Attacks on SS7: yesterday for special services, today for all
In late August, the Washington Post newspaper published a booklet of the American company Verint, which offers its customers Skylock service to track mobile network subscribers in different countries of the world - without the knowledge of the subscribers themselves and operators. Although offers of location services have long been found on the Internet, the case of Verint is perhaps one of the first when such services are offered quite officially and at the global level.
How is this possible? In response to stories about mobile surveillance, most often a version is put forward of complex technologies that can only be used by special services. In practice, everything is easier. A telecommunication network consists of a set of subsystems of various technological levels, and the level of security of the entire network is often determined by the level of the weakest link.
')
In particular, the process of establishing voice calls is still based on SS7 technology, which dates back to the 70s of the last century. In the early 2000s, the SIGTRAN specification was developed, allowing SS7 messages to be transmitted over IP networks. All the security flaws of the upper layers of the SS7 protocols were inherited. As a result, attackers have the ability to uncontrolledly send, intercept and modify SS7 protocol messages, carrying out various attacks on mobile networks and their subscribers.
One of the first public reports on SS7 vulnerabilities was sounded in 2008 at the hacker conference of the Chaos Computer Club, where the German researcher Tobias Engel showed the technique of spying on subscribers of mobile networks. However, in a professional environment, these vulnerabilities have been known before - since 2001 . Even then, the governments of some countries knew about these opportunities. So, in the book by Thomas Porter and Michael Gaf “How to bypass VoIP protection” (How to Cheat at VoIP Security) cites from a report of one of the US departments, which says that “the administration of the US President is seriously concerned about the high threat level of SS7-based attacks” .
A new surge of public concern occurred in 2013, when former CIA officer Edward Snowden revealed to the world the story of total surveillance by the US National Security Agency for citizens. Among the revelations of Snowden, SS7 vulnerabilities have resurfaced as one of the techniques used by the NSA. After that, it became known about the existence of private companies that offer such services at the global level, as already mentioned SkyLock:

As noted by the Washington Post, Verint does not use surveillance against US and Israeli citizens, "but a number of other similar services operating in Switzerland and Ukraine are not subject to such restrictions."
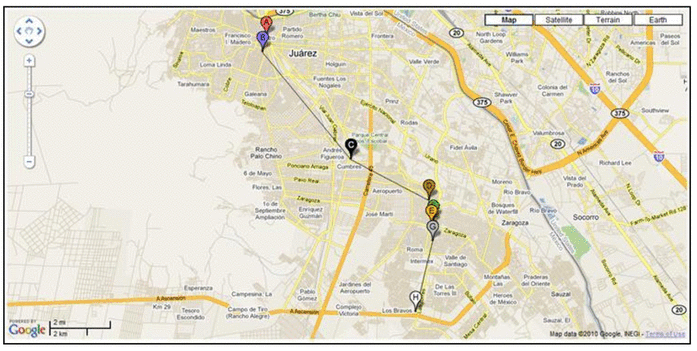
The above quote is one of the possible explanations of a whole wave of scandals related to the publication of telephone recordings in Ukraine. In June 2014, the National Commission for Regulation of Communications and Informatics of Ukraine reported cases of interception of MTS-Ukraine subscribers through a server allegedly owned by the Russian subsidiary of the operator Tele2:
According to the experts of Positive Technologies, the wiretapping algorithm used in this case is a combination of attacks that were reviewed at the PHDays IV conference on practical safety, as well as in selected publications of our blog. Now all these attacks are collected and described in more detail in the new study "Vulnerabilities of mobile communication networks based on SS7." Read the full text of the study here: www.ptsecurity.ru/lab/analytics
The materials presented in this report were collected in 2013 and 2014 in the course of consulting work on the analysis of the security of large mobile operators. In the course of this study, Positive Technologies experts were able to implement such attacks as disclosing the subscriber's location, disrupting subscriber accessibility, intercepting SMS messages, faking USSD requests and transferring funds using them, redirecting voice calls, eavesdropping conversations, and disrupting the mobile switch.
At the same time, it was demonstrated that even telecom operators included in the top ten world leaders are not protected from such attacks. And an attacker today does not need sophisticated equipment to carry out these attacks: the study used a node based on a regular computer running the Linux operating system, with the SDK installed to form SS7 packets - these programs are available for free download on the Internet.
Solutions to the problem are proposed in the final chapter of the study . In addition, if you have any questions about this study, you can ask the authors of the report on the webinar, which will be held on October 2 at 14:00 on the company's website.
The webinar is free, but you need to pre-register:
www.ptsecurity.ru/lab/webinars
Source: https://habr.com/ru/post/237981/
All Articles