un1c0rn, "Google for vulnerabilities"
On Habré already appeared articles about unprotected mongodb instances and unpatched openssl with heartbleed.
The un1c0rn project decided not to waste time on trifles and to make a whole “vulnerability search engine”, in an article on Motherboard.vice.com, un1c0rn was even called “Google for vulnerabilities.”
UPDATE 06/17/14 - un1c0rn became paid! Now, to access the results of the exploits, they are asked to transfer a sum of at least 0.01 BTC to their wallet
')
The principle of operation is similar to Shodan : the robot scans certain ports for all IP addresses (currently more than 62 thousand areabout 59 000 ), but unlike shodan it also launches a set of exploits, and, strangely enough, publishes the results in open form on the website .
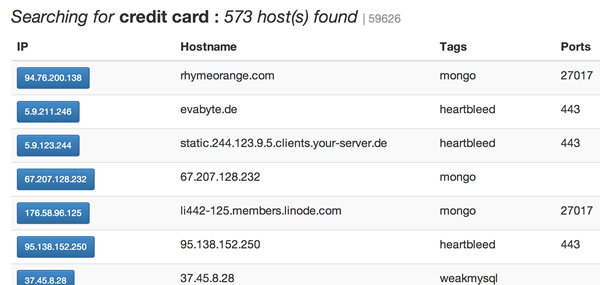
The authors of the article argue that if you type in the search box “credit card” and delve into the results you can find a lot of interesting things.
“Rummage” must be thoroughly, because the search leaves much to be desired (for example, you cannot filter by the same IP or range). I myself, to be honest, didn’t go further into viewing the results, but what I saw seems to be quite dangerous information, especially in vulnerabilities like heartbleed.
The un1c0rn project decided not to waste time on trifles and to make a whole “vulnerability search engine”, in an article on Motherboard.vice.com, un1c0rn was even called “Google for vulnerabilities.”

UPDATE 06/17/14 - un1c0rn became paid! Now, to access the results of the exploits, they are asked to transfer a sum of at least 0.01 BTC to their wallet
Warning:
Only part of the leaked data is available.
Send your contribution to ... (> 0.01 BTC) to unlock the full leak.
')
The principle of operation is similar to Shodan : the robot scans certain ports for all IP addresses (currently more than 62 thousand are
The authors of the article argue that if you type in the search box “credit card” and delve into the results you can find a lot of interesting things.
“Rummage” must be thoroughly, because the search leaves much to be desired (for example, you cannot filter by the same IP or range). I myself, to be honest, didn’t go further into viewing the results, but what I saw seems to be quite dangerous information, especially in vulnerabilities like heartbleed.
for example
un1c0rn.net/?module=hosts&action=detail&ip=168.144.27.186
- heartbleed - 8443 | b6j8
95c3166d6a53d23026887c1f8c; locale = en-US; psaContext = dashboard; BarExpanded = True
u5hM]
D = ce1a9195c3166d6a53d23026887c1f8c; locale = en-US; psaContext = dashboard
697178f7e7fa0c2863fb8f0886d9f04e / referer / branding-77-manage.myhosting.com / activated_by_mouse_click / true / nodeid / plesk_vps_main
Accept-Encoding: gzip, deflate, sdch
Accept-Language: en-US, en; q = 0.8
login_name = admin & passwd = Chicken1234 & locale = en-US & locale_id = en-US & login_locale = en-US ...
Or
un1c0rn.net/?module=hosts&action=detail&ip=212.186.117.162
- heartbleed - 443 | = RV>
yiNC
fFG>
Aog, C
r: 212.186.117.162/themes/pfsense_ng/login.css
Cookie: PHPSESSID = d5754d40720b50293753aeb61fc78954; cookie_test = 1401391652
Connection: keep-alive
If-Modified-Since: Fri, 12 Apr 2013 14:31:46 GMT
If-None-Match: "4079480975"
% 3Aed9e87ca72211055016df7735239f480bc83f0c1% 2C1397210984 & usernamefld = admin & passwordfld = khk% 2326% 239020 & login = Login
rjXp ~
UPDATE- Clear password for almost all systems with pfSense - string search & usernamefld = admin & passwordfld gives scary results
- heartbleed - 8443 | b6j8
95c3166d6a53d23026887c1f8c; locale = en-US; psaContext = dashboard; BarExpanded = True
u5hM]
D = ce1a9195c3166d6a53d23026887c1f8c; locale = en-US; psaContext = dashboard
697178f7e7fa0c2863fb8f0886d9f04e / referer / branding-77-manage.myhosting.com / activated_by_mouse_click / true / nodeid / plesk_vps_main
Accept-Encoding: gzip, deflate, sdch
Accept-Language: en-US, en; q = 0.8
login_name = admin & passwd = Chicken1234 & locale = en-US & locale_id = en-US & login_locale = en-US ...
Or
un1c0rn.net/?module=hosts&action=detail&ip=212.186.117.162
- heartbleed - 443 | = RV>
yiNC
fFG>
Aog, C
r: 212.186.117.162/themes/pfsense_ng/login.css
Cookie: PHPSESSID = d5754d40720b50293753aeb61fc78954; cookie_test = 1401391652
Connection: keep-alive
If-Modified-Since: Fri, 12 Apr 2013 14:31:46 GMT
If-None-Match: "4079480975"
% 3Aed9e87ca72211055016df7735239f480bc83f0c1% 2C1397210984 & usernamefld = admin & passwordfld = khk% 2326% 239020 & login = Login
rjXp ~
UPDATE- Clear password for almost all systems with pfSense - string search & usernamefld = admin & passwordfld gives scary results
Source: https://habr.com/ru/post/226089/
All Articles