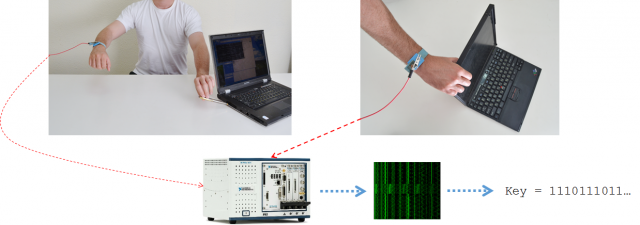
Touch to hack

Typically, hacking a computer involves searching for exploits or brute-force attacks, and both of these methods are rarely quick or easy. Nevertheless, a team of developers from Tel Aviv University have come up with a simpler way: touch the computer. If you make contact with a computer, you can measure changes in electrical potential, which show encryption keys. Moreover, sometimes even the PC itself is not necessary to touch - you can intercept the keys from the network or video cable. This method they demonstrated the other day.
')
What information can I steal?
- In most computers, you can distinguish processor inaction from its workload.
- On many computers, you can distinguish between patterns of processor operations and programs.
- Using GnuPG allows on some machines:
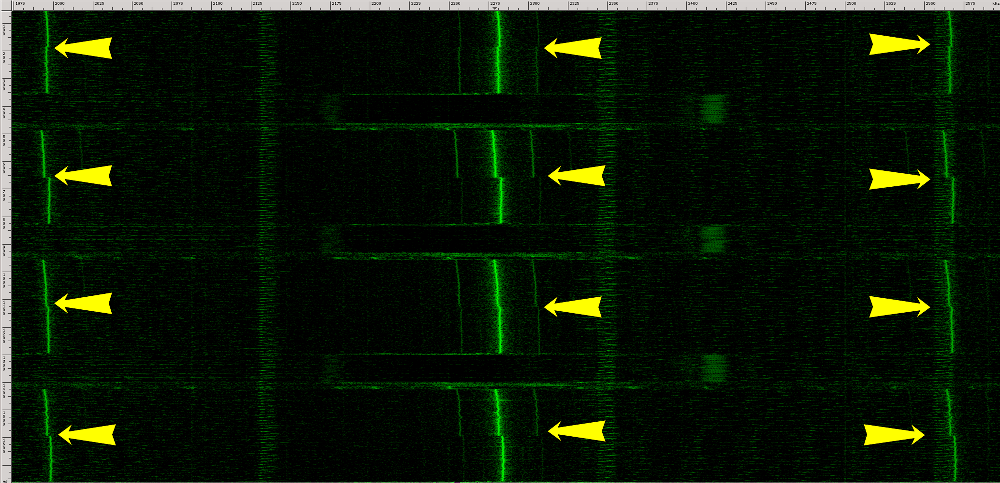
- distinguish spectral signatures of different RSA keys
- fully extract the encryption keys by measuring the electrical potential of the laptop while decrypting the ciphertext
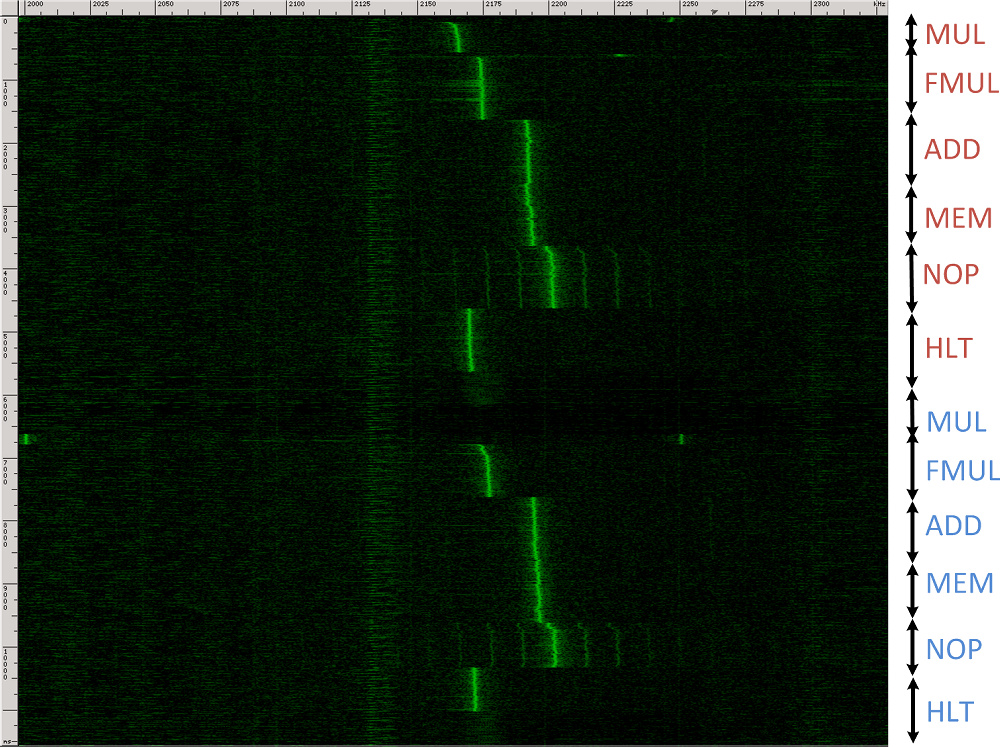
Why is this possible?
The electrical potential on the laptop chassis (under the chassis refers to metal panels, shields and ports) is ideally equal to the ground potential, but in reality it fluctuates significantly. Even when the laptop is grounded, there is resistance between the ground point and the other components of the chassis. Due to the current and electromagnetic fields inside the computer, a large voltage voltage develops through this impedance. This voltage and measured by the developers.
What equipment do you need?
Of course, in the laboratory it is easier to conduct such an experiment, but sometimes a regular smartphone will suffice. The phone was used to measure the potential of an ethernet cable.

What does an RSA leak look like?
Details of the study, as well as answers to questions are on the website of the Tel Aviv University .
Source: https://habr.com/ru/post/234359/
All Articles