IB in American. Part 1. What is NIST 800-53 and what do security controls look like?

* Guilty of disclosing confidential information! Your PHONE says only what YOU say ... *
The last time I covered the issue of providing information security in the United States almost a year ago in a material on the development of the Information Security Risk Management Framework . It is time to talk in more detail about how information security is arranged in America. At least on a paper published by quite a reputable organization NIST.
It is worth paying special attention to the fact that later we will focus on theoretical information security, the so-called best practices, which, as most security experts know, are rare in life. However, this does not diminish their importance in building a real information security system.
Links to all parts of the article:
IB in American. Part 1. What is NIST 800-53 and what do security controls look like?
IB in American. Part 2. Is it possible to learn more about NIST 800-53 and where does risk management go?
IB in American. Part 3. What is a basic set of controls and how to determine the criticality of systems?
IB in American. Part 4. We deal with the "fit" and "overlap" and complete this review.
Why America?
It's no secret that the United States is ahead of the rest of the world in many areas. This statement applies to a certain extent to the field of information security.
Historically, explosive growth and the spread of computer technology occurred in the United States. As well as the popularization of personal computers, the creation of the Internet
As the pioneers of the industry and the country with well-developed intelligence services, America has always had a certain advantage in the field of IT and, accordingly, information security. For example, it was with encryption algorithms at the dawn of their mass use in computers (for example, the DES encryption key's key length was 56 bits, but the export version of the algorithm for the whole world had a key limited to 40 bits long, guaranteeing insufficient security in the interests of the NSA) . The same applies to the processes of ensuring information security within the country. In the USA there are very serious requirements for information security and many interesting documents on information security have been developed.
Of course, it can be assumed that organizations themselves bother with the introduction of information security tools, but it seems to me that the stimulation, including legislative, comes from the special services and regulatory agencies, as well as under pressure from the public, seeking to protect themselves and their personal data.
By the way, it is interesting to pay attention to the following point: in the documents on information security prepared by American specialists, the term Nation is regularly found in the wording, i.e. nation. Documents are written taking into account the interests of the United States nation. This is in addition to the interests of individuals, organizations and the state. We do not immediately remember in what official document you can find a mention of the interests of the people of Russia. Here is such a small remark about the mentality.
')

* Before you go to the highway of information technology - think about the risks! *
Special publication code 53.
The following discussion focuses on one of the most applicable documents under conditions different from the laws and realities of the United States.
NIST - National Institute of Standards and Technology. A serious organization, on account of which an incredible number of publications on various topics. For publications on information security in NIST have identified a special series under the number 800. In this series already presented many documents of different directions. However, among all of them, I singled out the most interesting and, in my opinion, realistic publication of NIST Special Publication 800-53 “Security and Privacy Controls for Federal Information Systems and Organizations”. Translating literally we get "Security and Privacy Controls for Federal Information Systems and Organizations." This document has already gone through three processing and is now presented in 4 versions.
The essence of the document is to describe the security controls, as well as instructions on how to properly use them. It is worth noting that the document is very voluminous and the description of controls takes up almost 250 pages, and their total number totals several hundred (given the control enhancements, but more on that later)
Compared to the same ISO 27001, security controls are much more detailed compensatory measures, since ISO is still more focused on information security rather than specific compensatory measures.

* The reliable combination is safety and you. *
Overview of controls
The document is very well structured, it has a lot of illustrative examples, useful tables that simplify the work, etc. About this, Andrei Prozorov wrote in his blog a year ago, comparing the documents of FSTEC and NIST.
Naturally, all the controls in the standard are divided into families that correspond to various areas of information security. So, NIST operates with the following families of controls (my translation is my own, and therefore do not judge me. I myself prefer to use the original names in order to avoid unnecessary confusion and misinterpretations):
| Abbr | Control family | Adapted translation |
|---|---|---|
| AT | Awareness and Training | Awareness and learning |
| AU | Audit and Accountability | Audit and reporting |
| CA | Security Assessment and Authorization | Authorization and Security Assessment |
| CM | Configuration management | Configuration management |
| CP | Contingency planning | Business Continuity Planning |
| IA | Identification and Authentication | Identification and Authentication |
| IR | Incident response | Incident Response |
| MA | Maintenance | Service / Technical Support |
| MP | Media protection | Media protection |
| PE | Physical and Environmental Protection | Natural Disaster Protection and Physical Security |
| PL | Planning | Planning |
| PS | Personnel security | Staff security |
| RA | Risk assessment | Risk assessment |
| SA | System and Services Acquisition | Acquisition of systems and services |
| SC | System and Communications Protection | Protection of systems and communications |
| SI | System and Information Integrity | Integrity of systems and information |
| PM | Program Management | Management of the IB program |

* Do not play games with computer security! *
What is security control
Now is the time to talk about what security control is. Below is a typical control with a medium size description.
AU-3 CONTENT OF AUDIT RECORDS
There was no contact between the control system and the control system. the event.
This is an example of the need to follow the rules. flow control rules invoked. The event results are up to date.
Related controls : AU-2, AU-8, AU-12, SI-11.
Control Enhancements :
(1) CONTENT OF AUDIT RECORDS | ADDITIONAL AUDIT INFORMATION
The information system generates audit records
information: [Assignment: organization-defined additional, more detailed information].
Supplemental Guidance : Detailed information that organizations may consider in audit
records includes, for example, full-text recording of privileged commands or the individual
identities of group account users. Organizations consider limiting the additional audit
information to only for information audit requirements. This
it helps
it wouldn’t be possible.
(2) CONTENT OF AUDIT RECORDS | CENTRALIZED MANAGEMENT OF PLANNED AUDIT RECORD CONTENT
The information system provides centralized management and configuration of the content.
to be captured in audit records generated by [Assignment: organization-defined information
system components].
Supplemental Guidance : This is a control enhancement.
in audit records be configured from a central location (necessitating automation). Organizations
the centralized management and
configuration capability provided by the information system.
Related controls : AU-6, AU-7.
References : None.
Priority and Baseline Allocation :
P1 LOW AU-3 MOD AU-3 (1) HIGH AU-3 (1) (2)
The control description matches the following pattern.
First of all, there is the control family code and the number - AU-3. The following is the name of the security control: "Contents of audit records."
After that the following sections go:
- Control . A description of special actions or activities related to security that are performed in an organization or IP. For some controls, flexible configuration options are provided, allowing the organization to determine certain parameters related to control. For example, such a parameter may be the frequency of the audit, the retention period for logs, or the number of unsuccessful attempts to authorize a user. In this way, control can be tailored to specific needs, based on the security requirements of the organization’s business objectives, the results of risk assessment and risk acceptability, as well as the requirements of laws and regulators.
- Supplemental Guidance . Additional information for specific controls. May include explanatory information on the implementation or use of controls, etc. Reference may also be made to other related controls.
- Control Enhancements . This section presents the possibilities for “improving” the control by adding additional functionality to it or enhancing it. It turns out a kind of control that can only be used in conjunction with the main. In this example, the AU-3 (1) (2) control actually consists of the AU-3 control itself, defining the need to generate audit records and the basic composition of such records, the “gain” (1) of the list of additional information about the recorded events and the “gain” (2) describing the organization of centralized management of the content of audit records. As you can see, these extensions cannot be implemented without the control itself, however, it is not rational to allocate them to individual controls. It is also worth noting that these extensions also provide organizations with flexible configuration options by defining, for example, a complete list of necessary information in audit records and defining the list of IP, which audit records should be managed centrally.
- References . It contains references to legislation (of course American), standards, requirements of regulators, various guidelines, etc. For us, this is more background information.
- Priority and Baseline Allocation . The table provides information on the recommended priority when streamlining in the decision-making process on the implementation of controls (in the example above it is P1) as well as the initial distribution of control and its “gains” across the base sets for systems of various criticalities (which are a little further). The implementation priority allows the organization to implement controls in a more efficient and timely consistency, primarily implementing fundamental measures.

* Some professionals never reveal their secrets. *
Types of security controls
To streamline and provide a structural approach, the authors of the document provided for the separation of controls into different types, depending on their purpose:
- Common . Basic controls that can be inherited by different systems and have an impact beyond the scale of an individual IP. The system inherits the security control in case it performs its security function in this IS, however it was designed, implemented, evaluated, authorized outside this IS.
- System-specific . Control is the responsibility of the owners of a particular IP.
- Hybrid . Part of the control functions as a general, and part as a system of control. For example, IR-1 control may define incident response policies across the organization, but specific response procedures are defined for individual systems.
The authors introduce separation of controls into general, mixed and systemic, since in certain situations this can provide organizations with a reduction in the cost of implementation and evaluation processes, as well as ensure the integrity of the approach across the organization. This logical solution allows, for example, to simplify the process of determining responsibility for a particular control and to determine the areas in which control will effectively carry out its work.
And now a brief comparison of NIST 800-53 and ISO 27001
The ISO 27001 standard is much more widely known in the open spaces of Russia and almost everyone has heard about it, probably, whose work is more or less closely related to information security. This standard describes the requirements for an information security management system. In view of the popularity (or popularity) of the ISO standard, below I will give a brief comparison of it with the NIST document in question, in order to present it to the reader a little more clearly.
However, anticipating the fair objections of specialists, I want to note that I am not directly trying to compare these two standards with each other, this is not so. They are written for different purposes and complement each other rather than contrasted. However, the detail provided by NIST is commendable beyond doubt.
In order to visually compare the ratio of safety controls from NIST SP 800-53 and ISO / IEC 27001, below are two fragments from the tables with the compliance of these standards. (The table is taken from the NIST 800-53 document and excludes the existence of my subjective judgments about the ratio of controls of the two standards).
Table 1. On the left are the ISO 27001 controls, on the right are the corresponding controls from NIST 800-53

Table 2. Reverse Match:
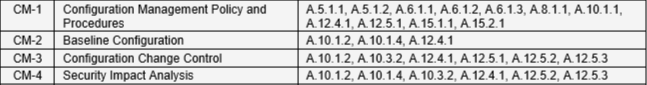
These tables clearly show that the ISO controls are more general in nature and include several more precisely formulated controls from NIST. Or, to put it another way, it can be concluded that, as a result of its specifics, one NIST control can serve the purposes described in several ISO controls of a high level nature. I hope not very difficult to explain. The question of which of these tablets can be made the opposite conclusion I leave on the conscience of the reader. As such assumptions disappear even after a cursory acquaintance with the standards and description of controls.
This is what a typical ISO 27001 security control looks like. In particular, this covers the scope of the AU-3 “Content of audit records” given as a sample on which we studied the control structure. Compare this description with what the NIST control described above describes.

What's next
In the next article I will try to describe in a simple form the process of working with security controls presented in the NIST 800-53 standard.
I hope someone will be useful or at least interesting.
Source: https://habr.com/ru/post/238245/
All Articles