Let me give you back?

The main enemy of hackers (we will not argue about the original meaning of this word - now we will use this term to designate those who create / spread malware) are antiviruses, which with varying degrees of success detect their crafts and delete. One way to prevent the detection of illegal activities and the utilities used for this is to attempt to “force” legal software to serve its purposes. For example, why download something from the Internet yourself, at the risk of falling out of favor with a firewall or heuristics (not to mention signatures), if you can run wget with parameters? Why build your mail sending, if there is a blat? Why do long and hard to do the remote monitoring utility for a computer when there are free remote administration programs?
Recently, the Remote Manipulator System (RMS) program, produced by TektonIT, has earned the greatest popularity among the motley hacker brotherhood.
There are several reasons for this, but it is quite difficult to go on to list them - something that they would not perceive as an advertisement, we simply list the main functions:
')
1. The possibility of hidden installation and operation;
2. Communication through the server, and not to IP directly;
3. The ability to manage a large fleet of computers;
4. Software legally, has EDS;
5. The files of the program itself are detected by a small number of antiviruses - you do not even need to encrypt anything (5-20, depending on the version);
6. Ease of use at the middle school level.
In short, the technological essence of the work is as follows:
1. RMS files are installed on the victim's computer in stealth mode, sometimes even with the help of an official installer, although more often “manually” - the script puts the files in the right folder and starts their “silent” registration or registers them itself;
2. The owner comes to the mail ID and password;
3. In the botnet +1.
This is implemented as a SFX archive with a bat file that does everything or as an NSIS installer. To help beginners there are many articles with beautiful screenshots, which describes in detail how to create such an archive ... the batch file and the files themselves are naturally attached to the article. For the gifted, even video manuals (in large quantities) are removed and “builders” are made - a beautiful window where you need to enter your data (where the password and ID should be sent) - and everything will be done by itself.
In the minds of some intellectuals so firmly established that RMS is a hacking utility that they even ... in general, see for yourself:

On the other hand, the barricades are not all calm either - nerve admins and users storm support with questions “how long ?!”, then one antivirus will remove something, then another, then users suspect the admin. The support throws up his hands, offers to write directly to antiviruses, they say, the more they write, the sooner they will remove the false positive. Then they release a new version - there are no detections there, but after a while they appear again and everything returns to normal.
But there is also a third party barricade, which usually no one notices and does not consider as a party at all, because the wall is generally two sides, as is commonly believed, but everything is not so simple, there are still antiviruses that keep all-round defense: you need to protect users from angry hackers, you need to communicate with managers / lawyers from TektonIT and dismiss admins asking about inconvenience, say our office does not pay for the antivirus so that it can be demolished by legal software.
Currently, anti-virus science has reached the following heights:
1. In the name of the detective, to the best of imagination, they try to convey information about what it is (there are the following component parts of the names: RemoteAdmin, RMS, Riskware, RemoteUtilities, not-a-virus ... etc, and even three of such hints some manage to put in the name of the detector);
2. Alerts on similar software have a softer color-sound scale, in order not to take the user out of the state of mental balance;
3. Detection of this class of software can be completely disabled in the settings of the antivirus;
4. And yet - this is a purely “national” problem - this is usually not extended beyond the CIS. The Russian program, builders in Russian, is distributed by spam and social engineering, so the majority of foreign antivirus companies simply do not know what is happening here. Of course, files come to their virlaby (from the same virustotal), but they, apparently, have a poorly visible situation in our region, but Russian antivirus programs and some foreign ones (who have a large staff in our country) do their best spoil the blood of virus makers.
This is how things work with the NSIS builder:
In this builder, you don’t even need to enter anything - there is no reference to the mail, ID + pass are generated at the assembly stage and saved to a file. This work to reduce the number of signature-based detectors uses a fairly popular method - creating an archive under a password: all RMS files are in a password-protected archive, and when installed in the command line parameters, the archive is given a password to the archiver. Such a trick allows you to bypass the scan of the file on the disk (usually antiviruses do not get passwords), but (if there is a detector) during installation, the files will be unpacked and detected by the anti-virus monitor (if enabled, of course).
You can put patched versions of RMS as a separate class - when a file is examined by reversing and an extra functionality is “cut out” (knocked, jumped), for example, displaying a window to the user that access data on his computer will be sent to such e- mail address (starting with one of the versions such functionality appeared). Sometimes patching is used to knock down antivirus detectors and to disguise (versioninfo, lines in the file are interrupted), as a result, the file after a while begins to be detected not as a Remote Tool (these detections are mentioned above), but as a trojan or backdoor, and evilly not 10 antiviruses, but 30 ... after all, the signature on the file flies in such a case and this is obtained from the point of view of an abstract virlab in a vacuum already a common malware.
In some cases, the builder serves only to write to the text ini-file with the settings, and all the work on patching / configuring the build itself has already been done by the author.
Here is an example of such a builder:
Sometimes crutches can be used in the form of scripts that monitor the appearance of windows from the RMS for their instant concealment and even in the form of a dll library that will put the necessary hooks in the process and will change the logic of the process work in the field of window display. These two-line scripts are practically not detected, and the library is detected by more than 30 antiviruses, which greatly jeopardizes the whole operation, because it is used extremely rarely.
If you search the search engine for the names of the detectors on the RMS, you can see that for the general public (and not for manual infection using social engineering cheaters in the chat), combinations are used that are not derived from public builders, but from articles about this - judging by such assemblies are sold to forums and even the builders to them, their essence is that the installation produces a bat-file - installs in a hidden mode a legal msi-installer. Accordingly, the antivirus has only two possibilities to stop it - to detect the bat-file (and it is easy to change them and “reset” the detections) and the RMS files themselves. If the antivirus does not detect the final files, and when such a Trojan elephant hit the computer on the batnik, it was all in vain - even if it starts to be detected with the next updates, it will be late, because for RMS it is no longer needed and it can be scrapped with a clear conscience.
It should be noted that this tool is used both by novice hackers (schoolchildren, script kiddies, etc.), and “working on an ongoing basis”, for those who are bread. Such accesses are sold on the forums in the hundreds at ridiculous prices:
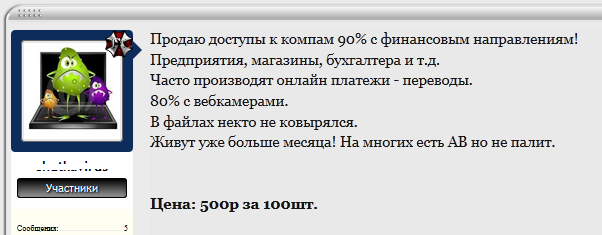
Such attacks are used not only for the extraction of already familiar profit (passwords, money), but also for selling to people with an excess of some kind of hormones - access to the computers of girls, who are often in front of the computer in a nude form.
Already in the process of writing this article, Kaspersky Lab published on September 11 “Investigation of incidents: theft in the RBS system” , which gave us inspiration, they say “the right way to go, comrades!”, Because it was the malware class we studied that was they were infected. Therefore, we decided to get the described malware and supplement the Kaspersky Lab article with new buns ...
The described distribution of the exploit was made in January 2014. When the document was opened, the file was downloaded and launched, which was the 7z-sfx archive, which unpacked the archive with the COyNldyU password, transferring it with the command line (the LC could have a different build of this malware, a slightly different modification, but they are extremely close relatives — all of the behavior and names match almost completely). After that, the bat-file was launched, extracted from the password-protected container, which installed the RMS (patched) files into the system. This batch file is interesting because it worked extremely correctly - previously tried to remove itself from the system by hitting processes and shutting down / removing services, and also checked the system rights, in the event of a shortage of which could be installed in% APPDATA% \ Microsoft \ System, and write settings in HKCU \ SOFTWARE \ System \ System \ Install \ Windows \ User \ Server \ Parameters.
Also carried out the patching and update of the Windows RDP (apparently, so that when the current user is connected remotely, it does not throw out), by running a heap of console utilities in hidden mode.
In conclusion, we would like to introduce the situation with detections.
Nominations are as follows:
1. Detection of the rutserv.exe file from different versions of RMS. In order not to help the hackers in this matter (it will be too clear which version shows which quantity and which antivirus it detects) we do as follows: If the antivirus detects at least 75% - it’s plus, less than half - the minus, the remaining interval will give ±;
2. Detection of the file from under the second builder (it is always the same, and the config is different);
3. Detection of bat-files to install RMS into the system - they were taken from various articles about the self-assembly of this malware and several from forums where, on the contrary, they try to reverse / get rid of this infection and upload files. Registration of results - similar to the first paragraph;
4. Bat-file described in the article from KasperskyLab.
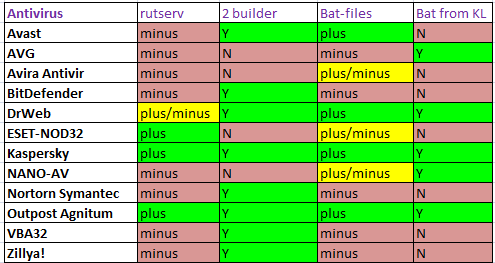
Actually, the image shows the results, but we will try to give them our own interpretation:
1. As expected, the three Russian antiviruses showed very good results, which indicates their close attention to this class of malware. Kaspersky traditionally shows good results, Dr.Web is almost completely focused on the domestic market (especially government offices and big business), the Outpost team - the creators of the legendary firewall, as it turned out, are also stubbornly struggling with the adversary ... And we offer foreign antivirus programs "to increase three times extreme concern. "
2. Comrades (VBA32) from the fraternal Republic of Belarus have somehow a little strange attitude to this family. It is possible that inadvertently ..., but if we want to play conspiracy, then an interesting puzzle will be formed: firstly, this antivirus is purely internal - state. enterprises there, and secondly, their KGB has already been noticed in the love of infecting its citizens with the RMS program. Whether these points are related to each other is an open question, the accuracy of the second point was also not notarized, but we still recommend reading the material by reference at least because of the comments of the “programmer-cracker” - in the light of all of the above, you can evaluate carries nonsense. Their assembly of RMS (since they started talking about it) also does not constitute anything outstanding: archive + crutch + archive + batch file + bulk RMS files.
Epilogue
Not a conclusion, but an epilogue. We do not know which conclusions can be drawn from this. If it was a diploma / abstract, then, according to the rules, we would have drifted along the tree, and so ... From what we learned, we tried to tell the most interesting and useful things so that the reader would not fall asleep - diluted with funny pictures and tried not to overload the article terminology and narrow moments (ala ACM code listings, screenshots with underscores of important places in red). Our words about spying through the camera for not very well-dressed persons (and not only) of the weaker sex, we still did not dare to illustrate with screenshots. We hope that this article did not become less informative and interesting.
Thanks for attention.
Source: https://habr.com/ru/post/238495/
All Articles