Cisco telemetry telemetry against cyber threats
Cyber Threat Defense (CTD) can detect and block complex attacks, including zero-day attacks, confidential information leaks and botnets. These are new mechanisms to combat advanced threats using network activity analysis, which will be revealed in an article on the example of OpenSSL HeartBleed.
The solution correlates and analyzes network telemetry collected by intelligent network equipment (in particular, switches, routers and Cisco firewalls), does not require the installation of agents on workstations and servers, and is able to scale for distributed networks of any size.

The traditional detection of attacks at the network level involves the collection and analysis of network traffic on a specific set of signatures that correspond to known attacks. This requires sensors (IDS / IPS) in key areas of the network that attempt to identify known bad patterns in network traffic. But for a number of reasons, this approach is no longer relevant in our time: first, signatures are helpless against zero-day attacks and advanced methods of disguising malicious code and control channels of botnets. Secondly, modern targeted attacks (APT) are able to “bypass” the traditional perimeter of the network, on which sensors are traditionally installed, and act from within the network. Internal networking between workstations and servers is usually out of sight of IDS / IPS. Since the installation of dedicated sensors within all network segments and the monitoring of each work station is a technically difficult and financially costly task.
')
For about 10 years, new approaches to identifying attacks have been developed in the industry by analyzing the behavior and anomalies of network traffic. In short, the behavior analysis systems reveal the known "bad behavior" of devices on the network, analyzing the network interaction. Elementary examples of this behavior are network scanning or opening a large number of TCP sessions.
Anomalies analysis reveals significant deviations of network device traffic from the “normal” traffic profile for a given device or group of devices. Anomalies analysis assumes availability of training and statistical analysis for building and updating the “normal” traffic profile. Examples of anomalies are a sudden increase in the Internet traffic of a workstation or a change in the structure of traffic (for example, an increase in encrypted SSL traffic) in comparison with the usual daily metrics for a given workstation. To identify bad behavior and anomalies in most cases, it is enough to analyze the main traffic parameters (telemetry) and there is no need to scrutinize the contents of each packet, as IPS does.

Each of these approaches has its own advantages and limitations:

The analysis of behavior and anomalies has much in common with each other and often these approaches are used together. Protection systems that are built on these principles are called Network Behavior Anomaly Detection (NBAD). It should be noted that NBAD systems do not replace, but complement traditional IDS / IPS in terms of detecting complex attacks and can be used together. IDS / IPS focuses on perimeter protection and critical network points. NBAD systems “penetrate the eye” deep into the entire network, collecting telemetry from network infrastructure devices and security devices.
NetFlow network protocol is an excellent source of information for security tasks. NetFlow was originally proposed by Cisco for network traffic accounting and monitoring as early as the 1990s. NetFlow collected statistics of network streams passing through the network infrastructure. A stream is a set of packets that pass in the same direction and have common parameters:
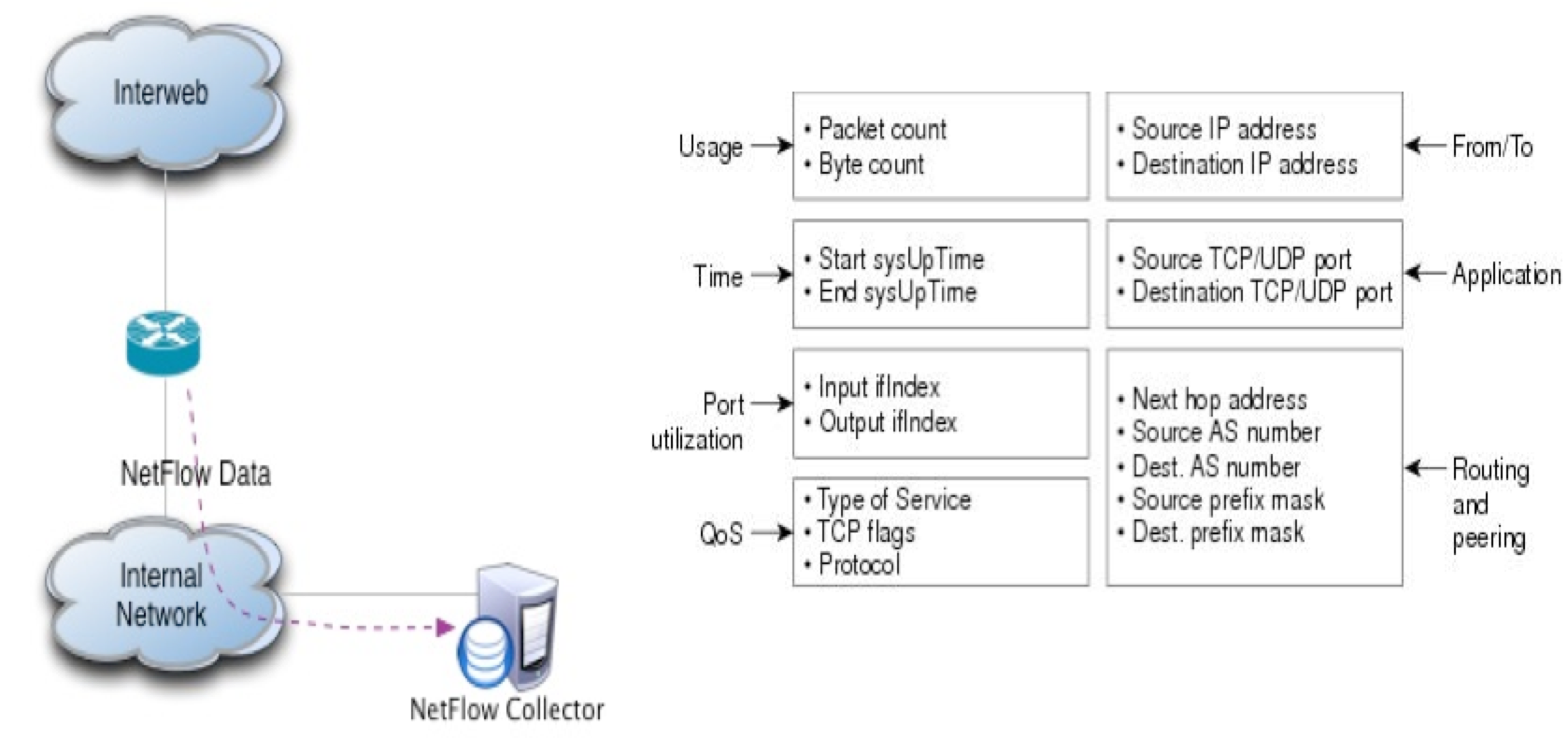
Over the past twenty years, NetFlow has been standardized as the IETF standard (IPFIX protocol) and has received many versions and extensions. NetFlow learned how to collect detailed granular statistics about traffic patterns, packet sizes and characteristics, fragmentation, and more. Information about applications can be added to NetFlow if DPI (Deep Packet Analysis) is enabled on network devices. Thus, using NetFlow, you can identify more than 1000 applications and, for example, differentiate normal web traffic from Skype or P2P file sharing sites on port 80. NetFlow statistics can be supplemented with information about the compliance of the flow of policies on the firewall, the content of the HTTP URL and other information of the application layer. Thus, the information obtained from NetFlow can be successfully used to analyze network behavior and identify security anomalies.
Another difference NetFlow - is the breadth of traffic grip. NetFlow is supported on all Cisco routers (including ISR G2 and ASR), Cisco ASA firewalls, and Catalyst 2960-X, 3560, 3750-X, 3850, 4500, 6500, and Nexus 7000 switches. Most recently, NetFlow support also appeared on server network interfaces Cisco UCS, which allows you to collect server traffic telemetry and virtual machine traffic. NetFlow and IPFIX are also supported by many other vendors and Open-Source products.
Thus, the NetFlow protocol can collect telemetry and provide visibility of attacks on all parts of the network - from the access level and data center to the remote branch office. In fact, NetFlow allows you to look into the "behavior" of a separate workstation and server without the need to install a software agent using only the infrastructure functionality.
NetFlow can count every packet it processes by providing a detailed analysis of all traffic. This distinguishes NetFlow from similar protocols such as sFlow, which are able to collect only aggregated statistics (sampled flow), analyzing every nth packet. Aggregated and full NetFlow can be compared with reading each page of the book and attentive page reading. Aggregated statistics gives a quick look at traffic, but worse for security tasks. Full NetFlow provides a comprehensive overview of network activity from a security point of view.
It is on the NetFlow protocol that the Cisco Cyber Threat Defense (CTD) cyber threat defense solution is based. The solution consists of several components:
The StealthWatch product is developed by Lancope in partnership with Cisco and is one of the oldest systems on the NBAD market. StealthWatch and ISE are available in both hardware and virtual device formats.
At the initial stage in Cyber Threat Defense it is necessary to describe the zones that make up the organization’s network. Such zones can be:
Zones can be nested in each other - for example, a data center zone, which includes zones for applications (web, mail servers, DNS servers, ERP). The web server zone, in turn, is divided into zones of external and internal web servers.
The more accurate the segmentation of the network into zones, the more accurate the solution will be able to analyze the telemetry and device behavior. CTD may suggest the likely assignment of devices and the ownership of devices in a particular zone. For example, if the server is the source of web traffic, you will be asked to assign this server to a group of web servers.
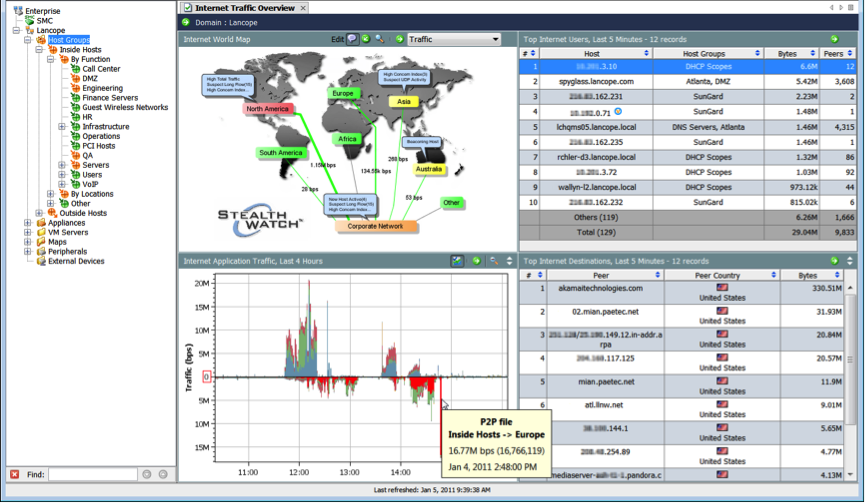
At the next stage, CTD collects NetFlow telemetry from the network infrastructure and builds network behavior profiles for zones and individual network devices. The initial self-study and adjustment takes place in the first 7 days, for the next 28 days the profile of normal behavior (baseline) is created. Profiles automatically adapt as traffic patterns gradually change.
If traffic deviates significantly from normal or “bad” behavior, a notification of a potential security incident will occur. When registering an incident, the key indicators are the numerical values:
These indices are calculated for all network hosts that are monitored by CTD, taking into account dozens of traffic parameters. The indices make it possible to track how abnormal the behavior of the hosts and the confidence of the system in the seriousness and reliability of this anomaly. Also, indexes allow prioritizing incident investigations. The higher the index value, the more dangerous the incident.
We give an example from life. If a bystander rings the doorbell and then reports that he had the wrong address, then there is no particular reason to worry. But if a passerby knocked on the tenth door in the same way, this would be a cause for concern. Thus, the concern index is 10.
Cyber Threat Defense comes in the same way - if the indexes exceed the threshold value, the corresponding alarm is generated. The system has a large number of standard policies for generating alarms and it is possible to create custom policies that describe unacceptable activity from the point of view of a particular organization.
In the work of the decision context is important. The NetFlow protocol usually operates with IP addresses and port numbers. Knowledge of the context allows Cyber Threat Defense to understand:
Thus, it becomes possible to “color” faceless information about IP addresses and ports, providing it with context, allowing you to more accurately and efficiently respond to security incidents.
Information about users and devices is gathered through the integration of CTD with the Cisco Identity Services Engine, which has intelligent mechanisms for identifying device types and user names on the network.
Reputation data of Internet hosts is obtained in real time from the cloud-based reputation database. This database in particular has dynamic information about active botnet control centers.
When the threshold value is reached, the CTD can perform a predetermined action. For example, issue a command to the firewall to block the suspicious activity of a specific host or block the switch port. Commands can be given automatically or semi-automatically (after confirmation by the administrator). The system has pre-installed scripts for routers and firewalls of different vendors, and it is also possible to create custom scripts.
Cyber Threat Defense can be used in different security scenarios to protect against more diverse attacks.
In particular, CTD can detect and help block the following types of attacks and anomalies affecting information security:

CTD is also an excellent tool for auditing information security, allowing you to check whether a network behaves as planned when setting up firewalls, IPS, and network infrastructure.
And, of course, Cyber Threat Defense can assist in the investigation of cyber incidents, the study of the propagation of malicious code and attack vectors. Since information is stored on all network flows and sessions, it is possible to find out with whom and how a suspicious host has interacted at a certain point in time in the past.
Consider the mechanisms of Cyber Threat Defense on the example of the high-profile vulnerability OpenSSL HeartBleed.
The difficulty in identifying HearBlead was that, if the attacker correctly exploited the vulnerability, there would be no traces of the exploit in the web server logs. Also, SSL encryption makes it difficult to differentiate between normal and malicious transactions by request content and signatures. Therefore, to identify attempts to exploit the vulnerability, it is necessary to focus on the characteristics of the size of SSL requests and responses of the web server.
If you look at the system report with attempts to exploit the HeartBleed vulnerability on a test system, you can see two features of these transactions.
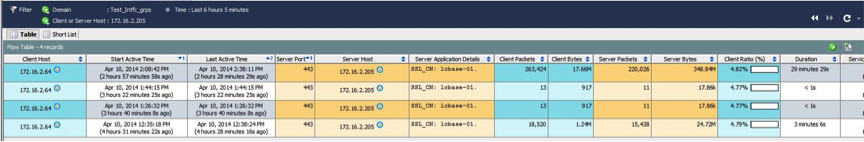
First, the ratio of the size of the client request and response is approximately 4.8%. Secondly, attacks aimed at HeartBleed are likely to create sessions with a longer lifetime. Each Heartbleed transaction returns a response to the attacker with the contents of a small piece of memory of the attacked web server. In order to obtain information of interest (SSL private keys or passwords), an attacker will have to repeat transactions many times and the user session will most likely last hours. CTD has a built-in mechanism for detecting such long-lived sessions (Suspect Long Flow).
Thus, using CTD, you can identify suspicious web transactions. Since NetFlow's network telemetry is usually stored for several months, it is also possible to find attacks that occurred in the past before the official publication of the vulnerability. Most importantly, to identify such attacks, you do not need to update signatures and the solution is able to find attacks from a “zero” day from the appearance of a vulnerability or exploit.
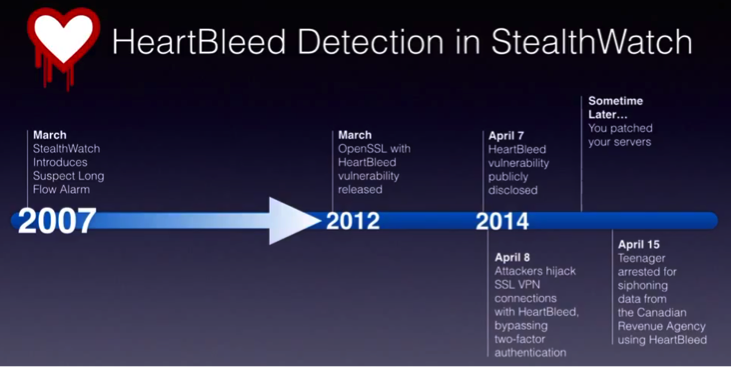
NetFlow is a great source of incident information, but not the only one. The development of Cisco Cyber Threat Defense is moving along the path of integration into the solution of additional sources of information - IPS SourceFire network, Cisco Advanced Malware Protection, email and web content filtering systems, cloud intelligence. The breadth of events, together with advanced processing and correlation technologies, will allow you to more accurately and quickly respond to the changing landscape of threats. Due to the limited size of the article, we focused only on the functionality of Cyber Threat Defense in terms of security. In fact, the CTD solution can also be very useful for IT administrators to monitor the network activity of users, monitor the use of network resources, analyze application performance and QoS. More on this in the following articles.
More information about the solution can be found at Cisco:
The solution correlates and analyzes network telemetry collected by intelligent network equipment (in particular, switches, routers and Cisco firewalls), does not require the installation of agents on workstations and servers, and is able to scale for distributed networks of any size.

New approaches to detect attacks
The traditional detection of attacks at the network level involves the collection and analysis of network traffic on a specific set of signatures that correspond to known attacks. This requires sensors (IDS / IPS) in key areas of the network that attempt to identify known bad patterns in network traffic. But for a number of reasons, this approach is no longer relevant in our time: first, signatures are helpless against zero-day attacks and advanced methods of disguising malicious code and control channels of botnets. Secondly, modern targeted attacks (APT) are able to “bypass” the traditional perimeter of the network, on which sensors are traditionally installed, and act from within the network. Internal networking between workstations and servers is usually out of sight of IDS / IPS. Since the installation of dedicated sensors within all network segments and the monitoring of each work station is a technically difficult and financially costly task.
')
For about 10 years, new approaches to identifying attacks have been developed in the industry by analyzing the behavior and anomalies of network traffic. In short, the behavior analysis systems reveal the known "bad behavior" of devices on the network, analyzing the network interaction. Elementary examples of this behavior are network scanning or opening a large number of TCP sessions.
Anomalies analysis reveals significant deviations of network device traffic from the “normal” traffic profile for a given device or group of devices. Anomalies analysis assumes availability of training and statistical analysis for building and updating the “normal” traffic profile. Examples of anomalies are a sudden increase in the Internet traffic of a workstation or a change in the structure of traffic (for example, an increase in encrypted SSL traffic) in comparison with the usual daily metrics for a given workstation. To identify bad behavior and anomalies in most cases, it is enough to analyze the main traffic parameters (telemetry) and there is no need to scrutinize the contents of each packet, as IPS does.

Each of these approaches has its own advantages and limitations:

The analysis of behavior and anomalies has much in common with each other and often these approaches are used together. Protection systems that are built on these principles are called Network Behavior Anomaly Detection (NBAD). It should be noted that NBAD systems do not replace, but complement traditional IDS / IPS in terms of detecting complex attacks and can be used together. IDS / IPS focuses on perimeter protection and critical network points. NBAD systems “penetrate the eye” deep into the entire network, collecting telemetry from network infrastructure devices and security devices.
NetFlow is a valuable source of security telemetry
NetFlow network protocol is an excellent source of information for security tasks. NetFlow was originally proposed by Cisco for network traffic accounting and monitoring as early as the 1990s. NetFlow collected statistics of network streams passing through the network infrastructure. A stream is a set of packets that pass in the same direction and have common parameters:
- Source / Destination Address
- Source / destination port for UDP and TCP
- Message Type and Code for ICMP,
- IP protocol number
- Network interface
- IP Type of Service.

Over the past twenty years, NetFlow has been standardized as the IETF standard (IPFIX protocol) and has received many versions and extensions. NetFlow learned how to collect detailed granular statistics about traffic patterns, packet sizes and characteristics, fragmentation, and more. Information about applications can be added to NetFlow if DPI (Deep Packet Analysis) is enabled on network devices. Thus, using NetFlow, you can identify more than 1000 applications and, for example, differentiate normal web traffic from Skype or P2P file sharing sites on port 80. NetFlow statistics can be supplemented with information about the compliance of the flow of policies on the firewall, the content of the HTTP URL and other information of the application layer. Thus, the information obtained from NetFlow can be successfully used to analyze network behavior and identify security anomalies.
Another difference NetFlow - is the breadth of traffic grip. NetFlow is supported on all Cisco routers (including ISR G2 and ASR), Cisco ASA firewalls, and Catalyst 2960-X, 3560, 3750-X, 3850, 4500, 6500, and Nexus 7000 switches. Most recently, NetFlow support also appeared on server network interfaces Cisco UCS, which allows you to collect server traffic telemetry and virtual machine traffic. NetFlow and IPFIX are also supported by many other vendors and Open-Source products.
Thus, the NetFlow protocol can collect telemetry and provide visibility of attacks on all parts of the network - from the access level and data center to the remote branch office. In fact, NetFlow allows you to look into the "behavior" of a separate workstation and server without the need to install a software agent using only the infrastructure functionality.
NetFlow can count every packet it processes by providing a detailed analysis of all traffic. This distinguishes NetFlow from similar protocols such as sFlow, which are able to collect only aggregated statistics (sampled flow), analyzing every nth packet. Aggregated and full NetFlow can be compared with reading each page of the book and attentive page reading. Aggregated statistics gives a quick look at traffic, but worse for security tasks. Full NetFlow provides a comprehensive overview of network activity from a security point of view.
Cisco cyber defense solution
It is on the NetFlow protocol that the Cisco Cyber Threat Defense (CTD) cyber threat defense solution is based. The solution consists of several components:
- network infrastructure (switches, routers, firewalls) with support for NetFlow protocol,
- Lancope StealthWatch network traffic analysis system
- Optional Cisco Identity Services Engine (ISE) that adds context information.
The StealthWatch product is developed by Lancope in partnership with Cisco and is one of the oldest systems on the NBAD market. StealthWatch and ISE are available in both hardware and virtual device formats.
At the initial stage in Cyber Threat Defense it is necessary to describe the zones that make up the organization’s network. Such zones can be:
- the local network,
- branches,
- workstations integrated by destination or location
- servers grouped by available services and applications, etc.
Zones can be nested in each other - for example, a data center zone, which includes zones for applications (web, mail servers, DNS servers, ERP). The web server zone, in turn, is divided into zones of external and internal web servers.
The more accurate the segmentation of the network into zones, the more accurate the solution will be able to analyze the telemetry and device behavior. CTD may suggest the likely assignment of devices and the ownership of devices in a particular zone. For example, if the server is the source of web traffic, you will be asked to assign this server to a group of web servers.

At the next stage, CTD collects NetFlow telemetry from the network infrastructure and builds network behavior profiles for zones and individual network devices. The initial self-study and adjustment takes place in the first 7 days, for the next 28 days the profile of normal behavior (baseline) is created. Profiles automatically adapt as traffic patterns gradually change.
If traffic deviates significantly from normal or “bad” behavior, a notification of a potential security incident will occur. When registering an incident, the key indicators are the numerical values:
- The alarm index - the Concern Index (CI) - an indicator that a particular host is the source of unacceptable or abnormal activity;
- Target Index - Target Index (TI) - an indicator that the host is a possible target of an attack or anomalous activity;
- File Sharing Index (FSI) - tracks potential P2P activity.
These indices are calculated for all network hosts that are monitored by CTD, taking into account dozens of traffic parameters. The indices make it possible to track how abnormal the behavior of the hosts and the confidence of the system in the seriousness and reliability of this anomaly. Also, indexes allow prioritizing incident investigations. The higher the index value, the more dangerous the incident.
We give an example from life. If a bystander rings the doorbell and then reports that he had the wrong address, then there is no particular reason to worry. But if a passerby knocked on the tenth door in the same way, this would be a cause for concern. Thus, the concern index is 10.
Cyber Threat Defense comes in the same way - if the indexes exceed the threshold value, the corresponding alarm is generated. The system has a large number of standard policies for generating alarms and it is possible to create custom policies that describe unacceptable activity from the point of view of a particular organization.
Add context
In the work of the decision context is important. The NetFlow protocol usually operates with IP addresses and port numbers. Knowledge of the context allows Cyber Threat Defense to understand:
- which user and device is hidden by this or that IP address,
- which application is using this port
- what is the reputation of the IP address or domain name and whether the Internet host was noticed earlier in the unlawful activity (for example, in the work of the botnet).
Thus, it becomes possible to “color” faceless information about IP addresses and ports, providing it with context, allowing you to more accurately and efficiently respond to security incidents.
Information about users and devices is gathered through the integration of CTD with the Cisco Identity Services Engine, which has intelligent mechanisms for identifying device types and user names on the network.
Reputation data of Internet hosts is obtained in real time from the cloud-based reputation database. This database in particular has dynamic information about active botnet control centers.
When the threshold value is reached, the CTD can perform a predetermined action. For example, issue a command to the firewall to block the suspicious activity of a specific host or block the switch port. Commands can be given automatically or semi-automatically (after confirmation by the administrator). The system has pre-installed scripts for routers and firewalls of different vendors, and it is also possible to create custom scripts.
What are we protecting from?
Cyber Threat Defense can be used in different security scenarios to protect against more diverse attacks.
In particular, CTD can detect and help block the following types of attacks and anomalies affecting information security:
- spreading malicious code and virus outbreaks,
- botnet activity,
- DDoS attacks
- network intelligence,
- unauthorized access to resources,
- unauthorized data accumulation
- data breach attempts
- the use of prohibited applications (such as P2P, IP telephony),
- unauthorized installation of services (for example, a website),
- violation of access policies and identification of gaps in the ITU configuration.

CTD is also an excellent tool for auditing information security, allowing you to check whether a network behaves as planned when setting up firewalls, IPS, and network infrastructure.
And, of course, Cyber Threat Defense can assist in the investigation of cyber incidents, the study of the propagation of malicious code and attack vectors. Since information is stored on all network flows and sessions, it is possible to find out with whom and how a suspicious host has interacted at a certain point in time in the past.
Consider the mechanisms of Cyber Threat Defense on the example of the high-profile vulnerability OpenSSL HeartBleed.
The difficulty in identifying HearBlead was that, if the attacker correctly exploited the vulnerability, there would be no traces of the exploit in the web server logs. Also, SSL encryption makes it difficult to differentiate between normal and malicious transactions by request content and signatures. Therefore, to identify attempts to exploit the vulnerability, it is necessary to focus on the characteristics of the size of SSL requests and responses of the web server.
If you look at the system report with attempts to exploit the HeartBleed vulnerability on a test system, you can see two features of these transactions.

First, the ratio of the size of the client request and response is approximately 4.8%. Secondly, attacks aimed at HeartBleed are likely to create sessions with a longer lifetime. Each Heartbleed transaction returns a response to the attacker with the contents of a small piece of memory of the attacked web server. In order to obtain information of interest (SSL private keys or passwords), an attacker will have to repeat transactions many times and the user session will most likely last hours. CTD has a built-in mechanism for detecting such long-lived sessions (Suspect Long Flow).
Thus, using CTD, you can identify suspicious web transactions. Since NetFlow's network telemetry is usually stored for several months, it is also possible to find attacks that occurred in the past before the official publication of the vulnerability. Most importantly, to identify such attacks, you do not need to update signatures and the solution is able to find attacks from a “zero” day from the appearance of a vulnerability or exploit.

NetFlow is a great source of incident information, but not the only one. The development of Cisco Cyber Threat Defense is moving along the path of integration into the solution of additional sources of information - IPS SourceFire network, Cisco Advanced Malware Protection, email and web content filtering systems, cloud intelligence. The breadth of events, together with advanced processing and correlation technologies, will allow you to more accurately and quickly respond to the changing landscape of threats. Due to the limited size of the article, we focused only on the functionality of Cyber Threat Defense in terms of security. In fact, the CTD solution can also be very useful for IT administrators to monitor the network activity of users, monitor the use of network resources, analyze application performance and QoS. More on this in the following articles.
More information about the solution can be found at Cisco:
Source: https://habr.com/ru/post/229073/
All Articles