New encryption options for Android found
Earlier we wrote about a new version of the extortionist for Android, which encrypts user files and is called Simplocker. Now we have additional information about other variants of this malicious program. These detected modifications differ from each other in the following ways.

')

Fig. Screenshot of the ransom demand form in the case of Android / Simplocker.B , which shows the portrait of the victim. Russian rubles are indicated as a currency for redemption.
A simplified approach to encryption using the AES algorithm and a hard-wired key is still present in most of the malware modifications that we found. In addition, some of these modifications do not include the encryption capability, that is, they do not encrypt files, but simply block access to the device.
As mentioned in our previous posts, the threat is most prevalent in Russia and Ukraine. When it hits the user's device, Android / Simplocker really gives him considerable trouble, as the user loses access to his files.

Fig. The geography of the spread of Android / Simplocker according to ESET LiveGrid cloud technology.
One of the most important issues when a malware is detected is its origin or infection vector, that is, how it can get on the user's device. Our ESET LiveGrid telemetry system showed several Android / Simplocker infection vectors. For him, the typical distribution method is disguise as an application related to pornography. In addition, the attackers also masked the extortionist for the game, for example, Grand Theft Auto: San Andreas.

Fig. Porn site that distributes Android / Simplocker.

Fig. Fake badge of the game Grand Theft Auto: San Andreas.
During the investigation, we discovered that Android / Simplocker spreads through another malicious program, so-called. Downloader or downloader that remotely loads the main Simplocker file. Using such boot loaders is common practice in the Windows world, but recently they have been used for Android as well.
Downloaders are an additional vector of malware distribution for Android. They complement traditional methods of social engineering, for example, the use of porn, as mentioned above. Another way to install malicious code on a device is to exploit a vulnerability in the software or OS.
The sample of one of the downloaders we analyzed is detected as Android / TrojanDownloader.FakeApp . He convinces the user to download a fake video player, which, in fact, is Android / Simplocker. Such an application as a downloader is much more likely to avoid exposing its malicious activity by Google Play security applications, such as Bouncer, due to the following features:
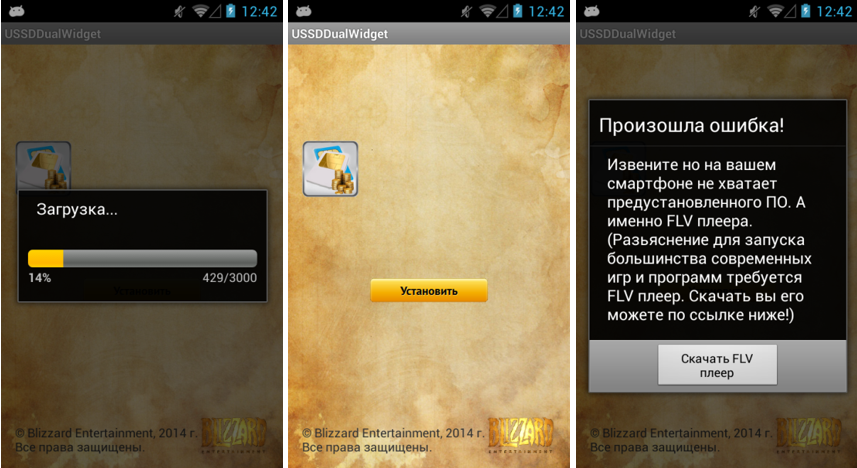
In addition, in the sample we analyzed, the URL that is contained in the application does not directly indicate the malicious APK file with Simplocker. Instead, the Trojan program is downloaded to the device after redirection to another server that is under the control of intruders. This loader was disguised in the app store as a legitimate application called USSDDualWidget.
- Using Tor. Some modifications use common domains to communicate with C & C, others use .onion domains that belong to Tor .
- Various ways of transmitting the decrypt command, which signals the fact of receiving a ransom by hackers.
- Various windows interface with information on the purchase, as well as various currencies to pay for it (Ukrainian hryvnia and Russian ruble).
- Using camera shots. Some modifications of Simplocker add a photo of the phone owner, which was made to the built-in camera, to the ransomware window interface.

')

Fig. Screenshot of the ransom demand form in the case of Android / Simplocker.B , which shows the portrait of the victim. Russian rubles are indicated as a currency for redemption.
A simplified approach to encryption using the AES algorithm and a hard-wired key is still present in most of the malware modifications that we found. In addition, some of these modifications do not include the encryption capability, that is, they do not encrypt files, but simply block access to the device.
As mentioned in our previous posts, the threat is most prevalent in Russia and Ukraine. When it hits the user's device, Android / Simplocker really gives him considerable trouble, as the user loses access to his files.

Fig. The geography of the spread of Android / Simplocker according to ESET LiveGrid cloud technology.
One of the most important issues when a malware is detected is its origin or infection vector, that is, how it can get on the user's device. Our ESET LiveGrid telemetry system showed several Android / Simplocker infection vectors. For him, the typical distribution method is disguise as an application related to pornography. In addition, the attackers also masked the extortionist for the game, for example, Grand Theft Auto: San Andreas.

Fig. Porn site that distributes Android / Simplocker.

Fig. Fake badge of the game Grand Theft Auto: San Andreas.
During the investigation, we discovered that Android / Simplocker spreads through another malicious program, so-called. Downloader or downloader that remotely loads the main Simplocker file. Using such boot loaders is common practice in the Windows world, but recently they have been used for Android as well.
Downloaders are an additional vector of malware distribution for Android. They complement traditional methods of social engineering, for example, the use of porn, as mentioned above. Another way to install malicious code on a device is to exploit a vulnerability in the software or OS.
The sample of one of the downloaders we analyzed is detected as Android / TrojanDownloader.FakeApp . He convinces the user to download a fake video player, which, in fact, is Android / Simplocker. Such an application as a downloader is much more likely to avoid exposing its malicious activity by Google Play security applications, such as Bouncer, due to the following features:
- the fact that the application opens the URL (navigates through it) does not yet indicate its malicious activity;
- The loader itself does not require “potentially dangerous” permissions for its application.
In addition, in the sample we analyzed, the URL that is contained in the application does not directly indicate the malicious APK file with Simplocker. Instead, the Trojan program is downloaded to the device after redirection to another server that is under the control of intruders. This loader was disguised in the app store as a legitimate application called USSDDualWidget.

Source: https://habr.com/ru/post/226847/
All Articles