Making a universal key for intercom
The title was too loud - and the key is not so universal, and the intercom does not give in to any. Anyway.
We will talk about intercoms, working with 1-wire DS1990 tablets, like this:

On the Internet you can find a lot of materials on how to read information from them. But these pills are not only read-only. It is common for a person to lose keys, and today a stall with DS1990 cloning services can be found in any underground passage. For recording, they use blanks that are compatible with the original keys, but have additional commands. Now we will learn how to program them.
')
Why do you need it? If we discard the obviously bad options, then the simplest thing is to reprogram the cloned tablets that have accumulated and become unnecessary from the old intercom, replaced with a new one, from the entrance of the rented apartment, where you no longer live, from work, where you no longer work, etc.
At once I will make a reservation that in the description I will omit some points that are obvious to most of those who are “in the subject line”, but perhaps not allowing a simple person who has come here from the search engine to repeat the procedure. This is done on purpose. Though I am for openness of information, and I believe that information about all vulnerabilities should be communicated to the public as quickly as possible, but still I don’t want anyone who can easily come to my doorway.
As you know, DS1990 is characterized, in general, by one parameter - its own identification number. It consists of 8 bytes and deposited on the surface of the tablet. And it is issued in response to a request for 1-wire. In fact, one of these bytes is a device type identifier, another one is a checksum, but for us this is all not important. All keys known to him are registered in the memory of the intercom, only the company managing the intercom can change this set. But in addition to the keys, clearly recorded in the memory, the intercom sometimes reacts to the so-called master keys, the same for the doorphone of this manufacturer, this series, this installer. Master key codes are kept secret, but sometimes they leak. In five minutes of googling, you can find about 20 master keys from various intercoms. I have a “visit”, so the choice fell on the key 01: BE: 40: 11: 5A: 36: 00: E1.
The blanks for which the keys are cloned come in different types. In our city the most common - is TM2004. According to the description, they support finalization, after which they lose the possibility of rewriting and function as the most common DS1990. But for some reason, craftsmen who make copies do not always finalize. Perhaps because the majority of programmers on the market have been bought for a long time and do not have such a function, perhaps because the finalization requires an increased (9V) voltage. I do not know. But the fact remains that of the 4 keys on which I experimented, only one was finalized. Others easily allowed to change their code for whatever you want.
We will assemble the programmer on Arduino Uno, which is suitable for similar purposes of prototyping and assembling disposable crafts. The simplest scheme, 1-Wire for that and 1-Wire.
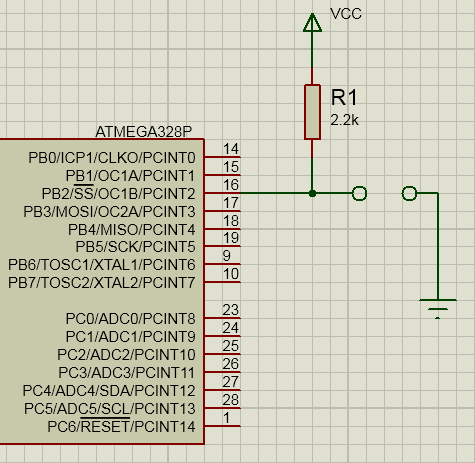
The build time of the device on the brainboard does not exceed five minutes

Sketch code. The recording algorithm itself is taken here - domofon-master2009.narod.ru/publ/rabota_s_kljuchom_tm_2004/1-1-0-5
There, however, it is written that you can write all 8 bytes in a row, but it did not work for me. Therefore, each byte is written separately, through its own command 0x3C.
Once launched, the program polls the 1-Wire interface once a second and issues the code read from it to the serial port. If this is FF: FF: FF: FF: FF: FF: FF: FF, then we assume that nothing is connected. In the general case, this, of course, is incorrect, since some discs, for example, TM2004, allow you to write 8 0xFF to the key identifier, so if your tablet is stitched with this code, then the test needs to be removed.
The order of work: we start, we connect the key, whose code we want to know, and the resulting value is hard-code in the key_to_write array. We remove marked with comments return. Start and connect the disc again, it should be flashed with a new key. Naturally, to write an already known code (say, a master key), the first step is not required.
If an error occurred during the recording of the first byte, then your key is not rewritable. If the error is not on the first, but on some of the following bytes, then check the contact between the tablet and arduine.
A successful write log looks something like this:
We get down to the street, we try to open the neighboring entrance. Works!
And was it worth it to spread? Suddenly a homeless man can enter my porch and start living there?
Well, first, let's face it - the master key will be programmed to you in any transition for very little money. Yes, and the Internet offers lots. In this regard, one and a half hackster, who repeated my experience, is a drop in the ocean.
Secondly, I still deliberately missed several fairly fundamental issues that would prevent a newcomer from launching the device. Well, an advanced person is unlikely to come to your door to sleep there or create indecency.
Therefore, publish without the slightest doubt. Use!
We will talk about intercoms, working with 1-wire DS1990 tablets, like this:

On the Internet you can find a lot of materials on how to read information from them. But these pills are not only read-only. It is common for a person to lose keys, and today a stall with DS1990 cloning services can be found in any underground passage. For recording, they use blanks that are compatible with the original keys, but have additional commands. Now we will learn how to program them.
')
Why do you need it? If we discard the obviously bad options, then the simplest thing is to reprogram the cloned tablets that have accumulated and become unnecessary from the old intercom, replaced with a new one, from the entrance of the rented apartment, where you no longer live, from work, where you no longer work, etc.
At once I will make a reservation that in the description I will omit some points that are obvious to most of those who are “in the subject line”, but perhaps not allowing a simple person who has come here from the search engine to repeat the procedure. This is done on purpose. Though I am for openness of information, and I believe that information about all vulnerabilities should be communicated to the public as quickly as possible, but still I don’t want anyone who can easily come to my doorway.
A bit of theory.
As you know, DS1990 is characterized, in general, by one parameter - its own identification number. It consists of 8 bytes and deposited on the surface of the tablet. And it is issued in response to a request for 1-wire. In fact, one of these bytes is a device type identifier, another one is a checksum, but for us this is all not important. All keys known to him are registered in the memory of the intercom, only the company managing the intercom can change this set. But in addition to the keys, clearly recorded in the memory, the intercom sometimes reacts to the so-called master keys, the same for the doorphone of this manufacturer, this series, this installer. Master key codes are kept secret, but sometimes they leak. In five minutes of googling, you can find about 20 master keys from various intercoms. I have a “visit”, so the choice fell on the key 01: BE: 40: 11: 5A: 36: 00: E1.
The blanks for which the keys are cloned come in different types. In our city the most common - is TM2004. According to the description, they support finalization, after which they lose the possibility of rewriting and function as the most common DS1990. But for some reason, craftsmen who make copies do not always finalize. Perhaps because the majority of programmers on the market have been bought for a long time and do not have such a function, perhaps because the finalization requires an increased (9V) voltage. I do not know. But the fact remains that of the 4 keys on which I experimented, only one was finalized. Others easily allowed to change their code for whatever you want.
Practice.
We will assemble the programmer on Arduino Uno, which is suitable for similar purposes of prototyping and assembling disposable crafts. The simplest scheme, 1-Wire for that and 1-Wire.

The build time of the device on the brainboard does not exceed five minutes

Sketch code. The recording algorithm itself is taken here - domofon-master2009.narod.ru/publ/rabota_s_kljuchom_tm_2004/1-1-0-5
There, however, it is written that you can write all 8 bytes in a row, but it did not work for me. Therefore, each byte is written separately, through its own command 0x3C.
#include <OneWire.h> #define pin 10 byte key_to_write[] = { 0x01, 0xBE, 0x40, 0x11, 0x5A, 0x36, 0x00, 0xE1 }; OneWire ds(pin); // pin 10 is 1-Wire interface pin now void setup(void) { Serial.begin(9600); } void loop(void) { byte i; byte data[8]; delay(1000); // 1 sec ds.reset(); delay(50); ds.write(0x33); // "READ" command ds.read_bytes(data, 8); Serial.print("KEY "); for( i = 0; i < 8; i++) { Serial.print(data[i], HEX); if (i != 7) Serial.print(":"); } // Check if FF:FF:FF:FF:FF:FF:FF:FF // If your button is really programmed with FF:FF:FF:FF:FF:FF:FF:FF, then remove this check if (data[0] & data[1] & data[2] & data[3] & data[4] & data[5] & data[6] & data[7] == 0xFF) { Serial.println("...nothing found!"); return; } return; // remove when ready to programm // Check if read key is equal to the one to be programmed for (i = 0; i < 8; i++) if (data[i] != key_to_write[i]) break; else if (i == 7) { Serial.println("...already programmed!"); return; } Serial.println(); Serial.print("Programming new key..."); for (uint8_t i = 0; i < 8; i++) { ds.reset(); data[0] = 0x3C; // "WRITE" command data[1] = i; // programming i-th byte data[2] = 0; data[3] = key_to_write[i]; ds.write_bytes(data, 4); Serial.print("."); uint8_t crc = ds.read(); if (OneWire::crc8(data, 4) != crc) { Serial.print("error!\r\n"); return; } else Serial.print("."); send_programming_impulse(); } Serial.println("done!"); } void send_programming_impulse() { pinMode(pin, OUTPUT); digitalWrite(pin, HIGH); delay(60); digitalWrite(pin, LOW); delay(5); digitalWrite(pin, HIGH); delay(50); } Once launched, the program polls the 1-Wire interface once a second and issues the code read from it to the serial port. If this is FF: FF: FF: FF: FF: FF: FF: FF, then we assume that nothing is connected. In the general case, this, of course, is incorrect, since some discs, for example, TM2004, allow you to write 8 0xFF to the key identifier, so if your tablet is stitched with this code, then the test needs to be removed.
The order of work: we start, we connect the key, whose code we want to know, and the resulting value is hard-code in the key_to_write array. We remove marked with comments return. Start and connect the disc again, it should be flashed with a new key. Naturally, to write an already known code (say, a master key), the first step is not required.
If an error occurred during the recording of the first byte, then your key is not rewritable. If the error is not on the first, but on some of the following bytes, then check the contact between the tablet and arduine.
A successful write log looks something like this:
KEY FF:FF:FF:FF:FF:FF:FF:FF...nothing found! KEY FF:FF:FF:FF:FF:FF:FF:FF...nothing found! KEY FF:FF:FF:FF:FF:FF:FF:FF...nothing found! KEY 1:98:2C:CD:C:0:0:EB Programming new key...................done! KEY 1:BE:40:11:5A:36:0:E1...already programmed! We get down to the street, we try to open the neighboring entrance. Works!
Moral ethical issues.
And was it worth it to spread? Suddenly a homeless man can enter my porch and start living there?
Well, first, let's face it - the master key will be programmed to you in any transition for very little money. Yes, and the Internet offers lots. In this regard, one and a half hackster, who repeated my experience, is a drop in the ocean.
Secondly, I still deliberately missed several fairly fundamental issues that would prevent a newcomer from launching the device. Well, an advanced person is unlikely to come to your door to sleep there or create indecency.
Therefore, publish without the slightest doubt. Use!
Source: https://habr.com/ru/post/237487/
All Articles