What are dangerous "smart" power

Electricity is becoming more expensive, and the global economy is intensely seeking ways to improve its energy efficiency. In addition to solar and wind power plants around the world, there is an active construction of “smart” power distribution networks, the so-called Smart Grid, which allow rational use of energy. They are usually automated and connected to the Internet, which causes a natural interest in their level of security.
Attention! All vulnerabilities described in this article have been passed on to manufacturers and eliminated by them, but may occur in existing systems
')
What are they made of?
Smart Grid technologies are just preparing to conquer the world. Now they are mainly used in home automatic climate control systems, where the simplest elements of smart electricity grids are being introduced. Such devices allow the end user to monitor, effectively use the energy of wind and sun, and in their absence switch to other sources. Is a smart home grid dangerous for progressive homeowners? To answer this question, you need to know which control components of such networks.
In 2013, China invested $ 4.3 billion in Smart Grid, while global investments amounted to $ 14.9 billion. According to forecasts by Pike Research, by 2015 more than $ 46 billion will be spent on the transition to this technology, it is supported not only by economists, but and environmentalists. In Greenpeace, for example, we are confident that Smart Grid networks will save the planet.
Fingerprint utilities send requests to a remote node in order to determine its belonging to one or another family. From the response to the request, you can determine the operating system or find out the modification of the device.
After a short fingerprint study, we found traces of embedded systems on the Internet from at least nine different manufacturers, on the basis of which Smart-Grid systems are being built.
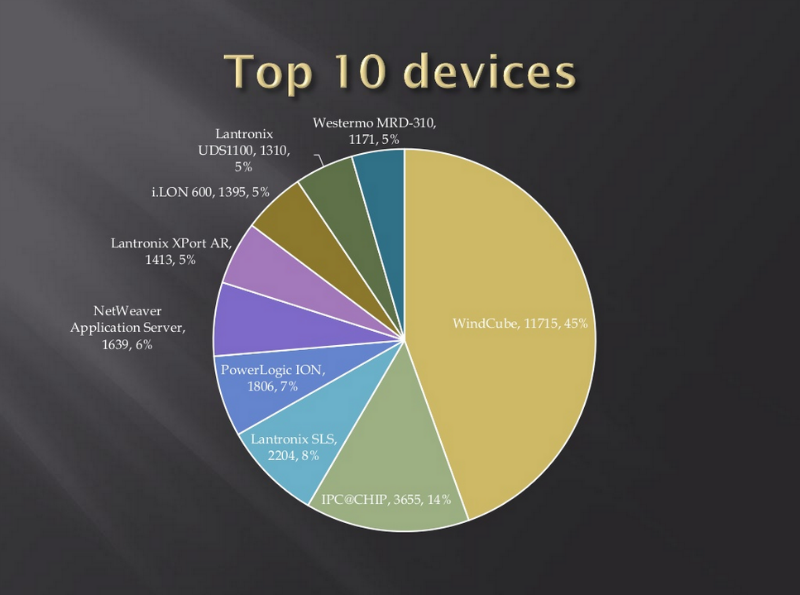
Smart Grid Microcontroller Statistics
WindCube turned out to be the most widespread family, but more “intelligent” devices of another manufacturer were chosen as a testing ground. The online catalog contains a controller with many promising features: PowerPC processor, RTOS real-time operating system, built-in web server, FTP support , Telnet, SSH, TCP / IP, HTTP, PPP.
We are looking for the smartest
Searching the Internet for Smart-Grid systems based on selected controllers did not cause much difficulty. Again, thanks to the official website of the manufacturer, which indicates the name of the operating system and posted instructions, according to which the owner of the device’s family’s device configuration settings can be found at ..... / ZZZ . After that, we went to Google, where we used the inurl modifier, which allows us to search for information in the subdirectories of the site, and entered a combination of the name of the OS and ZZZ. As a result, we received several pages with IP addresses, subnet masks and serial numbers of specific devices. But what systems do these microcomputers work with?
Dorks - keywords, URLs, or their components that allow you to find a path to the admin panel or to an error page using search engines or web crawlers.
As it turned out on one of the detected pages, the platform under study is working, in particular, as part of the Solar-Log photovoltaic monitoring systems, which have proven to be extremely common. According to the developer, more than 200 thousand solar power plants and almost 1 million inverters connected to the company's web server are operating in the world.

Solar panels connected to the Solar-Log web server
We disassemble the firmware
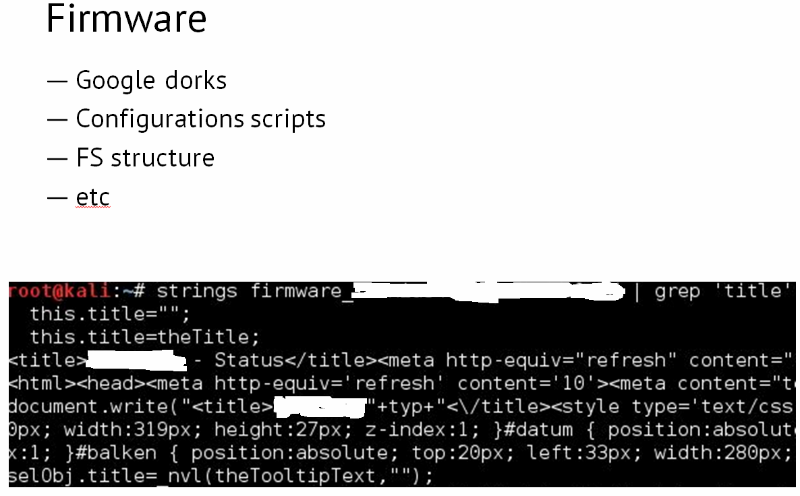
Cross-section firmware
After downloading the firmware for the Solar-Log systems, we looked at how its file structure looked, looked for “dorks” (Google dorks) and configuration scripts that allow us to manage the system. Using the strings and grep commands, the Solar-Log Client header was found in the firmware, which prompted the idea to google the inurl URL: Solar-Log-Client. As a result, we found many private user systems and pages with data on the power consumption of various Smart-Grid systems from Solar-Log. But this information may be of interest except for the supervisory authorities, but not for the attacker.

Power generation data from various Smart-Grid systems from Solar-Log
Possible without a password
More curious things were found in the admin panel. When studying Solar-Log admins, an interesting fact emerged: approximately 5% of the systems did not require a password to enter the configuration page. The remaining 95% of the systems had their password set, but there was little use for it. By forming a simple request to a single configuration script, you could force the Solar-Log admin panel to quietly give a backup of the configuration, download it to your local computer, and retrieve the password.
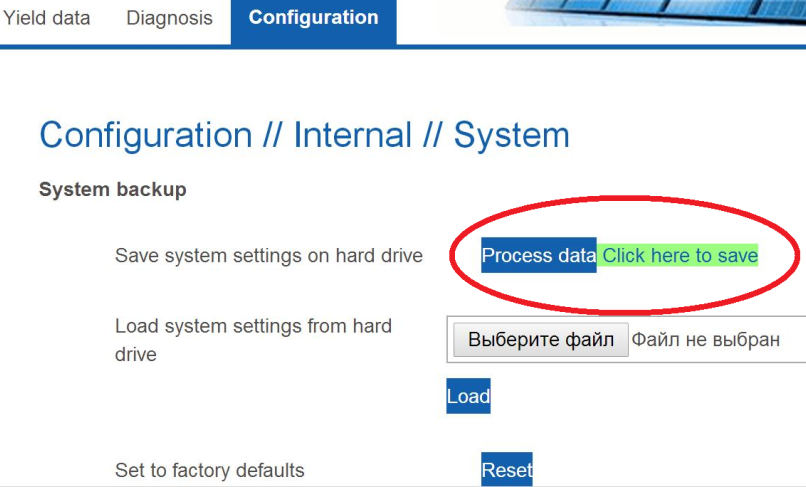
Admin panel
With the decryption of the password, which was always under the index 222, there were some difficulties. The HEX editor gave out some sort of rubbish, so we went the opposite way: looked at the device that was without a password, entered a random password (1234567890), saved it, then downloaded the configuration file and looked at how it looks in encrypted form.

Backup Configuration File
Similarly, you can make a list of all the necessary passwords match their encrypted options.
Go ahead
Getting to the Solar-Log configuration page, as you can see, turned out to be quite easy. A firmware download is available from this page, where you can search for curious artifacts. By the way, the official documentation states that the firmware update process is password protected. However, we were faced with the need to enter a password only on one of the systems, and it was very simple, coincided with the login and was inaccessible for changing to the ordinary user.
What tomorrow?
Users of “smart houses” and mini-offices connected to alternative energy sources are, in fact, beta testers of Smart Grid systems. And the developers are not too sparing economical owners, allowing serious errors in the mechanisms of protection. In our case, anyone could choose one of hundreds of thousands of owners of Smart Grid installations from Solar-Log on the Internet, bypass authorization (sometimes it is not required), remotely install defective firmware, take control of access to system parameters management, penetrate other network segments. Physical impacts are also possible, including disabling inverters, fire and other unpleasant events.
If the power supply networks of critical facilities will be intellectualized with the same haste, the level of risk may not be lower than in the case of SCADA systems, and the plot, when the attackers use a computer to disconnect the whole city from the power supply, will be quite realistic.
Author: Artem Chaykin
Source: https://habr.com/ru/post/228595/
All Articles