Researchers from Princeton discovered the “shadow” user identification tool in the AddThis plugin
The other day, several publications appeared on the Web at once, the topic of which is the hidden method of identifying users by visited sites. This method (called canvas fingerprint) is very difficult, if not impossible, to block using standard methods, such as blocking cookies or installing AddBlock or similar plug-ins.
However, this method of identification has already been found on 5% of the most popular sites in the world, including WhiteHouse.gov and YouPorn.com. The method itself is quite understandable: when entering any site with a user tracking code installed, such a resource requests the user's browser to render the hidden image, and the text is drawn using the available fonts and renderer. The font set and smoothing methods are slightly different on different machines. Renderer depends on browser version, OS and even GPU ( thanks to Goodkat for the addition ). As a result, the drawn image is unique.
')
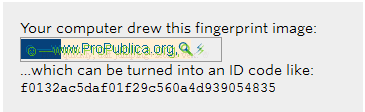 The drawn image can be used as a “fingerprint”, with a unique identifier assigned to the device. Well, and then, as they say, it is already a matter of technology - it is easy to track a PC with an assigned identifier and the actions of the owner of this PC on the Web. At the same time, as mentioned above, using standard methods to block such a method of identification is almost impossible.
The drawn image can be used as a “fingerprint”, with a unique identifier assigned to the device. Well, and then, as they say, it is already a matter of technology - it is easy to track a PC with an assigned identifier and the actions of the owner of this PC on the Web. At the same time, as mentioned above, using standard methods to block such a method of identification is almost impossible.The researchers found out that the code with the identifier was used on sites that collaborated with AddThis . As it turned out, this code is installed on 5% of 100 thousand top sites. Most of the "infected" sites used AddThis tools for social interaction, a set of plug-ins, where a site was built with instructions for the browser to draw the image.
All this is not something very new, similar methods of identifying users have been announced in 2012, researchers from the University of California.
In June, the Tor Project developers even added to their browser the function of notifying the user that a site is trying to use the described identification method. At the moment, no other browser developer company has offered a similar tool.
By the way, a year earlier, the Russian developer Valentin Vasilyev posted his code on the Web with a similar method of user identification. According to Vasiliev, the accuracy of identification using the latent image rendering is about 90%. According to Vasiliev , “Drawing a special image is only the first part. The main thing is to convert PNG to binary form, and then to base64. For this in modern browsers almost always meets the GPU. This is the difference in graphics processors and PNG decoding implementations and produces different base64 strings at the output. Canvas fingerprinting is just one of many sources that adds a few bytes to entropy. The main part is plugins and browser features. The cumulative imprint is built using all the possibilities. ”
At the same time, mobile devices are not very compatible with this method.
Representatives of AddThis, as far as can be judged, finalized the project of Vasilyev, and decided to try out their own code, placing it in their social plugin. According to company representatives, all of this was used not by malicious intent, but as a study of the possibility of replacing cookies with something else. And the sites that hosted the AddThis code were not notified of the presence of a site with an identification tool, so that the test results “in the field” were as real as possible.
In addition, AddThis reported that the data of already identified users were not used for any purpose other than the already mentioned study of the possibility of replacing cookies with alternative tools.
Via propublica
Source: https://habr.com/ru/post/230679/
All Articles