All broken
I present to you the translation of the article “ Everything is Broken” , published in May 2014 on The Medium by the American journalist Quinn Norton, who specializes in information security issues. The article examines the modern world of information technology and the place of data security and privacy issues in it. The article in some places contains rather harsh criticism, however, the problems raised in it are relevant and not resolved to this day. Ultimately, this is partly the job of a journalist - asking uncomfortable questions.
One day, a friend of mine got control of thousands of computers. He found a software vulnerability and began testing it. In the process, he realized that, theoretically, he could gain full administrative control over the entire network where this software is used. He uploaded the script to a remote server and ran it to see what would happen, and he went to sleep. The next morning, he decided to check the result of the work, and what was his surprise when he discovered that he had full access on 50,000 computers. Frightened of responsibility for his actions, he immediately stopped the process and began to delete his scripts. Ultimately, as he told me, he even destroyed the hard drive, throwing it into a fire. I can not give you the identity of this person, because I do not want him to be in the Federal Prison, which would have happened if he had reported the found vulnerability and his experiment to someone else. You might be wondering if this bug is fixed now? Perhaps yes, but certainly not thanks to my friend. This story is not so amazing. Spend time on the hacker scene and you'll hear worse stories.
It is difficult to explain to ordinary people how many technologies work very mediocre and that their lives have long been closely intertwined with IT infrastructure, like pressed wire.
')
Computers and computer technology - everything is broken.
For many of us, especially those who monitor security and unauthorized interception of information, these revelations are not a big surprise. We may not know all the specifics of the issue, but people who follow different software know that computer technology is going through hard times. We knew that for many years there were people who were ready to take advantage of these problems, like hawks circling over their prey. The NSA is not and has never been the most dangerous predator on the Internet. They are simply the largest garbage collector. But they are doing their job so well, not because they are all-powerful mages of mathematics.
NSA is doing its job as well as software is bad.
Eight months before the revelation of Edward Snowden, I tweeted this:
It was my annoyed admission that trying to find good software was doomed from the start. Developed by people who don’t have enough money, that time, most programs see the light at the moment when they are good enough to allow someone to go home and finally see their family. What we end up with is basically terrible.
Software is so bad because it is so complicated, because it interacts with other programs on the computer and other programs on other computers. Even your computer is a computer inside a computer, boxes inside other mailboxes, and each of these computers is full of small programs trying to interact with each other. Computers are becoming more and more complex over time, and people are still the same.
Your average Windows desktop is so complex that no one on earth knows everything about how and how it actually works.
Now imagine - billions of black boxes inside other boxes are constantly trying to interact with each other, at about the same time. They share gigabytes of data, and send commands from smaller programs to larger programs, such as a browser. This is the Internet. And all this should happen at the same time and smoothly, otherwise you will get into hysterics, because your chosen movie tickets have disappeared from the basket.
Our attention is often paid to the fact that your phone, on which you play casual games and which you hold in the toilet of the bar, has much more computing power than all the computing power used to launch rockets into space in the last century.
NASA had a huge staff of geniuses in order to create and use software of that era. Your phone has only you.
In addition, you are constantly postponing the automatic update, because it distracts you with your reminders from the game in Candy Crush Saga.
Because of all this, safety suffers in the first place. In addition to the fact that programs have rather annoying bugs, programs often have a special kind of vulnerability, called 0-day. Nothing can protect you from 0-day. Zero in the name of this term is the number of days that developers have to correct the problem. There are no dangerous 0-day, there are dangerous, and there are catastrophic. It is like giving the keys to the house to the first comer. I guarantee you that right now you are reading this on a device with all three types of 0-day. I hear you say, "But Quinn, if no one knows about them, how did you know about them?" That's because even high-quality software should interact with far less high-quality software. People whose job it is to make the software more secure can fit in a big bar. I saw them drinking together. And it does not console. The question is not whether there is a vulnerability, the question is when it will be exploited.
This refers to a case that really happened a few years ago. To fix a bug in one piece of software, a Debian developer simply commented out a line in another, not realizing that he left the encryption system vulnerable to attack.
Look at it from the other side - every time when you apply security updates (in my case almost daily on my Linux computer), they may contain potential vulnerabilities. And who knows how long they will exist. Maybe days, maybe years. Nobody advertises this part of the updates. People say: “You have to apply this critical patch!” Meaning “... because the developers have screwed up so much that your child’s personal data, probably now, has already been sold to the Estonian Mafia”

Truly bad bugs (and who knows which ones are present in the system when you click Restart Later?) Can be exploited by hackers, the government, and other individuals who scan the network to determine the version of software being used for which there are exploits. Any computer that successfully passes the scan says “Hey, it's me! I'm vulnerable! ”And the next second can become part of a botnet, along with thousands and hundreds of thousands of other computers. Often these computers are hacked again and become the property of another botnet. Some botnets even close the vulnerability after installation so that the computer does not go to the "competitors". How can you know that such a misfortune happened to you? No It's funny if your stay online is already rented by the hour.
Next time you will not think that your grandmother is so cool, giving her credit for her help to dangerous Russian criminals who extort money from offshore casinos, arranging DDOS attacks.
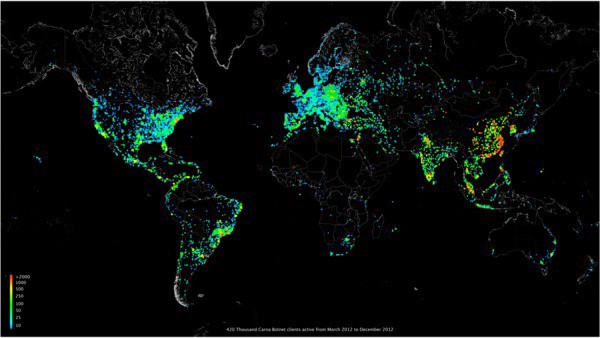
A map showing hacked computers during the “Internet census”
Not so long ago, one hacker wrote a script to gain control over embedded devices running Linux. These hacked devices scanned the rest of the Internet, and created a report that told us about Internet security more than we ever knew. The small cracked boxes gave back the full report (cumulatively about 10 TB) and quietly deactivated the hacking fact. It was a useful example of how the whole planet was mixed up with shit. If this were really malware, we would be in a very difficult situation.
This is because almost all computers are poorly protected - in hospitals, governments, banks, phones, traffic lights, as well as controlling switches, smart meters and air traffic control systems. Industrial computers that support infrastructure and production are even worse protected. Although I don’t know all the details, in these areas people think least about security. Another friend of mine stopped the work of the factory by sending a distorted ping request at the very beginning of the penetration test. For those who do not know, ping is the smallest request that you can send from one computer to another on the network. It took them a day to get everything back to working condition.
Computer experts love to pretend that they use a completely different, higher-quality software class, which is made of brilliant mathematical excellence, and whose interfaces can not be compared with any competitor. It is not true. The main form of security for this software is the unknown - so few people use this software that there is no point in looking for vulnerabilities in it. Well, only if you are not the NSA, and you want to spy, including for system administrators.
Let's take as an example one of these programs that an ordinary user will not use: OTR. OTR or Off The Record Messaging, is used for messaging and provides an encryption layer, on top of plain text. It’s as if you’ve used AIM or Jabber, or whatever you’re using, and communicate using code sequences. The computer generates such coded sequences for you. OTR is a promising and impenetrable technology, it has been carefully studied, and we can say with great certainty that it does not contain such unpleasant 0-day as those described above.
And besides, with a high degree of probability, OTR is not a program that you use.
There is a specification and library for software that supports OTR, but it still does not allow using it. It still has to be implemented in software by some not so brilliant people, for use by others, also not so brilliant people. Now you know that it usually ends in tears.
OTR is mainly used in a library called libpurple . If you want to see information security snobs distressed, remind libpurple. Libpurple is written in a programming language called C.
C works well for two things: for beauty and for creating catastrophic 0-day vulnerabilities in memory operations.

Heartbleed is a bug affecting servers around the world. It was used to leak passwords, encryption keys, and who knows what else? Classic C in all its glory.
Libpurple was written by people who wanted their open-source chat to interact with any instant messaging system in the world, and didn’t know anything about security and encryption. Security experts who audited the code said that there are so many potential ways to exploit libpurple vulnerabilities that there is no point in fixing them. Just throw everything away and rewrite from scratch. These were not bugs that allow you to read your encrypted messages, no. These were the bugs that allowed access to the computer: to see everything you enter, everything you read, and probably would allow watching through the webcam as you pick your nose.
This great tool, OTR, has been implemented in libpurple, on most systems that use it. Let me clarify something, because maybe even some geeks have still not understood: it does not matter how good your encryption algorithm is, if an attacker can just read the data from the screen, along with the user, and I guarantee you that they can. They may know how to do this or still not know it, but nevertheless there is such an opportunity. There are hundreds of such libpurple on your computer: small software components developed by people with a limited budget and deadlines who did not know or did not care about the security of the rest of the system.
Any of the small bugs allowed in them can be used to access everything else on your computer. We are updated again and again, and maybe new updates will be able to protect user data. Or maybe not. Nobody knows.
When we notify you that you need to apply new updates, we are not saying that you need to repair your ship. We say that you need to scoop out water faster than it reaches your neck.
To get a little away from the topic, from all this horror and chaos, let me say that the situation has become better than it was before. We have tools that weren't in the nineties, for example, sandboxes that run potentially vulnerable programs, where they can cause the rest of the system not much harm. (The sandbox keeps the program in a small artificial part of the computer, cutting it off from interacting with other programs, or discards all data generated by the program from launch to launch.)
The history of the struggle with a whole class of terrible mistakes was similar to the history of the struggle of humanity with smallpox. Security issues are now more relevant than ever before, and there are organizations fighting the spread of malware around the clock. But they can't really keep up with the times. The ecosystem of such problems has become much wider than it was even 10 years ago, and now it’s hard to believe that we can make progress.
“I trust you ...” is a phrase that I would like to hear the least from my anonymous sources. No doubt, it would be followed by information that they should not have divulged to me. But it’s so common for a person to share something personal with someone you trust. In such cases, I usually hurry to remind the interlocutor with irritation that all their data passes through countless servers, switches, routers, before reaching the destination point. I think this is obvious, but I will repeat it anyway: people never think about these things.
No one can use the software correctly. Absolutely everyone does it wrong. OTR starts encryption only after the first message, a fact that leading information security experts and hackers from 20 countries have lost sight of. Managing all public and private keys to ensure security on all devices, websites and accounts is theoretically possible. With the same success as cut his appendix. This, too, is theoretically possible. One guy did something like this in Antractide , why can't you?

With every malware expert I know, it happened that they mistakenly ran some kind of suspicious program instead of examining it before that. I know this because once this happened to me, I opened an infected PDF file, although I knew something was wrong with it. My friends, of course, laughed at me, but then calmly confessed that they, too, had made such mistakes. If some of the leading experts in the field of malware cannot keep track of all the infected files, why do you hope that your parents will not open the e-card that you allegedly sent.
The email you receive every day can be sent from anywhere - people can write any address in the From message header, and any of the executable files in attachments (such as Word, Excel or PDF files) can use a fresh 0-day opening This is probably the answer to the question why your grandmother started working for Russian criminals and why competitors find out about your plans long before the announcement. On the other hand, if you avoid viewing attachments, it means that you are not able to support office work in the modern world. That's the whole choice: constantly take the risk of being infected with malware or live under a bridge, leaving notes on the lawn of your former home, telling your children how you love them and how you miss them.
Data security and privacy experts notify the public about such problems, but keeping track of all this information is about as unusual and difficult as taking a blood test every morning. The consequences of neglecting one’s own privacy can be frightening to the public. And in each individual case, the consequences will be even worse. And all this is a real war of attrition between what we want for ourselves, for our family, and what we must do to survive as humans. This is a real Mexican duel, supported by corporations and controlled by the government.
I live in the midst of this and I'm no better. One day, an anonymous source asked me to confirm my identity. I had to take some photos showing the location and time of day. I had to download them and give access to my source. As a result, I still had to postpone identification, because I nervously turned off my computer before the files were transferred. “Why me?” I asked him. He answered: "Because only you are so stupid."
Touché.
But if I, being a trained person who tries to pay attention to these things all the time, I can allow this to be true of ordinary people.
A few years ago, I conducted a survey among fairly respected people involved in software security.
First of all, I have to explain something:
Most users do not have rights to install software on the computers they use.
That is, most computer users are not their owners. Whether it is located in an internet cafe, or at school or at work — it’s not so easy to install your software on a computer by a user on such a computer. Every week or two I was contacted by people who despaired of trying to ensure the security and confidentiality of the data, and I would like to help them. I would write them "Download this program here ...", and we would end on this. But the next thing people write to me is that they cannot install this software on their computers. Usually, this happened because in their IT department restrictions were placed on user rights as part of network management. These people needed applications that could work with limited rights, basically I mean browsers.
And so I asked the hackers, computer security experts, programmers the following question: “What should people do in cases when they cannot download and install new software on their computer, due to limited rights?”. All unanimously answered: "Nothing." They did not know what to do in such cases. It would be better for them to stop speaking in plain language, but they said to me: “Well, but they have no false sense of security.” I was told that if they do not have access to the best software, they should not interfere with the people who follow them. But I tried to explain that these people can be activists, organizers, journalists, dealing with governments, corporations and criminal organizations that cause real harm to people, these people are in great danger. I was told that in this case they should acquire computers for themselves and work for them.
Here is the answer: be rich enough to buy your own computer or trample. I told people that he wasn’t good enough, but it all ended in small tweets, and then we split up.
Soon after, I understood where our mutual understanding spread. I returned to this conversation again and tried to explain to the experts: even in the most dangerous situations, when people are in real danger, even when armed people begin to hunt them, even when encryption and confidentiality do not help - even then people do not stop publishing. They just hope they won't get it.
Here lies the same reason that lotteries have been around for thousands of years, despite the low chances of winning: “Maybe everything will be fine, maybe it's worth trying”
In the face of hostile organizations, technically unfamiliar activists try to be careful in their correspondence. In this matter, they are as good as Anomymous. Otherwise, people are warned that they need to worry about metadata, be careful on social networks and be aware of things like the first OTR message. People are adapting.
These interviews became a wake-up call for some interlocutors who did not understand that people who are activists of organizations and journalists regularly engage in such risky things. These interlocutors eventually took my side, realizing that even something imperfect could be better than nothing. But many others still live in their ideal world, where their perfect code is written.

There is an intelligence organization called IC . And they could like us if they stopped spying on us all the time, while they would like us to stop whining about it all the time.
After spending some time with them, I understand why they ignore all complaints. IC is one of the largest organizations in the world engaged in wiretapping. They carefully gather information and know a lot about their colleagues, their bosses, their lawyers, the staff of other agencies, the president, and sometimes even some members of Congress. Their lives are being watched, and they do not complain about it.
Despite all the calls for increased supervision, man will neglect them, such is his nature. You are not going to explain to agents that this is bad, while continuing to do the same.
There will always be loopholes, and as long as there are loopholes, or until the same things can be interpreted in different ways, the interception will be carried out as much as possible. People are mostly selfish beings. Agents, being humans, will never know why living without keeping some information secret is bad while they do it.
However, this is only the tip of the iceberg. What they do to alleviate the possibility of espionage is a cultural catastrophe. The most disturbing of these things are the 0day market, the introduction of exploits and the weakening of standards.The question is who wants to be part of "us", to assert that we are supposedly safe, with all these exploits, wiretapping, message decryption and data collection. When they attacked Natanz with the help of the Stuxnet virus and left all other nuclear installations vulnerable, we quietly informed the public that “we,” in this matter, begins and ends directly with IC. And this is the biggest danger.
If the IC or the Department of Defense or the executive branch consider themselves to be true Americans, and the rest are simply subordinate Americans, or even people not connected with the USA, we just have to be below the grass and quieter than water until time passes.
We are less and less worthy of rights and respect in the eyes of the IC. When the NSA injects exploits and hinders the cryptographic protection for our infrastructure, this means that they will use these exploits against people who are not part of the NSA, simply not fixing them. We can only protect ourselves after they secure themselves.
In theory, the reason for which we respect the soldiers, is that we have certain customs, the essence of which is in honoring the soldiers, as they sacrifice themselves for the good of the people. But with the NSA everything is exactly the opposite. Our well-being is being sacrificed to make their work of observing the world easier. When it is part of the cult of power, it only contributes to its abuse.
But the biggest of all cultural problems lies with another group that I haven’t considered yet - normal people living their lives alongside all this madness.
The problems of ordinary users and technologies are exactly the same as the problems of politicians and ordinary people, or the problems of society as a whole. People believe that they are powerless and lonely, but the only thing that makes people believe that they are powerless and alone is faith itself. People working together are immensely and terribly powerful.
Of course, there is a limit to what people who can share the same dream can do, but we have not yet discovered it.
Facebook and Google seem very powerful, but from complete ruin, in this case, they are separated somewhere in about a week. They know that the “fee” for individual removal from social networks is high, but on a massive scale it is almost absent. Windows can be replaced with something better. The US government may resign due to mass protests in a matter of days. Of course, this will not solve all the problems, because corporations and the government would rather accept the demands than die. These organizations are doing everything that they can get away with, but we forget that this is exactly what we are trying to do to them.
Computers do not provide security and privacy of data, not because it is mathematically impossible. There are many ways to securely encrypt your data, many ways to ensure privacy, to make our computers work better by default. This is not happening because there are not so smart people. This is not happening because we do not require.
So yes, geeks, their leaders, agents and the military put the world in an awkward position. But in the end, this is the work of people acting together - to return it to normal.
Added a small poll:
One day, a friend of mine got control of thousands of computers. He found a software vulnerability and began testing it. In the process, he realized that, theoretically, he could gain full administrative control over the entire network where this software is used. He uploaded the script to a remote server and ran it to see what would happen, and he went to sleep. The next morning, he decided to check the result of the work, and what was his surprise when he discovered that he had full access on 50,000 computers. Frightened of responsibility for his actions, he immediately stopped the process and began to delete his scripts. Ultimately, as he told me, he even destroyed the hard drive, throwing it into a fire. I can not give you the identity of this person, because I do not want him to be in the Federal Prison, which would have happened if he had reported the found vulnerability and his experiment to someone else. You might be wondering if this bug is fixed now? Perhaps yes, but certainly not thanks to my friend. This story is not so amazing. Spend time on the hacker scene and you'll hear worse stories.
It is difficult to explain to ordinary people how many technologies work very mediocre and that their lives have long been closely intertwined with IT infrastructure, like pressed wire.
')
Computers and computer technology - everything is broken.
Do it badly and they will come
For many of us, especially those who monitor security and unauthorized interception of information, these revelations are not a big surprise. We may not know all the specifics of the issue, but people who follow different software know that computer technology is going through hard times. We knew that for many years there were people who were ready to take advantage of these problems, like hawks circling over their prey. The NSA is not and has never been the most dangerous predator on the Internet. They are simply the largest garbage collector. But they are doing their job so well, not because they are all-powerful mages of mathematics.
NSA is doing its job as well as software is bad.
Eight months before the revelation of Edward Snowden, I tweeted this:
Everything has 0-day vulnerabilities, everything can be tracked, access to any information, everything is vulnerable. Everything, his mother, has already been hacked.
It was my annoyed admission that trying to find good software was doomed from the start. Developed by people who don’t have enough money, that time, most programs see the light at the moment when they are good enough to allow someone to go home and finally see their family. What we end up with is basically terrible.
Software is so bad because it is so complicated, because it interacts with other programs on the computer and other programs on other computers. Even your computer is a computer inside a computer, boxes inside other mailboxes, and each of these computers is full of small programs trying to interact with each other. Computers are becoming more and more complex over time, and people are still the same.
Your average Windows desktop is so complex that no one on earth knows everything about how and how it actually works.
Now imagine - billions of black boxes inside other boxes are constantly trying to interact with each other, at about the same time. They share gigabytes of data, and send commands from smaller programs to larger programs, such as a browser. This is the Internet. And all this should happen at the same time and smoothly, otherwise you will get into hysterics, because your chosen movie tickets have disappeared from the basket.
Our attention is often paid to the fact that your phone, on which you play casual games and which you hold in the toilet of the bar, has much more computing power than all the computing power used to launch rockets into space in the last century.
NASA had a huge staff of geniuses in order to create and use software of that era. Your phone has only you.
In addition, you are constantly postponing the automatic update, because it distracts you with your reminders from the game in Candy Crush Saga.
Because of all this, safety suffers in the first place. In addition to the fact that programs have rather annoying bugs, programs often have a special kind of vulnerability, called 0-day. Nothing can protect you from 0-day. Zero in the name of this term is the number of days that developers have to correct the problem. There are no dangerous 0-day, there are dangerous, and there are catastrophic. It is like giving the keys to the house to the first comer. I guarantee you that right now you are reading this on a device with all three types of 0-day. I hear you say, "But Quinn, if no one knows about them, how did you know about them?" That's because even high-quality software should interact with far less high-quality software. People whose job it is to make the software more secure can fit in a big bar. I saw them drinking together. And it does not console. The question is not whether there is a vulnerability, the question is when it will be exploited.

This refers to a case that really happened a few years ago. To fix a bug in one piece of software, a Debian developer simply commented out a line in another, not realizing that he left the encryption system vulnerable to attack.
Look at it from the other side - every time when you apply security updates (in my case almost daily on my Linux computer), they may contain potential vulnerabilities. And who knows how long they will exist. Maybe days, maybe years. Nobody advertises this part of the updates. People say: “You have to apply this critical patch!” Meaning “... because the developers have screwed up so much that your child’s personal data, probably now, has already been sold to the Estonian Mafia”

Truly bad bugs (and who knows which ones are present in the system when you click Restart Later?) Can be exploited by hackers, the government, and other individuals who scan the network to determine the version of software being used for which there are exploits. Any computer that successfully passes the scan says “Hey, it's me! I'm vulnerable! ”And the next second can become part of a botnet, along with thousands and hundreds of thousands of other computers. Often these computers are hacked again and become the property of another botnet. Some botnets even close the vulnerability after installation so that the computer does not go to the "competitors". How can you know that such a misfortune happened to you? No It's funny if your stay online is already rented by the hour.
Next time you will not think that your grandmother is so cool, giving her credit for her help to dangerous Russian criminals who extort money from offshore casinos, arranging DDOS attacks.

A map showing hacked computers during the “Internet census”
Not so long ago, one hacker wrote a script to gain control over embedded devices running Linux. These hacked devices scanned the rest of the Internet, and created a report that told us about Internet security more than we ever knew. The small cracked boxes gave back the full report (cumulatively about 10 TB) and quietly deactivated the hacking fact. It was a useful example of how the whole planet was mixed up with shit. If this were really malware, we would be in a very difficult situation.
This is because almost all computers are poorly protected - in hospitals, governments, banks, phones, traffic lights, as well as controlling switches, smart meters and air traffic control systems. Industrial computers that support infrastructure and production are even worse protected. Although I don’t know all the details, in these areas people think least about security. Another friend of mine stopped the work of the factory by sending a distorted ping request at the very beginning of the penetration test. For those who do not know, ping is the smallest request that you can send from one computer to another on the network. It took them a day to get everything back to working condition.
Computer experts love to pretend that they use a completely different, higher-quality software class, which is made of brilliant mathematical excellence, and whose interfaces can not be compared with any competitor. It is not true. The main form of security for this software is the unknown - so few people use this software that there is no point in looking for vulnerabilities in it. Well, only if you are not the NSA, and you want to spy, including for system administrators.
Okay, well written chat with encryption. What can go wrong?
Let's take as an example one of these programs that an ordinary user will not use: OTR. OTR or Off The Record Messaging, is used for messaging and provides an encryption layer, on top of plain text. It’s as if you’ve used AIM or Jabber, or whatever you’re using, and communicate using code sequences. The computer generates such coded sequences for you. OTR is a promising and impenetrable technology, it has been carefully studied, and we can say with great certainty that it does not contain such unpleasant 0-day as those described above.
And besides, with a high degree of probability, OTR is not a program that you use.
There is a specification and library for software that supports OTR, but it still does not allow using it. It still has to be implemented in software by some not so brilliant people, for use by others, also not so brilliant people. Now you know that it usually ends in tears.
OTR is mainly used in a library called libpurple . If you want to see information security snobs distressed, remind libpurple. Libpurple is written in a programming language called C.
C works well for two things: for beauty and for creating catastrophic 0-day vulnerabilities in memory operations.

Heartbleed is a bug affecting servers around the world. It was used to leak passwords, encryption keys, and who knows what else? Classic C in all its glory.
Libpurple was written by people who wanted their open-source chat to interact with any instant messaging system in the world, and didn’t know anything about security and encryption. Security experts who audited the code said that there are so many potential ways to exploit libpurple vulnerabilities that there is no point in fixing them. Just throw everything away and rewrite from scratch. These were not bugs that allow you to read your encrypted messages, no. These were the bugs that allowed access to the computer: to see everything you enter, everything you read, and probably would allow watching through the webcam as you pick your nose.
This great tool, OTR, has been implemented in libpurple, on most systems that use it. Let me clarify something, because maybe even some geeks have still not understood: it does not matter how good your encryption algorithm is, if an attacker can just read the data from the screen, along with the user, and I guarantee you that they can. They may know how to do this or still not know it, but nevertheless there is such an opportunity. There are hundreds of such libpurple on your computer: small software components developed by people with a limited budget and deadlines who did not know or did not care about the security of the rest of the system.
Any of the small bugs allowed in them can be used to access everything else on your computer. We are updated again and again, and maybe new updates will be able to protect user data. Or maybe not. Nobody knows.
When we notify you that you need to apply new updates, we are not saying that you need to repair your ship. We say that you need to scoop out water faster than it reaches your neck.
To get a little away from the topic, from all this horror and chaos, let me say that the situation has become better than it was before. We have tools that weren't in the nineties, for example, sandboxes that run potentially vulnerable programs, where they can cause the rest of the system not much harm. (The sandbox keeps the program in a small artificial part of the computer, cutting it off from interacting with other programs, or discards all data generated by the program from launch to launch.)
The history of the struggle with a whole class of terrible mistakes was similar to the history of the struggle of humanity with smallpox. Security issues are now more relevant than ever before, and there are organizations fighting the spread of malware around the clock. But they can't really keep up with the times. The ecosystem of such problems has become much wider than it was even 10 years ago, and now it’s hard to believe that we can make progress.
People, by the way, are also broken
“I trust you ...” is a phrase that I would like to hear the least from my anonymous sources. No doubt, it would be followed by information that they should not have divulged to me. But it’s so common for a person to share something personal with someone you trust. In such cases, I usually hurry to remind the interlocutor with irritation that all their data passes through countless servers, switches, routers, before reaching the destination point. I think this is obvious, but I will repeat it anyway: people never think about these things.
No one can use the software correctly. Absolutely everyone does it wrong. OTR starts encryption only after the first message, a fact that leading information security experts and hackers from 20 countries have lost sight of. Managing all public and private keys to ensure security on all devices, websites and accounts is theoretically possible. With the same success as cut his appendix. This, too, is theoretically possible. One guy did something like this in Antractide , why can't you?

With every malware expert I know, it happened that they mistakenly ran some kind of suspicious program instead of examining it before that. I know this because once this happened to me, I opened an infected PDF file, although I knew something was wrong with it. My friends, of course, laughed at me, but then calmly confessed that they, too, had made such mistakes. If some of the leading experts in the field of malware cannot keep track of all the infected files, why do you hope that your parents will not open the e-card that you allegedly sent.
The email you receive every day can be sent from anywhere - people can write any address in the From message header, and any of the executable files in attachments (such as Word, Excel or PDF files) can use a fresh 0-day opening This is probably the answer to the question why your grandmother started working for Russian criminals and why competitors find out about your plans long before the announcement. On the other hand, if you avoid viewing attachments, it means that you are not able to support office work in the modern world. That's the whole choice: constantly take the risk of being infected with malware or live under a bridge, leaving notes on the lawn of your former home, telling your children how you love them and how you miss them.
Data security and privacy experts notify the public about such problems, but keeping track of all this information is about as unusual and difficult as taking a blood test every morning. The consequences of neglecting one’s own privacy can be frightening to the public. And in each individual case, the consequences will be even worse. And all this is a real war of attrition between what we want for ourselves, for our family, and what we must do to survive as humans. This is a real Mexican duel, supported by corporations and controlled by the government.
I live in the midst of this and I'm no better. One day, an anonymous source asked me to confirm my identity. I had to take some photos showing the location and time of day. I had to download them and give access to my source. As a result, I still had to postpone identification, because I nervously turned off my computer before the files were transferred. “Why me?” I asked him. He answered: "Because only you are so stupid."
Touché.
But if I, being a trained person who tries to pay attention to these things all the time, I can allow this to be true of ordinary people.
And finally, the culture is also broken.
A few years ago, I conducted a survey among fairly respected people involved in software security.
First of all, I have to explain something:
Most users do not have rights to install software on the computers they use.
That is, most computer users are not their owners. Whether it is located in an internet cafe, or at school or at work — it’s not so easy to install your software on a computer by a user on such a computer. Every week or two I was contacted by people who despaired of trying to ensure the security and confidentiality of the data, and I would like to help them. I would write them "Download this program here ...", and we would end on this. But the next thing people write to me is that they cannot install this software on their computers. Usually, this happened because in their IT department restrictions were placed on user rights as part of network management. These people needed applications that could work with limited rights, basically I mean browsers.
And so I asked the hackers, computer security experts, programmers the following question: “What should people do in cases when they cannot download and install new software on their computer, due to limited rights?”. All unanimously answered: "Nothing." They did not know what to do in such cases. It would be better for them to stop speaking in plain language, but they said to me: “Well, but they have no false sense of security.” I was told that if they do not have access to the best software, they should not interfere with the people who follow them. But I tried to explain that these people can be activists, organizers, journalists, dealing with governments, corporations and criminal organizations that cause real harm to people, these people are in great danger. I was told that in this case they should acquire computers for themselves and work for them.
Here is the answer: be rich enough to buy your own computer or trample. I told people that he wasn’t good enough, but it all ended in small tweets, and then we split up.
Soon after, I understood where our mutual understanding spread. I returned to this conversation again and tried to explain to the experts: even in the most dangerous situations, when people are in real danger, even when armed people begin to hunt them, even when encryption and confidentiality do not help - even then people do not stop publishing. They just hope they won't get it.
Here lies the same reason that lotteries have been around for thousands of years, despite the low chances of winning: “Maybe everything will be fine, maybe it's worth trying”
In the face of hostile organizations, technically unfamiliar activists try to be careful in their correspondence. In this matter, they are as good as Anomymous. Otherwise, people are warned that they need to worry about metadata, be careful on social networks and be aware of things like the first OTR message. People are adapting.
These interviews became a wake-up call for some interlocutors who did not understand that people who are activists of organizations and journalists regularly engage in such risky things. These interlocutors eventually took my side, realizing that even something imperfect could be better than nothing. But many others still live in their ideal world, where their perfect code is written.

There is an intelligence organization called IC . And they could like us if they stopped spying on us all the time, while they would like us to stop whining about it all the time.
After spending some time with them, I understand why they ignore all complaints. IC is one of the largest organizations in the world engaged in wiretapping. They carefully gather information and know a lot about their colleagues, their bosses, their lawyers, the staff of other agencies, the president, and sometimes even some members of Congress. Their lives are being watched, and they do not complain about it.
Despite all the calls for increased supervision, man will neglect them, such is his nature. You are not going to explain to agents that this is bad, while continuing to do the same.
There will always be loopholes, and as long as there are loopholes, or until the same things can be interpreted in different ways, the interception will be carried out as much as possible. People are mostly selfish beings. Agents, being humans, will never know why living without keeping some information secret is bad while they do it.
However, this is only the tip of the iceberg. What they do to alleviate the possibility of espionage is a cultural catastrophe. The most disturbing of these things are the 0day market, the introduction of exploits and the weakening of standards.The question is who wants to be part of "us", to assert that we are supposedly safe, with all these exploits, wiretapping, message decryption and data collection. When they attacked Natanz with the help of the Stuxnet virus and left all other nuclear installations vulnerable, we quietly informed the public that “we,” in this matter, begins and ends directly with IC. And this is the biggest danger.
If the IC or the Department of Defense or the executive branch consider themselves to be true Americans, and the rest are simply subordinate Americans, or even people not connected with the USA, we just have to be below the grass and quieter than water until time passes.
We are less and less worthy of rights and respect in the eyes of the IC. When the NSA injects exploits and hinders the cryptographic protection for our infrastructure, this means that they will use these exploits against people who are not part of the NSA, simply not fixing them. We can only protect ourselves after they secure themselves.
In theory, the reason for which we respect the soldiers, is that we have certain customs, the essence of which is in honoring the soldiers, as they sacrifice themselves for the good of the people. But with the NSA everything is exactly the opposite. Our well-being is being sacrificed to make their work of observing the world easier. When it is part of the cult of power, it only contributes to its abuse.
But the biggest of all cultural problems lies with another group that I haven’t considered yet - normal people living their lives alongside all this madness.
The problems of ordinary users and technologies are exactly the same as the problems of politicians and ordinary people, or the problems of society as a whole. People believe that they are powerless and lonely, but the only thing that makes people believe that they are powerless and alone is faith itself. People working together are immensely and terribly powerful.
Of course, there is a limit to what people who can share the same dream can do, but we have not yet discovered it.
Facebook and Google seem very powerful, but from complete ruin, in this case, they are separated somewhere in about a week. They know that the “fee” for individual removal from social networks is high, but on a massive scale it is almost absent. Windows can be replaced with something better. The US government may resign due to mass protests in a matter of days. Of course, this will not solve all the problems, because corporations and the government would rather accept the demands than die. These organizations are doing everything that they can get away with, but we forget that this is exactly what we are trying to do to them.
Computers do not provide security and privacy of data, not because it is mathematically impossible. There are many ways to securely encrypt your data, many ways to ensure privacy, to make our computers work better by default. This is not happening because there are not so smart people. This is not happening because we do not require.
So yes, geeks, their leaders, agents and the military put the world in an awkward position. But in the end, this is the work of people acting together - to return it to normal.
Added a small poll:
Source: https://habr.com/ru/post/233533/
All Articles