NSA monitors those interested in Linux and information security
Thanks to the documents of Snowden, last year it became known about the existence of the XKeyscore program, which monitors Internet traffic by keywords, search queries, etc.
Yesterday, German journalist Jacob Appelbaum — one of those to whom Edward Snowden handed over some of the NSA's secret documents — published the xkeyscorerules100.txt file, which operates on the XKeyscore system. These are a few rules that monitor user activity on the Internet.
XKeyscore Deep Packet Inspection software runs on 150 dedicated servers around the world, usually installed near major telecommunications hubs. The modular architecture of XKeyscore provides for downloading individual small “rules” (rules) written in Genesis and XKScript, as well as in C ++ and Python. According to these rules, useful information is extracted from recorded Internet traffic.
')
As can be seen from the published rules, the NSA put under surveillance two Tor network nodes in Berlin and Nuremberg. The agency has compiled a list of IP addresses that access these servers.
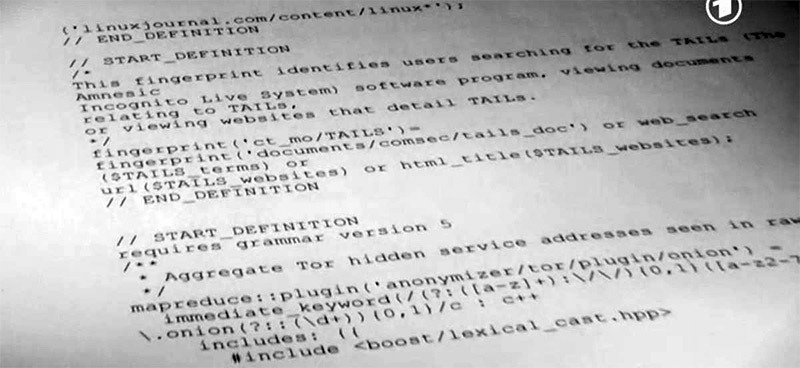
In addition, the NSA keeps track of those users who are looking for information on the web about the Linux operating system TAILS .
fingerprint('ct_mo/TAILS')= fingerprint('documents/comsec/tails_doc') or web_search($TAILS_terms) or url($TAILS_websites) or html_title($TAILS_websites) Funny, but other documents mention rules that track “potential extremists,” reading sites like Linux Journal. They are considered "extremist forums."
// START_DEFINITION /*These variables define terms and websites relating to the TAILs (The Amnesic Incognito Live System) software program, a comsec mechanism advocated by extremists on extremist forums. */ $TAILS_terms=word('tails' or 'Amnesiac Incognito Live System') and word('linux' or ' USB ' or ' CD ' or 'secure desktop' or ' IRC ' or 'truecrypt' or ' tor '); $TAILS_websites=('tails.boum.org/') or ('linuxjournal.com/content/linux*'); // END_DEFINITION There are rules for registering users who are interested in various information security services on the Internet, including HotSpotShield, FreeNet, Centurian, FreeProxies.org, MegaProxy, privacy.li and the anonymous mail service MixMinion. In the latter case, all traffic from the IP address is 128.31.0.34. It belongs to the MixMinion server, which is located on the campus of the Massachusetts Institute of Technology. By the way, besides the postal service, there are many other websites on this server, including open source games and other free projects.
Source: https://habr.com/ru/post/228665/
All Articles