How dangerous is an open recursive DNS server?
It is indisputable that “exposing the server” to the Internet it is necessary to take care of its security and limit access to it as much as possible. The DNS protocol can be used both for attacks on the infrastructure (DNS server, channel) of the victim, and to attack other companies. Over the past year, the number of such attacks has increased at least 2 times. On digitalattackmap.com , which visualizes DDoS attacks, DNS is separated from the general list along with attacks on the Web (80/443).
The DNS service works (mostly) using the UDP protocol, which does not imply a prior connection, so it can easily be used to attack other servers (spoofing) without special training. According to information from various sources 1,2 currently from 8 to 20 million DNS servers respond to recursive queries. These can be incorrectly configured authoritative and caching DNS servers or simple CPEs.
')
I was interested in how dangerous (for myself and others) to keep an open recursive DNS server, so I decided to do some research.
Formulation of the problem
The following questions were formulated and I would like to receive answers:
- How fast an open recursive DNS server will be detected;
- When they start using the server for illegal purposes;
- Determine the server load (the number of requests per second);
- Try to determine which organizations target attacks;
- Will compromised (blacklisted) domains and / or IP addresses be requested?
For testing, the server installed in the Nuremberg data center Hetzner is used. An authoritative DNS server was previously located on this server, the number of requests to which did not exceed 200 per day. The IP address of the server (due to the move to a new JSC) changed in July. To check the domains, the RPZ mechanism (response policy zone) and the black list from Infoblox were used .
Some theory
The following principles are used to carry out attacks through the DNS server:
- DNS works via UDP protocol, so an attacker can spoof his IP address with the address of the victim;
- DNS queries are asymmetric, the response traffic may exceed incoming traffic several times.
Based on these principles of this, the following types of attacks using DNS can be distinguished:
- Amplification attack (attack with amplification) - is aimed at overloading the outgoing channel of the DNS server. It starts with sending a large number of DNS queries specially selected to receive a very large response, the size of which can be up to 70 times the size of the request, which will lead to an overload of the outgoing channel of the DNS server and eventually denial of service (DoS );
- Reflection attack (attack with reflection) - third-party DNS servers (for example, my own) are used to spread DoS or DDoS attacks by sending a large number of queries. With such an attack, the address from which DNS requests are sent is replaced by the victim's IP address, and the request will have the data of the victim's server, not the attacker. As a result, when the name server receives requests, it will send all replies to the victim's IP address. A large amount of such "reflected" traffic can disable the server / network of the victim;
- Distributed reflection DoS (DrDoS) - combines reflection and amplification attacks, which greatly increases the likelihood of a victim server’s performance disruption. However, DNSSEC, designed specifically to protect DNS responses and prevent cache poisoning, can make this type of attack even more effective as the size of DNS messages increases. Gain can be up to 100 times, and attackers can use botnet networks - which can include thousands of computers.
The listed list of possible attacks is not complete, but it is sufficient for this study.
Research results
Over the week, a total of 416 thousand requests were received for 63 domains from 1,169 clients, which indicates the success of the study and the importance of this topic.
Below is a graph of the number of requests to the DNS server per second.
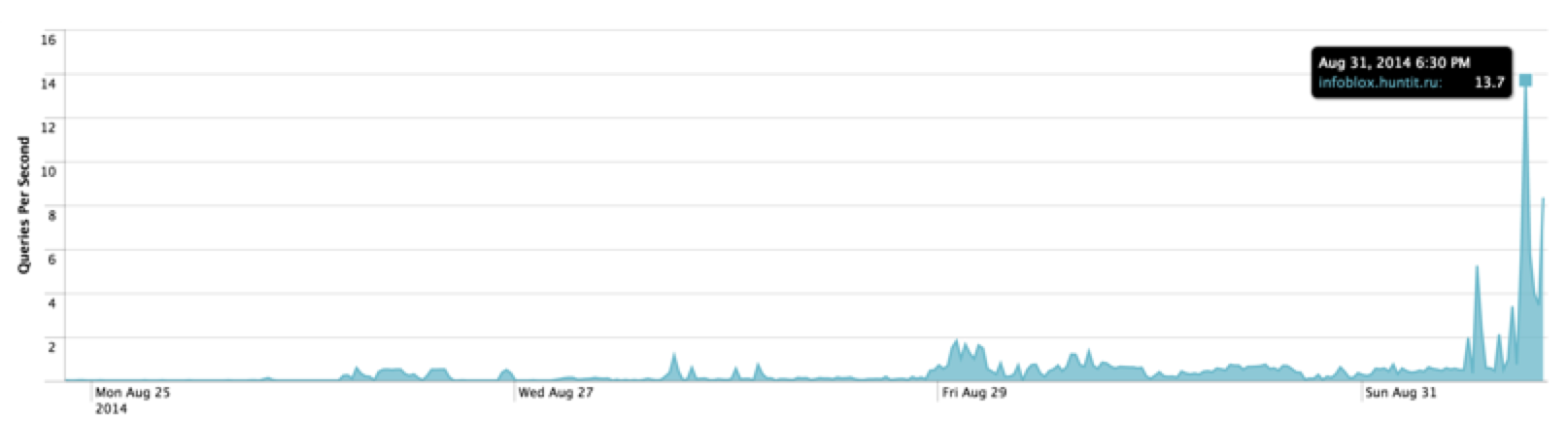
First of all, we will answer the questions posed:
- How fast an open recursive DNS server will be detected;
The first request came from China in 1 hour 20 minutes to the domain www.google.it - When they start using the server for illegal purposes;
After 1 day (the first small spike in the graph), periodic use of the server for attacks began. In 30 minutes, 300 requests to the webpanel.sk domain were received. Gradually, the number of requests and the duration of attacks increased. - Determine the server load (the number of requests per second);
At the time of the attacks, the server experienced a maximum load of 2-4 requests per second. On the last day of testing, the number of requests increased dramatically to 20 requests per second. The DNS Amplification attack was used; whether it was combined with DNS Reflection is difficult to determine. - Try to determine which organizations target attacks:

The number of domains requested was small, so it was easy to isolate potential victims and the domains used exclusively for attacks.
- The US Department of Labor, the domain doleta.gov , uses DNSSEC, the server's response is about 4 Kb, 127 thousand requests. The distribution of the number of requests by customers is quite even, TOP10 are located in different countries around the world (South and North America, Australia and New Zealand, Europe);
- A company in Slovakia, the domain webpanel.sk , use DNSSEC, the server's response is about 4 Kb - 162 thousand requests (most of the requests came on the day of the article, the numbers are constantly increasing). dnsamplificationattacks.blogspot.ru suspects that this domain is used exclusively for DNS amplification attacks. In fact, the responses from this server are no different from any other servers that use DNSSEC. A large number of requests comes from the servers of German hosting, Russian game hosting and some customers in the United States;
- The US Environmental Protection Agency, domain energystar.gov , uses DNSSEC, the server's response is about 4 Kb — 79 thousand requests. Total domain requested 69 customers, most of which are located in the USA. 18 thousand requests were received from the game server Royal Empire. Since there are no users on the server, and the news indicates that beta is online from 07/11/2014, we can assume that this server was hacked. IP addresses from Qwerty and Microsoft networks were seen.
- FamiNetwork, domain famicraft.com , 7.5 thousand requests. The domain contained meaningless “wowowow” TXT records, as a result of which the server response reached 4kb (50 times the attack gain). In the process of writing the article, I discovered that the response of the famicraft.com server has changed and it no longer represents a threat. Most likely the owner of the domain discovered the hacking and made the necessary corrections. Requests came from 4 servers, two of which belong to Akamai Technologies (5 thousand requests);
- 14 servers of Akamai Technologies were noticed in suspicious activity in all the domains listed above, perhaps this was an attack on Akamai or their servers were hacked;
- TOP10 by the number of incoming requests (30% of the total number of requests) included: German hosting (ironically providing protection from DDoS), game hosting (Russian), game server, two Akamai servers. Most likely, these servers were hacked, and the remaining clients are logged in botnets. - Whether compromised domains will be requested.
Not. For all the testing time, only one domain (ballsack.pw) was blocked by the IP address 104.28.0.111. The reason for blocking can be viewed on the ThreatStop server ( http://threatstop.com/checkip ). In principle, this is logical, since the botnet / malware through an external recursive DNS server carries out attacks, and the connection and receipt of commands from the control center occurs during initialization, and a recursive DNS server of the provider is used for this.
During the analysis of log files it was revealed:
- domains that were created and / or hacked for DDoS attacks: jerusalem.netfirms.com (gives a large number of A-records) and famicraft.com (described above). The response from these DNS servers is 4 Kb, that is, using data you can achieve a 50-fold overload of the outgoing channel (yellow color on the chart);
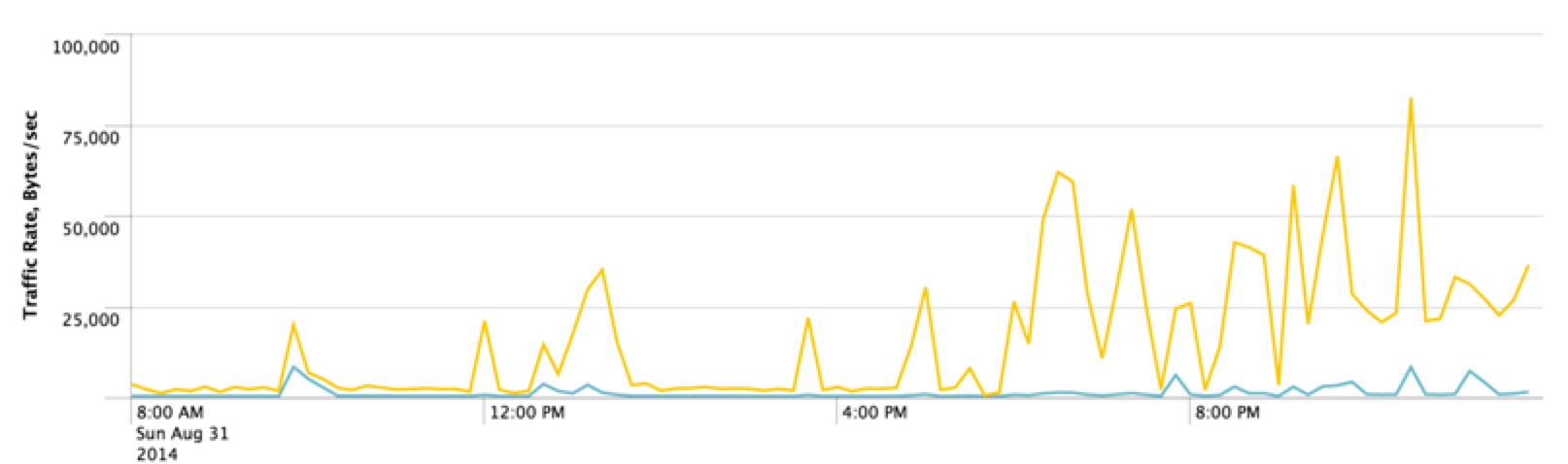
- organizations that actively monitor open recursive DNS servers:
- www.openresolverproject.org;
- dnsscan.shadowserver.org;
- there were several requests for the openresolvertest.net domain, but there is no information on the website.
Open recursive DNS servers
The dnsscan.shadowserver.org service has 8 million open recursive DNS servers. Most of these systems are located in China, Russia is located on the honorable 6th place.
| Country | Total |
| China | 2,886,523 |
| United States | 662,593 |
| Korea, Republic of | 591,803 |
| Taiwan | 449,752 |
| Brazil | 339,416 |
| Russian Federation | 264,101 |
An interesting graphical representation of the distribution of DNS servers across countries, both open recursive and authoritative.

findings
Based on the results obtained, the following obvious conclusions can be drawn:
- It is necessary to restrict access to all server resources, and in particular to a recursive DNS server;
- It is necessary to constantly monitor the load of the DNS server and the data channel. A sharp increase in load can indicate both the implementation of a DDoS attack and a hacking server;
- When using DNSSEC, it is necessary to reasonably limit the number of incoming requests (rate limit);
- Check your CPE for DNS access through the WAN interface;
- It makes sense for providers to forcibly restrict access from the Internet to recursive DNS servers of clients.
At first, I planned to complete testing in a week, but given the significant increase in load (from 2 to 20 QPS) on the last day of testing, I decided to extend the study for another week.
List of sources:
(c) Vadim Pavlov
Source: https://habr.com/ru/post/235197/
All Articles