TinyBanker banking trojan source leaked to network
A few years ago, our colleagues from CSIS Security Group were the first to write about the smallest banking Trojan "Tiny Banker" (aka Tinba, Zusy), which was known at that time. The size of the executable file is only about 20KB, as the authors used assembler for writing. Like many banking Trojans, he uses the technique of introducing (injection) his code into the browser and intercepts the necessary API calls to steal confidential bank data through form-grabbing and web-injects (the so-called Man-in-the-Browser attack). ). Detects ESET: Win32 / Tinba , Microsoft: Trojan: Win32 / Tinba.A , Symantec: Trojan.Tinba .
Recently on one of the underground forums there was information that the texts of the first version of Tinba are available for download. The archive includes the source code of the bot, as well as control panels, which attackers can use to obtain information about the bots. Tinba is focused on the popular web browsers MS Internet Explorer, Mozilla Firefox and Google Chrome, which is confirmed by the source code.
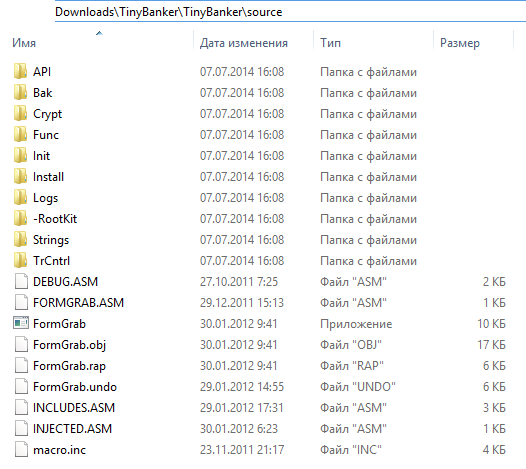
Fig. The source code of the bot Tinba. Visible files responsible for the form-grabbing browsers.
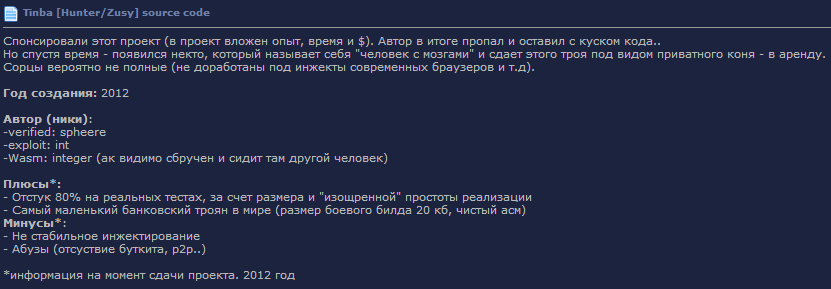
Fig. Information about the source code in a closed forum.
')
The consequences of uncovering similar sources of malicious software are difficult to overestimate, since this will enable attackers to create modified versions of this Trojan using an open code base. Last summer, we wrote about the leak of the giant Carberp source code archive, on the basis of which a number of new malicious programs have already been created.
One of the first versions of the malware based on these sources:
SHA256: 8cc5050f513ed22780d4e85857a77a1fb2a3083d792cd550089b64e1d2ef58e9
File size: 19968 bytes
Recently on one of the underground forums there was information that the texts of the first version of Tinba are available for download. The archive includes the source code of the bot, as well as control panels, which attackers can use to obtain information about the bots. Tinba is focused on the popular web browsers MS Internet Explorer, Mozilla Firefox and Google Chrome, which is confirmed by the source code.

Fig. The source code of the bot Tinba. Visible files responsible for the form-grabbing browsers.

Fig. Information about the source code in a closed forum.
')
The consequences of uncovering similar sources of malicious software are difficult to overestimate, since this will enable attackers to create modified versions of this Trojan using an open code base. Last summer, we wrote about the leak of the giant Carberp source code archive, on the basis of which a number of new malicious programs have already been created.
One of the first versions of the malware based on these sources:
SHA256: 8cc5050f513ed22780d4e85857a77a1fb2a3083d792cd550089b64e1d2ef58e9
File size: 19968 bytes
Source: https://habr.com/ru/post/229455/
All Articles