Even an inexperienced hacker can hack 8 out of 10 large companies.
Every year it is more difficult for big business to defend against cyber attacks and more and more successful attacks can be carried out by an unskilled malefactor. Such findings are contained in a study of Positive Technologies based on penetration tests conducted in 2013 and comparing the data obtained with the results of a similar study for 2011–2012.
14 systems of large state and commercial companies, both Russian and foreign, were selected for the study. Most of them belong to the industry, and the list also includes telecoms, banks, and construction companies. More than a third of the companies studied are distributed systems with many branches in different cities and countries.
According to the data obtained, in 2013, 86% of corporate systems were exposed to vulnerabilities, which allowed them to gain complete control over critical resources - payment systems, e-mail, personal data and document repositories, ERP systems (for example, SAP), process control systems. Half of the systems reviewed allowed for complete control of critical resources by an external attacker. For every third system (29%), in order to gain control over such resources, it is enough to have access to the user segment of the internal network.
')
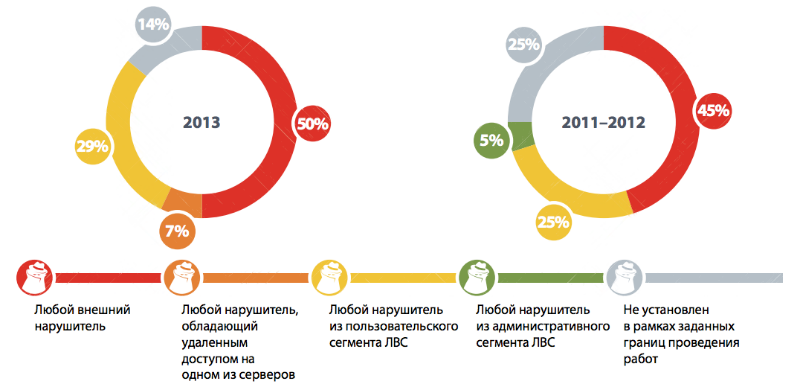
Only 14% of the most important resources are protected in practice, and not on paper.
More than half (57%) of the systems studied in 2013 contained critical vulnerabilities associated with the use of outdated software and operating system versions, which is worse than the results of previous years (45%). The average age of the most outdated unspecified updates is 32 months. In one of the systems, the dangerous vulnerability of 9 years ago (2004) was identified.
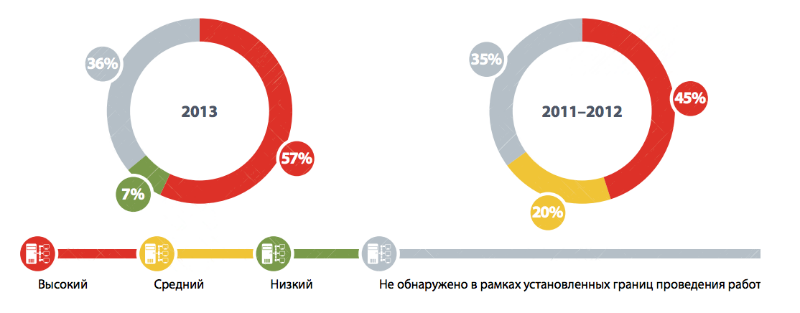
57% of systems have critical vulnerabilities that are easily fixed by installing updates.
On average, in 2013 an external attacker was required to use only two vulnerabilities to overcome the perimeter of the corporate network (in previous years, three steps were required). To conduct an attack in 82% of cases, a hacker needs to have a medium or low qualification.
The level of security of internal networks also decreased compared with 2011-2012. Only in 17% of cases, the internal attacker must be highly qualified to gain access to critical resources, and in half of all the systems studied, successful attacks are possible from any unqualified user of the internal network.
Such a deterioration of the situation is due to the fact that threats are growing faster than protection: cyber defense technologies barely change, while the methods and tools of intruders are developing very actively.
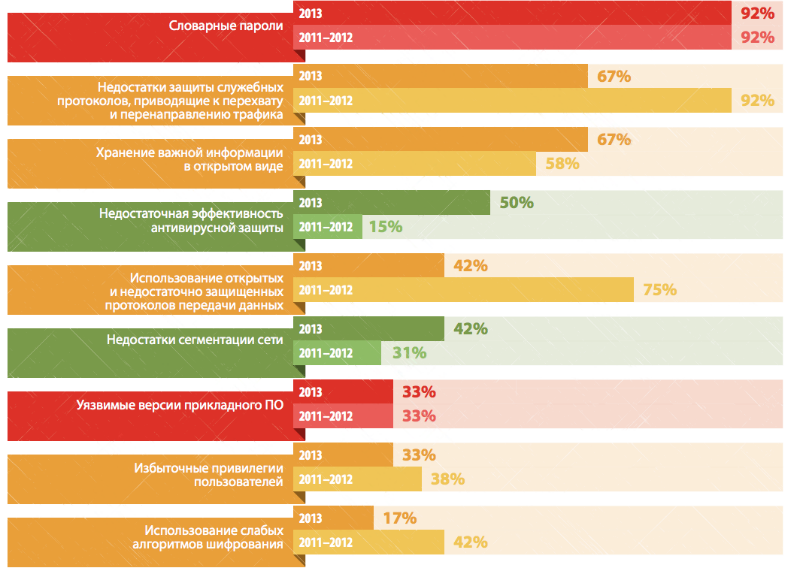
Top 10 vulnerabilities are headed by weak passwords
For both external attacks and internal intruders, the most common vulnerability is weak passwords. For example, the password “123456” was used by the administrators of the internal networks in every third system.
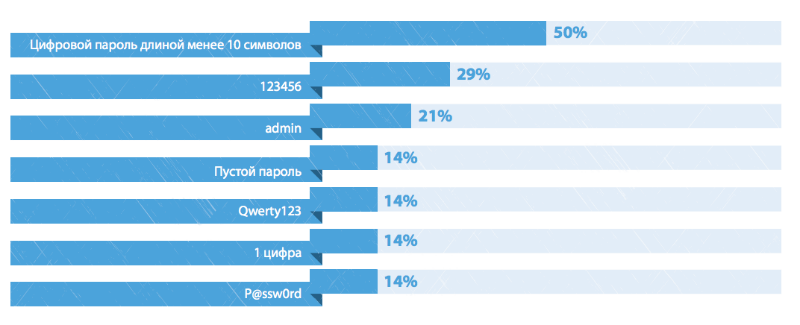
Top Admin Passwords
However, there are positive news: the awareness of employees of companies in security issues in 2013 has noticeably improved. The number of clicks on a potentially malicious link received in an e-mail (from 19% to 11%) decreased, there were fewer cases of entering credentials in fake forms and launching attached files (4% vs. 18% in the previous two years). However, the number of users who entered into an online dialogue with a potential attacker, remained at the level of previous years (3%).
The full text of the study “ Vulnerability statistics of corporate information systems (2013) ” can be found on the website of the Positive Technologies research center.
14 systems of large state and commercial companies, both Russian and foreign, were selected for the study. Most of them belong to the industry, and the list also includes telecoms, banks, and construction companies. More than a third of the companies studied are distributed systems with many branches in different cities and countries.
According to the data obtained, in 2013, 86% of corporate systems were exposed to vulnerabilities, which allowed them to gain complete control over critical resources - payment systems, e-mail, personal data and document repositories, ERP systems (for example, SAP), process control systems. Half of the systems reviewed allowed for complete control of critical resources by an external attacker. For every third system (29%), in order to gain control over such resources, it is enough to have access to the user segment of the internal network.
')

Only 14% of the most important resources are protected in practice, and not on paper.
More than half (57%) of the systems studied in 2013 contained critical vulnerabilities associated with the use of outdated software and operating system versions, which is worse than the results of previous years (45%). The average age of the most outdated unspecified updates is 32 months. In one of the systems, the dangerous vulnerability of 9 years ago (2004) was identified.

57% of systems have critical vulnerabilities that are easily fixed by installing updates.
On average, in 2013 an external attacker was required to use only two vulnerabilities to overcome the perimeter of the corporate network (in previous years, three steps were required). To conduct an attack in 82% of cases, a hacker needs to have a medium or low qualification.
The level of security of internal networks also decreased compared with 2011-2012. Only in 17% of cases, the internal attacker must be highly qualified to gain access to critical resources, and in half of all the systems studied, successful attacks are possible from any unqualified user of the internal network.
Such a deterioration of the situation is due to the fact that threats are growing faster than protection: cyber defense technologies barely change, while the methods and tools of intruders are developing very actively.

Top 10 vulnerabilities are headed by weak passwords
For both external attacks and internal intruders, the most common vulnerability is weak passwords. For example, the password “123456” was used by the administrators of the internal networks in every third system.

Top Admin Passwords
However, there are positive news: the awareness of employees of companies in security issues in 2013 has noticeably improved. The number of clicks on a potentially malicious link received in an e-mail (from 19% to 11%) decreased, there were fewer cases of entering credentials in fake forms and launching attached files (4% vs. 18% in the previous two years). However, the number of users who entered into an online dialogue with a potential attacker, remained at the level of previous years (3%).
The full text of the study “ Vulnerability statistics of corporate information systems (2013) ” can be found on the website of the Positive Technologies research center.
Source: https://habr.com/ru/post/233671/
All Articles