Extortionist for Android encrypts files on the device
Last week, our anti-virus laboratory discovered an interesting sample of malicious code for Android. It is an extortionist (ransomware) for devices running Android, which encrypts user files, and then demands a ransom for their decryption. This type of ransomware is widespread in the Windows world. Attackers encrypt user files, and then block the desktop for ransom.
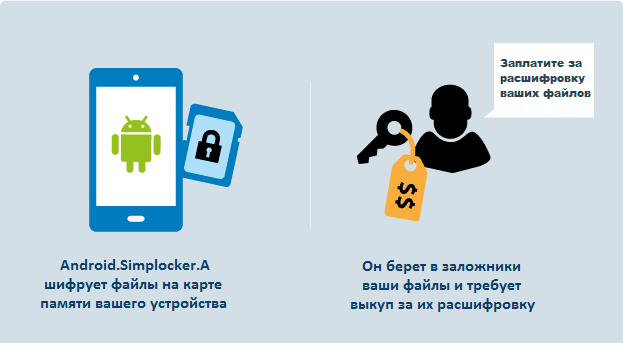
Malware has been added to our databases as Android / Simplocker . After infecting the device, it checks the memory card for the presence of certain types of files there, then encrypts them and blocks access to the device with a message about redemption. Simplocker performs its operations in the same way as extortionists for Windows do.
')
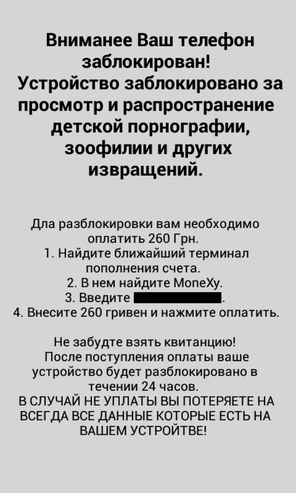
Fig. A message that a malicious program displays when a device is blocked.
As can be seen in the screenshot above, the message about blocking is written in Russian and requires payment of ransom in Ukrainian hryvnias, which suggests the focus of the extortionist on Ukraine. Note that the very first Android SMS Trojans ( including Android / Fakeplayer ), which appeared in 2010, also have Russian and Ukrainian origin.
The attackers send the victim to pay for the ransom using the MoneyXy service, since the clients of this service are not so easy to track down, unlike the clients of ordinary payment systems that work with credit cards.
After the infection of the device, the malicious code Android / Simplocker.A will check the file system of the memory card for the presence of pictures, documents or videos, i.e. files with the following extensions: jpeg, jpg, png, bmp, gif, pdf, doc, docx, txt, avi, mkv, 3gp, mp4. After detecting these files, each of them will be encrypted using AES symmetric encryption algorithm.
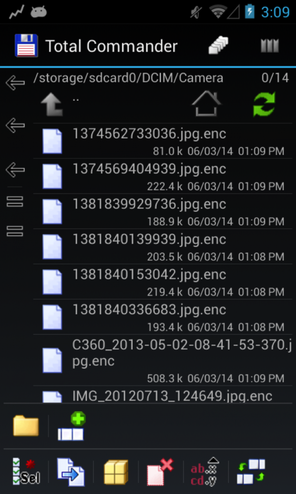
Fig. Encrypted Android / Simplocker.A files. A new .enc extension has been added for each file.
The extortioner interacts with his remote C & C server and sends him some identifying information about the device, for example, an IMEI ID. It is interesting to note that the URL of the C & C server itself is located on the .onion domain, which belongs to the anonymous TOR network. This allows attackers to ensure an adequate level of anonymity.
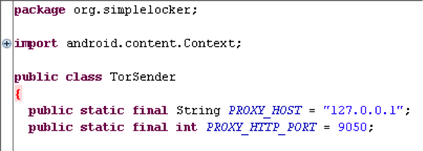
Fig. Part of the Android / Simplocker.A code to connect to the TOR network.
As you can see in the screenshot of the blocking screen above, the message does not contain a special field for entering a code confirming receipt of a ransom by intruders. Such a field for entering code is widespread in the case of ransomware for Windows. Instead, Android / Simplocker.A constantly listens to the connection to the C & C server to receive a message confirming that the funds have been successfully transferred to intruders.
The sample of Android / Simplocker.A analyzed by us was distributed as an application with the name “Sex xionix”. It has not been found on Google Play and we believe that it has a fairly low prevalence rate today.
Our analysis of this threat showed that in the case of Simplocker, attackers managed to get closer to implementing the concept of the infamous extortionist Cryptolocker, who made a lot of noise in the Windows world. Despite the fact that Android / Simplocker.A contains the code for decrypting encrypted files on the device, we strongly advise users not to be abused by intruders. There is no guarantee that after the required amount has been paid, the files will be decrypted or you will not fall into the bait of the intruders again.
We recommend that users protect themselves from this type of threat through prevention and protective proactive measures. To do this, you can use the ESET Mobile Security for Android application, which will keep your device secure. When working with Android, do not install applications from unreliable sources on your device; this will significantly reduce the risk of malware being compromised by the device. Perform timely backup of data on your device, this is one of the best ways to protect against extortionists, cryptographers, as it allows you to quickly restore your data from a backup source.

Malware has been added to our databases as Android / Simplocker . After infecting the device, it checks the memory card for the presence of certain types of files there, then encrypts them and blocks access to the device with a message about redemption. Simplocker performs its operations in the same way as extortionists for Windows do.
')

Fig. A message that a malicious program displays when a device is blocked.
As can be seen in the screenshot above, the message about blocking is written in Russian and requires payment of ransom in Ukrainian hryvnias, which suggests the focus of the extortionist on Ukraine. Note that the very first Android SMS Trojans ( including Android / Fakeplayer ), which appeared in 2010, also have Russian and Ukrainian origin.
The attackers send the victim to pay for the ransom using the MoneyXy service, since the clients of this service are not so easy to track down, unlike the clients of ordinary payment systems that work with credit cards.
After the infection of the device, the malicious code Android / Simplocker.A will check the file system of the memory card for the presence of pictures, documents or videos, i.e. files with the following extensions: jpeg, jpg, png, bmp, gif, pdf, doc, docx, txt, avi, mkv, 3gp, mp4. After detecting these files, each of them will be encrypted using AES symmetric encryption algorithm.

Fig. Encrypted Android / Simplocker.A files. A new .enc extension has been added for each file.
The extortioner interacts with his remote C & C server and sends him some identifying information about the device, for example, an IMEI ID. It is interesting to note that the URL of the C & C server itself is located on the .onion domain, which belongs to the anonymous TOR network. This allows attackers to ensure an adequate level of anonymity.

Fig. Part of the Android / Simplocker.A code to connect to the TOR network.
As you can see in the screenshot of the blocking screen above, the message does not contain a special field for entering a code confirming receipt of a ransom by intruders. Such a field for entering code is widespread in the case of ransomware for Windows. Instead, Android / Simplocker.A constantly listens to the connection to the C & C server to receive a message confirming that the funds have been successfully transferred to intruders.
The sample of Android / Simplocker.A analyzed by us was distributed as an application with the name “Sex xionix”. It has not been found on Google Play and we believe that it has a fairly low prevalence rate today.
Our analysis of this threat showed that in the case of Simplocker, attackers managed to get closer to implementing the concept of the infamous extortionist Cryptolocker, who made a lot of noise in the Windows world. Despite the fact that Android / Simplocker.A contains the code for decrypting encrypted files on the device, we strongly advise users not to be abused by intruders. There is no guarantee that after the required amount has been paid, the files will be decrypted or you will not fall into the bait of the intruders again.
We recommend that users protect themselves from this type of threat through prevention and protective proactive measures. To do this, you can use the ESET Mobile Security for Android application, which will keep your device secure. When working with Android, do not install applications from unreliable sources on your device; this will significantly reduce the risk of malware being compromised by the device. Perform timely backup of data on your device, this is one of the best ways to protect against extortionists, cryptographers, as it allows you to quickly restore your data from a backup source.
Source: https://habr.com/ru/post/225331/
All Articles