In search of free tickets, the study of the game Aeroflot
It all started with the fact that I received a link to the Aeroflot promotional website. The promotion consists of passing a small flash game and getting bonus miles. The top prize of 150,000 miles is given to the player who ranked first in the ranking. Actually, the principle of forming the rating and caused my interest in this action.

As everyone is well aware, the code of flash applications is executed on the client side, so protection against cheating is a very difficult task. In fact, the only correct solution is to transfer all game mechanics to the server side, and the flash application performs the role of a client to the API.
')
Let's see how to cope with this task in Aeroflot.
To start, start the game with an open developer console in Google Chrome. And ... apparently, everything will be boring. As it turned out, the request to the server is sent only once at the end of the game.

The data in the query is suspiciously similar to base64, but the conversion from this encoding only leads to a set of binary data. This means that the request is encrypted somewhere in the depths of the client. Unfortunately, or fortunately, swf files have never been resistant to decompilation.
Literally 10 seconds after viewing the ActionScript code, this fragment appears:
Yes, this is a banal XOR encryption, which means that it was possible not to get involved in decompiling, to recover the key of such a cipher in a matter of a few seconds. But if you still understand to the end, then the key here consists of two parts: the first one is hard-coded in the function, the second part is obtained from the SWF initialization parameters.
That is, the full key - aef-gamec958c089505d321994578a12fabbe73d almost all lies in plain sight, right in the page code.
By the way, apparently, the developers even were too lazy to independently implement the encryption algorithm and used the ready-made solution .
The result of the decryption with the voiced key:
Formatting added for readability.
As a result, anyone can post any rating. I don’t know how the organizers plan to separate honest participants from cheaters, but personally I have no longer any desire to participate in this action.
PS
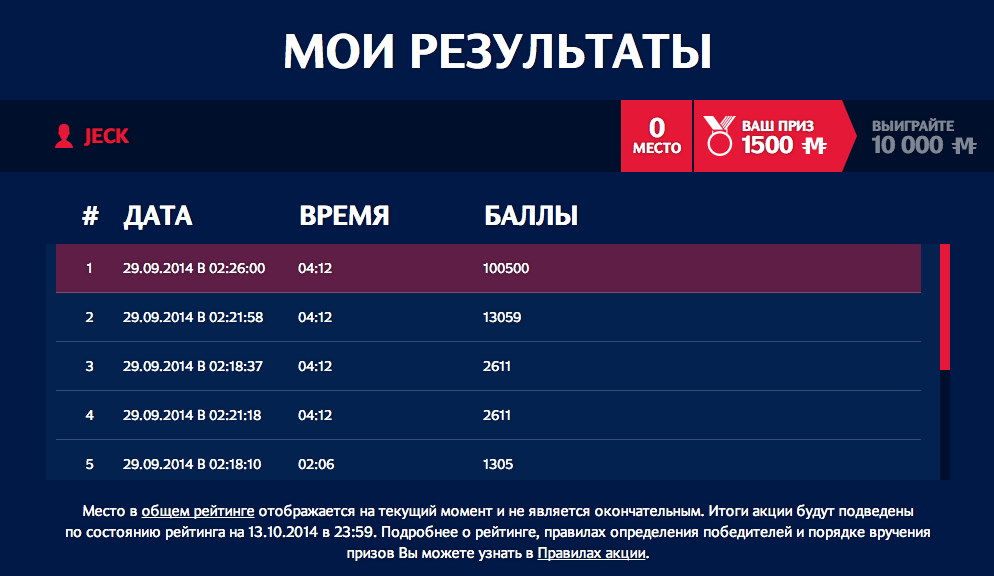
I do not have an Aeroflot Bonus card, so the results will not affect the overall rating.

As everyone is well aware, the code of flash applications is executed on the client side, so protection against cheating is a very difficult task. In fact, the only correct solution is to transfer all game mechanics to the server side, and the flash application performs the role of a client to the API.
')
Let's see how to cope with this task in Aeroflot.
To start, start the game with an open developer console in Google Chrome. And ... apparently, everything will be boring. As it turned out, the request to the server is sent only once at the end of the game.

The data in the query is suspiciously similar to base64, but the conversion from this encoding only leads to a set of binary data. This means that the request is encrypted somewhere in the depths of the client. Unfortunately, or fortunately, swf files have never been resistant to decompilation.
Literally 10 seconds after viewing the ActionScript code, this fragment appears:
public static function prepareForSend(param1:Object, param2:String) : String { return Xor64.encode(JSON.stringify(param1), "aef-game" + param2); } Yes, this is a banal XOR encryption, which means that it was possible not to get involved in decompiling, to recover the key of such a cipher in a matter of a few seconds. But if you still understand to the end, then the key here consists of two parts: the first one is hard-coded in the function, the second part is obtained from the SWF initialization parameters.
// main.as this._token = stage.loaderInfo.parameters["token"]; // http://aeroflotbonus15.ru/media/js/aef.js start : function( token, authState, connector, autoStart ){ . . . this._token = token; . . . }, . . . AEF.flashController.buildFlash({ token: this._token, connector: this._connector }, this._lang ); . . . // http://aeroflotbonus15.ru/ AEF.start('c958c089505d321994578a12fabbe73d', true, "http://aeroflotbonus15.ru/api/", false, 'ru'); That is, the full key - aef-gamec958c089505d321994578a12fabbe73d almost all lies in plain sight, right in the page code.
By the way, apparently, the developers even were too lazy to independently implement the encryption algorithm and used the ready-made solution .
The result of the decryption with the voiced key:
{ "result":{ "cities":11, "miles":749.9018522566122, "time":58356, "bonuses":2, "wins":6 }, "version":0.98, "bytes":7205605, "system":{ "cpuArchitecture":"x86", "screenDPI":72, "playerType":"PlugIn", "isDebugger":false, "version":"MAC 15,0,0,152", "manufacturer":"Google Pepper" }, "url":"http://aeroflotbonus15.ru/media/swf/game.swf?68" } Formatting added for readability.
As a result, anyone can post any rating. I don’t know how the organizers plan to separate honest participants from cheaters, but personally I have no longer any desire to participate in this action.
PS

I do not have an Aeroflot Bonus card, so the results will not affect the overall rating.
Source: https://habr.com/ru/post/238463/
All Articles