Hackers used Google to debug malicious software.

Brandon Dickson, an independent information security researcher, published in his blog a story about the traces of the use of Google’s VirusTotal resource by hackers to debug his malicious programs.
For several years, Dixon, using various methods (which it does not indicate specifically), collected data on the behavior of users of the VirusTotal resource, with which it is possible to scan various files for their security. According to the researcher, the service, which ordinary users of the network use to increase their level of security, served as a means for malicious users to debug software.
')
The VirusTotal project was founded in 2004 in Spain and bought by Google in 2012 - it brings together more than three dozen antiviruses and security scanners manufactured by Symantec, Kaspersky Lab, F-Secure and other companies. Security researchers and ordinary netizens can upload files to the site to check for malware.

Brandon dickson
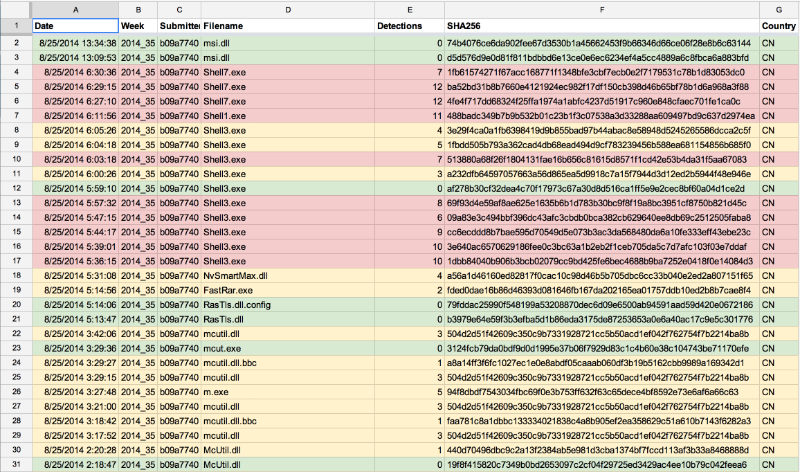
Dixon studied the behavior of users of VirusTotal using unique hashes that are assigned to them when they upload files to the site. Hackers uploaded files to the site until VirusTotal antiviruses reported that they did not find anything suspicious. Dickson found traces of several specific hackers or groups of cybercriminals. Moreover, the researcher even managed to determine the future targets of the attack of the intruders.
This was possible due to the fact that every time a file is uploaded to VirusTotal, metadata appears, including the name of the file and the time it was created and uploaded, as well as a hash created based on the IP address and the country from which the download occurred. Google uses various methods to complicate the allocation of IP addresses from the hash, but Dixon managed to at least determine the hashes of the IP addresses from which multiple file downloads were made.
By clicking the picture will open in full size.
The researcher has developed an algorithm for processing the collected data. According to the publication Wired, as a result, he was able to identify patterns and geographical areas of loading of two groups of hackers from China and Iran. At the same time, in some cases, Dixon could even track the development of attacks — first, the hackers themselves downloaded the malicious files for the test, and then from other addresses of the victim of the attack.
Dixon says he collected so much information about the activity on the attackers website, that it was time to share it with the public.
Source: https://habr.com/ru/post/235449/
All Articles