Directed IT attacks in the sphere of large business: how it happens in Russia
A few years ago, the state decided that targeted attacks were a threat to state security. This year, on the basis of the Ministry of Defense, special information security forces were created to protect military information systems and communication systems. At the same time, banks, large retail, oil and gas enterprises and other large companies are in the civilian sector. We protect them and other civilian teams.
Characteristics of a directed attack are usually:
- There is a professional group, usually financially motivated or by order. Random goals are rare, most often selected segments of industries or individual enterprises.
- The most frequent vectors are a combination of 0-day and sotsinzhiniring. 0-day vulnerabilities are often purchased from special “scouts” for large attacks.
- If the attack was detected and stopped, then the likelihood of a quick return on another vector is high. The attack goes to the result.
- The main goal is corporate secrets, source code, correspondence of top management.
- Possible return after the primary attack. There was an example of Nortel with an attack when the group came back 10 years later.
- Attacks are hidden, usually there is no Ponte. Priority - as much as possible to clear the logs and other traces.
We have banks, retail, insurance and many others on protection. I'll tell you about the practice and solutions.
')
Attack course
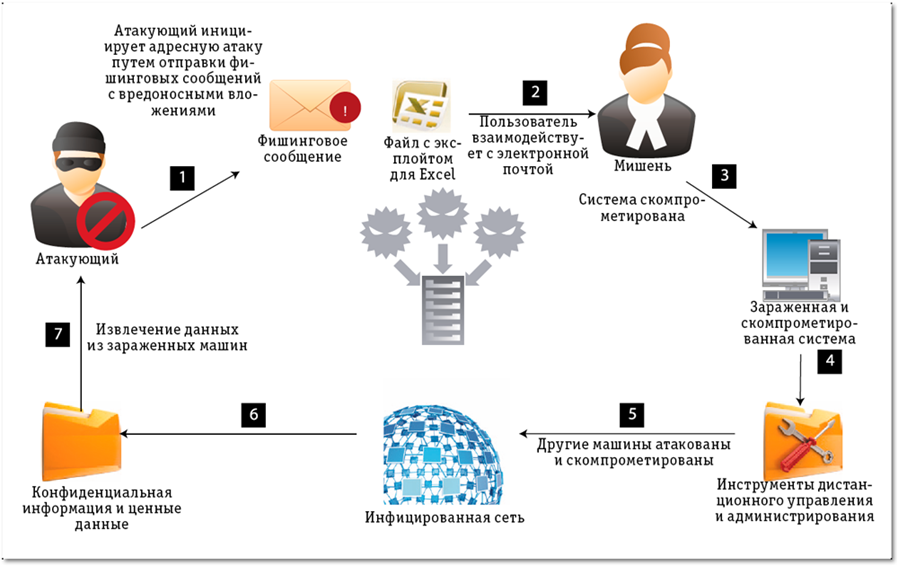
RSA, Red October Attack
As a rule, the attack develops according to standard principles:
- Intelligence and data collection. Social networks are scanned, especially LinkedIn, it turns out a hierarchy of employees and their names, connections. Technical methods investigate network architecture, gather IP addresses of services, information about equipment and software solutions, as well as about the means of protection used.
- The attack vector is selected, as a rule, the main question is how to deliver the malware for the DMZ. It can be anything: from the road apple (flash drives in the back) to the infection of sites that are visited by users of the company. Often the company's defense is so good that it takes another direct attack on one of the security providers in order to get the delivery vector inside the final goal. When breaking into RSA, master keys were stolen, which were used to attack other companies.
- An intrusion is performed directly, as a rule, control is taken over one of the network nodes. The malware uploads or assembles the main modules and begins distribution from this node, gradually increasing influence and privileges in the network.
- Influencing effect occurs. At this step, the activity of protective equipment is suppressed, the malware receives almost complete control necessary to solve the problem.
- Search for information. As a rule, some intermediate server for data storage is infected, for example, an update server. On it, the group collects all the interesting things that you want to extract from the network. Often the process of finding data takes days and weeks.
- Extract. The intermediate server segments the data, archives it, hides (encrypts or uses steganography), then sends it out. Methods - up to exotic, for example, mixing important data into technical traffic.
- Hiding tracks.
- Minimizing influence. Usually, all active components of the malware are removed, and only a small tab remains that can recreate or load code for future meetings.
Abstraction
According to the world practice, such attacks very often require masking, since they can be detected even in the early stages of scanning in the form of atypical activity within the network. For this, a powerful DDoS attack on the target is launched very often. It distracts security specialists from the target and helps to hide surgical movements along the real vector of attack.
Examples of protective equipment:
- NG FW class systems (Check Point, Stonesoft, HP Tipping Point);
- system for detecting potentially dangerous files (sandbox) (Check Point, McAfee, FireEye);
- Web application security (WAF) (Imperva SecureSphere WAF, Radware AppWall, Fortinet Fortiweb);
- network traffic anomaly detection systems (StealthWatch, RSA NetWitness, Solera Networks);
- systems for analyzing and optimizing the settings of the ME infrastructure (Algosec, Tufin, RedSeal, SkyBox);
- Code Security Audit (HP Fortify, ERPScan CheckCode, Digital Security, IBM AppScan Source);
- protection against fraud when accessing online banking systems (Versafe);
- digital information security incident investigation (Forensic Analysis and Incident Response) (AccessData);
- DDoS protection system (iron - Radware DefensePRO, ARBOR PRAVAIL, Check Point DDoS Protector; service - Kaspersky DDoS Prevention, QRATOR HLL).
Counteraction (theory)
- At the stage of data collection, firewalls and systems for detecting and preventing network attacks are traditionally used. The main problem is that they, as a rule, do not define a slow scan. NG FW (firewalls of the new generation) allow you to correlate events on the network, compare parts of attacks and see the full picture. For example, anomalies on the time of day, traffic on new ports and so on are investigated.
- At the intrusion stage, traditional query filtering, intrusion prevention systems, antiviruses, including “heavy” on gateways, are now being applied. In addition to the NG FW systems, two more methods are used - traps and sandboxes. Pitfalls are pseudo-vulnerable services within the network, the sole purpose of which is to take over the attack and raise the alarm. Sandboxes work to block intrusions as follows. Suppose a user receives mail with an archive. Within three minutes before delivery to the user, the sandbox “swings” this archive. To begin with, it turns out that inside there are three files, one is executable, it assembles its piece from the other two, and then creates a process and writes a key in the registry. The task is to simulate a regular machine, because many malicious programs perfectly detect the hypervisor mode and are not activated. In modern sandboxes, there is a network activity simulator (even allowing the malware to receive “answers” from the command center), using both static disassembling and dynamic code analysis, the malware is offered various environments - server, user, and so on, and directly from standard images of the current network. There is a GUI allowing you to see which code does what.
- If the intrusion has already passed, it is necessary to localize the threat and prevent data extraction. For this purpose, incident investigation systems are used, analyzing logs and tracing the paths of malware distribution over the network. If the extraction was still - the same systems help to understand what exactly was carried out. For example, Sony blocked the first attack on its infrastructure before extraction and began to celebrate, but, as you know, then there were more vectors.
- At this next stage, you need to start a formal investigation and go to court. For the court need evidence of attack. Have you ever tried to collect them over the network? So, the same Forensic Analysis can take a copy of the infrastructure and create a detailed report on the current number, and then close it with a digital signature. And the American courts are already accepting such megatuy files with all the memory snapshots, a list of processes, logs, and so on as evidence. They can be picked slowly and quietly.
Counteraction (practice)
We have a customer - a large retail chain - the infrastructure of which has been under constant targeted attacks for several months. A large botnet works with a wide range of IP, used as attempts to carry exploits, and good old brute force. All this is accompanied by waves of DDoS. I can’t tell you concretely on this occasion until the end of the attack is visible (and another two years ago), so I’ll show you what I would do in theory to protect such a system. In addition, that would have provided a deliberately unrevealed service under brute force.
- I would update network security tools to a new generation in order to analyze slow events, see non-standard data collection algorithms and decrypt malware channels.
- Profiling data flows between hosts and establishing control over this.
- Would register restrictions in network rules.
- I would launch on a regular basis the system of searching for vulnerabilities from the inside - these are sets of utilities that run around the network and try to attack everything that is badly lying. I would get a standard list of unclosed hardware exploits and un-updated software.
- Once a week, I would look at optimizing settings — these are utilities that analyze network rules on nodes (including intermediate equipment), prioritize them for speed, look for obvious children’s schools, and help establish best practice. Very useful, although quite expensive, solutions. By the way, it helps to close the holes removed from the support of applications on intermediate devices due to filtering.
- I would connect a data cleaning center on a trunk channel (in Russia there are a couple of such pieces) in case of powerful DDoS in order to transfer traffic to it in a maximum of 30 seconds.
- I would connect to the knowledge base about hacker groups actions. There are special teams that read hacker forums, merge minor vulnerabilities, and so on, seeking credibility in this environment. They signal new methods and tools.
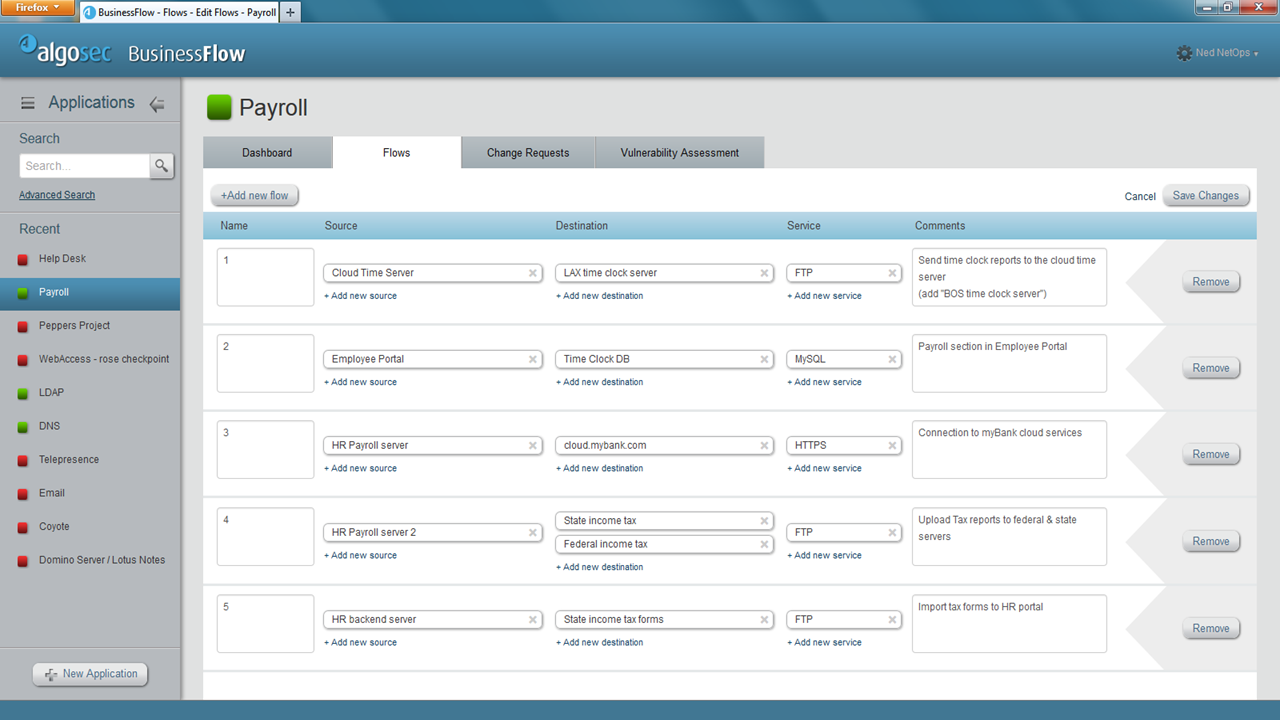
Algosec, an example of a GUI for setting up basic rules for an IT department manager (not a security officer)
Code Security
If a company develops code, then often the code itself becomes the target for attacks and bookmark embedding. For such situations, systems of checking the integrity of the code, analyzing references to it, source modification maps, and so on are used. In general, they make it possible to understand who and when should not have referred to a specific site, but turned and added something. In parallel, a static analysis is performed for vulnerabilities.
User protection
One of the frequent modern vectors in the banking sector is an attack not on the server part, but on the users equipment. A frequent example is a trojan that can, when you click on the submit button of a form, replace the account for the transfer of funds and the amount of payment. Some banks in their IB assume that the user equipment is obviously unreliable, and have protection against such attacks on their side.
Cases
The problem of cases in security is whether to consider the success of a non-happening attack as success. For example, there is a situation with Infostruktura (Lithuania) - an analogue of RSNet in Russia, its example is indicative. The company provides communication services to the Government of Lithuania. Uses the full range of AMS to protect government sites and some commercial structures (more than 200 sites). Uses AppWall, DP, Alteon, over 2 years reflecting attacks at all levels. The only provider that survived the massive attack on Lithuania during the European forum there last year. But, of course, the best defense is when an attack does not even occur, because it is too expensive. If interested, I will provide more cases on your field when you request to plutsik@croc.ru.
Summary
Attacks on large companies are not myths. Right now, one of our customers is experiencing several dozen different attacks a day, the other is defending himself against weekly DDoS, and several more consistently catch interesting files from sandboxes. Theoretically, with due attention, the race of the shield and sword in the field of information security continues all the time, and the balance is maintained. The only effective vulnerability is humans. Sotsinzhiniring is the most effective and timeless method. And the task of educating users, plus regular exercises, lies not only on our technical side, but also on the side of the customer’s staff.
Source: https://habr.com/ru/post/236411/
All Articles