Study: PHP sites turned out to be the most vulnerable for hackers
The attack on the corporate website not only disrupts online services and undermines the reputation of the owners, but often becomes the first step in hacking into the internal networks of large companies. At the same time, according to a study by Positive Technologies, the number of sites with high-risk vulnerabilities has noticeably increased recently. Researchers have identified the most common vulnerabilities and evaluated how effective their detection methods are.
In total, in the course of the security analysis tests conducted by the company in 2013, about 500 websites were examined, for more than 61 of them more in-depth analysis was conducted.
A significant part of the investigated portals belonged to banks because of the frequent attacks in this area. The demand for security analysis of media sites also increased, due to high-profile cases of hacking and the spread of misinformation. In addition, the sites of government agencies, industrial enterprises and telecommunications companies were investigated.
')
It turned out that 62% of sites in 2013 contained high-risk vulnerabilities. This figure is significantly higher than last year (45%). Most applications with high-risk vulnerabilities were detected on media sites (80%). As for the remote banking service sites, none of the RBS systems studied fully complied with the requirements of the PCI DSS security standard.
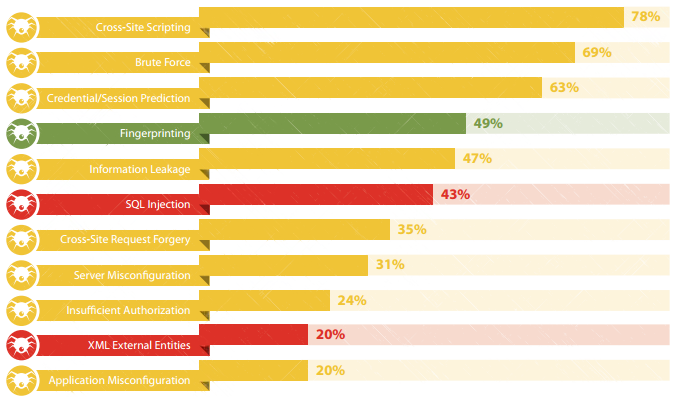
The most common vulnerabilities (share of sites,% )
The most common vulnerability of 2013 - cross-site scripting (Cross Site Scripting) - is found in 78% of the sites studied. This disadvantage allows an attacker to influence the content of a web page displayed in the user's browser, including the purpose of distributing malicious code or obtaining the victim's credentials. For example, in the case of a vulnerable Internet banking system, an attacker could form a link related to the real website of the bank, when clicking on which the user sees a fake authorization form. The data entered by the user will be sent to the attacker's server.
The second most popular (69%) is insufficient protection against the selection of user IDs or passwords (Brute Force), for example, due to the absence or incorrect implementation of the CAPTCHA mechanism. The top 10 also includes two high-risk vulnerabilities - “Deployment of SQL statements” (43%) and “Deployment of external XML entities” (20%).
The most unsafe sites turned out to be written in PHP: 76% of them contain critical vulnerabilities. Web resources in Java (70%) and ASP.NET (55%) are less vulnerable. Dangerous vulnerability "The introduction of SQL statements" is found on 62% of sites written in PHP; for other languages, this figure is much lower.
Positive Technologies experts also conducted a comparative analysis of application testing using black, gray and white box methods. The black box method involves the study of the system without obtaining data about it from the owner; the gray box method implies an intruder who has some privileges in the system; and finally, the white box method means analysis using all internal system data, including program source codes.
Among the web resources studied using black and gray mailboxes, 60% of sites found critical vulnerabilities. For the white box method, this figure is higher - 75%.

The average number of vulnerabilities on the same site with different methods of testing, taking into account the degree of risk
From the average number of vulnerabilities per system, it follows that testing with the white box method can detect almost 10 times more critical vulnerabilities than testing with the black and gray boxes. If it is possible to analyze the source codes of web applications, the white box method is preferred. But while site owners resort to it rarely: only 13% of web resources were investigated using this method.
Read the full text of the study on the Positive Technologies website: www.ptsecurity.ru/download/PT_Web_application_vulnerability_2014_eng.pdf
PS Continuing the theme, 09/04/2014 at 14:00, a webinar “The recommendations of the Central Bank for ensuring the information security of automated banking systems” will be held. On it we will try to talk about why the document turned out to be exactly this, why it does not contain SSDL / SDLC explicitly, and to highlight other questions that have arisen.
You can register here .
In total, in the course of the security analysis tests conducted by the company in 2013, about 500 websites were examined, for more than 61 of them more in-depth analysis was conducted.
A significant part of the investigated portals belonged to banks because of the frequent attacks in this area. The demand for security analysis of media sites also increased, due to high-profile cases of hacking and the spread of misinformation. In addition, the sites of government agencies, industrial enterprises and telecommunications companies were investigated.
')
It turned out that 62% of sites in 2013 contained high-risk vulnerabilities. This figure is significantly higher than last year (45%). Most applications with high-risk vulnerabilities were detected on media sites (80%). As for the remote banking service sites, none of the RBS systems studied fully complied with the requirements of the PCI DSS security standard.

The most common vulnerabilities (share of sites,% )
The most common vulnerability of 2013 - cross-site scripting (Cross Site Scripting) - is found in 78% of the sites studied. This disadvantage allows an attacker to influence the content of a web page displayed in the user's browser, including the purpose of distributing malicious code or obtaining the victim's credentials. For example, in the case of a vulnerable Internet banking system, an attacker could form a link related to the real website of the bank, when clicking on which the user sees a fake authorization form. The data entered by the user will be sent to the attacker's server.
The second most popular (69%) is insufficient protection against the selection of user IDs or passwords (Brute Force), for example, due to the absence or incorrect implementation of the CAPTCHA mechanism. The top 10 also includes two high-risk vulnerabilities - “Deployment of SQL statements” (43%) and “Deployment of external XML entities” (20%).
The most unsafe sites turned out to be written in PHP: 76% of them contain critical vulnerabilities. Web resources in Java (70%) and ASP.NET (55%) are less vulnerable. Dangerous vulnerability "The introduction of SQL statements" is found on 62% of sites written in PHP; for other languages, this figure is much lower.
Positive Technologies experts also conducted a comparative analysis of application testing using black, gray and white box methods. The black box method involves the study of the system without obtaining data about it from the owner; the gray box method implies an intruder who has some privileges in the system; and finally, the white box method means analysis using all internal system data, including program source codes.
Among the web resources studied using black and gray mailboxes, 60% of sites found critical vulnerabilities. For the white box method, this figure is higher - 75%.

The average number of vulnerabilities on the same site with different methods of testing, taking into account the degree of risk
From the average number of vulnerabilities per system, it follows that testing with the white box method can detect almost 10 times more critical vulnerabilities than testing with the black and gray boxes. If it is possible to analyze the source codes of web applications, the white box method is preferred. But while site owners resort to it rarely: only 13% of web resources were investigated using this method.
Read the full text of the study on the Positive Technologies website: www.ptsecurity.ru/download/PT_Web_application_vulnerability_2014_eng.pdf
PS Continuing the theme, 09/04/2014 at 14:00, a webinar “The recommendations of the Central Bank for ensuring the information security of automated banking systems” will be held. On it we will try to talk about why the document turned out to be exactly this, why it does not contain SSDL / SDLC explicitly, and to highlight other questions that have arisen.
You can register here .
Source: https://habr.com/ru/post/234845/
All Articles