Microsoft and Adobe released a set of updates, June 2014
Microsoft has released a series of updates for its products, which fix 66 unique vulnerabilities in Windows, Internet Explorer and Office products. Two fixes have Critical status and four more Important. Critical update MS14-035 fixes 59 vulnerabilities in this year’s all versions of Internet Explorer 6-11 on all supported operating systems. This update also fixes last month’s 0day vulnerability CVE-2014-1770 in IE8. Fixed vulnerabilities are of type Remote Code Execution and allow an attacker to execute arbitrary code through a vulnerable version of the browser. A reboot is required to use MS14-035.
MS14-036 Critical Update is addressed to all supported operating systems starting with Windows Server 2003 and ending with Windows 8.1 / RT 8.1. It also affects some versions of Office 2007-2010. The fixed RCE vulnerability CVE-2014-1817 is contained in the Unicode String Processor component and can be used by attackers to deliver malicious code to the system through a web page. Another vulnerability CVE-2014-1818 is present in the gdi32.dll library (Windows GDI +) and allows attackers to remotely execute code through a specially crafted image file. A reboot is required to apply the patch. Exploit code likely .
')
Important update MS14-034 fixes one Remote Code Execution vulnerability CVE-2014-2778 in Microsoft Word version 2007. Attackers can execute arbitrary code in the system through a specially formed MS Word file (Embedded Font Vulnerability). The vulnerability is contained in the files winword.exe and wwlib.dll. Exploit code likely .
Important update MS14-033 fixes one Information Disclosure vulnerability CVE-2014-1816 in the XML Core Services (MSXML) component for all supported OS. Criminals can get the information of interest (the user's personal information) through a specially crafted web page that contains an MSXML control. Exploit code unlikely .
Important update MS14-032 fixes one Information Disclosure vulnerability CVE-2014-1823 in MS Lynk Server 2010-2013. Exploit code unlikely .
An important update MS14-031 fixes one Denial of Service vulnerability CVE-2014-1811 in the TCP implementation implementation subsystem (Fwpkclnt.sys and Tcpip.sys drivers). An attacker could cause Vista + to freeze by sending a large number of specially crafted network packets. Exploit code unlikely .
An important MS14-030 update fixes one CVE-2014-0296 vulnerability of the Tampering type in the RDP component for Windows 7 and Windows 8 / 8.1. Attackers can successfully attack Man-in-the-Middle and gain access to information (for reading or modification), passing between the server and the client in the RDP session (RDP MAC Vulnerability). Exploit code unlikely .
1 - Exploit code likely
The probability of exploiting the vulnerability is very high, attackers can use an exploit, for example, for remote code execution.
2 - Exploit code would be difficult to build
The exploitation probability is average, since attackers are unlikely to be able to achieve a situation of sustainable exploitation, as well as due to the technical peculiarities of vulnerability and the complexity of developing an exploit.
3 - Exploit code unlikely
The exploitation probability is minimal and attackers are unlikely to be able to develop successfully working code and take advantage of this vulnerability to conduct an attack.
We recommend our users to install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (by default this option is enabled).

Adobe has released the APSB14-16 hotfix for Flash Player. These updates close six Critical vulnerabilities, three of which: CVE-2014-0531, CVE-2014-0532, CVE-2014-0533 could allow an attacker to perform a XSS (cross-site-scripting) attack. Two more fixable vulnerabilities CVE-2014-0534 and CVE-2014-0535 are of type Security Feature Bypass. Vulnerability CVE-2014-0536 allows attackers to remotely execute code in the system.
Browsers such as Internet Explorer (10 & 11 on Windows 8 / 8.1 through Windows Update) and Google Chrome update their Flash Player versions automatically. For IE, see the updated Security Advisory 2755801 . Check your version of Flash Player here .
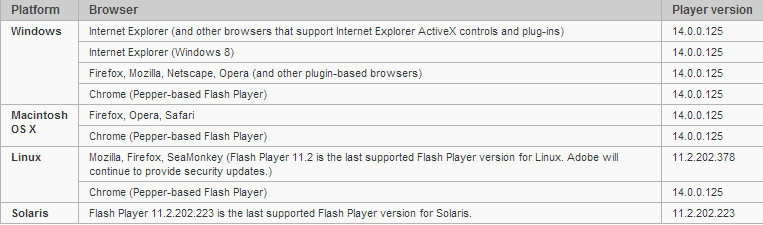
The current Flash Player versions for browsers are as follows.

be secure.

MS14-036 Critical Update is addressed to all supported operating systems starting with Windows Server 2003 and ending with Windows 8.1 / RT 8.1. It also affects some versions of Office 2007-2010. The fixed RCE vulnerability CVE-2014-1817 is contained in the Unicode String Processor component and can be used by attackers to deliver malicious code to the system through a web page. Another vulnerability CVE-2014-1818 is present in the gdi32.dll library (Windows GDI +) and allows attackers to remotely execute code through a specially crafted image file. A reboot is required to apply the patch. Exploit code likely .
')
Important update MS14-034 fixes one Remote Code Execution vulnerability CVE-2014-2778 in Microsoft Word version 2007. Attackers can execute arbitrary code in the system through a specially formed MS Word file (Embedded Font Vulnerability). The vulnerability is contained in the files winword.exe and wwlib.dll. Exploit code likely .
Important update MS14-033 fixes one Information Disclosure vulnerability CVE-2014-1816 in the XML Core Services (MSXML) component for all supported OS. Criminals can get the information of interest (the user's personal information) through a specially crafted web page that contains an MSXML control. Exploit code unlikely .
Important update MS14-032 fixes one Information Disclosure vulnerability CVE-2014-1823 in MS Lynk Server 2010-2013. Exploit code unlikely .
An important update MS14-031 fixes one Denial of Service vulnerability CVE-2014-1811 in the TCP implementation implementation subsystem (Fwpkclnt.sys and Tcpip.sys drivers). An attacker could cause Vista + to freeze by sending a large number of specially crafted network packets. Exploit code unlikely .
An important MS14-030 update fixes one CVE-2014-0296 vulnerability of the Tampering type in the RDP component for Windows 7 and Windows 8 / 8.1. Attackers can successfully attack Man-in-the-Middle and gain access to information (for reading or modification), passing between the server and the client in the RDP session (RDP MAC Vulnerability). Exploit code unlikely .
1 - Exploit code likely
The probability of exploiting the vulnerability is very high, attackers can use an exploit, for example, for remote code execution.
2 - Exploit code would be difficult to build
The exploitation probability is average, since attackers are unlikely to be able to achieve a situation of sustainable exploitation, as well as due to the technical peculiarities of vulnerability and the complexity of developing an exploit.
3 - Exploit code unlikely
The exploitation probability is minimal and attackers are unlikely to be able to develop successfully working code and take advantage of this vulnerability to conduct an attack.
We recommend our users to install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (by default this option is enabled).

Adobe has released the APSB14-16 hotfix for Flash Player. These updates close six Critical vulnerabilities, three of which: CVE-2014-0531, CVE-2014-0532, CVE-2014-0533 could allow an attacker to perform a XSS (cross-site-scripting) attack. Two more fixable vulnerabilities CVE-2014-0534 and CVE-2014-0535 are of type Security Feature Bypass. Vulnerability CVE-2014-0536 allows attackers to remotely execute code in the system.
Browsers such as Internet Explorer (10 & 11 on Windows 8 / 8.1 through Windows Update) and Google Chrome update their Flash Player versions automatically. For IE, see the updated Security Advisory 2755801 . Check your version of Flash Player here .
The current Flash Player versions for browsers are as follows.


be secure.
Source: https://habr.com/ru/post/225903/
All Articles