MAYHEM is a multipurpose bot for * NIX-servers. Investigation of Yandex. Security
UPD . A few hours after publication on Habré, the English version of this study by the Safe Search Team of Yandex is published on Virus Bulletin . Slightly more details and references to the bibliography.
Botnets from infected servers running an OS based on * nix are becoming increasingly popular with intruders. A wide channel, excellent uptime and powerful hardware make the server an attractive target for infection. It is considered that to fully infect * nix-systems, you must have root rights. However, the attackers come up with more and more new ways of extracting the maximum benefit from the infected server, while being content with small privileges. In this post we will tell about a rather non-standard botnet called MAYHEM, consisting of infected servers.

')
Initially, MAYHEM is a php script that, after launch, determines the system architecture (x86 or x64) and the presence of permissions to write to the current directory. In most cases, these privileges are available to the user under whom the web server is running, and in this case they are sufficient for the bot to work.

After the php script, it kills all the processes running under the current user “/ usr / bin / host”, extracts the shared object for the desired architecture (x86 or x64) and starts the process “/ usr / bin / host” with loading the shared object with the help of technology LD_PRELOAD.
The LD_PRELOAD technique is fairly well described. It allows you to load a shared object into the process address space before the original executable file. Also, this technique allows the substitution of functions, for example, the standard library. In short, if an object loaded via LD_PRELOAD exports some function that matches functions from other shared objects, then this function will be used.
Thus, the LD_PRELOAD technique makes it easy to intercept functions, which is what attackers use. In this case, the malicious object intercepts the exit function.
After starting and gaining control, the malicious shared object deletes the LD_PRELOAD environment variable and its body from the disk, and then produces several more anti-debugging techniques. As a result, practically no trace of its presence remains on the disk.
Further, if everything is all right, the configuration is decrypted, which is located in the data segment of this object. The configuration is encrypted using the XTEA algorithm (32 rounds) in ECB mode.

The configuration contains only three parameters: the URL of the command server (C & C), the file name with the hidden file system and the size of the hidden file system.
After initial setup, the bot determines whether a hidden file system is already created. If not, he creates it. The hidden file system is a disk image with the FAT file system, each block of which is encrypted with the XTEA algorithm (32 rounds, ECB mode). Work with FAT occurs using the open source library FAT 16/32 File System Library , and the encryption keys are generated from the block number in the file system and depend only on this number. This file system is used to store service files and bot plugins.
If the file system is successfully initialized or was created earlier, the bot moves to its main functions. First, he notifies the command server (C & C) about the start of work and then he receives and executes his commands: he downloads the necessary plug-in and tasks to it, creates a number of workflows and starts to execute the task.
As mentioned earlier, the bot expands its functionality with plug-ins. During the study, we were able to detect and analyze some of them. A set of plugins allows the botnet to perform the following tasks:
Thus, the modular structure allows the use of a botnet for a variety of tasks. Separately focus on C & C. In the course of research, we were able to detect three different command servers. One of them was no longer functioning, and the remaining two were used to control more than 1,400 bots.
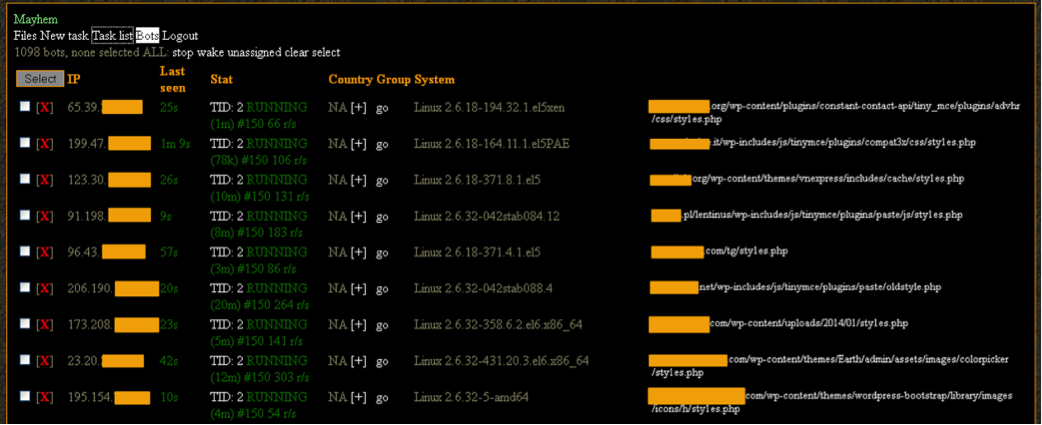
We analyzed the largest of the two command servers. General view of the botnet management system looks like this:
About 1100 bots were running under this server. The distribution of infected servers by country can be viewed on the map below. A darker tone means more infected servers.

Thus, the main part of the botnet was made up of servers located in Russia, the USA, Germany and Canada.
And this is how the interface looks like, which allows you to give a task to the entire botnet or separate groups of bots:

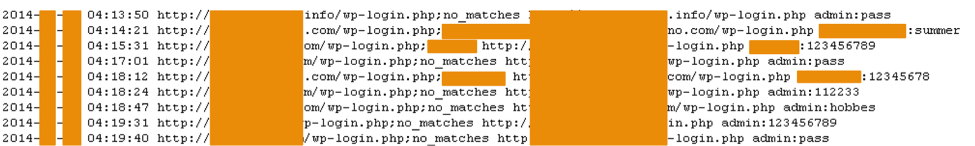
At the time of the study, this botnet was engaged in busting passwords for the administrative part of Wordpress CMS-based sites. The pictures below show the progress of the task and the part of the file with selected passwords - a report on the work done.

As you can see, users used weak passwords that are not robust.
Thus, to create a botnet from infected servers, it is not necessary to gain access to the server as root. Attackers are constantly inventing new ways to effectively use vulnerable sites and servers. Today they are ready to be content with even small privileges in the system. Keep this in mind when administering your servers and developing web applications, use brute-force passwords, update OpenSSL regularly and monitor the security of your web applications.
Take care of your users and your web servers.
Botnets from infected servers running an OS based on * nix are becoming increasingly popular with intruders. A wide channel, excellent uptime and powerful hardware make the server an attractive target for infection. It is considered that to fully infect * nix-systems, you must have root rights. However, the attackers come up with more and more new ways of extracting the maximum benefit from the infected server, while being content with small privileges. In this post we will tell about a rather non-standard botnet called MAYHEM, consisting of infected servers.

')
Initially, MAYHEM is a php script that, after launch, determines the system architecture (x86 or x64) and the presence of permissions to write to the current directory. In most cases, these privileges are available to the user under whom the web server is running, and in this case they are sufficient for the bot to work.

After the php script, it kills all the processes running under the current user “/ usr / bin / host”, extracts the shared object for the desired architecture (x86 or x64) and starts the process “/ usr / bin / host” with loading the shared object with the help of technology LD_PRELOAD.
The LD_PRELOAD technique is fairly well described. It allows you to load a shared object into the process address space before the original executable file. Also, this technique allows the substitution of functions, for example, the standard library. In short, if an object loaded via LD_PRELOAD exports some function that matches functions from other shared objects, then this function will be used.
Thus, the LD_PRELOAD technique makes it easy to intercept functions, which is what attackers use. In this case, the malicious object intercepts the exit function.
After starting and gaining control, the malicious shared object deletes the LD_PRELOAD environment variable and its body from the disk, and then produces several more anti-debugging techniques. As a result, practically no trace of its presence remains on the disk.
Further, if everything is all right, the configuration is decrypted, which is located in the data segment of this object. The configuration is encrypted using the XTEA algorithm (32 rounds) in ECB mode.

The configuration contains only three parameters: the URL of the command server (C & C), the file name with the hidden file system and the size of the hidden file system.
After initial setup, the bot determines whether a hidden file system is already created. If not, he creates it. The hidden file system is a disk image with the FAT file system, each block of which is encrypted with the XTEA algorithm (32 rounds, ECB mode). Work with FAT occurs using the open source library FAT 16/32 File System Library , and the encryption keys are generated from the block number in the file system and depend only on this number. This file system is used to store service files and bot plugins.

If the file system is successfully initialized or was created earlier, the bot moves to its main functions. First, he notifies the command server (C & C) about the start of work and then he receives and executes his commands: he downloads the necessary plug-in and tasks to it, creates a number of workflows and starts to execute the task.
As mentioned earlier, the bot expands its functionality with plug-ins. During the study, we were able to detect and analyze some of them. A set of plugins allows the botnet to perform the following tasks:
- Searches for sites vulnerable to Remote File Inclusion (RFI). The screenshot shows a piece of the list that is used to test the site.

- Definition of user names for sites based on Wordpress CMS. The bot receives from the command server a list of sites managed by Wordpress and, in the process, receives a list of registered users for each such site. This is done using a request of the following form:
< >/?author=<ID >. User IDs are enumerated in the range from 1 to 5. In the future, the collected data is used to select passwords. - Search authorization pages for sites on Joomla and Wordpress. The bot receives from C & C a list of sites and in the process of work tries to get the pages /wp-login.php or / administration /. If successful, it returns to the command server a list of sites on which these pages were found.
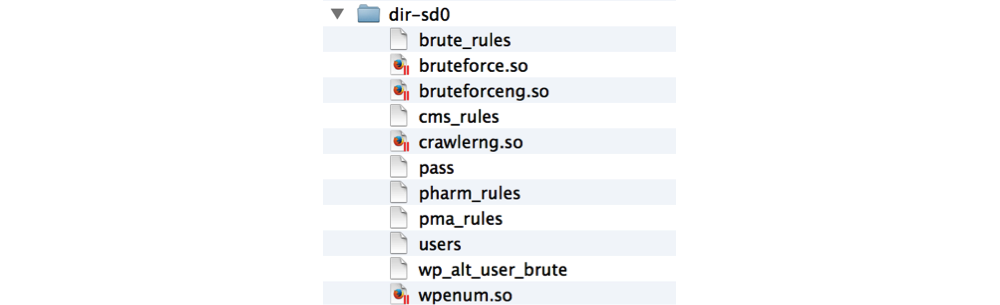
- Search of passwords for authorization pages of CMS and ISP-panels. This plugin is configured using a flexible system of rules and allows you to sort passwords for almost any authorization pages. An example of setting this plugin can be seen in the screenshot below.

To search through the attackers use a dictionary consisting of 17911 passwords with lengths from 1 to 32 characters. The cloud of these passwords serves as the title picture for this post. - Search for pages with a given theme. The plugin receives a list of sites, recursively circumvents them (the depth of the traversal is specified in the configuration) and collects the addresses of pages that satisfy a specific set of rules. An example of such a rule set is shown in the screenshot below.

- Plugins for brute force passwords of FTP accounts, plugins for bypassing IP address ranges, searching for phpMyAdmin and so on.
- Separately worth staying at the plugin to exploit the HeartBleed vulnerability Despite the fact that many system administrators have already updated OpenSSL, there are still quite a large number of vulnerable servers on the Internet.
Thus, the modular structure allows the use of a botnet for a variety of tasks. Separately focus on C & C. In the course of research, we were able to detect three different command servers. One of them was no longer functioning, and the remaining two were used to control more than 1,400 bots.
We analyzed the largest of the two command servers. General view of the botnet management system looks like this:

About 1100 bots were running under this server. The distribution of infected servers by country can be viewed on the map below. A darker tone means more infected servers.

Thus, the main part of the botnet was made up of servers located in Russia, the USA, Germany and Canada.
And this is how the interface looks like, which allows you to give a task to the entire botnet or separate groups of bots:

At the time of the study, this botnet was engaged in busting passwords for the administrative part of Wordpress CMS-based sites. The pictures below show the progress of the task and the part of the file with selected passwords - a report on the work done.


As you can see, users used weak passwords that are not robust.
Thus, to create a botnet from infected servers, it is not necessary to gain access to the server as root. Attackers are constantly inventing new ways to effectively use vulnerable sites and servers. Today they are ready to be content with even small privileges in the system. Keep this in mind when administering your servers and developing web applications, use brute-force passwords, update OpenSSL regularly and monitor the security of your web applications.
Take care of your users and your web servers.
Source: https://habr.com/ru/post/230167/
All Articles