Personal devices when working with corporate data: BYOD or bring your own device
One of the directions of development of modern IT is the concept of BYOD (Bring Your Own Device, or literally "Bring your own device"). The arsenal of the modern user consists of several devices: a laptop, tablet, phone; each of which has its own characteristics and can function on the basis of different operating systems. At the same time, it remains important to use personal devices of users to work with corporate data. If laptops and tablets on Windows 8 Pro can be connected to the domain without any problems, then with all other versions of operating systems, things are not so good. But access to corporate resources to the user, however, must be provided. This begins the choice of flour between the convenience of users and the security of internal information. Often attempts to find a solution come to a standstill. However, with the release of Windows Server 2012 R2 and Windows 8.1, various tools have appeared that will help in solving this eternal problem and in implementing the BYOD concept. A review of the new functionality I want to present to you in this article.

')
Traditionally, the device can be included in the domain or not. If the device is included in the domain, then there is no problem - it is completely controlled by the IT department of your organization. If the device is not included in the domain, then the administrator is faced with a difficult choice: to provide access to information to an absolutely unknown device or to provide access to a limited number of users and only limited information. One of the challenges with the release of Windows Server 2012 R2 was to provide the system administrator with the tools to solve this problem and implement the BYOD concept within the organization. To date, there are several possibilities for connecting to work files from the outside from a personal device:
Using VDI may be justified in some scenarios, but not all due to its cost, the need to work with peripherals, and so on. In this regard, in the framework of this article, we will consider the first three possibilities for connecting external files to work files from outside.
Tools that allow you to connect to work files from the outside, as well as help implement the BYOD concept in an organization, include Work Folders, Workplace Join, Windows Intune (device management tool), and Web Application Proxy (as mechanism for publishing resources and applications). Next, I will tell you about the principles of operation of each of these tools and the opportunities that they provide.
Work Folders provide the ability to synchronize work files on various personal and work devices. Work folders (Work Folders) are configured on the server in the organization, permanently stored on it and can be synchronized to various devices - both personal devices of the user and computers connected to the organization's domain network.
When using Work Folders, the user gets access to working documents, even if he is not connected to the network (especially convenient on business trips and other business trips, when access to the Internet may be restricted). Files stored in the working folder are synchronized to the server of the organization and from there to other working folders of this user on another device. Files are stored and transmitted in encrypted form.
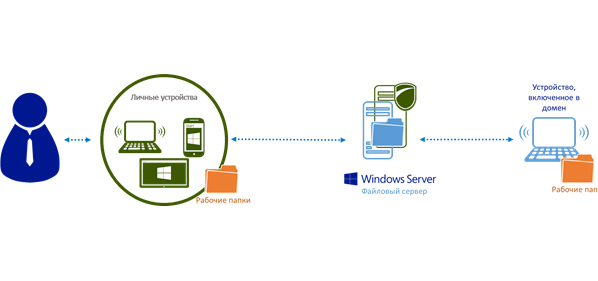
Work folders cannot be used to collaborate with multiple users on a single file. Versioning in working folders is not supported, therefore in case of simultaneous correction of the same file on different devices, all versions separately will be saved. In this situation, the user will have to manually review the changes and form a single version of the document.
The user can access the Work Folders by using the Control Panel and selecting the “Work Folders” option in the System and Security category .
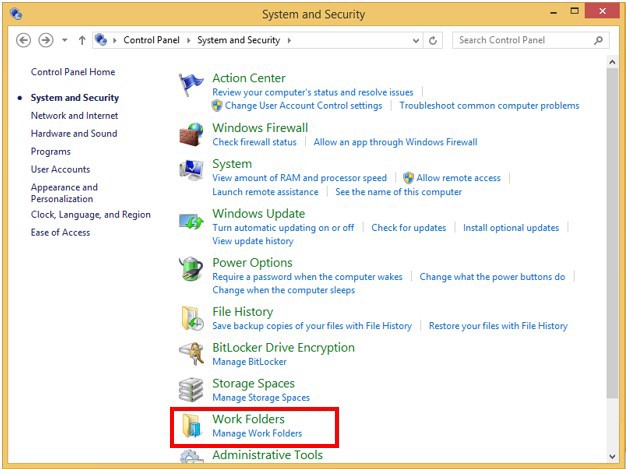
I will not dwell on the topic of working folders any longer, since I already wrote about what it is and how to set it up. Therefore, more detailed information you can see here .
Web Application Proxy appeared with the release of Windows Server 2012 R2 and provides various possibilities for users to connect to applications hosted on your corporate network from any device.
An organization's IT department can publish enterprise applications and, through the Web Application Proxy, provide end users with the ability to connect and work with these applications from their own devices. Thus, the user when working with internal applications is not limited to a computer that is issued to him at work and is included in the domain. Now the user can use his home computer, tablet or smartphone.
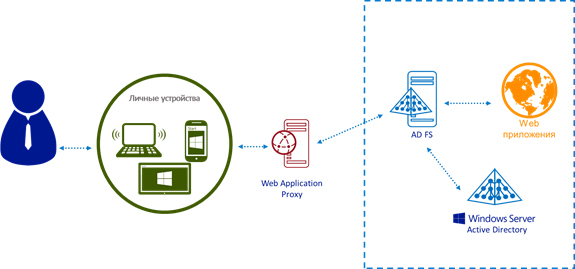
The Web Application Proxy should always be deployed on your server along with Active Directory Federation Services (AD FS, Active Directory Federation Services). When trying to access a corporate application from the outside, the request will go to the Web Application Proxy, which, in turn, will redirect it to the ADFS server. After that, the user will be prompted to go through the authentication process. The screenshot below demonstrates this process. Note that the user accesses the application at a specific address, however, in the process of gaining access, he is redirected to the ADFS server in order to authenticate.

The joint deployment of ADFS and Web Application Proxy will allow you to use various features of AD FS, for example, Single Sign On (Single Sign-On). Using the single sign-on feature allows the user to enter their credentials only once, and the next connection attempts will not require the user to enter a login and password. It is important to understand that providing access to internal applications from unknown devices is a source of great risk. Sharing the Web Application Proxy and AD FS for authentication and authorization ensures that only users with devices that are also authenticated and authorized can access corporate resources.
Workplace Join, by and large, is a compromise between complete control over a device that is included in the domain, and connecting to corporate resources from a completely unknown device. After the device is registered in the corporate network through Workplace Join, administrators can control the access of these devices to various corporate applications.
When a user's personal device is registered using Workplace Join, it becomes known to the network, and can be used to provide access to corporate applications. At the same time, this device remains the user's personal device and is not regulated by group policies applied by the organization. By the way, Workplace Join is the only solution for devices that, in principle, cannot be included in the domain (for example, devices running iOS).
A device registered using Workplace Join is used as the second authentication factor and allows single sign-on to corporate resources. More specifically, when registering, a certificate is loaded onto the device, which will be used as an additional authentication factor.

If the device is not registered, then the user each time you open the browser must enter a username and password to access the corporate application. If Workplace Join is executed on the device, then it is enough to log in only once; in all subsequent cases, the user will access corporate resources automatically. At the same time, the system administrator can monitor the registered devices, and in the event of a message about the loss of the device from the user can prevent this device from connecting to corporate applications, thereby securing the network.
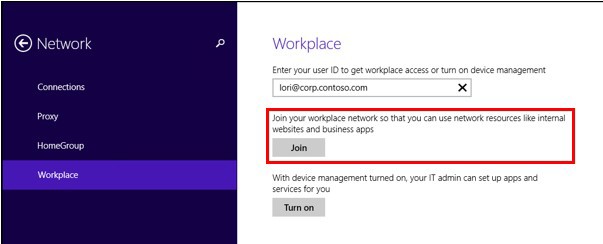
For an employee of the organization, setting up Workplace Join is as simple as possible. If Workplace Join is configured on the network (the theme of Workplace Join settings deserves a separate article that will appear in the near future), then the user just needs to go to PC Settings , select the Network item and select Workplace Join . The user needs to enter his working email and click Join .
Windows Intune is a cloud service that can help an organization manage and protect user devices. Since Intune is a cloud service, the administrator can get access to his control panel from almost any browser.
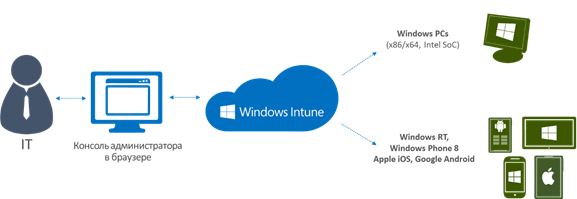
Windows Intune can be used as a separate tool for managing desktops and mobile devices from the cloud, as well as being integrated with System Center 2012 R2 Configuration Manager to configure device management policies on any operating system (Windows, Mac, Unix, or Linux).
What does an administrator get after he starts using Windows Intune? Administrators can apply different policies to user devices: set password parameters and encryption settings, manage system settings, determine which applications and games can be used on the device, and which are not; manage access to information, and more. As a tool for implementing all these actions, the administrator can use two tools: the Account Portal (Account Portal) and the Administrator Console (Administrator Console).
In turn, the user can install the Company Portal application on his device, which is available for free on four main platforms: Windows, Windows Phone 8.1, iOS, Android.
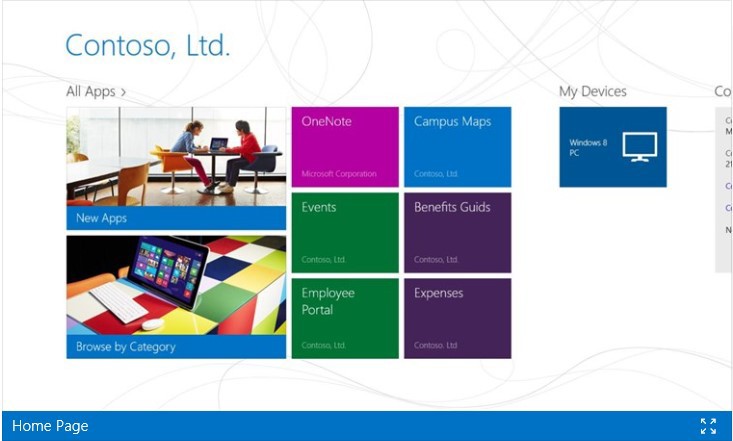
With the help of Company Portal, a user can install on his device the applications allowed by the administrator of the application he needs to work. Installing applications through Company Portal does not require a connection to the corporate network. In addition, using this application, you can connect or disconnect a device from Windows Intune.
Using Windows Intune, you can provide users of your corporate network with the ability to access corporate data and applications from any device without restricting them to computers included in the domain. Using Windows Intune on managed computers, you can install various software necessary for the employee to work. But more importantly, Windows Intune allows you to disable your device from accessing corporate information if it has been lost or stolen. Thus, Windows Intune solves not only the problem of managing users' personal devices, but also increases the level of network security. I already mentioned that Intune can be integrated with System Center Configuration Manager to configure device management policies. With SCCM, you can designate a device as personal or corporate; manage VPN profiles, manage and distribute certificates, configure Wi-Fi connection settings, manage email account settings, etc.
In order to enable the device management function, the user needs to enter the PC Settings , select the Network item and the Workplace item. The user needs to enter his working email and click not Join (you need to use it if you want to configure the Workplace Join function), a Turn On .

The development of the concept of BYOD is gaining momentum. And now you cannot blindly force users to use only issued corporate devices for work. New features of Windows Server 2012 R2 simplify the implementation of the BYOD concept in an organization. In this article, we briefly reviewed each of the new features and will discuss in more detail each in the following articles. Also, for those who want to learn more about the features of Windows Server 2012 R2 listed in the article, I recommend watching the course “Everything about Windows Server 2012 R2” on the MVA portal (Microsoft Virtual Academy). The course includes demos, so you can see how these functions work.
I hope the information was helpful! Thanks for attention!

')
Traditionally, the device can be included in the domain or not. If the device is included in the domain, then there is no problem - it is completely controlled by the IT department of your organization. If the device is not included in the domain, then the administrator is faced with a difficult choice: to provide access to information to an absolutely unknown device or to provide access to a limited number of users and only limited information. One of the challenges with the release of Windows Server 2012 R2 was to provide the system administrator with the tools to solve this problem and implement the BYOD concept within the organization. To date, there are several possibilities for connecting to work files from the outside from a personal device:
- Connecting via a browser to a corporate application published for access from outside;
- Installing the application from the corporate application portal on devices (personal and work);
- Synchronize work files across devices.
- Using VDI (Virtual Desktop Infrastructure)
Using VDI may be justified in some scenarios, but not all due to its cost, the need to work with peripherals, and so on. In this regard, in the framework of this article, we will consider the first three possibilities for connecting external files to work files from outside.
Tools that allow you to connect to work files from the outside, as well as help implement the BYOD concept in an organization, include Work Folders, Workplace Join, Windows Intune (device management tool), and Web Application Proxy (as mechanism for publishing resources and applications). Next, I will tell you about the principles of operation of each of these tools and the opportunities that they provide.
Work Folders
Work Folders provide the ability to synchronize work files on various personal and work devices. Work folders (Work Folders) are configured on the server in the organization, permanently stored on it and can be synchronized to various devices - both personal devices of the user and computers connected to the organization's domain network.
When using Work Folders, the user gets access to working documents, even if he is not connected to the network (especially convenient on business trips and other business trips, when access to the Internet may be restricted). Files stored in the working folder are synchronized to the server of the organization and from there to other working folders of this user on another device. Files are stored and transmitted in encrypted form.

Work folders cannot be used to collaborate with multiple users on a single file. Versioning in working folders is not supported, therefore in case of simultaneous correction of the same file on different devices, all versions separately will be saved. In this situation, the user will have to manually review the changes and form a single version of the document.
The user can access the Work Folders by using the Control Panel and selecting the “Work Folders” option in the System and Security category .

I will not dwell on the topic of working folders any longer, since I already wrote about what it is and how to set it up. Therefore, more detailed information you can see here .
Web Application Proxy
Web Application Proxy appeared with the release of Windows Server 2012 R2 and provides various possibilities for users to connect to applications hosted on your corporate network from any device.
An organization's IT department can publish enterprise applications and, through the Web Application Proxy, provide end users with the ability to connect and work with these applications from their own devices. Thus, the user when working with internal applications is not limited to a computer that is issued to him at work and is included in the domain. Now the user can use his home computer, tablet or smartphone.

The Web Application Proxy should always be deployed on your server along with Active Directory Federation Services (AD FS, Active Directory Federation Services). When trying to access a corporate application from the outside, the request will go to the Web Application Proxy, which, in turn, will redirect it to the ADFS server. After that, the user will be prompted to go through the authentication process. The screenshot below demonstrates this process. Note that the user accesses the application at a specific address, however, in the process of gaining access, he is redirected to the ADFS server in order to authenticate.

The joint deployment of ADFS and Web Application Proxy will allow you to use various features of AD FS, for example, Single Sign On (Single Sign-On). Using the single sign-on feature allows the user to enter their credentials only once, and the next connection attempts will not require the user to enter a login and password. It is important to understand that providing access to internal applications from unknown devices is a source of great risk. Sharing the Web Application Proxy and AD FS for authentication and authorization ensures that only users with devices that are also authenticated and authorized can access corporate resources.
Workplace join
Workplace Join, by and large, is a compromise between complete control over a device that is included in the domain, and connecting to corporate resources from a completely unknown device. After the device is registered in the corporate network through Workplace Join, administrators can control the access of these devices to various corporate applications.
When a user's personal device is registered using Workplace Join, it becomes known to the network, and can be used to provide access to corporate applications. At the same time, this device remains the user's personal device and is not regulated by group policies applied by the organization. By the way, Workplace Join is the only solution for devices that, in principle, cannot be included in the domain (for example, devices running iOS).
A device registered using Workplace Join is used as the second authentication factor and allows single sign-on to corporate resources. More specifically, when registering, a certificate is loaded onto the device, which will be used as an additional authentication factor.

If the device is not registered, then the user each time you open the browser must enter a username and password to access the corporate application. If Workplace Join is executed on the device, then it is enough to log in only once; in all subsequent cases, the user will access corporate resources automatically. At the same time, the system administrator can monitor the registered devices, and in the event of a message about the loss of the device from the user can prevent this device from connecting to corporate applications, thereby securing the network.
For an employee of the organization, setting up Workplace Join is as simple as possible. If Workplace Join is configured on the network (the theme of Workplace Join settings deserves a separate article that will appear in the near future), then the user just needs to go to PC Settings , select the Network item and select Workplace Join . The user needs to enter his working email and click Join .

Windows intune
Windows Intune is a cloud service that can help an organization manage and protect user devices. Since Intune is a cloud service, the administrator can get access to his control panel from almost any browser.

Windows Intune can be used as a separate tool for managing desktops and mobile devices from the cloud, as well as being integrated with System Center 2012 R2 Configuration Manager to configure device management policies on any operating system (Windows, Mac, Unix, or Linux).
What does an administrator get after he starts using Windows Intune? Administrators can apply different policies to user devices: set password parameters and encryption settings, manage system settings, determine which applications and games can be used on the device, and which are not; manage access to information, and more. As a tool for implementing all these actions, the administrator can use two tools: the Account Portal (Account Portal) and the Administrator Console (Administrator Console).
In turn, the user can install the Company Portal application on his device, which is available for free on four main platforms: Windows, Windows Phone 8.1, iOS, Android.

With the help of Company Portal, a user can install on his device the applications allowed by the administrator of the application he needs to work. Installing applications through Company Portal does not require a connection to the corporate network. In addition, using this application, you can connect or disconnect a device from Windows Intune.
Using Windows Intune, you can provide users of your corporate network with the ability to access corporate data and applications from any device without restricting them to computers included in the domain. Using Windows Intune on managed computers, you can install various software necessary for the employee to work. But more importantly, Windows Intune allows you to disable your device from accessing corporate information if it has been lost or stolen. Thus, Windows Intune solves not only the problem of managing users' personal devices, but also increases the level of network security. I already mentioned that Intune can be integrated with System Center Configuration Manager to configure device management policies. With SCCM, you can designate a device as personal or corporate; manage VPN profiles, manage and distribute certificates, configure Wi-Fi connection settings, manage email account settings, etc.
In order to enable the device management function, the user needs to enter the PC Settings , select the Network item and the Workplace item. The user needs to enter his working email and click not Join (you need to use it if you want to configure the Workplace Join function), a Turn On .

The development of the concept of BYOD is gaining momentum. And now you cannot blindly force users to use only issued corporate devices for work. New features of Windows Server 2012 R2 simplify the implementation of the BYOD concept in an organization. In this article, we briefly reviewed each of the new features and will discuss in more detail each in the following articles. Also, for those who want to learn more about the features of Windows Server 2012 R2 listed in the article, I recommend watching the course “Everything about Windows Server 2012 R2” on the MVA portal (Microsoft Virtual Academy). The course includes demos, so you can see how these functions work.
I hope the information was helpful! Thanks for attention!
Source: https://habr.com/ru/post/238557/
All Articles