Free AnyConnect VPN Server equivalent

In my last note, I described the Softether VPN Server and how to install it from source. Since that time, I have been very disappointed in this server, because for all the time I could not get it to work at normal speed. I wrote to the developers forum, but did not get a clear answer what was the matter. Well, there is nothing to do that will have to choose another solution.
I tried the StrongSwan VPN server, but the server turned out to be difficult to configure, and it also failed to make money via http-Proxy (and by the way it should not).
In the end, I opted for the Open Connect Server, a free and excellent implementation of the Cisco AnyConnect server.
I think many of you are familiar with Any Connect server, a proprietary vpnserver for Cisco routers.
Unfortunately, I don’t have any information whether this program is in the Debian repository or in some other program, but we can compile it from source.
...
InstallNettle ()
{
if ["$ isget" = "get"]
then
rm -rfv ./nettle*
wget -c ftp.gnu.org/gnu/nettle/nettle-2.7.1.tar.gz
tar -xvf nettle-2.7.1.tar.gz
fi
cd nettle-2.7.1
#autoreconf
./configure --prefix = / --host = $ HOST
check_success
make V = 0 -j 4 LDFLAGS = "- ldl"
check_success
make V = 0 install DESTDIR = $ SYSROOT
check_success
cd ...
}
')
InstallGnutls ()
{
if ["$ isget" = "get"]
then
rm -rfv ./gnutls*
git clone git: //gitorious.org/gnutls/gnutls.git
fi
cd gnutls
make autoreconf
check_success
./configure --prefix = / --host = $ HOST NETTLE_CFLAGS = "- I $ SYSROOT / include" NETTLE_LIBS = "- L $ SYSROOT / lib -lnettle" \
HOGWEED_CFLAGS = "- I $ SYSROOT / include" HOGWEED_LIBS = "- L $ SYSROOT / lib -lhogweed" \
--disable-doc --with-default-trust-store-file = "/ etc / ssl / ca-bundle.crt" --enable-local-libopts = yes
check_success
make V = 0 -j 4
check_success
make V = 0 install DESTDIR = $ SYSROOT
check_success
cd ...
InstallOpenConnect ()
{
if ["$ isget" = "get"]
then
rm -rfv ./ocserv*
git clone git: //git.infradead.org/ocserv.git
fi
cd ocserv
make autoreconf
chmod + x ./autogen.sh
./autogen.sh
./configure --prefix = / --host = $ HOST LIBGNUTLS_CFLAGS = "- I $ SYSROOT / include" LIBGNUTLS_LIBS = "- L $ SYSROOT / lib -lgnutls" \
LIBREADLINE_CFLAGS = "- I $ SYSROOT / include / readline" LIBREADLINE_LIBS = "- L $ SYSROOT / lib -lreadline -lncurses" \
--enable-local-libopts = yes
check_success
make V = 0 AUTOGEN = "autogen"
check_success
sed -i -e 's | / bin / true | autogen | g' ./doc/Makefile
make V = 0 install DESTDIR = $ SYSROOT
check_success
cd ...
}
}
Certificate Generation
#! / bin / bash
certtool --generate-privkey --outfile ca-key.pem
cat << _EOF_> ca.tmpl
cn = "loft.dtdns.net"
organization = "loft inc."
serial = 1
expiration_days = 999
ca
signing_key
cert_signing_key
crl_signing_key
_EOF_
certtool --generate-self-signed --load-privkey ca-key.pem --template ca.tmpl --outfile ca-cert.pem
certtool --generate-privkey --outfile server-key.pem
cat << _EOF_> server.tmpl
cn = "loft.dtdns.net"
organization = "loft inc."
serial = 2
expiration_days = 999
signing_key
encryption_key #only if the generated key is an RSA one
tls_www_server
_EOF_
certtool --generate-certificate --load-privkey server-key.pem --load-ca-certificate ca-cert.pem --load-ca-privkey ca-key.pem --template server.tmpl --outfile server -cert.pem
mv -fv ./server-cert.pem / etc /
mv -fv ./server-key.pem / etc /
ocpasswd root -c / etc / ocpasswd
Settings file
max-clients = 16
max-same-clients = 16
tcp-port = 443
udp-port = 443
keepalive = 32400
dpd = 1900
mobile-dpd = 1800
try-mtu-discovery = false
auth = "plain [/ etc / ocpasswd]"
server-cert = /etc/server-cert.pem
server-key = /etc/server-key.pem
tls-priorities = "NORMAL:% SERVER_PRECEDENCE:% COMPAT"
auth-timeout = 4000
cookie-timeout = 300
deny-roaming = false
rekey-time = 172800
rekey-method = ssl
use-utmp = true
use-occtl = true
pid-file = /var/run/ocserv.pid
socket-file = / var / run / ocserv-socket
run-as-user = root
run-as-group = root
cgroup = "cpuset, cpu: test"
device = vpns
cisco-client-compat = true
predictable-ips = true
default-domain = example.com
# The pool of addresses that leases will be given from.
ipv4-network = 192.168.2.0
ipv4-netmask = 255.255.255.0
dns = 8.8.8.8
ping-leases = false
Unit to run in systemd
[Unit]
Description = OpenConnect server
After = network.target [Service]
Type = forking Environment = "LD_LIBRARY_PATH = / lib: / lib" PIDFile = / var / run / ocserv.pid
ExecStart = / sbin / ocserv --config = / etc / ocserv.conf Restart = always
[Install]
WantedBy = multi-user.target
After starting the server with the command "/ sbin / ocserv --config = / etc / ocserv.conf"
we can connect using the official AnyConnect Client.
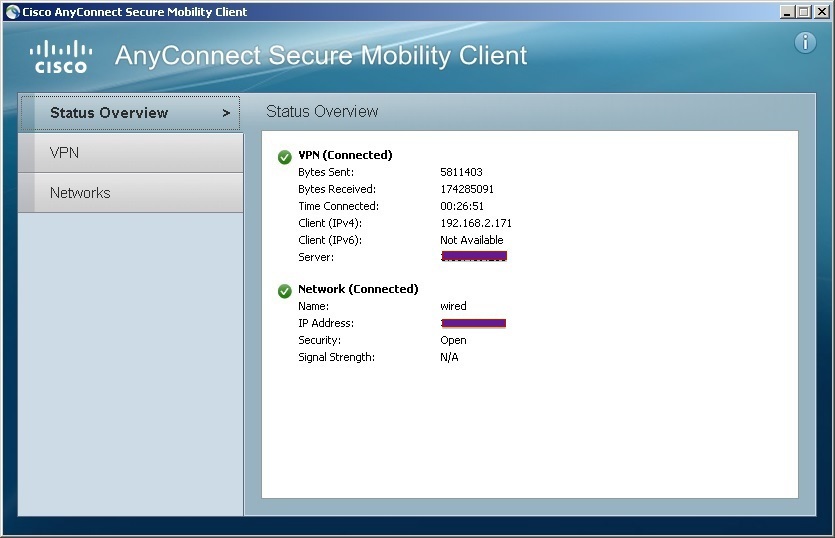
through the official iOS app.
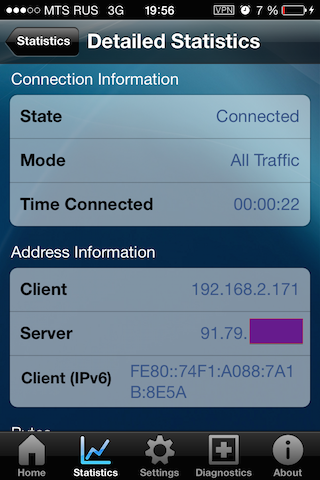
Well, in the end I want to say that I really liked the project. I corresponded with the developer and he answered me very promptly and in detail.
The server is very smart, it seemed to me that the speed is not cut at all
Do not pass by!
Source: https://habr.com/ru/post/231375/
All Articles