Cisco Identity Services Engine
The practical value of the access control system to the corporate network based on the Cisco Identity Services Engine.
If the following words are not abstract concepts for you, but actual tasks - this article is for you:
● (network) security policy;
● reducing the risks of implementing information security threats;
● access control to the corporate network;
● automation of IT tasks;
● implementation of IT solutions that increase business dynamics (BYOD, Mobility).
Access control is a key measure of information security. The introduction of an access control system to an enterprise network will not only significantly reduce the risks of implementing information security threats, but also achieve economic benefits from the introduction of such systems.
')
The Cisco Identity Services Engine (Cisco ISE) is a multifunctional solution that covers the full range of issues of controlling access to the corporate network [CD]. Centralizing network access policies and automating a variety of routine tasks are key benefits of the Cisco ISE solution.
Access control in the corporate network
The project of introducing the CD system affects the interests of many departments in the enterprise:
● the access control task affects IT departments as the main actor;
● information security units are also interested in such projects in the context of the implementation of enterprise security policies;
● top management can get a significant benefit from the implementation of access control systems, as they contribute to the introduction of new business models, such as: Mobility (safe mobility of the employee’s workplace) and BYOD (use of personal devices for working with corporate data);
● for managers it is also an opportunity to achieve separation of powers and responsibilities of IT departments and information security departments, increase the response of the company's IT infrastructure to new business requirements, reduce operating costs and automate resource-intensive IT processes;
● users will be able to get their usual set of network services regardless of the location and method of connecting to the network.
Even at home on your own tablet, you can safely handle corporate information, receiving the same set of services as in the office with a wired connection or from a client via guest Wi-Fi. In the end, by introducing a CD system, you can get significant benefits for all departments of the enterprise.
The effectiveness of the CD system, as any high-tech tool, depends on how well it is used. Let us dwell on the issues that need to be remembered when planning the implementation of such systems.
Should all employees have equal access to all corporate information? Obviously not. This is prompted to us by the theory of information security and common sense. The secretary does not need to know the financial performance of the company; The accountant does not have to see in the corporate CRM contacts and schedule of the head. The company's customer base should not be accessible to the administrator of the company's mail server; The commercial director should not have access to the control technology network.
How was this question resolved earlier? Users were divided into groups by access level. For each group, settings were made at the employee connection ports on the network. It is more efficient to authenticate users when they log on to the network and apply access policies at the network connection point.
Corporate Directory Authentication
Maintaining a separate user base for each access control solution is inconvenient. There is a question of synchronization with other similar databases.
Most organizations have a corporate directory - a single place to store user data. Most often this is Microsoft Active Directory (MS AD), but it can also be an LDAP server. It is convenient to bring users in one place and manage most of the settings of their working environment. Many systems can receive data from the active directory: mail server, CRM, etc. The problem is that the “network”, as an entity, cannot authenticate in the active directory. There should be an intermediate device that understands, for example, MS AD and the network.
Using Cisco ISE as an intermediate device can easily solve this problem.
Read more in the video review:
RADIUS is one of the oldest and most common network authentication protocols. To authenticate users on the network, a RADIUS server must be deployed.
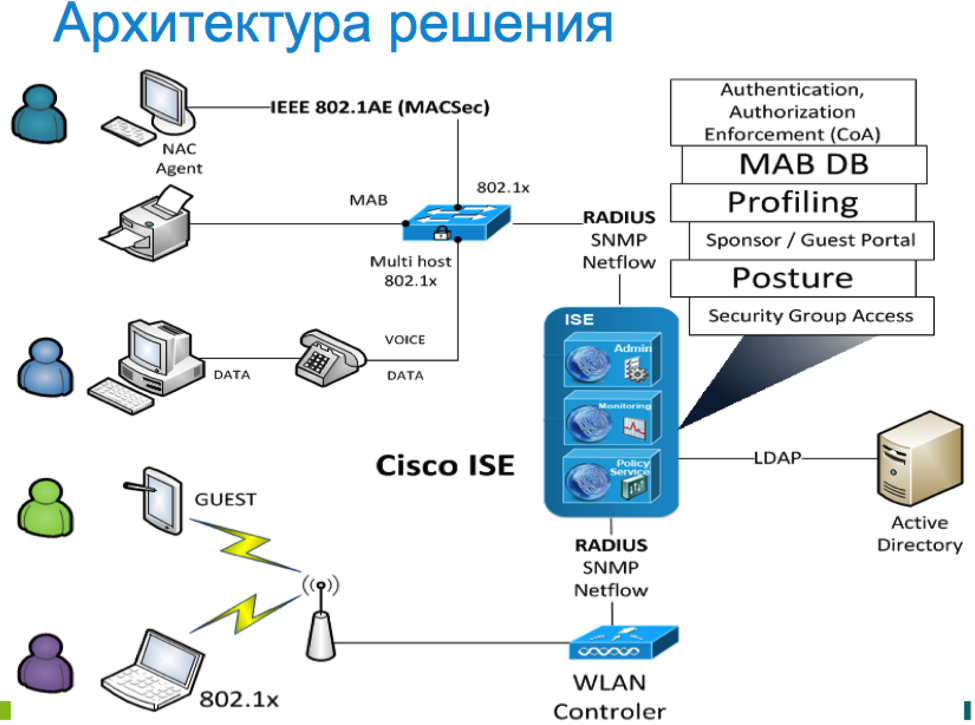
An example of the architecture of a solution based on Cisco ISE
In modern Cisco network designs, the role of such a RADIUS server is performed by Cisco ISE. In addition, Cisco ISE allows you to automate many tasks that inevitably arise in conjunction with projects implementing a RADIUS server to control network access.

Cisco ISE Solution Network Interaction Structure
Practical value for IT departments
Mobile gadgets have penetrated not only in our lives, but also in work. Who does not read corporate mail from your smartphone? The requirements of business and the modern world impose on the IT departments a rather difficult task - to provide users with access to corporate resources from any device.
Widespread mobilization has pushed for the development of Wi-Fi. Laptops have become the norm, and some even got rid of the wired interface, leaving only Wi-Fi. Moving with a laptop around the office and the ability to connect it to the network anywhere in the office - the actual requirements for the workplace.
Many people want to be able to use personal devices for work (BYOD). It's so easy to “be in touch” and “in work” when there is nothing else besides your tablet. Remote access via VPN has long been the norm for most organizations. IT departments have to synchronize access policies and settings across wired, wireless, and remote access devices.
The user must receive the same level of network services in order to effectively perform his work as a mobile employee. Business requirements for user mobility determine that the policy is not linked to the connection point, but to the user — this complicates network settings and maintenance.
Support issues are also multiplied by the number of possible network access options. Often, even for a basic assessment of current network problems, automation tools will be needed. To reduce the time for user support, it would be convenient to be able to see the username in all logs and monitoring windows. This eliminates the need to find out how and how a user is connected to the network.
Cisco ISE will allow you to solve a whole range of tasks related to CD.
Increase network observability and speed
To increase the observability and speed of solving problems, it is advisable to implement a single solution, deeply integrated into the existing infrastructure and linking all access policies on network equipment into one. This task for IT departments is solved by Cisco ISE.
Centralization and simplification of CD management
Cisco ISE allows you to simplify and centralize network access policies.
Corporate information has its own value. Network access control is one of the means of protecting information. With such a variety of connectivity options, manual policy management becomes time consuming. This introduces significant delays in the speed of network response to changes. Some tasks, such as monitoring the status of network connections in real time and retrospective, cannot be done manually and will unequivocally require the development of any scripts and putting all their functions together in one control system. The support of such solutions becomes, over time, an unbearable burden for IT. To be sure that only trusted devices in the enterprise network need to centralize network policy management and deep integration with other network services.
Automate routine tasks
By significantly reducing operational costs, you can improve the efficiency of IT and the enterprise as a whole. The introduction of automation tools for network access policies will allow to divide the tasks and areas of responsibility of IT and information security. Time spent on internal and external audits can also be minimized. All account information is stored in one place. It is always possible to assess the current state.
The implementation of the Cisco ISE access control automation solution will reduce the operating costs of maintaining all network services.
Cisco ISE will help accelerate the adoption of new business support technologies. Trends like Mobility, BYOD can be easily adopted by IT departments.
It should be noted that the use of Cisco ISE will significantly reduce costs in the data center through the use of new architectures and technologies (TrustSec / SGT). It is important to have a single solution connecting access policies on different devices: access switches, firewalls, data center infrastructure.
Thanks to Cisco ISE, it is possible to differentiate access according to a variety of criteria:
● who should have access;
● from which devices;
● what time of day;
● through which network devices;
● what level of access is needed.
All this determines the context of access to the network.
Practical value for information security units
Information security divisions are the main internal client for network access control solutions.
Access control is a primary security measure. Cisco ISE makes it possible to increase the ease of managing network access and dynamic monitoring of user connectivity to the network. Simplification and centralization of network access policies make it possible to look where previously not looked. Find the most problematic moments, take prompt measures to reduce information security risks.
Having at their disposal an effective tool that allows you to personalize access to the network, information security units significantly increase the efficiency of their daily work.

Access policy visualization example
The division of powers and responsibilities of IT and information security will allow better control over compliance with security policies. At the same time, audits can be conducted as soon as possible due to the availability of all accounting information and summarizing it in the form of detailed reports.
Cisco ISE makes it possible to deeply integrate the concept of network access context (who? How? From where? From which device?) Into a wide range of network and information security solutions.
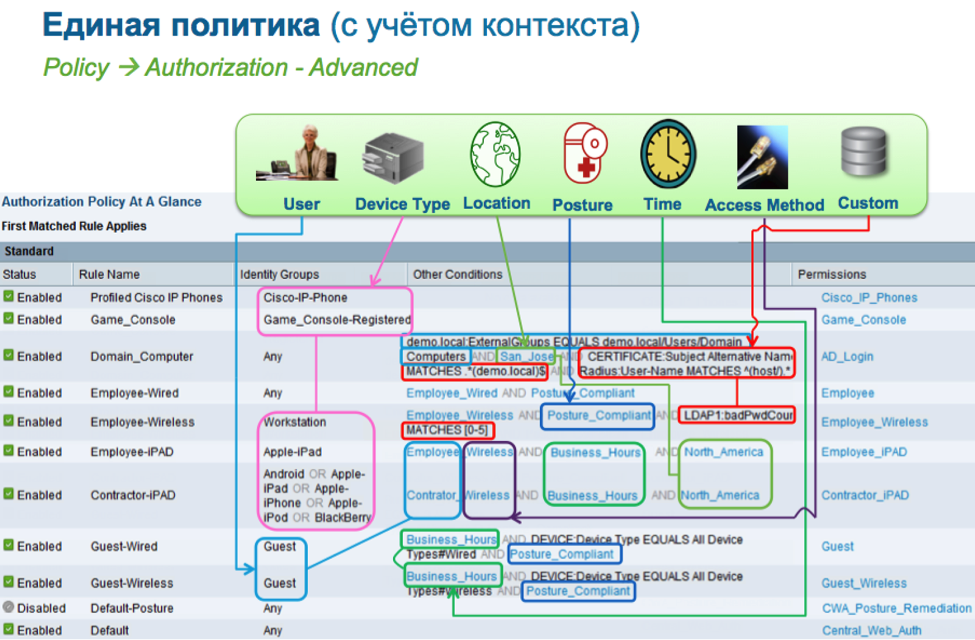
Policy example based on network access context
Thus, it is possible to achieve a significant reduction in the risks associated with the security of information.
Practical value for company management
Improving the operational efficiency of IT and IB will reduce costs and increase the “network” response to business requirements.
New business models, with the support of IT, will be able to get a new push. The introduction of the BYOD concept in an enterprise can be organically incorporated into the existing information security model due to the implementation of the Cisco ISE solution.
The introduction of high-quality automation and control equipment will help reduce the risks of information security and the expected losses as a result of information security incidents.
To ensure the necessary business dynamics, access policies must be tied to the user, not to the place and method of access. This important task ISE allows you to solve quickly and efficiently.
Read more in the analytical report "Increasing the value of workplace mobility . "
Cisco ISE will allow you to bundle disparate network access control components into a single architecture. The Cisco ISE solution is a key part of the secure access architecture for Cisco TrustSec corporate networks. Cisco's advanced approach to network access control has been repeatedly noted by analytical agencies such as Gartner.
Cisco ISE is part of a comprehensive modular TrustSec architecture.
TrustSec architecture tree
This allows you to be confident that the engineers who set up the solution have all the accompanying documents from the manufacturer for this, which has a positive effect on the speed and quality of project implementation.
Practical value for marketing departments
The company's image depends not only on the quality of the product being created, but also on the relationship with potential customers. Such image elements, like guest Wi-Fi access, will allow you to get a positive impression from customers.
The technologies incorporated in Cisco ISE allow you to enrich the client's portrait with the registration data that the client provides when registering in the guest network.
The starting page of the guest portal may contain a description of marketing campaigns or links to sections of the company's website.
Providing large-scale events with high-quality Wi-Fi service will also not be a problem. Cisco ISE allows you to generate access data for the list of visitors in advance.
Practical value for ordinary users
Employees will be able to more flexibly distribute their working time, without being tied to work with the walls of the office. In this case, the set of network services may be unchanged, which erases the boundaries of the workplace, transferring it to a more convenient plane. An employee who has the tools to find the optimal balance between work and personal time will be able to work more efficiently and with less labor.
Familiar personal devices (BYOD) can become reliable business companions.
More about Cisco ISE:
www.cisco.com/go/ise
Ovrashko Andrew,
Cisco Systems Engineer
Source: https://habr.com/ru/post/229525/
All Articles