Anonymization on the Internet and the use of self-hosted services
In this article, I will describe my actions to increase anonymity on the Internet, as well as give instructions on switching from google dependent services to my own.
Table of contents.

All that is transmitted in unencrypted form can be intercepted and modified (classic MitM ). And our provider can easily identify the request with the accuracy of the MAC address and the client agreement.
')
Even if your provider does not deal with such things, then in his data center there certainly is an inconspicuous server where the mirror has certain traffic. This is a SORM server. And what happens there is unknown to anyone except SORM suppliers.

If you use gmail to read work / personal mail or use the chrome browser, it will be very convenient for Google corporation to collect information about where you go and what they write to you.
Russian services do the same, remember YandexCrypt , VK is generally a breeding ground for user information.
And remember hundreds of sites where you can leave comments by logging in to social networks.
Of course, for now this is done only to show us more “correct advertising”, but who knows what will happen in the future.
Now that we have understood why it is necessary to preserve anonymity on the Internet, let's see how this can be achieved.

Information compiled as paranoid increases

Go to the address about: config in the address bar to tweak the list of options affecting privacy

If we want to transfer the file securely, then it is highly desirable to use encryption. For example gpg / pgp
A person who has received a letter or file from you encrypted and signed by our pgp key can be 100% sure that it is not fake and only the recipient specified by the sender can read it. Thus, our mail can be significantly more secure and it will be more difficult for intruders to get data even in case of full access to the box during hacking.
You can simply encrypt any file. To do this, simply give the command:
The system will request a password twice. As a result, we will get next to the original file with a new .gpg extension at the end. For example, file.gpg. Decoding is also very simple:
And after entering the password, we will receive our source file.
A bit more complicated procedure, because 2 keys are involved here. One of our personal, secret, known only to us and to no one else. Another public one, handed out to us by friends in any convenient way. Just this option and the most frequently used, because in the first variant, besides the encrypted file, it is necessary to transfer the password to it and there is no guarantee that it will not be intercepted.
The topic was covered in Runet - one , two
Now we come to the second part of the article, where I will try to tell you what and how can I replace the popular guglopochts and rss readers, etc.
The whole attempt to remain anonymous and imperceptible to the Internet is nothing, if you use the calendar and contacts from Google, keep the correspondence in Yandex mail, write notes in evernote and put the files in the dropbox
To prevent Internet services from spying on us, we need to stop using them!

In order to host our applications, we need vps with anonymous payment (bitcoins or something like that) and an encrypted disk (KVM, XEN and other virtualization that will allow it)
External ip address that can be purchased with vps and dns name.
What do we use most often?
You can configure the entire mail binding yourself (for example: postfix + dovecot + antispam), or you can use the iredmail assembly.
About her on Habré wrote here and fresher .


Quite a lot of opensource applications can be considered as replacing dropbox, I will give a small list of them with links to installation examples:

Unfortunately, I did not find a full-fledged web-based replacement for the evernote service.
There is only laverna , but this is still too fresh software. Full of children's bugs and bugs

This is of course everyone's favorite jabber, configured and running on its own vps.
Installation instructions prosody , lightweight and small server to communicate via jabber.

For reading the news, I use the rss reader Tiny Tiny rss, it has a lively community and a rather nice interface.
Installation Instructions

About how to configure vpn on Habrr wrote more than once and not two
Link1
Link2

In order for me to synchronize passwords and bookmarks in the browser, I use the firefox sync server.
Setup Instructions
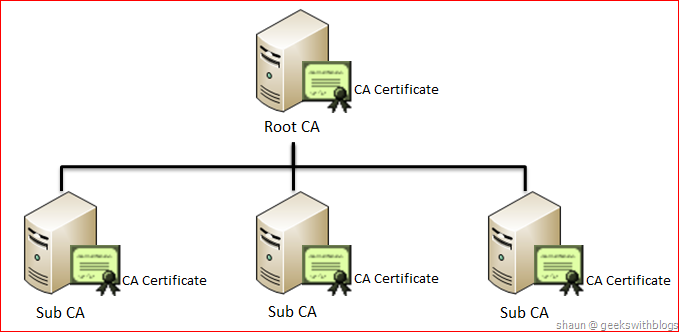
In order for all our services to work on a secure connection, you must either buy an ssl certificate (wildcard certificate or a few ordinary ones), or create your own certificate authority, integrate it into your browsers and sign their service ssl certificates to them.
Setup Instructions
Additional elements that increase serenity in paranoid
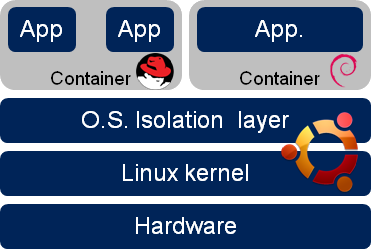
Why is this necessary? For example, we want to launch Skype or a couple of Skype or launch another firefox to view a super secret Japanese movie through a Japanese vpn.
The reasons may be many.
So, the implementation is described in the articles of one of the creators of lxc
Unprivileged containers
and
GUI in containers

How exactly the browser merges information about you is pretty well described on Lurk:
Identification of users on the Internet
There is a great article on wikibooks for using the Internet anonymously:
Protection of confidential data and anonymity on the Internet
Unfortunately, the article does not contain a lot of information security solutions.
I will try to fill in the gaps with links to interesting solutions.
habrahabr.ru/post/120620 - DNSSEC, what is and why
prism-break.org/ru - Project for finding alternatives to proprietary solutions to protect against SORM
www.opennet.ru/base/sec/ubuntu_disk_crypt.txt.html - disk encryption for linux
Table of contents.
- Why do you need it
- The provider is watching us.
- We are followed by a service provider.
- Anonymity on the Internet
- Rules for registration on Internet sites
- Browser Setup
- Using pgp encryption
- Using self-hosted services
- Bonus
- Links
Why do you need it

The provider is watching us.
All that is transmitted in unencrypted form can be intercepted and modified (classic MitM ). And our provider can easily identify the request with the accuracy of the MAC address and the client agreement.
')
Even if your provider does not deal with such things, then in his data center there certainly is an inconspicuous server where the mirror has certain traffic. This is a SORM server. And what happens there is unknown to anyone except SORM suppliers.
We are followed by service owners.

If you use gmail to read work / personal mail or use the chrome browser, it will be very convenient for Google corporation to collect information about where you go and what they write to you.
Russian services do the same, remember YandexCrypt , VK is generally a breeding ground for user information.
And remember hundreds of sites where you can leave comments by logging in to social networks.
Of course, for now this is done only to show us more “correct advertising”, but who knows what will happen in the future.
What got into the Internet will stay there forever
Anonymity on the Internet
Now that we have understood why it is necessary to preserve anonymity on the Internet, let's see how this can be achieved.

Rules for the use of Internet services
Information compiled as paranoid increases
- Do not use real names / surnames / dates of birth
- Do not use the same password everywhere (one will break - all will break)
- If possible, use multiple accounts with different nicknames, different types of activity
- If the site sends you a clear password in the mail - this is a bad site. They keep your password unencrypted, which means they know it themselves and can sell / give the opportunity to steal.
- If possible, use incognito mode during registration, login to important sites (for example, bank-client site or super-duper important bug tracker)
- If we want to post photos, then we first need to check if there is any deanon metadata
- If you need to transfer secret data over an open channel, you can pre-encrypt using pgp or transfer information in parts on different channels. Login can be sent via Skype, the password is said in person, and the address can be sent via whatsapp.
- Login and register only where there is HTTPS!
- Login and register using vpn, in order not to shine your ip-Schnick
Browser Setup
- The browser should not remember your passwords.
- The browser should not synchronize your history / cookies / passwords and other information with an unknown server on the Internet
- The browser should not store cookies between its restarts.
- Much more
Setup example for firefox

Go to the address about: config in the address bar to tweak the list of options affecting privacy
- media.peerconnection.enabled = false - denies support for the WebRTC protocol, the current implementation of which allows for a user to get a list of IP addresses on his local network (using JavaScript), which increases the user's uniqueness.
- browser.safebrowsing.enabled = false and browser.safebrowsing.malware.enabled = false - disables the transfer of information on web sites visited to Google, the base of which is used for alerts about fraudulent sites.
- browser.search.suggest.enabled = false - disables the transmission of text typed in the search window to the search engine without explicit confirmation from the user. Depriving the offers from the search engine as you type the query, but if you suddenly start typing the query and change your mind, it will not go until you press Enter.
- dom.enable_performance = false - disables the browser sending information about the start and end time of the page loading. Analysis of this data allows you to determine whether a proxy server is used
- network.dns.disablePrefetch = true - disables the preliminary resolution of DNS names for all links on a web page (until the user himself clicks the link). This can lead to the leakage of DNS-traffic when working through anonymizing proxy server.
- network.proxy.socks_remote_dns = true - send DNS requests through a proxy when using a proxy. Otherwise, they will go directly and may lead to the disclosure of the real IP-address.
- dom.battery.enabled = false - prohibits tracking battery status.
- dom.network.enabled = false - forbids to determine the parameters of the connection to the network (the type of connection is transmitted: LAN, Wifi, 3G, and so on).
- network.proxy.no_proxies_on = (empty value) - prohibits sites from accessing the local machine, which would allow them to analyze the list of open ports.
Using pgp encryption

If we want to transfer the file securely, then it is highly desirable to use encryption. For example gpg / pgp
A person who has received a letter or file from you encrypted and signed by our pgp key can be 100% sure that it is not fake and only the recipient specified by the sender can read it. Thus, our mail can be significantly more secure and it will be more difficult for intruders to get data even in case of full access to the box during hacking.
Encryption
You can simply encrypt any file. To do this, simply give the command:
gpg -c file The system will request a password twice. As a result, we will get next to the original file with a new .gpg extension at the end. For example, file.gpg. Decoding is also very simple:
gpg file And after entering the password, we will receive our source file.
Asymmetric encryption and signature
A bit more complicated procedure, because 2 keys are involved here. One of our personal, secret, known only to us and to no one else. Another public one, handed out to us by friends in any convenient way. Just this option and the most frequently used, because in the first variant, besides the encrypted file, it is necessary to transfer the password to it and there is no guarantee that it will not be intercepted.
The topic was covered in Runet - one , two
Now we come to the second part of the article, where I will try to tell you what and how can I replace the popular guglopochts and rss readers, etc.
Using self-hosted services
The whole attempt to remain anonymous and imperceptible to the Internet is nothing, if you use the calendar and contacts from Google, keep the correspondence in Yandex mail, write notes in evernote and put the files in the dropbox
To prevent Internet services from spying on us, we need to stop using them!
So let's go

In order to host our applications, we need vps with anonymous payment (bitcoins or something like that) and an encrypted disk (KVM, XEN and other virtualization that will allow it)
External ip address that can be purchased with vps and dns name.
What do we use most often?
post office

You can configure the entire mail binding yourself (for example: postfix + dovecot + antispam), or you can use the iredmail assembly.
About her on Habré wrote here and fresher .
Dropbox


Quite a lot of opensource applications can be considered as replacing dropbox, I will give a small list of them with links to installation examples:
- Seafile, installation described in detail on the official website
- OwnCloud installation and use
- Sparkleshare
- Pydio
Replacing evernote / google keep

Unfortunately, I did not find a full-fledged web-based replacement for the evernote service.
There is only laverna , but this is still too fresh software. Full of children's bugs and bugs
Replacement of Asechke / Skype / Messenger

This is of course everyone's favorite jabber, configured and running on its own vps.
Installation instructions prosody , lightweight and small server to communicate via jabber.
Using rss

For reading the news, I use the rss reader Tiny Tiny rss, it has a lively community and a rather nice interface.
Installation Instructions
Using vpn

About how to configure vpn on Habrr wrote more than once and not two
Link1
Link2
Using the firefox sync server

In order for me to synchronize passwords and bookmarks in the browser, I use the firefox sync server.
Setup Instructions
Create rootCA

In order for all our services to work on a secure connection, you must either buy an ssl certificate (wildcard certificate or a few ordinary ones), or create your own certificate authority, integrate it into your browsers and sign their service ssl certificates to them.
Setup Instructions
Bonus
Additional elements that increase serenity in paranoid
Using lxc sandboxes for unreliable programs

Why is this necessary? For example, we want to launch Skype or a couple of Skype or launch another firefox to view a super secret Japanese movie through a Japanese vpn.
The reasons may be many.
So, the implementation is described in the articles of one of the creators of lxc
Unprivileged containers
and
GUI in containers
Build a secure OS on your computer / laptop
- This means using Linux or another open source OS.
- This means using a strong password (or better authenticating with a fingerprint)
- This means using encryption of your disk partitions.
Setting up an Android phone

- Replacing standard firmware with Cyanogenmod / Replicant / Paranoid Android
- Using File System Encryption
- Access to the Internet only via VPN
- Failure to use google play, replacement for F-Droid
- Use a long, strong password
- Track your phone (gps tracker android self hosted in search)
Links
How exactly the browser merges information about you is pretty well described on Lurk:
Identification of users on the Internet
There is a great article on wikibooks for using the Internet anonymously:
Protection of confidential data and anonymity on the Internet
Unfortunately, the article does not contain a lot of information security solutions.
I will try to fill in the gaps with links to interesting solutions.
habrahabr.ru/post/120620 - DNSSEC, what is and why
prism-break.org/ru - Project for finding alternatives to proprietary solutions to protect against SORM
www.opennet.ru/base/sec/ubuntu_disk_crypt.txt.html - disk encryption for linux
Source: https://habr.com/ru/post/237335/
All Articles