We kill the "bell" from Google Chrome in the tray

Recently, Google Chrome has a new feature with the name of the alert. From time to time, under incomprehensible circumstances, a bell appears in the system tray, that's all. That is, if you do not configure it manually, it simply takes place there without performing any functions. And in order for it to appear there, for example, it’s enough to deploy a full-screen video in YouTube, then you cannot remove it, just close the chrome. Finding ways to remove it properly did not succeed. Ways like and worked but then the bell reappeared in the tray, and annoyed. One evening he got a lot, and had to take on heavy artillery.
IDA, Hiew, Bell Cutting
The first thing we look at is where Google Crhome itself lies, I looked at the shortcut it lies, as it turned out, in% USERPROFILE% \ AppData \ Local \ Google \ Chrome \ Application and apparently there are two versions, past and current. Now we need the 35.0.1916.114 directory in it there is a lot of dll'ok, but for some reason I immediately liked chrome.dll. Copy it somewhere to a convenient place open in IDA, and start to wait, 28 megabytes is pretty impressive. While we wait, we will think a little what to look for further. In general, there are not many options, but rather one (for Win) API function Shell_NotifyIcon from shell32.dll will be searched for it. So while we thought IDA had already analyzed the file. Go to the Import tab and look for the function we need there.
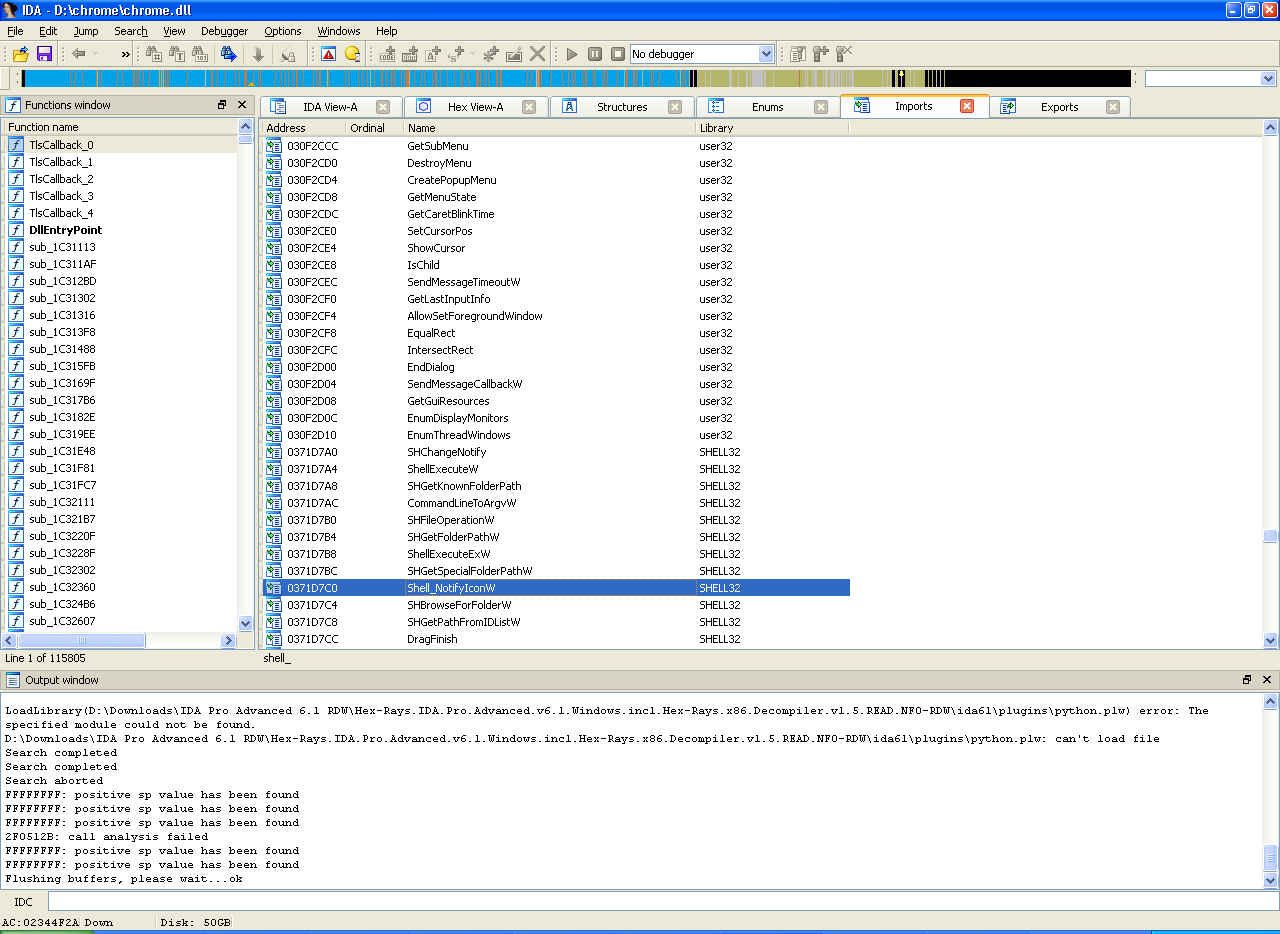
We are lucky feature imported. And to call it, the address 0x371d7c0 will be used . In general, we no longer need the IDA. So we have the address to which the function we need is imported. Then immediately there is an idea to replace all calls to this function with the NOP, but it is worth remembering how the call to WinApi functions occurs. Yeah, here's the stack problem, we have to clear ourselves, but let's see what we can do. Open the dll in Hiew, switch it to Asm mode (Press Enter twice) and start searching for a function call by searching for the address we already know in the file here. Don't forget that in x86 the numbers are written in reverse order, from the low byte to the high byte that is, it is necessary to search not 371d7c0 but c0d77103 . What in general we find
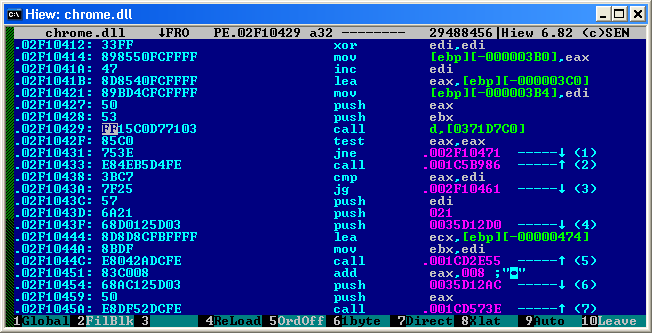
So, we have FF 15 C0 D7 71 03 6 bytes to call the function, we need to replace them by clearing the stack and let's be honest with chrome resetting the EAX register. The latter is necessary so that Chrome understood that for some reason he was unable to add the icon to the tray. The Shell_NotifyIcon function takes two parameters, so two parameters must also be removed from the stack. I decided to use two pop eax calls for this, followed by a reset of EAX via XOR EAX, EAX, and then two more bytes remain that NOP scored.
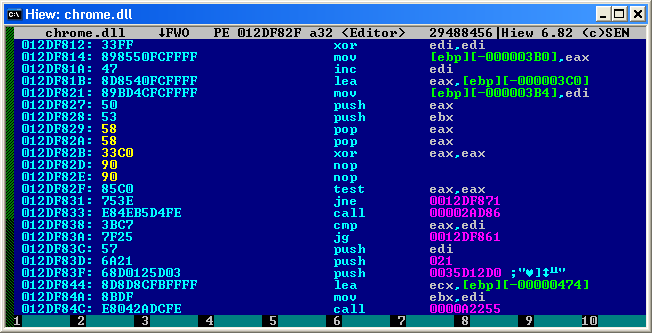
As a result, we get the following: you need to change the sequence of bytes FF15C0D77103 to 585833C09090, which is done simply by searching and replacing. There were seven such calls. Then we copy the dll processed by us to its rightful place (having previously closed all Google Chrome). We are launching Chrome trying to get the appearance of the bell by turning YouTuba to full screen, but nothing comes out, the bell is no more, the result is a victory.
Ps. I myself do not really like this method, I hope that Google will introduce a full-time opportunity to disable this functionality, but for now it will come down.
')
Source: https://habr.com/ru/post/225945/
All Articles