The use of two-factor authentication when connecting to 1C

Many of the clients of our company are very concerned about the security of access to 1C via the Internet. This situation is especially aggravated by the situation when accountants store their password on a sticker stuck to a monitor. In this scenario, the introduction of additional requirements for the complexity of the password and its regular weather changes does not.
To maximize the exclusion of the human factor, I was given the task of organizing two-factor authentication for web access to 1C. Below is a detailed description of how this works.
')
The first authentication factor is the username and password. As the second authentication factor, we will use one-time passwords sent as SMS messages to the registered user’s phone. Using SMS as a transport is a fairly convenient and common solution.
Along with SMS, we tested the use of tokens and the option of receiving a password via e-mail. Tokens are not the most convenient solution, since you have to buy a separate token for each user and install additional software on users' computers. The option of receiving passwords by e-mail was no longer due to the fact that not all of our users have access to e-mail at the time when they want to log in to 1C. In the end, they decided to use SMS as the most simple and convenient solution for receiving one-time passwords.
The result was this. From the user's point of view, the scheme of work looks like this:
Access to 1C is provided by a direct link to the database. When you go directly to the login window, it requires a username and password. At this step, the existence of the given user is checked and he has the right to access the site.

After that, the authorized user is sent a code by SMS.

Next, the user must enter the received six-digit numeric code. Time to enter the code - 3 minutes.

After entering the code, the user is redirected to the site, where he can log in to 1C.
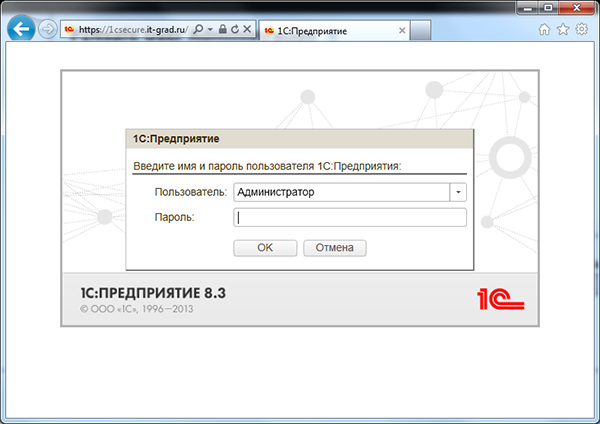
The boot screen ... a little bit more :)

Done! You can get to work!

Schematically, a two-factor authentication solution is the following:

Consider the algorithm of the system:
- The user connects via the received link to the proxy server, enters his login and password.
- UAG sends the login / password to the Swivel server via the RADIUS protocol. The RADIUS protocol is an authentication protocol that allows different systems to authenticate access to their resources.
- Swivel checks for the presence of such a user, the correctness of the password, and informs UAG about the success / failure of the first stage of authentication.
- If the first stage is successful, Swivel sends a one-time code through the SMS gateway.
- The user receives the code on his phone and enters it on the proxy server.
- The UAG sends the code to the Swivel server and receives an answer about the success / failure of the second authentication stage.
- If the code is successfully entered, the user gets access to the 1C Web server.
Of all the variety of servers depicted in the diagram, the most interesting, in my opinion, is the two-factor authentication server Swivel. It supports a variety of authentication methods, including a mobile application, SMS, OATH tokens and a phone call, as well as strong authentication by displaying images in the browser. In our implementation, one-time passwords are sent via SMS. In addition, Swivel software integrates with a large number of different applications and servers, has an extensive knowledge base on setting up and solving possible problems.
In the process of choosing a product for two-step authentication along with Swivel, I happened to consider RSA and Aladdin variants. RSA is a rather expensive product with a wide range of possibilities, which for our task is like shooting a gun on sparrows. Aladdin and Swivel are similar in functionality and are in the same price range. The main difference between Swivel is that Swivel has a permanent license, Aladdin has a one-year or two-year license. In the end, I stopped at the server and software Swivel. Here are some screenshots of the server management console:
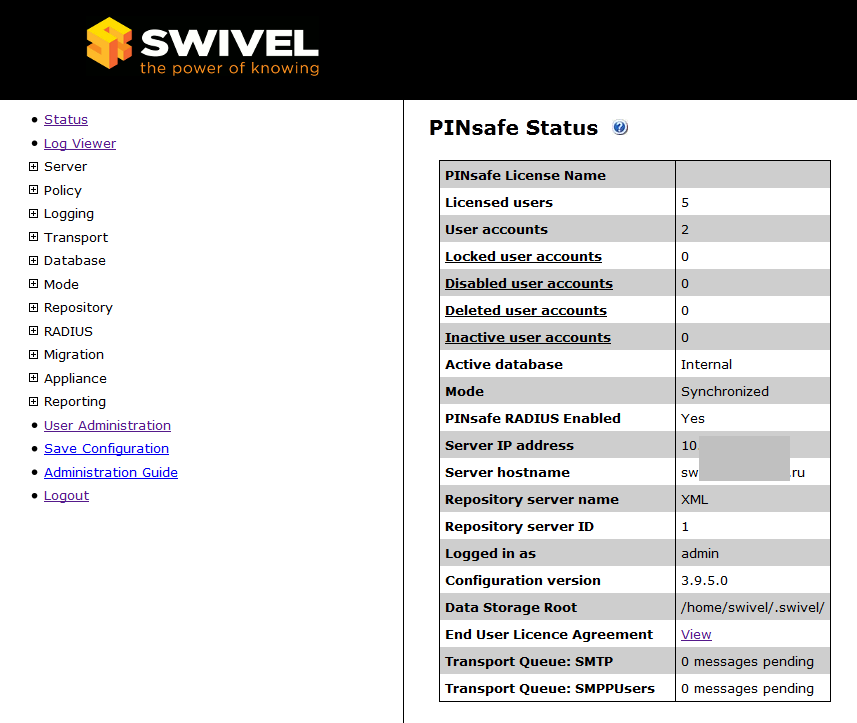
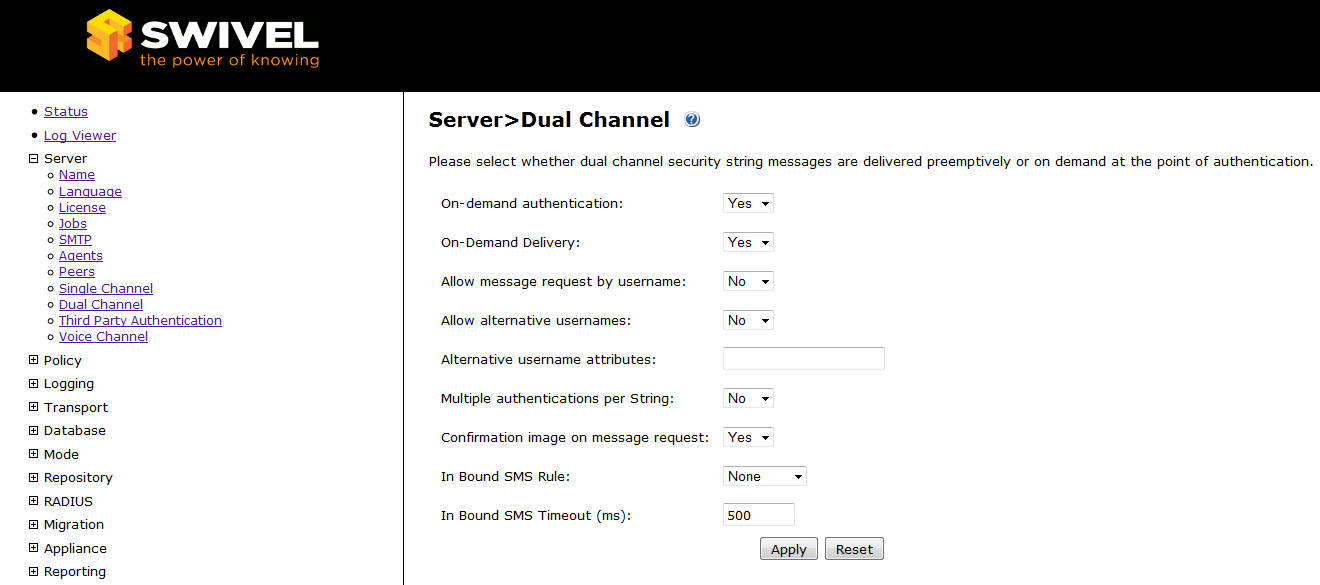


I hope that I have revealed the solution as fully as possible, write my questions.
Source: IT-GRAD
Source: https://habr.com/ru/post/225503/
All Articles