Access Control Tibbo Project System
Continuing the series of articles on how easy it is to assemble automation devices on the Tibbo Project System , we decided to talk about creating an access control system. In this market segment, a variety of devices are presented: from cheap and simple controllers to distributed flexible systems with a complex structure and high price. We will try to create our own universal controller with the basic functionality of the access control system. At the same time, given the flexibility of our hardware platform, you can build your own configurations of such devices for personal or commercial purposes, based on our version, the description of which is under the cut.
Access control is a key element in a complex of security systems. The installation of the system allows you to organize authorized access to protected objects, thereby ensuring the safety of wealth, security, control of the situation, access to paid facilities and services. We set ourselves the task of creating a universal access controller on the platform of the Tibbo Project System . The platform already has onboard Ethernet, memory, optional Wi-Fi, connectors for installing I / O modules. The presence of a universal case allows you to create finished products, not semi-finished products on the board. A full description of the platform is available in our review article . But first, it is necessary to understand what types of access control systems are divided into?
Local or network access control?
Access control systems are divided into two categories: autonomous and network. The first type does not require centralized management. Authorization of access is carried out either through a local database, or due to external information from the identifier. Autonomous systems are suitable for small objects: offices of small companies, classrooms, vehicles, access to paid services in entertainment centers. Network access control systems have a centralized management that allows you to quickly respond to the situation, integrate data into other systems, creating a single information space of the object. The principal differences between the network controller and the autonomous are: the presence of a network interface and a protocol for exchanging data with the central server. This type of system is suitable for installation on large objects, such as business centers, large companies with multiple access points, geographically distributed organizations, objects with multi-level access roles, as well as for small objects that require remote monitoring and control.
')
Requirement to the universal controller number 1: the ability to work in offline and network mode.
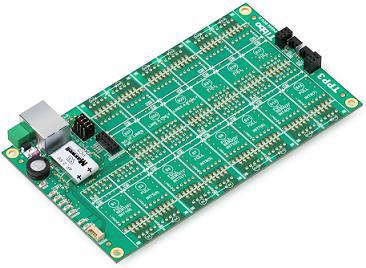
To implement this requirement, we chose the TPP3 board, which already has an Ethernet interface (optional Wi-Fi) for communication with the central server, as the basis for the future device. The presence of memory allows you to contain a local database of up to 2000 users and record event logs (up to 20,000 entries). We decided to make the controller at two points of passage. If necessary, the system can be easily ported to a smaller TPP2 board for monitoring one pass point or two points, but with limited connection of external sensors.
Identification device connections
In general, the tasks of the ACS controller are simple: identifying users on the principle of "one's own" / "someone else's", polling sensors for unauthorized entry, managing the input group, managing signaling.
By the type of user identification, access control systems impose different requirements. For access to the premises with an ATM, bank card readers are used. Business centers typically use RFID technology, magnetic stripe cards, barcode passes, iButton keys. For more stringent control, biometric readers are used. It is also possible to directly enter the access code from the keyboard. There are objects where multi-level authorization is required, then a combination of various identification methods is applied.
Requirement to the universal controller number 2: the ability to connect various identification devices.
We noticed that most external readers are connected via RS232 interface. Therefore , the input / output module (tibbit) # 01 was the first to be considered. The functionality of the module is simple - the transceiver / transmitter microcircuit converts the UART levels into the RS232 specification. What we need. We install four such modules on platforms S1, S5, S9 and S13: for connecting readers to the input and output to 2 points of passage. For ease of installation, clamps and DB9 connectors are provided. We chose the first option.
For identification devices that use other interfaces, we just change the corresponding Tibbits: for Wiegand, Clock / data - # 08, for RS485 - # 05. It is also possible to connect devices using the 1-Wire protocol using the PIC coprocessor for polling this bus (Tibbit # 31).
Input group and sensors
The control of the input group (barriers, turnstiles, electromagnetic or electromechanical locks), as well as alarm control, as a rule, is implemented with the help of a relay, which closes the external circuit of the actuators.
Requirement to the universal controller No. 3: the presence of normally-open relays to control the actuators.
For the base version of the controller, it was decided to apply Tibbit # 03-2 with two relays, switching current up to 1A (as can be seen from the module circuit, one relay has normally open and normally closed outputs, the second relay has only NO contacts). One relay is used to control the input group, the second for alarm. On the platforms S11 and S15 we install the selected tibbits, using the already installed terminals as a connector. If more current needs to be switched, other tibbits can be selected. For example, module # 06 is designed for currents up to 16A.
To monitor unauthorized access, use sensors of the “dry contact” type, motion sensors, window, volume breaking, etc. Typically, such sensors have a discrete output.
Requirement to the universal controller №4: The presence of discrete inputs for monitoring external sensors and connecting the door open button.
Direct I / O tibbits are commonly used to connect sensors. We will install tibbits 001 on the S3 and S7 platforms. Each tibbit has 4 lines of direct entry. This option is suitable for us, although you can choose other options: opto-decoupled inputs, inputs with a common "+", etc.
The fee is ready. S17-S23 sites were reserved for possible expansion of functionality. In our version of the controller, we additionally installed a Wi-Fi module in order not to pull the cable to the installation site. It remains to install a plate of vibration protection for reliability and place the assembly in a universal case . The presence of a cap with the possibility of signatures of conclusions will help future servicemen not to get lost in the conclusions of the controller.
For programming, it is enough to apply power to the board and connect it to our local network.
Firmware
The firmware logic is trivial, so it makes no sense to publish the source code. But I would like to draw attention to some of the nuances.
The first thing to note is that we create a universal controller with the ability to quickly change the functionality. Therefore, the program code tied to a specific Tibbit is rendered into separate libraries. This allows you to create your own configurations of the controller on the fly: increasing the points of passage, connecting additional sensors, changing the type of identification readers - you will not have to rewrite anything in the code, replacing a pair of constants and the new version of the controller is ready.
In addition to the hardware characteristics, the controller also needs to identify the functionality: storing event logs, data exchange with the server, security mode, remote configuration, support for modern data exchange protocols, etc. All this is also implemented in the base firmware.
The source code is open and distributed for free.
Soft
At the moment, there are two options for the network mode of the controller. The first is based on connecting to an external MySql database. When identifying the controller makes a request to the server and if the code is found in the database opens access to the object.
The second, more complex - the controller is controlled via the AggreGate platform. This allows you to remotely configure the controller, create complex branched access schemes, provide different types of reports, etc.
Open source and free programming allow you to connect the controller to almost any access control system.
The result is an access controller with the following characteristics:
- management of two passage zones;
- interfaces Ethernet, WiFi;
- connection of up to 4 external readers via RS232, RS485, Wiegand, Clock / data, 1-Wire, WiFi interfaces;
- 4 relays, optionally expandable to 10 relays;
- 4 dry contacts with the possibility of expansion;
- built-in audible indicator and LEDs for monitoring the status of the controller;
- adjustment of time of opening of the lock;
- built-in RTC. Calendar support;
- support up to 8 individual access schedules with the possibility of increasing this number;
- support for the validity of the card;
- control of re-entry or exit (antipassback);
- control of the prohibition of entry without a leader;
- code under duress;
- remote alarm notification (possible via SMS or email);
- the ability to customize the discipline of the passage;
- the ability to change the hardware configuration for the local project requirements;
- open source code that allows you to modify the firmware for unique tasks.
References:
Product page on our site.
Accounting for working time on TPS .
Overview of the Tibbo Project System .
Indoor weather station
Source: https://habr.com/ru/post/238277/
All Articles