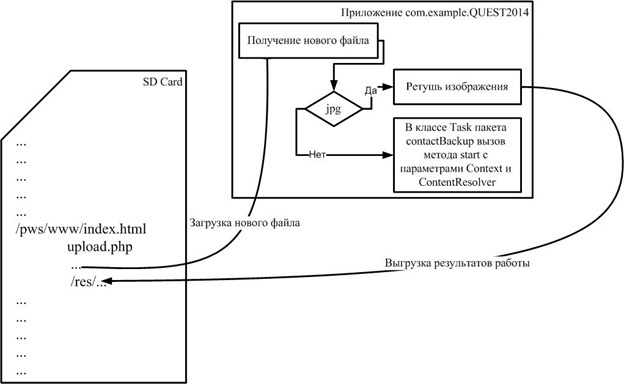
And after this doubt that this is a phone, should not remain. It remains to connect Java + phone = Android and it turns out that we have a web server raised on an Android phone, although you can see once more by scanning it with Nmap.
So, what we have: in front of us is a web server on Android, we know the path to the root of the server “/ sdcard / pws / www /”, we can download jar-files. And here the most important thing to remember is that in the assignment we are told “Surely a lot of useful numbers are stored in the phone book”, which means according to the downloaded picture we need to create a jar that will write all the phone numbers stored by the Android phone to a file on the memory card by the following path: "/ sdcard / pws / www /". Looking at the picture it becomes clear that you need to create a com.example.QUEST2014.contactBackup package in which you create a start method that accepts Context and ContentResolver as input and records phone numbers to a file.
Next, you need to make this jar applicable for Android, there are several ways. The first path is performed in 4 stages:
- Exporting only our class to a jar file, after which a regular jar file will be received as a zip archive with a class file inside.
- Creating a dex-file from our jar-file using the jar2dex utility, you get the classes.dex file.
- Archiving the classes.dex file into a zip archive.
- Rename the resulting zip archive to a jar file.
Another method includes 5 stages.
- Compile our application.
- Search the directory where the Android SDK is located, the directory containing the dx.bat utility (for example, “android-sdk \ platforms \ android-3 \ tools”).
- Creation of a directory with an arbitrary name in this directory, for example, "1". Inside the directory "1" create a file structure, similar to the structure of our application, i.e. "1 \ com \ example \ QUEST2014 \ contactBackup".
- Copying into this directory the contents of the directory "\ out \ production \ APPLICATION NAME \ com \ example \ QUEST2014 \ contactBackup".
- Call dx.bat with the following parameters - “dx --dex --no-strict --output = ctf.jar 1 /”. In the end, got the desired file - ctf.jar.
It would seem that everything was a victory, but it was not there! When you try to download this jar, the site gives an error that convert.jar does not know such a file. Everything turns out to be very simple if you look at index.html (the source code is shown below). You may notice that in the upload.php passed a hidden tag called action and having the value "convert.jar"
<html> <head> <title>Make your retro pattern</title> </head> <body> <h2><p><b>Upload your image</b></p></h2> <form action="upload.php" method="post" enctype="multipart/form-data"> <input type="file" name="filename"> <input type="hidden" name="action" value="convert.jar"> <input type="submit" value="Upload"> </form> </body> </html> Now you need to change the value to the name of the jar-file being downloaded and that's it, voila! We get a list of contacts.
ID 190 NAME Max Smith PHONE +44234234234
ID 134 NAME Max Smith PHONE +4467652341
ID 137 NAME Alex Smith PHONE +4487653827
ID 193 NAME NeoQuestKey PHONE +78123123481
ID 4 NAME Andrey Petrov PHONE +79219325680
ID 11 NAME Max Sushinsky PHONE +79843214982
ID 13 NAME Arkady Mamontov PHONE 000001
ID 1 NAME Test Test PHONE 1234567
ID 7 NAME Petr Ivanov PHONE 2359631
ID 119 NAME Ivan Zhukov PHONE 89215897894
It is clear that you need to take the NeoQuestKey phone and count hash from it. Well, that's all, the flag is extracted, the task is completed!
To be continued...
While the audience listened to reports on cybersecurity and received gifts, participating in fun contests, our heroic participants of the competition very dynamically coped with the tasks. We congratulate the winners once again and remind you that the online stage of NeoQUEST-2015 is already nearing - with even more interesting tasks related to each other by a mysterious (as always, by the way) legend! Follow the updates on our website and blog Habrahabr.

Source: https://habr.com/ru/post/239089/
All Articles