Microsoft and Adobe released a set of updates, July 2014
The company has released a set of updates for its products, which fix 29 unique vulnerabilities in Windows OS components and Internet Explorer web browser. Two fixes have Critical status and three Important. Critical update MS14-037 fixes 24 vulnerabilities in all versions of Internet Explorer 6-11 on all operating systems from Windows Server 2003 to Windows 8 / 8.1 (IE memory-corruption). Using these vulnerabilities, attackers can remotely execute code in a browser through a specially crafted web page (so-called drive-by downloads). A reboot is required to apply the patch.

Another critical update MS14-038 closes the CVE-2014-1824 vulnerability in the Windows Journaling component (Windows Journal) on Windows Vista +. Attackers can remotely execute the code they need through a specially crafted Windows log file. Such a file may be located on a malicious site, to which the victim may be redirected. The update corrects the necessary data in executable files that are responsible for processing the log files (Jnwdrv.dll, Jnwdui.dll, Jnwmon.dll, etc.).
')
The MS14-039 update fixes one CVE-2014-2781 vulnerability of the Elevation of Privelege type in the so-called. screen keyboard. Attackers can take advantage of this vulnerability to elevate their privileges to the current user in a low Integrity Level process (for example, the Internet Explorer tab process). To do this, use the on-screen keyboard feature. The update makes the necessary corrections to the system libraries, correcting flaws in the interaction of programs that operate at different levels of Integrity Level (new security flags in the KBDLLHOOKSTRUCT and MSLLHOOKSTRUCT structures ). Exploit code likely .
The MS14-040 update fixes one CVE-2014-1767 vulnerability of the Elevation of Privelege type in the afd.sys (Ancillary Function Driver) driver, which implements the kernel-mode network sockets mechanism (Winsock TCP / IP). The update is intended for users of all supported Microsoft OS. Provided that the attacker has credentials to access the target system, he can run a special application that will execute arbitrary code in kernel mode (user-mode restrictions). In addition, malicious code can also exploit the exploitation of this vulnerability to launch its code in kernel mode (Local Privelege Escalation exploit). The vulnerability is present in the driver function, which is responsible for checking the parameters passed from user mode. Exploit code likely .
The MS14-041 update fixes one CVE-2014-2780 vulnerability of the Elevation of Privelege type in the DirectShow component. Attackers can exploit this vulnerability to bypass the restrictions of the sandbox or Integrity Level browser (raise their privileges to the level of the current user). However, they must use another exploit for remote code execution. Exploit code likely .
1 - Exploit code likely
The probability of exploiting the vulnerability is very high, attackers can use an exploit, for example, for remote code execution.
2 - Exploit code would be difficult to build
The exploitation probability is average, since attackers are unlikely to be able to achieve a situation of sustainable exploitation, as well as due to the technical peculiarities of vulnerability and the complexity of developing an exploit.
3 - Exploit code unlikely
The exploitation probability is minimal and attackers are unlikely to be able to develop successfully working code and take advantage of this vulnerability to conduct an attack.
We recommend our users to install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (by default this option is enabled).

Adobe has released the APSB14-17 update for Flash Player. Updates fix three vulnerabilities: CVE-2014-0537, CVE-2014-0539, CVE-2014-4671, which can be used by attackers to install malicious code into the system (“allow”).
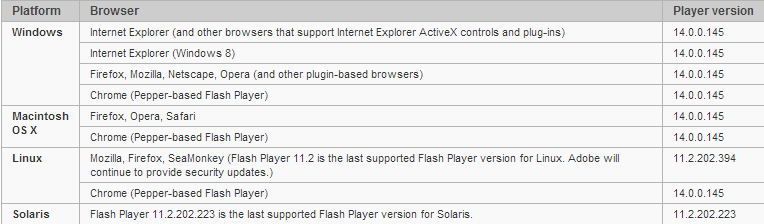
We recommend updating your Flash Player as soon as possible. Browsers such as Internet Explorer 10 & 11 on Windows 8 / 8.1 and Google Chrome update their Flash Player versions automatically. For IE, see the updated Security Advisory 2755801 . Check your version of Flash Player for relevance here , the table below shows these versions for various browsers.

be secure.

Another critical update MS14-038 closes the CVE-2014-1824 vulnerability in the Windows Journaling component (Windows Journal) on Windows Vista +. Attackers can remotely execute the code they need through a specially crafted Windows log file. Such a file may be located on a malicious site, to which the victim may be redirected. The update corrects the necessary data in executable files that are responsible for processing the log files (Jnwdrv.dll, Jnwdui.dll, Jnwmon.dll, etc.).
')
The MS14-039 update fixes one CVE-2014-2781 vulnerability of the Elevation of Privelege type in the so-called. screen keyboard. Attackers can take advantage of this vulnerability to elevate their privileges to the current user in a low Integrity Level process (for example, the Internet Explorer tab process). To do this, use the on-screen keyboard feature. The update makes the necessary corrections to the system libraries, correcting flaws in the interaction of programs that operate at different levels of Integrity Level (new security flags in the KBDLLHOOKSTRUCT and MSLLHOOKSTRUCT structures ). Exploit code likely .
The MS14-040 update fixes one CVE-2014-1767 vulnerability of the Elevation of Privelege type in the afd.sys (Ancillary Function Driver) driver, which implements the kernel-mode network sockets mechanism (Winsock TCP / IP). The update is intended for users of all supported Microsoft OS. Provided that the attacker has credentials to access the target system, he can run a special application that will execute arbitrary code in kernel mode (user-mode restrictions). In addition, malicious code can also exploit the exploitation of this vulnerability to launch its code in kernel mode (Local Privelege Escalation exploit). The vulnerability is present in the driver function, which is responsible for checking the parameters passed from user mode. Exploit code likely .
The MS14-041 update fixes one CVE-2014-2780 vulnerability of the Elevation of Privelege type in the DirectShow component. Attackers can exploit this vulnerability to bypass the restrictions of the sandbox or Integrity Level browser (raise their privileges to the level of the current user). However, they must use another exploit for remote code execution. Exploit code likely .
1 - Exploit code likely
The probability of exploiting the vulnerability is very high, attackers can use an exploit, for example, for remote code execution.
2 - Exploit code would be difficult to build
The exploitation probability is average, since attackers are unlikely to be able to achieve a situation of sustainable exploitation, as well as due to the technical peculiarities of vulnerability and the complexity of developing an exploit.
3 - Exploit code unlikely
The exploitation probability is minimal and attackers are unlikely to be able to develop successfully working code and take advantage of this vulnerability to conduct an attack.
We recommend our users to install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (by default this option is enabled).

Adobe has released the APSB14-17 update for Flash Player. Updates fix three vulnerabilities: CVE-2014-0537, CVE-2014-0539, CVE-2014-4671, which can be used by attackers to install malicious code into the system (“allow”).
We recommend updating your Flash Player as soon as possible. Browsers such as Internet Explorer 10 & 11 on Windows 8 / 8.1 and Google Chrome update their Flash Player versions automatically. For IE, see the updated Security Advisory 2755801 . Check your version of Flash Player for relevance here , the table below shows these versions for various browsers.


be secure.
Source: https://habr.com/ru/post/229171/
All Articles